UNITED STATES
SECURITIES AND EXCHANGE COMMISSION
Washington, D.C. 20549
FORM
(Mark One)
ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 |
For the fiscal year ended
OR
TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 FOR THE TRANSITION PERIOD FROM TO |
Commission File Number
(Exact name of Registrant as specified in its Charter)
(State or other jurisdiction of incorporation or organization) |
(I.R.S. Employer Identification No.) |
(Address of principal executive offices) |
(Zip Code) |
Registrant’s telephone number, including area code: (
Securities registered pursuant to Section 12(b) of the Act:
Title of each class |
|
Trading Symbol(s) |
|
Name of each exchange on which registered |
|
|
The |
Securities registered pursuant to Section 12(g) of the Act: None
Indicate by check mark if the Registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. YES ☐
Indicate by check mark if the Registrant is not required to file reports pursuant to Section 13 or 15(d) of the Act. YES ☐
Indicate by check mark whether the Registrant: (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the Registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days.
Indicate by check mark whether the Registrant has submitted electronically every Interactive Data File required to be submitted pursuant to Rule 405 of Regulation S-T (§232.405 of this chapter) during the preceding 12 months (or for such shorter period that the Registrant was required to submit such files).
Indicate by check mark whether the registrant is a large accelerated filer, an accelerated filer, a non-accelerated filer, smaller reporting company, or an emerging growth company. See the definitions of “large accelerated filer,” “accelerated filer,” “smaller reporting company,” and “emerging growth company” in Rule 12b-2 of the Exchange Act.
|
☒ |
|
Accelerated filer |
|
☐ |
|
|
|
|
|
|||
Non-accelerated filer |
|
☐ |
|
Smaller reporting company |
|
|
|
|
|
|
|
|
|
Emerging growth company |
|
|
|
|
|
|
If an emerging growth company, indicate by check mark if the registrant has elected not to use the extended transition period for complying with any new or revised financial accounting standards provided pursuant to Section 13(a) of the Exchange Act. ☐
Indicate by check mark whether the registrant has filed a report on and attestation to its management’s assessment of the effectiveness of its internal control over financial reporting under Section 404(b) of the Sarbanes-Oxley Act (15 U.S.C. 7262(b)) by the registered public accounting firm that prepared or issued its audit report.
Indicate by check mark whether the Registrant is a shell company (as defined in Rule 12b-2 of the Exchange Act). YES
As of June 25, 2021, the last business day of the registrant’s most recently completed second quarter, the aggregate market value of the voting and non-voting common equity held by non-affiliates of the Registrant was $
As of February 17, 2022 there were
Table of Contents
|
|
Page |
PART I |
|
|
Item 1. |
4 |
|
Item 1A. |
14 |
|
Item 1B. |
49 |
|
Item 2. |
49 |
|
Item 3. |
49 |
|
Item 4. |
49 |
|
|
|
|
PART II |
|
|
Item 5. |
50 |
|
Item 6. |
51 |
|
Item 7. |
Management’s Discussion and Analysis of Financial Condition and Results of Operations |
52 |
Item 7A. |
79 |
|
Item 8. |
80 |
|
Item 9. |
Changes in and Disagreements With Accountants on Accounting and Financial Disclosure |
123 |
Item 9A. |
123 |
|
Item 9B. |
123 |
|
Item 9C. |
Disclosure Regarding Foreign Jurisdictions that Prevent Inspections |
123 |
|
|
|
PART III |
|
|
Item 10. |
124 |
|
Item 11. |
130 |
|
Item 12. |
Security Ownership of Certain Beneficial Owners and Management and Related Stockholder Matters |
156 |
Item 13. |
Certain Relationships and Related Transactions, and Director Independence |
159 |
Item 14. |
160 |
|
|
|
|
PART IV |
|
|
Item 15. |
162 |
|
Item 16 |
166 |
i
Cautionary Note Regarding Forward-Looking Statements
The discussion below contains forward-looking statements, which are subject to safe harbors under the Securities Act of 1933, as amended (the Securities Act) and the Exchange Act of 1934, as amended (the “Exchange Act”). Forward-looking statements include references to our ability to utilize our deferred tax assets, as well as statements including words such as “expects,” “plans,” “anticipates,” “believes,” “estimates,” “predicts,” “goal,” “intent,” “momentum,” “projects,” and similar expressions. In addition, projections of our future financial performance; anticipated growth and trends in our businesses and in our industries; the anticipated impacts of acquisitions, restructurings, stock repurchases, and investment activities; the outcome or impact of pending litigation, claims or disputes; statements regarding any future dividends; plans for and anticipated benefits of our solutions; matters arising out of the ongoing U.S. Securities and Exchange Commission (the “SEC”) investigation; the impact of the Covid-19 pandemic on our business operations and target markets; and other characterizations of future events or circumstances are forward-looking statements. These statements are only predictions, based on our current expectations about future events and may not prove to be accurate. We do not undertake any obligation to update these forward-looking statements to reflect events occurring or circumstances arising after the date of this report. These forward-looking statements involve risks and uncertainties, and our actual results, performance, or achievements could differ materially from those expressed or implied by the forward-looking statements on the basis of several factors.
We may not actually achieve the plans, intentions, or expectations disclosed in our forward-looking statements, and you should not rely on our forward-looking statements in making your investment decision. Actual results or events could differ materially from the plans, intentions, and expectations disclosed in the forward-looking statements we make. Important factors that could cause actual results and events to differ materially from those indicated in the forward-looking statements include, among others, the following:
1
SUMMARY OF RISKS ASSOCIATED WITH OUR BUSINESS
Our business is subject to a number of risks, which are discussed more fully under the heading “Risk Factors” in this Annual Report on Form 10-K. These risks include the following:
2
3
PART I
Item 1. Business.
ORGANIZATION
McAfee Corp. (the “Corporation”) (or “we,” “us” or “our”) was incorporated in Delaware on July 19, 2019. The Corporation was formed for the purpose of completing an initial public offering (“IPO”) and related transactions in order to carry on the business of Foundation Technology Worldwide LLC (“FTW”) and its consolidated subsidiaries (the Corporation, FTW and its subsidiaries are collectively the “Company”). On October 21, 2020, the Corporation became the sole managing member and holder of 100% of the voting power of FTW due to the Reorganization Transactions. With respect to the Corporation and the Company, each entity owns only the respective entities below it in the corporate structure and each entity has no other material operations, assets, or liabilities. See Note 1 to the Consolidated Financial Statements in Part II, Item 8 for a detailed discussion of the Reorganization Transactions, as defined in that footnote, and the IPO.
AGREEMENT AND PLAN OF MERGER; PROPOSED MERGER
On November 5, 2021, the Company entered into an Agreement and Plan of Merger (the “Merger Agreement”) with Condor BidCo, Inc., a Delaware corporation (“Parent”), and Condor Merger Sub, Inc., a Delaware corporation and wholly owned subsidiary of Parent (“Merger Subsidiary”), pursuant to which Merger Subsidiary will merge with and into the Company whereupon the separate corporate existence of Merger Subsidiary will cease and the Company will be the surviving corporation in the Merger and will continue as a wholly owned subsidiary of Parent (the “Merger”). Parent has obtained equity financing and debt financing commitments for the purpose of financing the transactions contemplated by the Merger Agreement. Affiliates of funds advised by each of Advent International Corporation, Permira Advisers LLC, Crosspoint Capital Partners L.P., Abu Dhabi Investment Authority, and Canada Pension Plan Investment Board and GIC Private Ltd. have committed to capitalize Parent at the Closing with an aggregate equity contribution equal to $5.2 billion on the terms and subject to the conditions set forth in signed equity commitment letters. On February 3, 2022, Merger Subsidiary received commitments of $5,160 million under a proposed U.S. dollar term loan facility and Euro-equivalent $1,800 million under a proposed Euro term loan facility. On February 17, 2022, Merger Subsidiary closed its offering of $2,020 million 7.375% senior notes due 2030. Under the terms of the Merger Agreement, the Company’s stockholders will receive $26.00 in cash for each share of Class A common stock they hold on the transaction closing date. The transaction’s closing is subject to customary closing conditions, including, among others, approval by the Company’s stockholders, the expiration or early termination of the applicable waiting period under the Hart-Scott-Rodino Antitrust Improvements Act of 1976, as amended (the “HSR Act”), the receipt of other regulatory approvals, and clearance by the Committee on Foreign Investment in the United States. On December 20, 2021 at 11:59 p.m., the waiting period under the HSR Act expired. On February 9, 2022, the Company’s stockholders approved the Merger at a special meeting of stockholders. On February 22, 2022, the Committee on Foreign Investment in the United States closed its review and cleared the transactions contemplated by the Merger Agreement. Pursuant to the terms of the Merger Agreement, the completion of the Merger remains subject to various customary conditions, including (1) the absence of an order, injunction or law prohibiting the Merger, (2) the receipt of antitrust approval in the European Union and Switzerland, (3) the accuracy of each party’s representations and warranties, subject to certain materiality standards set forth in the Merger Agreement, (4) compliance in all material respects with each party’s obligations under the Merger Agreement, and (5) no Company Material Adverse Effect (as defined in the Merger Agreement) having occurred since the date of the Merger Agreement.
For a summary of the transaction, please refer to our Form 8-K filed with the U.S. Securities and Exchange Commission (the “SEC”) on November 8, 2021.
OVERVIEW
McAfee has been a pioneer and leader in protecting consumers from cyberattacks with integrated security, privacy, identity and trust solutions. For over 30 years, consumers have turned to McAfee as a leader in cybersecurity services. We built our platform through a deep, rich history of innovation and have established a leading global brand. When securing the digital experience of a consumer who is increasingly living life online, McAfee is singularly committed to one mission: to protect our subscribers' digital presence through leading-edge cybersecurity.
4
We live in a digital world. Consumers are increasingly mobile, interacting through multiple devices, networks and platforms, while leveraging technology as they work, socialize, consume and transact. Remote and increasing work and study from home arrangements are driving a pronounced convergence of professional and personal life. This lifestyle shift has been accompanied by a more advanced cyberthreat landscape and a proliferation of points of vulnerability, risking individuals’ privacy, identity, personal data, sensitive information and other vital resources. This challenge has heightened the importance of securing the consumers’ converged digital life.
We have a differentiated ability to secure the consumers’ digital experience against cyberthreats, using our proprietary advanced artificial intelligence and machine learning capabilities combined with our real-time threat intelligence that leverages the scale and diversity of our threat sensor network. Our network of over 600 million customer devices generates massive amounts of telemetry that we translate into actionable, real-time insights. As of 2020, our vast and dynamic data set and advanced analytics capabilities enabled us to provide defense for advanced zero-day threats by training machine learning models on the over 60 billion threat queries. McAfee simplifies the complexity of threat detection and response by correlating events, detecting new threats, reducing false positives, and guiding consumers through remediation. Protecting our subscribers has been the foundation of our success, enabling us to maintain an industry-leading reputation among our subscribers and partners.
Our Personal Protection Service provides holistic digital protection for an individual or family at home, on the go, and on the web. Our platform includes device security, privacy and safe Wi-Fi, online protection, and identity protection, creating a seamless and integrated digital moat. With a single interface, simple set up and ease of use, consumers obtain immediate time-to-value whether on a computer, smartphone or tablet, and across multiple operating systems.
Our broad and digitally-led omni-channel go-to-market strategy reaches the consumer at crucial moments in their cybersecurity purchase lifecycle resulting in the protection of over 600 million devices. We acquire customers through our extensive direct channel (McAfee.com). This includes traffic driven through Search Engine Marketing (“SEM”), Affiliate, Social and organic traffic. We have longstanding exclusive partnerships with many of the leading PC original equipment manufacturers (“OEMs”). We also increasingly have partnerships as the consumer security provider to mobile and internet service providers (“ISPs”) as the demand for mobile security protection increases. Through many of these relationships, our consumer security software is pre-installed on devices on a trial basis until conversion to a paid subscription. Our go-to-market channel also includes some of the largest retailers globally. We operate a global business, with 39% of our fiscal 2021 net revenue earned outside of the United States.
SALE OF OUR ENTERPRISE BUSINESS
On July 27, 2021, we completed the sale of our Enterprise Business to STG, pursuant to a Contribution and Equity Purchase Agreement (the “Purchase Agreement”) entered in on March 6, 2021 between McAfee, LLC (“US Seller”) and McAfee Security UK LTD (“UK Seller” and together with US Seller, the “Seller Entities”) and Magenta Buyer LLC, organized by a consortium led by STG, in exchange for (i) $4,000,000,000 in cash consideration and (ii) the assumption of certain liabilities of the Enterprise Business as specified in the Purchase Agreement. We believe this transaction allows McAfee to singularly focus on our Consumer business and to accelerate our strategy to be a leader in personal security for consumers.
In connection with the closing of the sale, the Seller Entities and Buyer entered into a Transition Services Agreement, Transitional Trademark License Agreement, Intellectual Property Matters Agreement and Commercial Services Agreement, under which each party granted certain licenses to the other party with respect to certain intellectual property rights and technology transferred by us in the Enterprise Sale and retained by us after the consummation of the sale of our Enterprise Business. We also agreed not to compete with the Enterprise Business for four years following the closing of the transaction. In addition, we and Buyer agreed to indemnify each other for losses arising from certain covenant breaches under the Purchase Agreement and certain liabilities expressly assumed or retained by the relevant indemnifying party.
FINANCIAL SUMMARY
For the year ended December 25, 2021 compared to the year ended December 26, 2020 we delivered the following:
5
See “Non-GAAP Financial Measures” for a description of adjusted EBITDA, and adjusted EBITDA margin, and a reconciliation of these measures to the nearest financial measure calculated in accordance with generally accepted accounting principles (“GAAP”).
INDUSTRY BACKGROUND
We live in an increasingly digitally interconnected and mobile world that is driving profound changes for consumers, causing them to react to the following trends:
Adoption of online lifestyle is global and continues to grow. According to IDC, there were over 4 billion Internet users in 2020, of which the number of mobile-only Internet users is expected to grow at an approximate 8% compound annual growth rate (“CAGR”) from 2020 to 2024. Furthermore, Frost & Sullivan estimates there were over 6 billion Internet-connected devices worldwide in 2020. This significant growth in the mobile install base is driving the ubiquity of the Internet and online browsing.
Consumers everywhere are living more of their everyday lives online, thereby expanding their digital footprint. Consumers are more comfortable engaging in critical transactions, including financial transactions and medical consultations, on mobile devices and their PCs. At the same time, they are rapidly expanding their social interactions and media consumption online, while shifting data storage to cloud-based solutions to store personal photos and large amounts of private data that is accessible across any connected endpoint device. Per eMarketer, the average U.S. adult spent over 7.8 hours per day consuming digital media in 2020, representing 55% of total media consumption and an increase of 12% over the prior year. On average, one single users owns 300 online accounts, and each smartphone has 90 apps downloaded. The COVID-19 pandemic has accelerated digital transformation even further. According to Statista, eCommerce accounts for 20% of total retail sales in 2021, and digital transformation and mobile payments is expected to be $8.2 trillion in 2024. While unlocking consumers’ digital life allows for convenience, using an ever-increasing number of online applications and web services increases the attach surface area that cybercriminals can use to obtain, misuse, corrupt, destroy or otherwise exploit consumers’ data.
Increased attack surface combined with more organized cybercriminal heightens risk of being hacked and personal data used for profit. Cyberattacks have evolved from rudimentary malware into highly sophisticated and large-scale attacks. According to RiskBased Security, during 2020, nearly 4,000 data breaches were reported, resulting in over 37 billion records being exposed. Increasing ransomware attacks have generated billions of dollars in payments to cybercriminals and inflicted significant damage and expenses for consumers. In the fourth quarter of 2021, McAfee Labs observed an average of 354 threats per minute.
There is a need for integrated online protection solutions that secure consumers in a connected world by offering the following:
6
KEY BENEFITS OF OUR SOLUTIONS
We protect consumers with our differentiated ability to detect, analyze, and manage responses to adversarial threats. Our subscribers trust us to protect and defend their families, data, network and online experience whether it is on a device or in the cloud, at home or on the go.
Our products are multi-faceted privacy protection solutions that provide consumers security in their everyday lives. Our Personal Protection Service is designed to provide a comprehensive suite of features that protect consumers and their families across their digital life. Our products provide cross-device identity protection, online privacy, and device security against virus, malware, spyware and ransomware attacks that are pervasive across all digital devices. Personal Protection Service allows consumers to have mobile and PC antivirus protection across all of their devices, provides spam filtering capabilities, has the ability to securely encrypt sensitive files on public networks, and erases digital footprints that could be used to compromise their data, identity and privacy.
Our solutions provide a seamless and user friendly experience. From working on laptops, to accessing social media on phones, or accessing online videos, our Personal Protection Service provides unified multi-device protection for the modern connected family. With a single McAfee Total Protection subscription, our subscribers can protect multiple devices without impeding the consumer experience via cloud-based online and offline protection across devices to enjoy security at home and on the go. McAfee Total Protection comes with performance-enhancing features that allow for more productivity and entertainment by automatically assigning more dedicated processor power to the apps consumers are actively using. With a single interface, simple set up and intuitive user experience, consumers obtain immediate value from our solutions once installed. Our security, privacy and trust solutions provide a seamless and convenient experience, and an integrated digital moat. We are one of the few scaled cybersecurity companies with integrated data protection and threat defense capabilities built into technologies and solutions that span the digital ecosystem.
Our solutions have comprehensive features that provide consumers peace of mind that their online experience is protected. Our Personal Protection Service is designed to be a holistic digital protection of consumers and their families. Personal Protection Service encompasses data and device security and identity protection through our suite of products while delivering an experience that is equally easy to use whether on a PC, a mobile smartphone or a tablet and across multiple operating system platforms.
Our solutions are supported by our global real-time threat intelligence network, which is bolstered by artificial intelligence, machine learning, and deep learning to increase efficacy and efficiency. As of December 25, 2021, our portfolio leverages over 600 million telemetry sensors across multiple domains that feed our threat intelligence and insights engines. As of 2020, McAfee’s Global Threat Intelligence (“GTI”) supplies threat intelligence to over 2.3 trillion threat queries each year. By leveraging artificial intelligence, machine learning, and deep learning, we use complex threat detection and response algorithms that collect data from our vast customer base to correlate events, detect new threats, reduce false positives, and customers through remediation.
MARKET OPPORTUNITY
According to Frost & Sullivan, the global consumer endpoint security market (comprised of endpoint protection and prevention and consumer privacy and identity protection) addressed by our solutions was expected to reach nearly $13.1 billion in 2020, growing to $18.7 billion in 2024 (9% CAGR). The consumer endpoint security market has remained strong throughout the COVID-19 pandemic and did not show signs of waning during 2021. While the COVID-19 pandemic may have accelerated the market for consumer endpoint security solutions, we believe there continues to be a robust market for consumer personal protection, including mobile solution and broader consumer protection offerings as consumers continue to increase their digital footprint. We believe Consumer Digital Protection represents a large and underpenetrated market opportunity with less than five percent of current global internet users using paid cyber safety solutions, resulting in a greater than ninety five percent whitespace opportunity.
COMPETITIVE STRENGTHS
Our competitive strengths include:
7
OUR GROWTH STRATEGY
Our strategy is to maintain and extend our technology leadership in consumer cybersecurity solutions by driving frictionless and secure digital experiences as a privately-held company. The following are key elements of our growth strategy:
8
OUR PRODUCTS
We believe we have one of the industry's most comprehensive cybersecurity portfolios protecting consumers’ digital life.
Our Personal Protection Service provides holistic online protection of the individual and family across their entire digital life. It encompasses device security, privacy, and safe Wi-Fi, and identity protection through a trusted brand with an intuitive experience that is equally easy to use whether on a PC, a mobile smartphone or a tablet and across multiple operating system platforms. Our Personal Protection Service delivers a simple user interface with no performance trade-offs, and with a focus on proactive, intelligent, and seamless protection during a consumer’s digital experience. Our platform frees consumers to work on sensitive documents, videoconference their friends and coworkers, and have their kids go on social media platforms while having peace of mind that our Personal Protection Service is keeping their data and files encrypted, proactively alerting them when they are at risk, and helping them to resolve security threats. We achieve this by integrating the following solutions and capabilities within our Personal Protection Service:
We also provide these services to consumers who want to complement their existing protection in the form of individual products, as well as to consumers who want to protect their complete digital life through our Total Protection and LiveSafe portfolio brands.
In addition, we extended our protection services to small business owners and the gamer community. Our Small Business Security package helps small businesses keep their businesses and customer data safe by leveraging our award-winning multi-device protection and privacy capabilities, enhanced with our 24/7 technical support and virus removal service. Our Gamer Security package delivers anti-malware functionality while enhancing gaming performance. By offloading threat detection to the cloud, keeping necessary virus definitions locally, and optimizing system resources like the central processing unit, graphics processing unit, and random-access memory by pausing background services, we deliver a smoother and safer gaming experience.
OUR TECHOLOGY
We deploy the latest technologies to maintain our competitive advantage in our product offerings as well as to design a personalized digital experience for consumers that drive customer engagement, satisfaction, and retention.
9
Quality of Our Protection and Artificial Intelligence/Machine Learning
Our solutions seek to defend against a wide range of threats by using technology that leverages a combination of threat intelligence, artificial intelligence and machine learning. Unlike other alternatives that rely only on artificial intelligence, our approach minimizes false positives while detecting a wide range of threats, including new zero-day threats.
Our solutions are enhanced by our Global Threat Intelligence Telemetry from detected events across the product portfolio in addition to structural and behavioral feature vectors from telemetry collected through our network of threat sensors. This telemetry enables McAfee to understand the blueprint of threats for which we do not necessarily possess the sample but can identify based on behavioral and structural vectors which improves our efficacy in detecting zero-day threats.
Our Machine Learning Scanner provides two options for performing automated analysis—on the device or in the cloud. The former uses machine learning on customer systems to determine whether existing and incoming files match known malware. Our cloud-based machine learning scanner collects and sends file attributes and behavioral information to the machine-learning system in the cloud for malware analysis, without transmitting personally identifiable information.
Anti-Malware Engine
Our anti-malware engine is the core component of our award-winning products. Using patented technology, the engine analyzes potentially malicious code to detect and block Trojans, viruses, worms, adware, spyware, ransomware and other threats. The engine scans files at particular points, processes, and pattern-matches malware definitions with data it finds within scanned files, decrypts, and runs malware code in an emulated environment, applies heuristic techniques to recognize new malware, and removes infectious code from legitimate files.
Consumer Experience Innovation
We continuously improve the digital experience for consumers through the following technologies:
SALES AND MARKETING
Our go-to-market engine consists of a digitally-led omni-channel approach to reach the consumer at crucial moments in their purchase lifecycle including direct-to-consumer online sales, acquisition through trial pre-loads on PC OEM devices, and other indirect modes via additional partners such as mobile providers, ISPs, electronics retailers, eCommerce sites, and search providers.
10
Our omni-channel approach and strong partnerships work together to increase our presence at key moments of purchase and security engagement for consumers, allowing us to drive customer engagement and acquisition of new subscribers.
INTELLECTUAL PROPERTY
Our intellectual property is an important and vital asset of the company that enables us to develop, market, and sell our products and services and enhance our competitive position. We rely on trademarks, patents, copyrights, trade secrets, license agreements, intellectual property assignment agreements, confidentiality procedures, non-disclosure agreements, and employee non-disclosure and invention assignment agreements to establish and protect our proprietary rights.
We maintain an internal patent program to identify inventions that provide the basis for new patent applications in areas of importance to our business. As of December 25, 2021, we had approximately 1,235 issued U.S. patents, in addition to approximately 735 issued foreign patents, which generally relate to inventive aspects of our products and technology. The duration of our issued patents is determined by the laws of the issuing country. Although we have patent applications pending, there can be no assurance that patents will issue from pending applications or that claims allowed on any future issued patents will be sufficiently broad to protect our technology. Also, these protections may not preclude competitors from independently developing products with functionality or features similar to our products.
In certain cases, we license intellectual property from third parties for use in our products and generally must rely on those third parties to protect the licensed rights. This can include open source software, which is subject to limited proprietary rights. While the ability to maintain and protect our intellectual property rights is important to our success, we believe our business is not materially dependent on any individual patent, copyright, trademark, trade secret, license, or other intellectual property right. For information on the risks associated with our intellectual property, please see “Risk Factors” in Item 1A.
THIRD-PARTY SERVICE PROVIDERS
We are heavily reliant on our technology and infrastructure to provide our products and services to our customers. For example, we host many of our products using third-party data center facilities, and we do not control the operation of these facilities. In addition, we rely on certain technology that we license from third parties, including third-party commercial software and open source software, which is used with certain of our solutions. For information on the risks associated with our dependence on such third-party service providers, please see “Risk Factors” in Item 1A.
11
GOVERNMENTAL REGULATION
We collect, use, store or disclose an increasingly high volume, variety, and velocity of personal information, including from employees and customers, in connection with the operation of our business, particularly, in relation to our identity and information protection offerings, which rely on large data repositories of personal information and consumer transactions. The personal information we process is subject to an increasing number of federal, state, local, and foreign laws regarding privacy and data security. For information on the risks associated with complying with privacy and data security laws, please see “Risk Factors” in Item 1A.
EMPLOYEE & HUMAN CAPITAL
Protecting all that matters demands constant innovation. Doing our job well requires building a workplace that embraces individuality, encourages different perspectives, and welcomes a range of experiences to boost real innovation, creativity, and strategic problem-solving. But it’s not just the right thing to do for business—it’s about every person’s innate right to be their true self and belong.
Building a more inclusive, sustainable world starts within our walls. We believe that when we mirror the varying perspectives of the outside world, we are stronger, more innovative, and better positioned to solve tomorrow’s toughest cybersecurity challenges. Our approach starts with our hiring and interview practices, but representation isn’t enough. Once people walk through our open door, we ensure all life experiences are not just valued, but accepted and encouraged. Only when people feel a deep sense of belonging can they thrive.
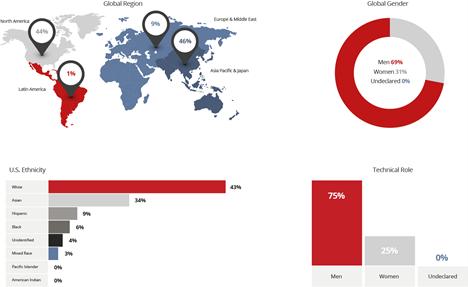
To solve tomorrow’s cybersecurity challenges, we know that our industry needs a more diverse, innovative workforce. To fulfill our mission to protect all that matters, we stand firm in our commitment to drive this change. But first, we must understand who we are today to define our journey ahead. As of December 25, 2021, McAfee employed 2,262 employees in 32 countries worldwide. Of these employees, 434 are expected to transfer to McAfee Enterprise in 2022 as a result of the divestiture which occurred in July 2021. The core McAfee population demographic was as follows:

To contribute a more diverse workforce to the cybersecurity industry, we know that we will need to exercise genuine, authentic, and transparent recruiting and hiring practices aligned with our values. That’s why we support techniques and programs designed specifically to connect us with people of all backgrounds:
12
Real collaboration, innovation, and impact happens in workplaces where you can express yourself authentically. That’s why we work hard to ensure life at McAfee is one where our employees can be authentic, engage with others, and reach the best versions of themselves, both at the office and away from it:
A more detailed overview of McAfee’s inclusion and diversity practices can be viewed at https://www.mcafee.com/en-us/consumer-corporate/inclusion-diversity.html.
AVAILABLE INFORMATION
Our internet website is www.mcafee.com. We make available on the Investor Relations section of our website, free of charge, our annual reports on Form 10-K, quarterly reports on Form 10-Q, current reports on Form 8-K, Proxy Statements, and Forms 3, 4 and 5, and amendments to those reports as soon as reasonably practicable after filing such documents with, or furnishing such documents to, the Securities and Exchange Commission (“SEC”). The SEC maintains a website (www.sec.gov) that contains reports, proxy and information statements and other information regarding issuers that file electronically with the SEC.
On the Investor Relations section of our website, we webcast our earnings calls and certain events we participate in or host with members of the investment community. Additionally, we provide notifications of news or announcements regarding our financial performance, including SEC filings, investor events, press and earnings releases. Further corporate governance information, including our board committee charters, and, code of ethics, is also available on our Investor Relations website under the heading "Corporate Governance—Documents & Charters."
Our internet website is included herein as an inactive textual reference only. The information contained on our website is not incorporated by reference herein and should not be considered part of this report.
13
Item 1A. Risk Factors
Risks Related to the Merger
The announcement and pendency of the proposed Merger may adversely affect our business, financial condition and results of operations.
On November 5, 2021, the Company entered into an Agreement and Plan of Merger (the “Merger Agreement”) with Condor BidCo, Inc., a Delaware corporation (“Parent”), and Condor Merger Sub, Inc., a Delaware corporation and wholly owned subsidiary of Parent (“Merger Subsidiary”), pursuant to which Merger Subsidiary will merge with and into the Company whereupon the separate corporate existence of Merger Subsidiary will cease and the Company will be the surviving corporation in the Merger and will continue as a wholly owned subsidiary of Parent (the “Merger”). Uncertainty about the effect of the proposed Merger on our employees, customers, and other parties may have an adverse effect on our business, financial condition and results of operation regardless of whether the proposed Merger is completed. These risks to our business include the following, all of which could be exacerbated by a delay in the completion of the proposed Merger:
Additionally, in approving the Merger Agreement, our board of directors considered a number of factors and potential benefits, including the fact that the Merger consideration to be received by holders of our common stock represented an approximately 22.6% premium to our unaffected share price of $21.21 on November 4, 2021, the day prior to initial media speculation of a transaction. If the Merger is not completed, neither the Company nor the holders of our common stock will realize this benefit of the Merger. Moreover, we would have incurred substantial transaction-related fees and costs and the loss of management time and resources
Failure to consummate the proposed Merger within the expected timeframe or at all could have a material adverse impact on our business, financial condition and results of operations.
There can be no assurance that the proposed Merger will be consummated. The consummation of the proposed Merger is subject to customary closing conditions. The obligation of each party to consummate the Merger is also conditioned upon the other party’s representations and warranties being true and correct to the extent specified in the Merger Agreement and the other party having performed in all material respects its obligations under the Merger Agreement. There can be no assurance that these and other conditions to closing will be satisfied in a timely manner or at all.
The Merger Agreement also includes customary termination provision for both the Company and Parent, subject, in certain circumstances, to the payment by the Company of a termination fee of 1.25% or 2.5% of the Company’s equity value. If we are required to make this payment, doing so may materially adversely affect our business, financial condition and results of operations.
14
There can be no assurance that a remedy will be available to us in the event of a breach of the Merger Agreement by Parent or its affiliates or that we will wholly or partially recover for any damages incurred by us in connection with the proposed Merger. A failed transaction may result in negative publicity and a negative impression of us among our customers or in the investment community or business community generally. Further, any disruptions to our business resulting from the announcement and pendency of the proposed Merger, including any adverse changes in our relationships with our customers, partners, suppliers and employees, could continue or accelerate in the event of a failed transaction. In addition, if the proposed Merger is not completed, and there are no other parties willing and able to acquire the Company at a price of $26.00 per share or higher, on terms acceptable to us, the share price of our Class A common stock will likely decline to the extent that the current market price of our common stock reflects an assumption that the proposed Merger will be completed. Also, we have incurred, and will continue to incur, significant costs, expenses and fees for professional services and other transaction costs in connection with the proposed Merger, for which we will have received little or no benefit if the proposed Merger is not completed. Many of these fees and costs will be payable by us even if the proposed Merger is not completed and may relate to activities that we would not have undertaken other than to complete the proposed Merger.
Prior to the completion of the Merger or the termination of the Merger Agreement in accordance with its terms, we are prohibited from entering into certain transactions and taking certain actions that might otherwise be beneficial to us and our stockholders.
After the date of the Merger Agreement and prior to the effective time, the Merger Agreement restricts us from taking specified actions without the consent of the Parent (which consent may not be unreasonably withheld, conditioned or delayed) and requires that our business be conducted in all material respects in the ordinary course of business. These restrictions may prevent us from making appropriate changes to our businesses or organizational structures or from pursuing attractive business opportunities that may arise prior to the completion of the Merger and could have the effect of delaying or preventing other strategic transactions. Adverse effects arising from the pendency of the Merger could be exacerbated by any delays in consummation of the Merger or termination of the Merger Agreement.
The Merger, including uncertainty regarding the Merger, may cause customers, suppliers, distributors or strategic partners to delay or defer decisions, which could negatively affect our business and adversely affect our ability to effectively manage our business.
The Merger will happen only if certain conditions are met. Many of the conditions are outside our control, and both we and Parent also have the right to terminate the Merger Agreement in certain circumstances. Accordingly, there may be uncertainty regarding the completion of the Merger. This uncertainty may cause customers, suppliers, distributors, strategic partners or others that deal with us to delay or defer entering into contracts with us or making other decisions concerning us or seek to change or cancel existing business relationships, which could negatively affect our business. Any delay or deferral of those decisions or changes in existing agreements could have a material adverse effect on our business, regardless of whether the Merger is ultimately completed.
The Merger may cause difficulty in attracting, motivating and retaining employees.
Our current and prospective employees may experience uncertainty about their future role with the Company until strategies with regard to these employees are announced or executed, which may impair our ability to attract, retain and motivate key management, technical, business development, operational and customer-facing employees and other personnel prior to the Merger. If we are unable to retain and replace personnel, we could face disruptions in our operations, loss of existing customers, loss of key information, expertise or know-how, and unanticipated additional recruitment and training costs.
The Merger Agreement limits our ability to pursue alternatives to the Merger and may discourage other companies from trying to acquire us for greater consideration than what the Parent has agreed to pay.
The Merger Agreement contains provisions that make it more difficult for us to sell our business to a company other than the Parent. These provisions include a general prohibition on us soliciting any acquisition proposal or offer for a competing transaction. If we or the Parent terminate the Merger Agreement and we agree to be or are subsequently acquired by another company, we may in some circumstances be required to pay to Parent a termination fee of 1.25% or 2.5% of the Company’s equity value.
15
These provisions might discourage a third party that has an interest in acquiring all or a significant part of the Company from considering or proposing an acquisition, even if the party were prepared to pay consideration with a higher per share cash or market value than the cash value proposed to be received in the Merger, or might result in a potential competing acquirer proposing to pay a lower price than it might otherwise have proposed to pay because of the added expense of the termination fee that may become payable in certain circumstances.
Stockholder litigation could result in substantial costs and may delay or prevent the Merger from being completed.
Stockholder lawsuits are often brought against public companies that have entered into merger agreements. As of the date of this Annual Report on Form 10-K, the Company has received three demand letters on behalf of purported stockholders of the Company challenging certain disclosures in the definitive proxy statement filed with the SEC on January 4, 2022 (the “Definitive Proxy Statement”). In addition, five stockholder complains relating to the Merger have been filed, four of which allege that the Definitive Proxy Statement is false and/or misleading and asserts claims for violations of Sections 14(a) and 20(a) of the Exchange Act and SEC Rule 14a-9 against the Company and its directors and the fifth alleges that the preliminary proxy statement filed with the SEC on December 21, 2021 is false and/or misleading and asserts claims for violations of Section 14(a) and 20(a) of the Exchange Act and SEC Rule 14a-9 against the Company and its directors. Each of the complains purport to seek, among other things, injunctive relief preventing the Merger, damages, and an award of plaintiffs’ costs and expenses, including reasonable attorneys’ and expert fees. The Company believes that the claims asserted in the demand letters and complaints are without merit. However, defending against these claims can result in substantial costs and divert management time and resources. Such claims could prevent or delay the consummation of the Merger, including through an injunction, and result in additional costs to us. The ultimate resolution of these lawsuits cannot be predicted, and an adverse ruling in any such lawsuit may cause the Merger to be delayed or not to be completed, which could cause us not to realize some or all of the anticipated benefits of the Merger.
Risks Related to the COVID-19 Pandemic
The COVID-19 pandemic has affected how we are operating our business, and the duration and extent to which this will impact our future results of operations and overall financial performance remains uncertain.
The COVID-19 pandemic is having widespread, rapidly evolving, and unpredictable impacts on global society, economies, financial markets, and business practices. Federal, state and foreign governments have implemented measures to contain the virus, including social distancing, travel restrictions, border closures, limitations on public gatherings, work from home, and closure of non-essential businesses. At the onset of the COVID-19 pandemic, we implemented work-from-home requirements, made substantial modifications to employee travel policies, and cancelled or shifted marketing and other corporate events to virtual-only formats. While we have adjusted our current policies and procedures in accordance with public health guidance that is available, we cannot be certain that similar precautionary measures will not be necessary in the future, and any such precautionary measures could negatively affect our customer success efforts, sales and marketing efforts, delay and lengthen our sales cycles, or create operational or other challenges, any of which could harm our business and results of operations. In addition, the COVID-19 pandemic has disrupted the operations of many of our channel partners, and may continue to disrupt their operations, for an indefinite period of time, including as a result of any future public health precautionary measures, uncertainty in the financial markets, or other harm to their businesses and financial results, resulting in delayed purchasing decisions, extended payment terms, and postponed or cancelled projects, all of which could negatively impact our business and results of operations, including our revenue and cash flows. Further, if the COVID-19 pandemic has a substantial impact on our employees’, partners’, or third-party service providers’ health, attendance, or productivity in the future, our results of operations and overall financial performance may be adversely impacted.
16
The ultimate duration and extent of the impact from the COVID-19 pandemic depends on future developments that cannot be accurately forecasted at this time, such as the efficacy of new vaccines, the efficiency and scope of global inoculation efforts, the severity and transmission rate of the disease and new variants, the actions of governments, businesses and individuals in response to the pandemic, the extent and effectiveness of containment actions, the impact on economic activity, and the impact of these and other factors on our employees, partners, and third-party service providers. This uncertainty also affects management’s accounting estimates and assumptions, which could result in greater variability in a variety of areas that depend on these estimates and assumptions, including those related to investments, receivables, retention rates, renewal and pricing. For example, we have experienced growth and increased demand for our solutions in recent quarters, which may be due in part to greater demand for devices or our solutions in response to the COVID-19 pandemic. We cannot determine what, if any, portion of our growth in net revenue, the number of our Direct to Consumer Subscribers, or any other measures of our performance during 2021 was the result of such responses to the COVID-19 pandemic. However, if we are unable to successfully drive renewals of new subscriptions and retention of new customers in future periods, including any such new subscriptions or new customers that may be related to the response to the COVID-19 pandemic, or if global conditions and macroeconomic forces, including those related to the COVID-19 pandemic, reduce demand for solutions in the future, we may be unsuccessful in sustaining our recent growth rates. In addition, the extent to which the COVID-19 pandemic will continue to drive demand for devices is uncertain, and if demand for devices decreases, we may experience slower growth in future periods. These uncertainties may increase variability in our future results of operations and adversely impact our ability to accurately forecast changes in our business performance and financial condition in future periods. If we are not able to respond to and manage the impact of such events effectively or if global economic conditions do not improve, or deteriorate further, our business, financial condition, results of operations, and cash flows could be adversely affected.
Risks Related to the Recent Sale of our Enterprise Business
If we are unsuccessful at executing our business plan and necessary transition activities as a standalone consumer cybersecurity company following the recent sale of our Enterprise Business, our business and results of operations may be adversely affected and our ability to invest in and grow our business could be limited.
On July 27, 2021, we completed the sale of our Enterprise Business to STG, which divestiture comprised a substantially whole operating segment. This and other operational transitions have involved turnover in management and other key personnel and changes in our strategic direction. Transitions of this type can be disruptive, result in the loss of focus and employee morale and make the execution of business strategies more difficult. We also expect to pay approximately $300 million in additional one-time separation costs and stranded cost optimization, a portion of which will be expenses paid by proceeds from the transaction. We have also entered into a transition service agreement under which we will provide assistance to STG including, but not limited to, business support services and information technology services as well as a commercial services agreement, under which we will provide certain product services and licensed technology, including certain threat intelligence data, that has historically been provided to the Enterprise Business. We may experience delays in the anticipated timing of activities related to such transitions and higher than expected or unanticipated execution costs. If we do not succeed in executing on these transition activities while achieving our cost optimization goals, or if these efforts are more costly or time-consuming than expected, our business and results of operations may be adversely affected, which could limit our ability to invest in and grow our business.
We may not achieve the intended benefits of the sale of our Enterprise Business.
We may not realize some or all of the anticipated benefits from the sale of our Enterprise Business. The resource constraints as a result of our focus on completing the transaction, which include the loss of employees, could have a continuing impact on the execution of our business strategy and our overall operating results. Further, our remaining employees may become concerned about the future of our remaining operations and lose focus or seek other employment. There can be no guarantee that the divestiture will result in stronger long term financial and operational results for our remaining consumer business.
Additionally, in connection with the divestiture, our Board of Directors returned a portion of the proceeds of the sale of our Enterprise Business in the form of distributions paid to holders of LLC Units of FTW, including McAfee Corp., and to holders of our Class A common stock in the form of a special dividend of $4.50 per share to holders of record of our Class A common stock as of August 13, 2021. The use of proceeds in this manner could impair our future financial growth.
17
Our future results of operations are dependent solely on the operations of our pure play consumer cyber security business and will differ materially from our previous results.
The Enterprise Business generated approximately 46% of total combined company revenue for fiscal 2020, and approximately 51% of total combined company revenue for fiscal 2019. Accordingly, our future financial results will differ materially from our previous results since our future financial results are dependent solely on our consumer operations. Any downturn in our consumer business could have a material adverse effect on our future operating results and financial condition and could materially and adversely affect the trading price of our outstanding securities.
Risks Related to Competition and Industry Trends
The cybersecurity market is rapidly evolving and becoming increasingly competitive in response to continually evolving cybersecurity threats from a variety of increasingly sophisticated cyberattackers. If we fail to anticipate changing customer requirements or industry and market developments, or we fail to adapt our business model to keep pace with evolving market trends, our financial performance will suffer.
The cybersecurity market is characterized by continual changes in customer preferences and requirements, frequent and rapid technological developments and continually evolving market trends. We must continually address the challenges of dynamic, and accelerating market trends, such as the emergence of new cybersecurity threats, the continued decline in the sale of new personal computers, and the rise of mobility and cloud-based solutions, all of which make satisfying our customers’ diverse and evolving needs more challenging.
The technology underlying our solutions is particularly complex because it must effectively and efficiently identify and respond to new and increasingly sophisticated threats while meeting other stringent technical requirements in areas of performance, usability, and availability. Although our customers expect new solutions and enhancements to be rapidly introduced to respond to new cybersecurity threats, product development requires significant investment, the efficacy of new technologies is inherently uncertain, and the timing for commercial release and availability of new solutions and enhancements is uncertain. We may be unable to develop new technologies to keep pace with evolving threats or experience unanticipated delays in the availability of new solutions, and therefore fail to meet customer expectations. If we fail to anticipate or address the evolving and rigorous needs of our customers, or we do not respond quickly to shifting customer expectations or demands by developing and releasing new solutions or enhancements that can respond effectively and efficiently to new cybersecurity threats on an ongoing and timely basis, our competitive position, business, and financial results will be harmed.
The introduction of new products or services by competitors, market acceptance of products or services based on emerging or alternative technologies, and the evolution of new standards, whether formalized or otherwise, could each render our existing solutions obsolete or make it easier for other products or services to compete with our solutions. In addition, modern cyberattackers are skilled at adapting to new technologies and developing new methods of breaching customers. We must continuously work to ensure our solutions protect against the increased volume and complexity of the cybersecurity threat landscape. Changes in the nature of advanced cybersecurity threats could result in a shift in cybersecurity spending and preferences away from solutions such as ours. If our solutions are not viewed by our customers as necessary or effective in addressing their cybersecurity needs, then our revenues may not grow as quickly as expected, or may decline, and our business could suffer.
We cannot be sure that we will accurately predict how the cybersecurity markets in which we compete or intend to compete will evolve. Failure on our part to anticipate changes in our markets and to develop solutions and enhancements that meet the demands of those markets will significantly impair our business, financial condition, results of operations, and cash flows.
We operate in a highly competitive environment, and we expect competitive pressures to increase in the future, which could cause us to lose market share.
The markets for our solutions are highly competitive, and we expect both the requirements and pricing competition to increase, particularly given the increasingly sophisticated attacks, changing customer preferences and requirements, current economic pressures, and market consolidation. Competitive pressures in these markets may result in price reductions, reduced margins, loss of market share and inability to gain market share, and a decline in sales, any one of which could seriously impact our business, financial condition, results of operations, and cash flows.
We face competition from players, such as NortonLifelock, Avast/AVG, Kaspersky, Trend Micro, ESET, and Microsoft, which expanded from desktop anti-malware into mobile, security, VPN, and identity protection among others. At the same time we compete with point-tool providers, such as Cujo and Dojo in the home IoT space or AnchorFree, ExpressVPN, and ProtonVPN in the network security space, across our full consumer offering.
18
In addition to competing with these and other vendors directly for sales to end-users of our products, we compete with several of them for the opportunity to have our products bundled with the product offerings of our strategic partners, including computer hardware OEMs, ISPs, mobile carriers, and other distribution partners. Our competitors could gain market segment share from us if any of these strategic partners replace our solutions with those of our competitors or if these partners more actively promote our competitors’ offerings than ours. In addition, vendors who have bundled our products with theirs may choose to bundle their products with their own or other vendors’ software or may limit our access to standard product interfaces and inhibit our ability to develop products for their platform. We also face competition from many smaller companies that specialize in particular segments of the markets in which we compete, including Crowdstrike, VMware, Netskope, and Zscaler. In the future, further product development by these providers could cause our products and services to become redundant or lose market segment share, which could significantly impact our sales and financial results.
We face growing competition from network equipment, computer hardware manufacturers, large operating system providers, telecommunication companies, and other large or diversified technology companies. Examples of large, diversified competitors include Microsoft, International Business Machines Corporation, and Dell Technologies. Large vendors of hardware or operating system software increasingly incorporate cybersecurity functionality into their products and services, and enhance that functionality either through internal development or through strategic alliances or acquisitions. Similarly, telecommunications providers are increasingly investing in the enhancement of the cybersecurity functionality in the devices and services they offer. Certain of our current and potential competitors may have competitive advantages such as longer operating histories, more extensive international operations, larger product development and strategic acquisition budgets, and greater financial, technical, sales, and marketing resources than we do. Such competitors also may have well-established relationships with our current and potential customers and extensive knowledge of our industry and the markets in which we compete and intend to compete. As a result, such competitors may be able to respond more quickly to new or emerging technologies and changes in customer requirements, or to devote greater resources to the development, marketing, sale, and support of their products. These competitors have made strategic acquisitions or established cooperative relationships among themselves or with other providers, thereby increasing their ability to provide a broader suite of products, and potentially causing customers to decrease purchases of, or defer purchasing decisions with respect to, our products and services. Additionally, some or all of our solutions may rely upon access to certain hardware or software interfaces. These competitors may limit our access to such interfaces or may provide greater or earlier access available to others. These actions could adversely affect the operations of our products relative to competitors or render our solutions inoperative.
Cybersecurity protection is also offered by certain of our competitors at prices lower than our prices or, in some cases, free of charge. Other companies bundle their own or our competitors’ lower-priced or free cybersecurity products with their own computer hardware or software product offerings in a manner that discourages users from purchasing our products and subscriptions. Our competitive position could be adversely affected to the extent that our current or potential customers perceive these cybersecurity products as replacing the need for our products or if they render our solutions unmarketable—even if these competitive products are inferior to or more limited than our products and services. The expansion of these competitive trends could have a significant negative impact on our sales and financial results by causing, among other things, price reductions of our products, reduced profitability, and loss of market share.
To compete successfully, we must continue to develop new solutions and enhance existing solutions, effectively adapt to changes in the technology or rights held by our competitors, respond to competitive strategies, and effectively adapt to technological changes within the consumer cybersecurity market. If we are unsuccessful in responding to our competitors, our competitive position and our financial results could be adversely affected.
Our business depends substantially on our ability to retain customers and to expand sales of our solutions to them. If we are unable to retain our customers or to expand our product offerings, our future results of operations will be harmed.
For us to maintain or improve our results of operations in a market that is rapidly evolving and places a premium on market-leading solutions, it is important that we retain existing customers and that our customers expand their use of our solutions. Our customers have no obligation to renew their subscription with us upon their expiration. Retention rates may decline or fluctuate as a result of a number of factors, including but not limited to the level of our customers’ satisfaction or dissatisfaction with our solutions, our prices and the prices of competing products or services, industry consolidation, the effects of global economic conditions, new technologies, changes in our customers’ spending levels, and changes in how our customers perceive the cybersecurity threats. In addition, a significant portion of our renewals come from autorenewal arrangements incorporated within our solutions. Any changes in the laws regarding autorenewal arrangements could adversely affect our ability to retain consumer customers and harm our financial condition and operating performance.
19
In addition, our ability to generate revenue and maintain or improve our results of operations partly depends on our ability to cross-sell our solutions to our existing customers. We expect our ability to successfully cross-sell our solutions will be one of the most significant factors influencing our growth. We may not be successful in cross-selling our solutions because our customers may find our additional solutions unnecessary or unattractive. Our failure to sell additional solutions to our existing and new customers could adversely affect our ability to grow our business.
We may need to change our pricing models to compete successfully.
The intense competition we face in the cybersecurity market, in addition to general economic and business conditions (including the economic volatility resulting from the COVID-19 pandemic), can result in downward pressure on the prices of our solutions. If our competitors offer significant discounts on competing products or services, or develop products or services that our customers believe are more valuable or cost-effective, we may be required to decrease our prices or offer other incentives in order to compete successfully. Additionally, if we increase prices for our solutions, demand for our solutions could decline as customers adopt less expensive competing products and our market share could suffer. If we do not adapt our pricing models to reflect changes in customer use of our products or changes in customer demand, our revenues could decrease.
Any broad-based change to our pricing strategy could cause our revenues to decline or could delay future sales as our sales force implements and our customers adjust to the new pricing terms. We or our competitors may bundle products for promotional purposes or as a long-term go-to-market or pricing strategy or provide price guarantees to certain customers as part of our overall sales strategy. These practices could, over time, significantly limit our flexibility to change prices for existing solutions and to establish prices for new or enhanced products and services. Any such changes could reduce our margins and adversely affect our results of operations.
If cybersecurity industry analysts publish unfavorable or inaccurate research reports about our business, our financial performance could be harmed.
An increasing number of independent industry analysts and researchers regularly evaluate, compare, and publish reviews regarding the performance, efficiency, and functionality of cybersecurity products and services, including our own solutions. The market’s perception of our solutions may be significantly influenced by these reviews. We do not have any control over the content of these independent industry analysts and research reports, or the methodology they use to evaluate our solutions, which may be flawed or incomplete. Demand for our solutions could be harmed if these industry analysts publish negative reviews of our solutions or do not view us as a market leader. If we are unable to maintain a strong reputation, sales to new and existing customers and renewals could be adversely affected, and our financial performance could be harmed.
Risks Related to Our Financial and Operating Performance
Our results of operations can be difficult to predict and may fluctuate significantly, which could result in a failure to meet investor expectations.
Our results of operations have in the past varied, and may in the future vary, significantly from period to period due to a number of factors, many of which are outside of our control, including the macroeconomic environment. These factors limit our ability to accurately predict our results of operations and include factors discussed throughout this “Risk Factors” section, including the following:
20
Furthermore, a high percentage of our expenses, including those related to overhead, research and development, sales and marketing, and general and administrative functions are generally fixed in nature in the short term. As a result, if our net revenue is less than forecasted, we may not be able to effectively reduce such expenses to compensate for the revenue shortfall and our results of operations will be adversely affected. We also expect the recent sale of our Enterprise Business to lead to increased costs that were previously allocated to both segments to now be part of continuing operations, which will have a dilutive impact on operating margins. We also expect to pay approximately $300 million in additional one-time separation costs and stranded cost optimization, a portion of which will be expenses paid by proceeds from the transaction. In addition, our ability to maintain or expand our operating margins may be limited given economic and competitive conditions, and we therefore could be reliant upon our ability to continually identify and implement operational improvements in order to maintain or reduce expense levels. There can be no assurance that we will be able to maintain or expand our current operating margins in the future.
We derive revenue from the sale of security products and subscriptions or a combination of these items, which may decline.
Our sales may decline and fluctuate as a result of a number of factors, including our customers’ level of satisfaction with our products and services, the prices of our products and services, the prices of products and services offered by our competitors, reductions in our customers’ spending levels, and other factors beyond our control. We also derive part of our revenue through indirect agreements with third parties including mobile providers, ISPs, electronics retailers, ecommerce sites, and search providers. Any change in these agreements, in indirect party’s demand with end consumers in mobile, ISP, and retail, in user search behavior, advertising market for search or ecosystem changes could adversely affect our revenue. If our sales decline, our revenue and revenue growth may decline, and our business will suffer. We recognize a majority of revenue as control of the goods and services is transferred to our customer. As a result, a majority of revenue we report each quarter is the recognition of deferred revenue from subscriptions entered into during previous quarters. Consequently, a decline in sales in any single quarter will not be fully or immediately reflected in revenue in that quarter but will continue to negatively affect our revenue in future quarters. Accordingly, the effect of significant downturns in sales is not reflected in full in our results of operations until future periods. Furthermore, it is difficult for us to rapidly increase our revenue through additional sales in any period, as revenue from subscriptions must be recognized over the applicable future time period. Finally, any increase in the average term of a subscription would result in revenue for such subscriptions being recognized over longer periods of time.
The sudden and significant economic downturn or volatility in the economy in the United States and our other major markets could have a material adverse impact on our business, financial condition, results of operations, or cash flows.
We operate globally and as a result our business and revenues are impacted by global macroeconomic conditions. In recent periods, investor and customer concerns about the global economic outlook, which significantly increased in 2020 and early 2021 due to the COVID-19 pandemic, have adversely affected market and business conditions in general. In addition, a weakening of economic conditions, including from a worsening of the ongoing labor shortage or rise in inflation, could lead to reductions in demand for our solutions. Weakened economic conditions or a recession could reduce the amounts that customers are willing or able to spend on our products and solutions, and could make it more difficult for us to compete against less expensive and free products for new customers. Furthermore, a high percentage of our expenses, including those related to overhead, research and development, sales and marketing, and general and administrative functions are generally fixed in nature in the short term. If we are not able to timely and appropriately adapt to changes resulting from a weak economic environment, it could have an adverse impact on our business, financial condition, results of operations, and cash flows.
We have experienced net losses in recent periods and may not maintain profitability in the future.
We experienced net losses of $236 million and $289 million for fiscal 2019 and 2020, respectively. While we have experienced revenue growth over these same periods, we may not be able to sustain or increase our growth or maintain profitability in the future or on a consistent basis. In recent years, we have changed our portfolio of products and invested in research and development to develop new products and enhance current solutions.
21
We also expect to continue to invest for future growth. We expect that to achieve profitability we will be required to increase revenues, manage our cost structure, and avoid significant liabilities. Revenue growth may slow, revenue may decline, or we may incur significant losses in the future for a number of possible reasons, increasing competition, a decrease in the growth of the markets in which we operate, or if we fail for any reason to continue to capitalize on growth opportunities. We also expect the recent sale of our enterprise business to lead to increased costs that were previously allocated to both segments to now be part of continuing operations, which will have a dilutive impact on operating margins. Additionally, we may encounter unforeseen operating expenses, difficulties, complications, delays, and other unknown factors that may result in losses in future periods. If these losses exceed our expectations or our revenue growth expectations are not met in future periods, our financial performance may be harmed.
Changes in tax laws or in their implementation may adversely affect our business and financial condition.
Changes in tax law may adversely affect our business or financial condition. As part of Congress’s response to the COVID-19 pandemic, the Families First Coronavirus Response Act, commonly referred to as the FFCR Act, was enacted on March 18, 2020, the Coronavirus Aid, Relief, and Economic Security Act, commonly referred to as the CARES Act, was enacted on March 27, 2020, the act commonly known as the Consolidated Appropriations Act, 2021 was enacted on December 27, 2020, and the act commonly known as the American Rescue Plan Act was enacted on March 11, 2021. Each contains numerous tax provisions. In particular, the CARES Act retroactively and temporarily (for taxable years beginning before January 1, 2021) suspended application of the 80%-of-taxable-income limitation on the use of NOLs, which was enacted as part of the TCJA. It also provided that NOLs arising in any taxable year beginning after December 31, 2017 and before January 1, 2021 are generally eligible to be carried back up to five years. The CARES Act also temporarily (for taxable years beginning in 2019 or 2020) relaxed the limitation of the tax deductibility for net interest expense by increasing the limitation from 30% to 50% of adjusted taxable income.
Regulatory guidance under the Tax Cuts and Job Act (“TCJA”), the FFCR Act, the CARES Act, the Consolidated Appropriations Act, 2021, and the American Rescue Plan Act is and continues to be forthcoming, and such guidance could ultimately increase or lessen impact of these laws on our business and financial condition. It is also likely that Congress will enact additional legislation in connection with the COVID-19 pandemic, some of which could have an impact on our Company. In addition, it is uncertain if and to what extent various states will conform to the TCJA, the FFCR Act, the CARES Act, the Consolidated Appropriations Act, 2021, or the American Rescue Plan Act. The Biden Administration has also proposed a significant number of changes to U.S. tax laws, including an increase in the maximum tax rate applicable to U.S. corporations and certain individuals, which could potentially have retroactive effect and may significantly affect McAfee Corp. or FTW. Any such rate increases or future changes to U.S. tax laws could also require McAfee Corp. to increase its payments to the Continuing Owners and Management Owners pursuant to its tax receivable agreement.
As a multinational corporation, forecasting our estimated annual effective tax rate is complex and subject to uncertainty, and there may be material differences between our forecasted and actual tax rates.
Forecasts of our income tax position and effective tax rate are complex and subject to uncertainty because our income tax position for each year combines the effects of a mix of profits and losses earned by us and our subsidiaries in various tax jurisdictions with a broad range of income tax rates, as well as changes in the valuation of deferred tax assets and liabilities, the impact of various accounting rules and changes to these rules and tax laws, such as the U.S. federal income tax laws, including impacts of the TCJA, FFCR Act, CARES Act, Consolidated Appropriations Act, 2021, and American Rescue Plan Act arising from future interpretations of such legislation, the results of examinations by various tax authorities and the impact of any acquisition, business combination, or other reorganization or financing transaction. To forecast our global tax rate, we estimate our pre-tax profits and losses by jurisdiction and forecast our tax expense by jurisdiction. If our mix of profits and losses, our ability to use tax credits, or effective tax rates by jurisdiction is different than those estimated, our actual tax rate could be different than forecasted, which could have a material impact on our financial condition and results of operations.
As a multinational corporation, we conduct our business in many countries and are subject to taxation in many jurisdictions. The taxation of our business is subject to the application of multiple and conflicting tax laws and regulations as well as multinational tax conventions. Our effective tax rate is highly dependent upon the geographic distribution of our worldwide earnings or losses, the tax regulations in each geographic region, the availability of tax credits and carryforwards, changes in accounting principles (including accounting for uncertain tax positions), and changes in the valuation of our deferred tax assets, and the effectiveness of our tax planning strategies. The application of tax laws and regulations is subject to legal and factual interpretation, judgment, and uncertainty, and significant judgment is required to determine the recognition and measurement attributes prescribed in certain accounting guidance. Tax laws themselves are subject to change as a result of changes in fiscal policy, changes in legislation, and the evolution of regulations and court rulings. Consequently, taxing authorities may impose tax assessments or judgments against us that could materially impact our tax liability and/or our effective income tax rate.
22
Our provision for income taxes is subject to volatility and can be adversely affected by a variety of factors, including but not limited to: unanticipated decreases in the amount of revenue or earnings in countries with low statutory tax rates, changes in tax laws and the related regulations and interpretations (including various proposals currently under consideration), changes in accounting principles (including accounting for uncertain tax positions), and changes in the valuation of our deferred tax assets. Significant judgment is required to determine the recognition and measurement attributes prescribed in certain accounting guidance. This guidance applies to all income tax positions, including the potential recovery of previously paid taxes, which if settled unfavorably could adversely impact our provision for income taxes.
In addition, we are subject to examination of our income tax returns by the Internal Revenue Service (“IRS”) and other tax authorities. If tax authorities challenge the relative mix of our U.S. and international income, our future effective income tax rates could be adversely affected, including for future periods and retroactively. While we regularly assess the likelihood of adverse outcomes from such examinations and the adequacy of our provision for income taxes, there can be no assurance that such provision is sufficient and that a determination by a tax authority will not have an adverse effect on our business, financial condition, results of operations, and cash flows.
Our ability to use certain net operating loss carryforwards and certain other tax attributes may be limited.
Under Sections 382 and 383 of the Code, if a corporation undergoes an “ownership change,” the corporation’s ability to use its pre-change net operating loss carryforwards and other pre-change tax attributes to offset its post-change income and taxes may be limited. In general, an “ownership change” occurs if there is a cumulative change in ownership of the relevant corporation by “5% shareholders” (as defined under U.S. income tax laws) that exceeds 50 percentage points over a rolling three-year period. Similar rules apply under state tax laws. If our corporate subsidiaries experience one or more ownership changes in connection with transactions in our stock, then we may be limited in our ability to use our corporate subsidiaries’ net operating loss carryforwards and other tax assets to reduce taxes owed on the net taxable income that such subsidiaries earn. Any such limitations on the ability to use net operating loss carryforwards and other tax assets could adversely impact our business, financial condition, results of operations, and cash flows.
We face risks associated with past and future investments, acquisitions, and other strategic transactions.
We may buy or make investments in complementary or competitive companies, products, and technologies, sell strategic businesses or other assets, or engage in other strategic transactions. For example, in fiscal 2018 we bolstered our consumer VPN offering through our acquisition of TunnelBear. The consideration exchanged for an acquisition may be greater than the value we realize from the transaction. In addition, we and TPG, Thomas Bravo and Intel periodically evaluate our capital structure and strategic alternatives with advisors and other third parties in an effort to maximize value for our stockholders. We cannot be certain when or if any of the discussions we have will lead to a proposal that we may find attractive, including with respect to the refinancing or repricing of some or all of our indebtedness, the sale of some or a significant portion of our assets, or other similar significant transactions. Whether in connection with such events or otherwise, we may also take other actions that impact our balance sheet and capital structure, including the payment of special dividends, the increase or decrease of regular dividends, repayment of debt, repurchases of our equity through privately negotiated transactions, as part of a tender offer, in the open market and/or through a share repurchase plan, including an accelerated share repurchase plan, or any other means permitted by law. In some cases these transactions could be with, or disproportionately benefit, one or more of our significant stockholders.
Future transactions could result in significant transactions-related charges, acceleration of some or all payments under our tax receivable agreement, disparate tax treatment for our stockholders, distraction for our management team, and potential dilution to our equity holders. In addition, we face a number of risks relating to such transactions, including the following, any of which could harm our ability to achieve the anticipated benefits of our past or future strategic transactions.
Technology and market risk. Cybersecurity technology is particularly complex because it must effectively and efficiently identify and respond to new and increasingly sophisticated threats while meeting other stringent technical requirements in areas of performance, usability, availability, and others. Our investments and acquisitions carry inherent uncertainty as to the efficacy of our technology roadmap. The decisions we make regarding customer requirements, market trends, market segments, and technologies may not be correct and we may not achieve the anticipated benefits of these transactions.
Integration or separation. Integration of an acquired company or technology is a complex, time consuming, and expensive process. The successful integration of an acquisition requires, among other things, that we integrate and retain key management, sales, research and development, and other personnel; integrate or separate the acquired products into or from our product offerings from both an engineering and sales and marketing perspective; integrate and support, or separate from, existing suppliers, distribution, and partner relationships; coordinate research and development efforts; and potentially consolidate, or prepare standalone, facilities and functions and back-office accounting, order processing, and other functions. If we do not successfully integrate an acquired company or technology, we may not achieve the anticipated benefits.
23
The geographic distance between sites, the complexity of the technologies and operations being integrated or separated, and disparate corporate cultures, may increase the difficulties of such integration or separation. Management’s focus on such operations may distract attention from our day-to-day business and may disrupt key research and development, marketing, or sales efforts. In addition, it is common in the technology industry for aggressive competitors to attract customers and recruit key employees away from companies during the integration phase of an acquisition.
Internal controls, policies, and procedures. Acquired companies or businesses are likely to have different standards, controls, contracts, procedures, and policies, making it more difficult to implement and harmonize company-wide financial, accounting, billing, information, and other systems. Acquisitions of privately held and/or non-U.S. companies are particularly challenging because their prior practices in these areas may not meet the requirements of GAAP and U.S. export regulations. Furthermore, we may assume liabilities associated with past practices and the Company’s compliance with legal and regulatory requirements in the jurisdictions in which they or we operate. Any acquisitions may require that we spend significant management time and attention establishing these standards, controls, contracts, procedures, and policies.
Key employees may be difficult to retain and assimilate. The success of many strategic transactions depends to a great extent on our ability to retain and motivate key employees. This can be challenging, particularly in the highly competitive market for technical personnel. Retaining key executives for the long term can also be difficult due to other opportunities available to them. Disputes that may arise out of earn-outs, escrows, and other arrangements related to an acquisition of a company in which a key employee was a principal may negatively affect the morale of the employee and make retaining the employee more difficult.
Risks Related to Our Solutions and Sales to Our Customers
Over the last several years, we have pursued a variety of strategic initiatives designed to optimize and reinforce our cybersecurity platform. If the benefits of these initiatives are less than we anticipate, or if the realization of such benefits is delayed, our business and results of operations may be harmed.
Over the last several years, we have pursued a variety of strategic initiatives designed to optimize and reinforce our cybersecurity platform, including investing in new routes to market and partnerships, refining our go-to-market strategies, adding new capabilities and products through strategic acquisitions, and divesting our enterprise business to focus on a standalone consumer-focused strategy. The anticipated benefits of these initiatives may not be fully realized, if at all, until future periods. However, if we do not achieve the anticipated benefits from these and our other strategic initiatives, or if the achievement of such anticipated benefits is delayed, our financial condition, results of operations, and cash flows may be adversely affected.
Our investments in new or enhanced solutions may not yield the benefits we anticipate.
The success of our business depends on our ability to develop new technologies and solutions, to anticipate future customer requirements and applicable industry standards, and to respond to the changing needs of our customers, competitive technological developments, and industry changes. Within our consumer business, we are presently investing in cybersecurity solutions to protect consumers’ PC and mobile devices, identity, privacy, family safety, web browsing, IoT, and smart home devices. We intend to continue to invest in these cybersecurity solutions by adding personnel and other resources to our business. We will likely recognize costs associated with these investments earlier than the anticipated benefits. If we do not achieve the anticipated benefits from these investments, or if the achievement of these benefits is delayed, our business, financial condition, results of operations, and cash flows may be adversely affected.
The process of developing new technologies is time consuming, complex, and uncertain, and requires the commitment of significant resources well in advance of being able to fully determine market requirements and industry standards. Furthermore, we may not be able to timely execute new technical product or solution initiatives for a variety of reasons such as errors in planning or timing, technical difficulties that we cannot timely resolve, or a lack of appropriate resources. Complex solutions like ours may contain undetected errors or compatibility problems, particularly when first released, which could delay or adversely impact market acceptance. We may also experience delays or unforeseen costs related to integrating products we acquire with products we develop, because we may be unfamiliar with errors or compatibility issues of products we did not develop ourselves. Any of these development challenges, or the failure to appropriately adjust our go-to-market strategy to accommodate new offerings, may result in delays in the commercial release of new solutions or may cause us to terminate development of new solutions prior to commercial release. Any such challenges could result in competitors bringing products or services to market before we do and a related decrease in our market segment share and net revenue. Our inability to introduce new solutions and enhancements in a timely and cost-effective manner, or the failure of these new solutions or enhancements to achieve market acceptance and comply with industry standards and governmental regulation, could seriously harm our business, financial condition, results of operations, and cash flows.
24
If our solutions have or are perceived to have defects, errors, or vulnerabilities, or if our solutions fail or are perceived to fail to detect, prevent, or block cyberattacks, including in circumstances where customers may fail to take action on attacks identified by our solutions, our reputation and our brand could suffer, which would adversely impact our business, financial condition, results of operations, and cash flows.
Many of our solutions are complex and may contain design defects, vulnerabilities, or errors that are not detected before their commercial release. Our solutions also provide our customers with the ability to customize a multitude of settings, and it is possible that a customer could misconfigure our solutions or otherwise fail to configure our solutions in an optimal manner. Such defects, errors, and misconfigurations of our solutions could cause our solutions to be vulnerable to cybersecurity attacks, cause them to fail to perform the intended operation, or temporarily interrupt the operations of our customers. In addition, since the techniques used by adversaries change frequently and generally are not recognized until widely applied, there is a risk that our solutions would not be able to address certain attacks. Moreover, our solutions could be targeted by bad actors and attacks specifically designed to disrupt our business and undermine the perception that our solutions are capable of providing their intended benefits, which, in turn, could have a serious impact on our reputation. The risk of a cybersecurity attack increased during the recent COVID-19 pandemic as more individuals are working from home and utilizing home networks for the transmission of sensitive information. Any cybersecurity vulnerability or perceived cybersecurity vulnerability of our solutions or systems could adversely affect our business, financial condition, results of operations, and cash flows.
Changing, updating, enhancing, and creating new versions of our solutions may cause errors or performance problems in our products and solutions, despite testing and quality control. We cannot be certain that defects, errors, or vulnerabilities will not be found in any such changes, updates, enhancements, or new versions, especially when first introduced. In addition, changes in our technology may not provide the additional functionality or other benefits that were expected. Implementation of changes in our technology also may cost more or take longer than originally expected and may require more testing than initially anticipated. While new solutions are generally tested before they are used in production, we cannot be sure that the testing will uncover all problems that may occur in actual use.
If any of our customers are affected by a cybersecurity attack (such as suffering a ransomware attack or otherwise becoming infected with malware) while using our solutions, such customers could be disappointed with our solutions or perceive that our solutions failed to perform their intended purpose, regardless of whether our solutions operated correctly, blocked, or detected the attack or would have blocked or detected the attack if configured properly. If our customers experience security breaches or incidents, such customers and the general public may believe that our solutions failed. Real or perceived security breaches or incidents impacting our customers could cause disruption or damage or other negative consequences and could result in negative publicity about us, reduced sales, damage to our reputation and competitive position, increased expenses, and customer retention challenges.
Furthermore, our solutions may fail to detect or prevent malware, viruses, worms, or similar threats for any number of reasons, including our failure to enhance and expand our solutions to reflect market trends and new attack methods, new technologies and new operating environments, the complexity of our customers’ environment and the sophistication and coordination of threat actors launching malware, ransomware, viruses, intrusion devices, and other threats. Failure to keep pace with technological changes in the cybersecurity industry and changes in the threat landscape could also adversely affect our ability to protect against security breaches and incidents and could cause us to lose customers.
If we are unable to increase sales of our solutions to new customers, our future results of operations may be harmed.
An important part of our growth strategy involves continued investment in direct marketing efforts, channel partner relationships, our sales force, and infrastructure to add new customers. The number and rate at which new customers may purchase our products and services depends on a number of factors, including those outside of our control, such as customers’ perceived need for our solutions, competition, general economic conditions, market transitions, product obsolescence, technological change, public awareness of security threats to IT systems, macroeconomic conditions, and other factors. These new customers, if any, may renew their subscriptions at lower rates than we have experienced in the past, which could affect our financial results.
25
We rely on large amounts of data from a variety of sources to support our solutions and the loss of access to or the rights to use such data could reduce the efficacy of our solutions and harm our business.
Like many of our industry peers, we leverage large amounts of data related to threats, vulnerabilities, cyberattacks, and other cybersecurity intelligence to develop and maintain a number of our products and services. We collect, develop, store, and otherwise process portions of this data using third parties and our own technology. We cannot be assured that such third parties or our technology that support the collection, development, storage or other processing of such data, and the sources of such data itself, will continue to be effective or available and the loss or reduction in quality of such data may adversely impact the efficacy of our solutions. Changes in laws or regulations in the United States or foreign jurisdictions, or their interpretation or application, or the actions of governmental or quasi-governmental entities may increase the costs to collect, develop, store, or otherwise process such data, partially or completely prohibit use of such, impose burdensome obligations in connection with such, or could result in disclosure of such data to the public or other third parties, which may reduce its value to us or as part of our solutions and thereby harm our business.
Risks Related to Our Brand and Intellectual Property
If the protection of our proprietary technology is inadequate, we may not be able to adequately protect our innovations and brand.
Our success is dependent on our ability to create proprietary technology and to protect and enforce our intellectual property rights in that technology, as well as our ability to defend against adverse claims of third parties with respect to our technology and intellectual property rights. To protect our proprietary technology, we rely primarily on a combination of patent, copyright, trademark, and trade secret laws, as well as contractual provisions and operational and procedural confidentiality protections. The agreements that we enter into with our employees, contractors, partners, vendors, and end-users may not prevent unauthorized use or disclosure of our proprietary technology or infringement of our intellectual property rights and may not provide an adequate remedy in the event of unauthorized use or disclosure of our proprietary technology or infringement of our intellectual property rights, which may substantially harm our business. Furthermore, we cannot be assured that such agreements will be fully enforceable, or that they will not be breached by the counterparties, or that we will be able to detect, deter, or adequately address any such breach or threatened breach. As a provider of cybersecurity solutions, we may be an attractive target for computer hackers or other bad actors and may have a greater risk of unauthorized access to, and misappropriation of, our systems, technology, and proprietary information. Despite our efforts to protect our proprietary rights, unauthorized parties may attempt to copy aspects of our products or obtain and use information that we regard as proprietary. Policing unauthorized use of our products and infringement of our rights is difficult. In addition, the laws of some foreign countries, including countries where we sell solutions or have operations, do not protect proprietary rights to as great an extent as do the laws of the United States. Our means of protecting our proprietary rights may not be adequate and third parties, including current and future competitors, may independently develop similar or superior technology, duplicate or reverse engineer aspects of our products, or design around our patented technology or otherwise infringe or circumvent our intellectual property rights.
As of December 25, 2021, we had approximately 1,235 issued U.S. patents, in addition to approximately 735 issued foreign patents. There can be no assurance that any of our pending patent applications will issue or that the patent examination process will not result in our narrowing the claims applied for in our patent applications or that any current or future issued patents will not be later challenged, limited, or invalidated. Furthermore, there can be no assurance that we will be able to detect any infringement of our existing or future intellectual property rights or, if infringement is detected, that we will be successful in asserting claims or counterclaims, that our intellectual property rights will be enforceable, that any damages awarded to us will be sufficient to adequately compensate us for the infringement, that we will be able to obtain injunctive relief to prevent ongoing infringement, or that the costs of seeking enforcement will not outweigh any benefits.
There can be no assurance or guarantee that any products, services, or technologies that we are presently developing, or will develop in the future, will result in intellectual property that is subject to legal protection under the laws of the United States or a foreign jurisdiction or that produces a competitive advantage for us.
26
We may be sued by third parties for alleged infringement, misappropriation, or other violation of their proprietary rights, and it may be necessary for us to sue third parties to enforce and protect our proprietary rights, resulting in potential lengthy and expensive litigation.
From time to time, third parties may claim that we have infringed, misappropriated, or otherwise violated their intellectual property rights, including claims regarding patents, copyrights, trademarks, and trade secrets. Because of constant technological change in the segments in which we compete, the extensive patent coverage of existing technologies, and the rapid rate of issuance of new patents, we expect the trend of third-party claims to continue and that we will be required to defend against actual or threatened litigation of this type. The litigation process is subject to inherent uncertainties, so we may not prevail in litigation matters regardless of the merits of our position. Our participation in any litigation could cause us to incur substantial costs and could distract our management from the day-to-day operations of our business. In addition to the expense and distraction associated with litigation, adverse determinations could cause us to lose our proprietary rights, prevent us from manufacturing or selling our products, require us to obtain licenses to patents or other intellectual property rights that our products are alleged to infringe, misappropriate, or otherwise violate (which licenses may not be available on commercially reasonable terms or at all), or re-design or re-engineer our products to address actual or claimed infringement, misappropriation, or other violation and subject us to significant liabilities.
If we acquire technology to include in our products from third parties, our exposure to actions alleging infringement, misappropriation, or other violation may increase because we must rely upon these third parties to verify the origin and ownership of such technology. Our agreements with such third parties may not provide adequate protections or remedies, and we may not be able to compel such third parties to provide any available remedies in the case of such actions. Similarly, we face exposure to actions alleging infringement, misappropriation, or other violation if we hire or engage software engineers or other personnel who were previously engaged by competitors or other third parties and those personnel inadvertently or deliberately incorporate proprietary technology of third parties into our products despite efforts to prevent such infringement, misappropriation, or other violation.
From time to time, the U.S. Supreme Court, other U.S. federal courts and the U.S. Patent and Trademark Appeals Board, and their foreign counterparts, have made and may continue to make changes to the interpretation of patent, copyright, trademark, or other intellectual property laws in their respective jurisdictions. We cannot predict future changes to the interpretation of such existing laws or whether U.S. or foreign legislative bodies will amend such laws in the future. Any such changes may lead to uncertainties or increased costs and risks surrounding the prosecution, validity, ownership, enforcement, and defense of our issued patents and patent applications and other intellectual property, the outcome of third-party claims of infringement, misappropriation, or other violation of intellectual property brought against us and the actual or enhanced damages (including treble damages) that may be awarded in connection with any such current or future claims, and could have a material adverse effect on our business, financial condition, results of operations, and cash flows.
We rely on certain technology that we license from third parties, including software that is integrated with internally developed software and used with our products. Any loss of those licenses or any quality issues with third-party technology integrated with our products could have an adverse impact on our reputation and business.
We rely on certain technology that we license from third parties, including third-party commercial software and open source software, which is integrated into or used with many of our solutions. This third-party technology may currently or could, in the future, infringe the intellectual property rights of third parties or the licensors may not have sufficient rights to the technology they license us in all jurisdictions in which we may sell our solutions. The licensors of the third-party technology we use may discontinue their offerings or change the prices for and other terms under which their technology is licensed. If we are unable to continue to license any of this technology on terms we find acceptable, or if there are quality, security, or other substantive issues with any of this technology, we may face delays in releases of our solutions or we may be required to find alternative vendors or remove functionality from our solutions. In addition, our inability to obtain certain licenses or other rights might require us to engage in potentially costly and time-consuming dispute resolution or litigation regarding these matters. Any of the foregoing could have a material adverse effect on our business, financial condition, results of operations, and cash flows.
27
Our use of open source software could negatively affect our ability to sell our solutions and subject us to possible litigation.
We use open source software in our solutions and our development and operating environments and expect to continue to use open source software in the future. Open source software is typically provided without assurances of any kind and could contain errors, bugs, or vulnerabilities or infringe the intellectual property rights of third parties. Because the source code of open source software components included in our solutions is publicly available, in instances where our usage is publicly disclosed or known, it may be easier to identify exploits or vulnerabilities in such open source software components, making our solutions using such open source software components more vulnerable to third parties seeking to compromise, undermine, or circumvent our solutions. If open source software programmers do not continue to develop and enhance open source technologies, our development expenses could increase and our schedules could be delayed. In addition, we may face claims from others seeking to enforce the terms of open source licenses, including by demanding release of derivative works or our proprietary source code that was developed using or otherwise used in connection with such open source software. The terms of many open source licenses have not been interpreted by U.S. or foreign courts, and these licenses could be construed in a way that could impose other unanticipated costs, conditions, or restrictions on our ability to commercialize our products. These claims could also result in litigation, require us to purchase a costly license, require us to devote additional research and development resources to change our solutions, or stop or delay shipment of such solutions, any of which could have a negative effect on our business, financial condition, results of operations, and cash flows. In addition, if the license terms for the open source software that we utilize change, we may be forced to reengineer our solutions or incur additional costs. Although we have policies designed to manage the use, incorporation, and updating of open source software into our products, we cannot be certain that we have in all cases incorporated open source software in our products in a manner that is consistent with the applicable open source license terms and inclusive of all available updates or security patches, and as a result we may be subject to claims for breach of contract or infringement by the applicable licensor, claims for breach of contract or indemnity by our partners or customers, or other third parties, or we or our partners or customers could be required to release our proprietary source code, pay damages, royalties, or license fees or other amounts, seek licenses, or experience quality control or security risks, any of which could require us to re-engineer our solutions, discontinue sales in the event re-engineering cannot be accomplished on a timely basis, or take other remedial action that may divert resources away from our development efforts, any of which could adversely affect our business.
If we fail to successfully promote or protect our brand, our business, and competitive position may be harmed.
Due to the intensely competitive nature of our markets, we believe that building and maintaining our brand and reputation is critical to our success, and that the importance of positive brand recognition will increase as competition in our market further intensifies. Over our 30-year history, we have invested and expect to continue to invest substantial resources to promote and maintain our brand as a trusted cybersecurity provider, but there is no guarantee that our brand development strategies will enhance the recognition of our brand or lead to increased sales of our solutions.
In recent years, there has been a marked increase in the use of social media platforms, including blogs, chat platforms, social media websites, and other forms of internet-based communications that allow individuals access to a broad audience of consumers and other persons. The rising popularity of social media and other consumer-oriented technologies has increased the speed and accessibility of information dissemination and given users the ability to more effectively organize collective actions such as boycotts. Negative publicity, whether or not justified, can spread rapidly through social media. The dissemination of information via social media could harm our brand or our business, regardless of the information’s accuracy. To the extent that we are unable to respond timely and appropriately to negative publicity, our reputation and brand could be harmed. This could include negative publicity related to our products or services or negative publicity related to actions by our executives, team members or other unaffiliated individuals or entities that may be perceived as being associated with us. Moreover, even if we are able to respond in a timely and appropriate manner, we cannot predict how negative publicity may affect our reputation and business. In addition, we and our employees use social media and other internet-based communications methods to communicate with our end-users, customers, partners, and the public in general. There is risk that the social media communications of us or our employees could be received negatively. Failure to use social media or other internet-based communication methods effectively could lead to a decline in our reputation. Further, laws and regulations, including associated enforcement priorities, rapidly evolve to govern social media platforms and other internet-based communications, any failure by us or third parties acting at our direction to abide by applicable laws and regulations in the use of social media or internet-based communications could adversely impact our reputation, financial performance or subject us to fines or other penalties. Other risks associated with the use of social media and internet based-communication include improper disclosure of proprietary information, negative comments about our brand, products, or services, exposure of personally identifiable information, fraud, hoaxes, or malicious dissemination of false information.
28
Risks Related to Third Party Relationships
We rely significantly on third-party channel partners to facilitate the sale of our products and solutions. If we fail to manage our sales and distribution channels effectively, or if our partners choose not to market and sell our solutions to their customers, our operating results could be adversely affected.
We sell a significant portion of our solutions through third-party intermediaries such as affiliates, retailers, ecommerce, PC OEMs, and other distribution channel partners (we refer to them collectively as “channel partners”). In fiscal 2021, fiscal 2020, and fiscal 2019, our largest customer accounted for 16%, 13%, and 13%, respectively, of our net revenue. Our reliance on these channel partners is subject to a number of risks, including:
From an anti-bribery and anti-corruption perspective, our business activities are subject to the FCPA and similar anti-bribery or anti-corruption laws, regulations, and rules of the countries that we operate in. These laws generally prohibit companies and their employees and third party business partners, representatives, and agents from engaging in corruption and bribery, including offering, promising, giving, or authorizing the provision of anything of value, either directly or indirectly, to a government official or commercial party to influence any official action, direct business to any person, gain any improper advantage, or obtain or retain business. Anti-corruption and anti-bribery laws have been enforced aggressively in recent years and are interpreted broadly. We and our third-party partners may have direct or indirect interactions with officials and employees of government agencies or state-owned or affiliated entities and may be held liable for inaccurate or incomplete accounting records, internal accounting controls deemed inadequate by applicable regulatory authorities, and corrupt or other illegal activities of our employees, affiliates, third parties, representatives, and agents even if we did not explicitly authorize those activities. This risk is even greater in the countries where we operate that are known to present a heightened risk for corruption.
A significant portion of our revenue is derived from sales through our PC OEM partners that bundle our products with their products. Our reliance on this sales channel is significantly affected by our partners’ sales of new products into which our products or services are bundled. Our revenue from sales through our PC OEM partners is affected primarily by the number of personal computers on which our products are bundled, the geographic mix of their sales, and the rate at which consumers purchase or subscribe to the bundled products. Our PC OEM partners are also in a position to exert competitive pricing pressure. The rate at which consumers purchase or subscribe to the bundled products is affected by other factors, including other terms with the OEM. The continued decline in the PC market as the market shifts towards mobility has increased competition for PC OEMs’ business and gives PC OEMs leverage to demand financial concessions from us in order to secure their business. These agreements require a significant commitment of resources and capital. There is no guarantee we will have sufficient resources to maintain these agreements or secure new PC OEM partners. Even if we negotiate what we believe are favorable terms when we first establish a relationship with a PC OEM, at the time of the renewal of the agreement, we may be required to renegotiate our agreement with them on less favorable terms. Lower net prices for our products or other financial concessions would adversely impact our financial results. Further, acquiring high numbers of customers through our PC OEM partner channel may adversely impact our profitability, as we may see lower average prices from higher mix of new customers and under the PC OEM agreements we may see higher partner related spending during the period of high PC demand and high customer acquisition, until such customers renew with us upon subscription expiration. Any adverse changes in our relationship with our channel partners could have an adverse effect on our business and financial results.
29
We rely on third-parties to replicate and package certain of our software products, which subjects us to risks of product delivery delays and other supply risks.
We rely on a limited number of third parties to replicate and package our boxed software products. Our reliance on these third-parties reduces our control over our supply chain and exposes us to risks, including reduced control over quality assurance, product costs, product supply, timing, and transportation risk. From time to time, we may be required to add new partners to accommodate growth in orders or the addition of new products. It is time consuming and costly to qualify and implement new supply chain partner relationships, and such additions increase the complexity of our supply chain management. If we lose, terminate, or fail to effectively manage our supply chain partner relationships, or if any of our partners experience production interruptions or shut-downs, including those caused by a natural disaster, epidemic, pandemic (such as the COVID-19 pandemic), capacity shortage, or quality-control problem, it would negatively affect sales and adversely affect our business and results of operations.
We rely on third parties to support our information technology infrastructure and any service interruptions or other failures of our third-party providers or of our information technology infrastructure could result in disruption to our operations or adversely impact our business.
We engage third parties to provide variety of information technology products and services to support our information technology infrastructure. Any failure on the part of our third-party providers or of our information technology infrastructure to operate effectively, stemming from maintenance problems, upgrading or transitioning to new platforms, a breach in security or other unanticipated problems could result in interruptions to or delays in our operations or our products or services. Our third-party providers may also discontinue providing the information technology products or services we use and we may be required to replace such products or services, which could result in unanticipated expenses and disruptions to our information technology infrastructure.
In addition, we make significant investments in new information technology infrastructure, but the implementation of such investments could exceed estimated budgets and we may experience challenges that prevent new strategies or technologies from being realized according to anticipated schedules. If we are unable to effectively maintain our current information technology and processes or encounter delays, or fail to exploit new technologies, then the execution of our business plans may be disrupted. Our employees and other personnel require effective tools and techniques supported by our information technology infrastructure to perform functions integral to our business. Any failure to successfully provide such tools and systems, or ensure that our personnel have properly adopted them, could materially and adversely impact our ability to achieve positive business outcomes.
Some of our systems or data that we may maintain or process may not be adequately backed up, and our disaster recovery planning cannot account for all eventualities. The occurrence of a natural disaster, intentional sabotage, or other unanticipated problems could result in significant interruptions to our operations or the permanent loss of valuable data, which could harm our reputation and reduce the efficacy and value of products and services. In addition, the implementation of changes and upgrades to our information technology infrastructure and any errors, vulnerabilities, damage, or failure of our information technology infrastructure, could result in interruptions to our operations or products or services and non-compliance with certain laws or regulations, which may lead us to face fines or penalties, give rise to indemnification or other contractual claims against us by our customers or other third parties, and otherwise adversely impact our business.
Our third-party strategic alliances expose us to a range of business risks and uncertainties that are outside of our control and that could have a material adverse impact on our business and financial results.
We have entered, and intend to continue to enter, into strategic alliances with third parties to support our future growth plans. These relationships involve technology licensing, product integration, and co-marketing and co-promotion activities. For example, we have arrangements with operating system vendors that provide us with sufficient technological access to new and updated versions of their operating systems to enable us to develop and deploy interoperable products that are deeply integrated with their operating systems on our customers’ networks and devices. We also partner with certain Internet search providers to promote their offerings to our customers. We invest significant time, money, and resources to establish and maintain these strategic relationships, but we have no assurance that any particular relationship will continue for any specific period of time.
Furthermore, certain of these strategic partners currently offer, and may in the future offer, products, and services that compete with our own solutions in certain markets, and in the future these partners may impose limitations on, or terminate, our partnerships in order to improve their own competitive position. Generally, our agreements with these partners are terminable without cause with no or minimal notice or penalties. Any adverse change in our relationships with a significant strategic partner could limit or delay our ability to offer certain new or competitive solutions, increase our development costs, and reduce our revenue, any of which could have an adverse impact on our competitive position and our financial performance. In addition, we could be required to incur significant expenses to develop a new strategic partnership or to develop and implement an alternative plan to pursue the opportunity that we targeted with the former partner, which could adversely affect our business, financial condition, results of operations, and cash flows.
30
Risks Related to our Technology Systems and Privacy
If our security measures are breached or unauthorized access to our data is otherwise obtained, or if we suffer other cybersecurity incidents, our brand, reputation, and business could be harmed, and we may incur significant liabilities.
As a cybersecurity leader, we are a high-profile target for data breaches, cyberattacks, and other intentional disruptions of our systems and our solutions. Our networks and solutions may have bugs, defects, or vulnerabilities that may be targeted by hackers and could be targeted by attacks specifically designed to disrupt our business, access our network, source code or other data (including by causing data to be lost, corrupted or unavailable), and harm our reputation. Similarly, experienced computer programmers or other sophisticated individuals or entities, including malicious hackers, state-sponsored organizations, criminal networks, and insider threats including actions by employees and third-party service providers, may attempt to penetrate our network security or the security of our systems and websites, and misappropriate proprietary information or cause interruptions of our solutions, including the operation of the global civilian cyber intelligence threat network. This risk has increased during the current COVID-19 pandemic as more individuals are working from home and utilizing home networks for the transmission of sensitive information. The techniques used to obtain unauthorized access, disable or degrade service, or sabotage systems change frequently, often are not recognized until launched against a target, and may originate from less regulated or remote areas around the world. As a result, we may be unable to proactively prevent these techniques, implement adequate preventative or reactionary measures, react to or address any attack or incident in a timely manner or enforce the laws and regulations that govern such activities. Such attacks may go undetected for a period of time complicating our ability to respond effectively. In addition, it is possible that hardware failures, human errors (including being subject to phishing attacks, social engineering techniques, or similar methods) or errors in our systems could result in data loss, unavailability, or corruption, or cause the information that we collect to be incomplete or contain inaccuracies. We may not be able to correct any security flaws or vulnerabilities promptly, or at all. A breach of our network security and systems or other cybersecurity incidents or events, including attacks involving ransomware or other malware, that cause the loss or public disclosure of, or access by third parties to, our systems or any unauthorized access to, or loss, corruption, unavailability, or unauthorized use of data that we maintain or process, or the perception that any of these have occurred, could have serious negative consequences for our business, including possible fines, penalties and damages, reduced demand for our solutions, an unwillingness of our customers to use our solutions, harm to our brand and reputation, and time consuming and expensive litigation. In addition, such a security breach or incident could impair our ability to operate our business, including our ability to provide subscription and support services to our customers. Additionally, our service providers may suffer or be perceived to suffer, data security breaches or other incidents, or may have exploitable defects or bugs in their systems, software, or networks, that may compromise data stored or processed for us that may give rise to any of the foregoing. Additionally, supply chain attacks have increased in frequency and severity, and we cannot guarantee that third parties and infrastructure in our supply chain have not been compromised or that they do not contain exploitable defects or bugs that could result in a breach of or disruption to our solutions, systems, or networks or the systems and networks of third parties that support us and our services. Any of these negative outcomes could adversely impact our business and results of operations.
We incur significant costs in an effort to detect and prevent security breaches and other security-related incidents and we expect our costs will increase as we make improvements to our systems and processes to prevent further breaches and incidents. In the event of a future breach or incident, we could be required to expend additional significant capital and other resources in an effort to prevent further breaches or incidents, which may require us to divert substantial resources. Moreover, we could be required or otherwise find it appropriate to expend significant capital and other resources to respond to, notify third parties of, and otherwise address the incident or breach and its root cause. Each of these could require us to divert substantial resources.
Furthermore, while our errors and omissions insurance policies include liability coverage for certain of these matters, if we experience a widespread security breach or other incident, we could be subject to indemnity claims or other damages that exceed our insurance coverage. We also cannot be certain that our insurance coverage will be adequate for data handling or data security liabilities actually incurred, that insurance will continue to be available to us on economically reasonable terms, or at all, or that any insurer will not deny coverage as to any future claim. The successful assertion of one or more large claims against us that exceed available insurance coverage, or the occurrence of changes in our insurance policies, including premium increases or the imposition of large deductible or co-insurance requirements, could have a material adverse effect on our business, including our financial condition, results of operations, and reputation.
31
We rely on payment cards to receive payments and are subject to payment-related risks.
We accept a variety of payment methods, including credit cards and debit cards, as payment for certain of our consumer solutions. Accordingly, we are, and will continue to be, subject to significant and evolving regulations and compliance requirements relating to payment card processing. This includes laws governing the collection, processing and storage of sensitive consumer information, as well as industry requirements such as the Payment Card Industry Data Security Standard (“PCI-DSS”). These laws and obligations may require us to implement enhanced authentication and payment processes that could result in increased costs and liability, and reduce the ease of use of certain payment methods. For certain payment methods, including credit and debit cards, we pay interchange and other fees, which may increase over time. We are also subject to payment card association operating rules and agreements, including PCI-DSS, certification requirements, and rules governing electronic funds transfers, which could change or be reinterpreted to make it difficult or impossible for us to comply. If we fail to comply with these rules or requirements, or if our data security systems are breached or compromised, we may be liable for losses incurred by card issuing banks or consumers, subject to fines and higher transaction fees, lose our ability to accept credit or debit card payments from our consumers, or process electronic fund transfers or facilitate other types of payments. Any failure to comply with these requirements could significantly harm our brand, reputation, business, and results of operations.
Our failure to adequately maintain and protect personal information of our customers or our employees in compliance with evolving legal requirements could have a material adverse effect on our business.
We collect, use, store, disclose, or transfer (collectively, “process”) personal information, including from employees and customers, in connection with the operation of our business. A wide variety of local and international laws and regulations apply to the processing of personal information. Data protection and privacy laws and regulations are evolving and being tested in courts and may result in increasing regulatory and public scrutiny and escalating levels of enforcement and sanctions. For example, the E.U. has adopted the General Data Protection Regulation (“GDPR”), which took effect on May 25, 2018. The GDPR imposes requirements that may limit how we are permitted to process data on behalf of ourselves and our clients, and we may be required to incur significant additional costs to comply with these requirements. Applicable laws, regulations and court decisions in the E.U. relating to privacy and data protection could also impact our ability to transfer personal data internationally. The GDPR specifies substantial maximum fines for failure to comply of up to 20 million Euros or 4% of a company’s worldwide turnover, whichever is higher. Continued compliance with the GDPR and national laws in the E.U. may require significant changes to our products and practices to ensure compliance with applicable law.
A variety of data protection legislation also apply in the United States at both the federal and state level, including new laws that may impact our operations. For example, in June 2018, the State of California enacted the California Consumer Privacy Act of 2018 (“CCPA”), which went into effect on January 1, 2020, with enforcement by the state attorney general beginning July 1, 2020. The CCPA defines “personal information” in a broad manner and generally requires companies that process personal information of California residents to make new disclosures about their data collection, use, and sharing practices, allows consumers to opt-out of certain data sharing with third parties or sale of personal information, and provides a new cause of action for data breaches. Moreover, California voters approved the California Privacy Rights Act (“CPRA”), in November 2020. The CPRA significantly modifies the CCPA, creating obligations relating to consumer data beginning on January 1, 2022, with enforcement beginning July 1, 2023. On March 2, 2021, Virginia enacted the Virginia Consumer Data Protection Act, or CDPA, which becomes effective on January 1, 2023, and on June 8, 2021, Colorado enacted the Colorado Privacy Act, or CPA, which takes effect on July 1, 2023. The CPA and CDPA share similarities with the CCPA, CPRA, and legislation proposed in other states. Aspects of these state privacy statutes remain unclear resulting in uncertainty and potentially requiring us to modify our data practices and policies and to incur substantial additional costs and expenses in an effort to comply. Additionally, the Federal Trade Commission, and many state attorneys general are interpreting federal and state consumer protection laws to impose standards for the online collection, use, dissemination, and security of data. The burdens imposed by the CCPA and other similar laws that have been or may be enacted at the federal and state level may require us to modify our data processing practices and policies and to incur substantial expenditures in order to comply.
32
Global privacy and data protection legislation, enforcement, and policy activity are rapidly expanding and evolving, and may be inconsistent from jurisdiction to jurisdiction. On July 16 2020, the Court of Justice of the European Union (“CJEU”), Europe’s highest court, held in the Schrems II case that the E.U.-U.S. Privacy Shield, a mechanism for the transfer of personal data from the E.U. to the U.S., was invalid, and imposed additional obligations in connection with the use of standard contractual clauses approved by the European Commission. The impact of this decision on the ability to lawfully transfer personal data from the E.U. to the U.S. remains uncertain. The European Commission released a draft of revised standard contractual clauses addressing the CJEU concerns in November 2020, and on June 4, 2021, published new standard contractual clauses. We may, in addition to other impacts, experience additional costs associated with increased compliance burdens relating to the Schrems II case, regulatory guidance, and other developments relating to cross-border data transfers, and we and our customers face the potential for regulators in the European Economic Area (“EEA”) to apply different standards to the transfer of personal data from the EEA to the U.S., and to block, or require ad hoc verification of measures taken with respect to, certain data flows from the EEA to the U.S. We may experience reluctance or refusal by current or prospective European customers to use our products, and we may find it necessary or desirable to make further changes to our handling of personal data of EEA residents. The regulatory environment applicable to the handling of EEA residents’ personal data, and our actions taken in response, may cause us to assume additional liabilities or incur additional costs and could result in our business, operating results and financial condition being harmed. We and our customers may face a risk of enforcement actions by data protection authorities in the EEA relating to personal data transfers to us and by us from the EEA. Any such enforcement actions could result in substantial costs and diversion of resources, distract management and technical personnel and negatively affect our business, operating results and financial condition. Additionally, we may be or become subject to data localization laws mandating that data collected in a foreign country be processed only within that country. If any country in which we have customers were to adopt a data localization law, we could be required to expand our data storage facilities there or build new ones in order to comply. The expenditure this would require, as well as costs of compliance generally, could harm our financial condition.
In addition to the GDPR, the European Commission has another draft regulation in the approval process that focuses on a person’s right to conduct a private life. The proposed legislation, known as the Regulation of Privacy and Electronic Communications, or ePrivacy Regulation, would replace the current ePrivacy Directive. Originally planned to be adopted and implemented at the same time as the GDPR, the ePrivacy Regulation is still being negotiated. Most recently, on February 10, 2021, the Council of the E.U. agreed on its version of the draft ePrivacy Regulation. If adopted, the earliest date for entry into force is in 2023, with broad potential impacts on the use of internet-based services and tracking technologies, such as cookies. Aspects of the ePrivacy Regulation remain for negotiation between the European Commission and the Council.
Further, in June 2016, the U.K. voted to leave the E.U., which resulted in the U.K. exiting the E.U. on January 31, 2020, subject to a transition period that ended on December 31, 2020. Brexit could lead to further legislative and regulatory changes. The U.K. has implemented legislation similar to the GDPR, including the U.K. Data Protection Act and legislation similar to the GDPR referred to as the U.K. GDPR, and which provides for substantial penalties of up to the greater of 17.5 million British Pounds or 4% of a company’s worldwide turnover, whichever is higher. Further, it remains to be seen whether the U.K.’s withdrawal from the E.U. pursuant to Brexit will substantially impact the manner in which U.K. data protection laws or regulations will develop in the medium to longer term and how data transfers to and from the U.K. will be regulated. On June 28, 2021, the European Commission announced a decision of “adequacy” concluding that the UK ensures an equivalent level of data protection to the GDPR, which provides some relief regarding the legality of continued personal data flows from the EEA to the U.K. Some uncertainty remains, however, as this adequacy determination must be renewed after four years and may be modified or revoked in the interim.
Our actual or alleged failure to comply with any applicable laws and regulations or contractual obligations relating to privacy, data protection, or information security, or to protect such data that we process, could result in litigation, regulatory investigations, and enforcement actions against us, including fines, orders, public censure, claims for damages by employees, customers, and other affected individuals, public statements against us by consumer advocacy groups, damage to our reputation and competitive position, and loss of goodwill (both in relation to existing customers and prospective customers), any of which could have a material adverse effect on our business, financial condition, results of operations, and cash flows. Evolving and changing definitions of personal information, personal data, and similar concepts within the E.U., the United States, and elsewhere, especially relating to classification of IP addresses, device identifiers, location data, household data, and other information we may collect, may limit or inhibit our ability to operate or expand our business, including limiting strategic partnerships that may involve the sharing of data. Additionally, if third parties that we work with, such as vendors or developers, violate applicable laws or our policies, such violations may also place personal information at risk and have an adverse effect on our business. Even the perception of privacy concerns, whether or not valid, may harm our reputation, subject us to regulatory scrutiny and investigations, and inhibit adoption of our products by existing and potential customers.
33
Risks Related to Our International Operations
We operate globally and are subject to significant business, economic, regulatory, social, political, and other risks in many jurisdictions.
Global or regional conditions may harm our financial results. We have operations in many countries and our business activities are concentrated in certain geographic areas including without limitation the Asia Pacific (“APAC”), Europe, Middle-East, and Africa (“EMEA”), and Latin American Region (“LAR”) regions. We derived 39% of our net revenue from international customers for fiscal 2021. As a result, our domestic and international operations and our financial results may be adversely affected by a number of factors outside of our control, including:
Research and development risks. We employ engineers in a number of jurisdictions outside the United States. In many of these jurisdictions the laws relating to the protection of rights in technology and intellectual property are less strict than the laws in the United States or not enforced to the same extent as they are enforced in the United States. As a result, in some foreign jurisdictions we may be subject to heightened attempts to gain unauthorized access to our information technology systems or surreptitiously introduce software into our products. These attempts may be the result of hackers or others seeking to harm us, our products, or our customers. We have implemented various measures to manage our risks related to these disruptions, but these measures may be insufficient, and a system failure or security breach or incident could negatively impact our business, financial condition, results of operations, and cash flows. The theft or unauthorized use or publication of our trade secrets and other confidential or proprietary business information as a result of such an incident could negatively impact our competitive position. In addition, we may incur additional costs to remedy the damages caused by these disruptions or security breaches or incidents.
34
Other operating risks. Additional risks of international business operations include the increased costs of establishing, managing, and coordinating the activities of geographically dispersed and culturally diverse operations (particularly sales and support and shared service centers) located on multiple continents in a wide range of time zones.
Risks Related to Regulation
We are subject to governmental export and import controls that could subject us to liability or impair our ability to compete in international markets.
Our solutions are subject to U.S. export and import controls, specifically the Export Administration Regulations and economic sanctions enforced by the Office of Foreign Assets Control. We incorporate standard encryption algorithms into certain of our solutions, which, along with the underlying technology, may be exported outside of the United States only with the required export authorizations, including by license, license exception, or other appropriate government authorizations, which may require the filing of a classification request or report. Furthermore, U.S. export control laws and economic sanctions prohibit the shipment of certain products and services to countries, governments, and persons targeted by U.S. sanctions. Even though we take precautions to ensure that we and our channel partners comply with all relevant regulations, any failure by us or our channel partners to comply with U.S. export requirements, U.S. customs regulations, U.S. economic sanctions, or other laws could have negative consequences, including reputational harm, government investigations, and substantial civil and criminal penalties (e.g., fines, incarceration for responsible employees and managers, and the possible loss of export or import privileges).
In addition, changes in our solutions or changes in export and import regulations may create delays in the introduction of our solutions into international markets, including as a consequence of new licensing requirements, prevent certain personnel from developing or maintaining our products, prevent our end-customers with international operations from deploying our products globally or, in some cases, prevent or delay the export or import of our solutions to certain countries, governments, or persons altogether. Any change in export or import regulations, economic sanctions or related legislation, shift in the enforcement or scope of existing regulations, or change in the countries, governments, entities, persons, or technologies targeted by such regulations, could result in decreased use of our solutions by, or in our decreased ability to develop, export to, import into, or sell our solutions to, existing or potential end-customers with international operations. Any decreased use of our solutions or limitation on our ability to develop, export to, import into, or sell our solutions in international markets would likely adversely affect our business, financial condition, results of operations, and cash flows.
There is also significant uncertainty about the future relationship between the United States and various other countries, most significantly China, with respect to trade policies, treaties, government regulations, and tariffs. The current United States presidential administration is continuing to pursue substantial changes to United States foreign trade policy imposed by the previous administration with respect to China, Mexico, and other countries, including the possibility of imposing greater restrictions on international trade, restrictions on sales and technology transfers to certain Chinese corporations, and continued increased tariffs on goods imported into the United States. Given the relatively fluid regulatory environment in China and the United States and uncertainty regarding how the United States or foreign governments will act with respect to tariffs, international trade agreements and policies, a trade war, further governmental action related to tariffs or international trade policies, or additional tax or other regulatory changes in the future could occur and could directly and adversely impact our financial results and results of operations.
Failure to comply with the U.S. Foreign Corrupt Practices Act, other applicable anti-corruption and anti-bribery laws, and applicable anti-money-laundering laws could subject us to penalties and other adverse consequences.
We currently conduct a substantial portion of our operations and sell our products and services in numerous countries outside of the United States, including in the APAC, EMEA, and LAR regions. Our global operations are subject to the FCPA, the U.K. Bribery Act 2010, and other anti-corruption, anti-bribery, anti-money laundering, and similar laws in the United States and other countries in which we conduct activities. In addition, other applicable anti-corruption laws prohibit bribery of domestic government officials as well as commercial bribery, which involves the giving or receiving improper payments to or from non-government parties.
While we have implemented policies, internal controls, and other measures reasonably designed to promote compliance with applicable anti-corruption, anti-bribery, and anti-money-laundering laws and regulations, our employees, agents, and strategic partners may engage in improper conduct for which we might be held responsible. Any violations of these anti-corruption, anti-bribery laws and anti-money laundering laws and regulations, or even allegations of such violations, can lead to an investigation and/or enforcement action, which could disrupt our operations, involve significant management distraction, and lead to significant costs and expenses, including legal fees. If we, or our employees, agents, or strategic partners acting on our behalf, are found to have engaged in practices that violate these laws and regulations, we could suffer severe fines and penalties, profit disgorgement, injunctions on future conduct, securities litigation, bans on transacting government business, and other consequences that may have a material adverse effect on our business, financial condition, results of operations, and cash flows.
35
In addition, our brand and reputation, our sales activities, or the value of our business could be adversely affected if we become the subject of any negative publicity related to actual or potential violations of anti-corruption, anti-bribery, or anti-money-laundering laws and regulations.
If we fail to comply with environmental requirements, our business, financial condition, results of operations, cash flows, and reputation could be adversely affected.
Our operations and the sale of our solutions are subject to various federal, state, local, and foreign environmental and safety regulations, including laws adopted by the E.U., such as the Waste Electrical and Electronic Equipment Directive (“WEEE Directive”), and the Restriction of the Use of Certain Hazardous Substances in Electrical and Electronic Equipment Directive (“E.U. RoHS Directive”), of certain metals from global hot spots. The WEEE Directive requires electronic goods producers to be responsible for marking, collection, recycling, and treatment of such products. Changes in the WEEE Directive of the interpretation thereof may cause us to incur additional costs or meet additional regulatory requirements, which could be material. Similar laws and regulations have been passed or are pending in China, South Korea, Norway, and Japan and may be enacted in other regions, including in the United States, and we are, or may in the future be, subject to these laws and regulations.
The E.U. RoHS Directive and similar laws of other jurisdictions limit the content of certain hazardous materials such as lead, mercury, and cadmium in the manufacture of electrical equipment, including our products. Currently, our products comply with the E.U. RoHS Directive requirements. However, if there are changes to this or other laws, or to their interpretation, or if new similar laws are passed in other jurisdictions, we may be required to reengineer our products or to use different components to comply with these regulations. This reengineering or component substitution could result in substantial costs to us or disrupt our operations or logistics.
We are also subject to environmental laws and regulations governing the management of hazardous materials, which we use in small quantities in our engineering labs. Our failure to comply with past, present, and future environmental and safety laws could result in increased costs, reduced sales of our products, substantial product inventory write-offs, reputational damage, penalties, third-party property damage, remediation costs, and other sanctions, any of which could harm our business, financial condition, results of operations, and cash flows. To date, our expenditures for environmental compliance have not had a material impact on our results of operations or cash flows, and although we cannot predict the future impact of such laws or regulations, they will likely result in additional costs and may increase penalties associated with violations or require us to change the content of our products or how they are manufactured, which could have a material adverse effect on our business, financial condition, results of operations, and cash flows. We also expect that our business will be affected by new environmental laws and regulations on an ongoing basis, which may be more stringent, imposing greater compliance costs and increasing risks and penalties associated with violations which could harm our business.
General Business Risks
If we are unable to attract, train, motivate, and retain senior management and other qualified personnel, our business could suffer.
Our success depends in large part on our ability to attract and retain senior management personnel, as well as technically qualified and highly skilled sales, consulting, technical, finance, and marketing personnel. It could be difficult, time consuming, and expensive to identify, recruit, and onboard any key management member or other critical personnel. Competition for highly skilled personnel is often intense, particularly in the markets in which we operate including Silicon Valley. If we are unable to attract and retain qualified individuals, our ability to compete in the markets for our products could be adversely affected, which would have a negative impact on our business and financial results. Our competitors may be successful in recruiting and hiring members of our management team or other key employees, including key employees obtained through our acquisitions, and it may be difficult for us to find suitable replacements on a timely basis, on competitive terms or at all.
Changes in management or other critical personnel may be disruptive to our business and might also result in our loss of unique skills, loss of knowledge about our business, and may result in the departure of other existing employees, customers or partners. We have experienced recent turnover in our senior management team, and further turnover in the future could adversely affect our business.
We operate in an industry with an overall shortage of skilled and experienced talent that generally experiences high employee attrition. We have experienced significant turnover over the last few years and expect that may continue. The loss of one or more of our key employees could seriously harm our business. If we are unable to attract, integrate, or retain the qualified and highly skilled personnel required to fulfill our current or future needs, our business, financial condition, results of operations, and cash flows could be harmed.
36
Effective succession planning is also important to the long-term success of our business. If we fail to ensure effective transfer of knowledge and smooth transitions involving key employees could hinder our strategic planning and execution. The loss of senior management or any ineffective transitions in management, especially in our sales organization, could significantly delay or prevent the achievement of our development and strategic objectives, which could adversely affect our business, financial condition, results of operations, and cash flows.
We may become involved in litigation, investigations, and regulatory inquiries and proceedings that could negatively affect us and our reputation.
From time to time, we are involved in various legal, administrative, and regulatory proceedings, claims, demands, and investigations relating to our business, which may include claims with respect to commercial, product liability, intellectual property, data privacy, consumer protection, breach of contract, employment, class action, whistleblower, and other matters. In the ordinary course of business, we also receive inquiries from and have discussions with government entities regarding the compliance of our contracting and sales practices with laws and regulations. Such matters can be costly and time consuming and divert the attention of our management and key personnel from our business operations. We have been and are currently, and expect to continue to be, subject to third-party intellectual property infringement claims by entities that do not have operating businesses of their own and therefore limit our ability to seek counterclaims for damages and injunctive relief. Plaintiffs may seek, and we may become subject to, preliminary or provisional rulings in the course of any such litigation, including potential preliminary injunctions requiring us to cease some or all of our operations. Similarly, if any litigation to which we are a party is resolved adversely, we may be subject to an unfavorable judgment that may not be reversed upon appeal. Any claims or litigation could cause us to incur significant expenses and, if successfully asserted against us, could require that we pay substantial damages (including, for example, treble damages if we are found to have willfully infringed patents and increased statutory damages if we are found to have willfully infringed copyrights), pay ongoing royalty payments, delay or prevent us from offering our products or services, or require that we comply with other unfavorable terms. In addition, we might be required to seek a license for the use of such intellectual property, which may not be available on commercially reasonable terms or at all. We may also decide to settle such matters on terms that are unfavorable to us.
Our business is subject to the risks of product defects, warranty claims, product returns, and product liability.
Our solutions are highly complex and may contain design defects or errors that are not detected before their commercial release, particularly when first introduced or as new versions or upgrades are released. Despite testing by us and by current and potential customers, design defects or errors may not be found until after commencement of commercial shipments, resulting in customer dissatisfaction and loss of or delay in market acceptance and sales opportunities. These errors and quality problems could also cause us to incur significant repair or replacement costs, divert the attention of our engineering personnel from our product development efforts, and cause significant customer relations problems. We may also incur significant costs in connection with a product recall and any related indemnification obligations. We have experienced errors or quality problems in the past in connection with solutions and enhancements and expect that errors or quality problems will be found from time to time in the future. Any of these errors or other quality problems could adversely affect our results of operations.
Historically, the amount of warranty claims we have received has not been significant, but there is no guarantee that claims will not be significant in the future. Any errors, defects, or other problems with our products could negatively impact our customers and result in financial or other losses. While we typically seek by contract to limit our exposure to damages, liability limitation provisions in our standard terms and conditions of sale, and those of our channel partners, may not be enforceable under some circumstances or may not fully or effectively protect us from customer claims and related liabilities and costs, including indemnification obligations under our agreements with channel partners or customers. The sale and support of our solutions also entail the risk of product liability claims. In addition, even claims that ultimately are unsuccessful could require us to incur costs in connection with litigation and divert management’s time and other resources, and could seriously harm the reputation of our business and solutions.
We may be unable to raise additional capital on acceptable terms, or at all.
We believe that our available cash and cash equivalents generated from our operating activities and unused availability under our Revolving Credit Facility, will be sufficient to meet our near term working and other capital requirements. However, if cash is required for unanticipated needs, including in connection with a proposed acquisition of a company or technology, we may need additional capital. The development and marketing of new solutions and our investment in sales and marketing efforts require a significant commitment of resources. If the markets for our solutions develop at a slower pace than anticipated, we could be required to raise additional capital. We cannot guarantee that, should it be required, sufficient debt or equity capital will be available to us under acceptable terms, if at all. If we were unable to raise additional capital when required, our business, financial condition, results of operations, and cash flows could be seriously harmed.
37
Our business, financial condition, results of operations, or cash flows could be significantly hindered by the occurrence of a natural disaster, terrorist attack, pandemic, or other catastrophic event.
Our business operations are susceptible to outages due to fire, floods, unusual weather conditions, power loss, telecommunications failures, terrorist attacks, pandemics, such as the COVID-19 pandemic, and other events beyond our control, and our sales opportunities may also be affected by such events. Natural disasters including tornados, hurricanes, floods and earthquakes may damage the facilities of our customers or those of their suppliers or retailers or their other operations, which could lead to reduced revenue for our customers and thus reduced sales. In addition, a substantial portion of our facilities, including our headquarters, are located in Northern California, an area susceptible to earthquakes. We do not carry earthquake insurance for earthquake-related losses. Despite our implementation of network security measures, our servers are vulnerable to computer viruses, break-ins, and similar disruptions from unauthorized tampering with our computer systems. We may not carry sufficient business interruption insurance to compensate us for losses that may occur as a result of any of these events.
Additionally, our customers may face a number of potential business interruption risks that are beyond our respective control. For example, our customers depend on the continuous availability of our cloud-based offerings. Our cloud-based offerings are vulnerable to damage or interruption from a variety of sources, including damage or interruption caused by telecommunications or computer systems failure, fire, earthquake, power loss, cyberattack, human error, terrorist acts, and war. We use a variety of third-party data centers and do not control their operation. These facilities and networks may experience technical failures and downtime, may fail to distribute appropriate updates, or may fail to meet the increased requirements of a growing customer base, any of which could temporarily or permanently expose our customers’ networks, leaving their networks unprotected against the latest security threats, or, in the case of technical failures and downtime of a customer’s security operation center, all security threats. Depending upon how customers have configured their use of our products and services, network downtime within our data centers may also prevent certain customers from being able to access the Internet during the period of such network downtime.
To the extent that such events disrupt our business or the business of our current or prospective customers, or adversely impact our reputation, such events could adversely affect our business, financial condition, results of operations, and cash flows.
Risks Related to Our Indebtedness
Our substantial leverage could adversely affect our financial condition.
As of December 25, 2021, our total debt outstanding under our Senior Secured Credit Facilities was approximately $2,935 million and additional unused borrowing capacity under our Revolving Credit Facility was approximately $660 million.
Our high degree of leverage could have important consequences, including:
Borrowings under our Senior Secured Credit Facilities are at variable rates of interest and expose us to interest rate risk. If interest rates increase, our debt service obligations may increase even though the amount borrowed remains the same, and our net income and cash flows, including cash available for servicing our indebtedness, will correspondingly decrease.
38
Restrictions imposed by our outstanding indebtedness and any future indebtedness may limit our ability to operate our business and to take certain actions.
The terms of our outstanding indebtedness restrict us from engaging in specified types of transactions. These covenants restrict our ability to:
In addition, our First Lien Credit Agreement includes a financial covenant which requires that, at the end of each fiscal quarter, for so long as the aggregate principal amount of borrowings under the Revolving Credit Facility exceeds 35% of the aggregate commitments under the Revolving Credit Facility, our first lien net leverage ratio cannot exceed 6.30 to 1.00. Our ability to comply with this financial covenant can be affected by events beyond our control, and we may not be able to satisfy it. As a result of these restrictions, we may be:
Our Senior Secured Credit Facilities also contain numerous affirmative covenants that will remain in effect as long as our Senior Secured Credit Facilities remain outstanding. We are also required to make mandatory prepayments of the obligations under our Senior Secured Credit Facilities in certain circumstances, including upon certain asset sales or receipt of certain insurance proceeds or condemnation awards, upon certain issuances of debt, and, annually, with a portion of our excess cash flow.
We cannot guarantee that we will be able to maintain compliance with these covenants or, if we fail to do so, that we will be able to obtain waivers from the lenders or investors and/or amend the covenants.
A breach of any of the covenants in the credit agreements governing our Senior Secured Credit Facilities could result in an event of default, which, if not cured or waived, could trigger acceleration of our indebtedness and an increase in the interest rates applicable to such indebtedness, and may result in the acceleration of or default under any other debt we may incur in the future to which a cross-acceleration or cross-default provision applies. The acceleration of the indebtedness under our Senior Secured Credit Facilities or under any other indebtedness could have a material adverse effect on our business, results of operations, and financial condition. In the event of any default under our existing or future credit facilities, the applicable lenders could elect to terminate borrowing commitments and declare all borrowings and loans outstanding, together with accrued and unpaid interest and any fees and other obligations, to be due and payable. In addition, we have granted a security interest in a significant portion of our assets to secure our obligations under our Senior Secured Credit Facilities. During the existence of an event of default under our Senior Secured Credit Facilities, the applicable lenders could exercise their rights and remedies thereunder, including by way of initiating foreclosure proceedings against any assets constituting collateral for our obligations under the Senior Secured Credit Facilities.
39
Despite our level of indebtedness, we and our subsidiaries may still be able to incur substantially more debt, including off-balance sheet financing, contractual obligations, and general and commercial liabilities. This could further exacerbate the risks to our financial condition described above.
We and our subsidiaries may be able to incur significant additional indebtedness in the future, including additional tranches of term loans and/or term loan increases, increases to our revolving commitments and/or additional revolving credit facilities as well as off-balance sheet financings, contractual obligations, and general and commercial liabilities. Although the terms of Senior Secured Credit Facilities contain restrictions on the incurrence of additional indebtedness, such restrictions are subject to a number of significant exceptions and qualifications and any additional indebtedness incurred in compliance with such restrictions could be substantial. These restrictions also will not prevent us from incurring obligations that do not constitute indebtedness. If we and our subsidiaries incur significant additional indebtedness or other obligations, the related risks that we face could increase.
We may be adversely affected by the phase-out of, or changes in the method of determining, the London Interbank Offered Rate (“LIBOR”) or the Euro Interbank Offered Rate (“EURIBOR”), or the replacement of LIBOR and/or EURIBOR with different reference rates.
LIBOR is the basic rate of interest used in lending between banks on the London interbank market and is widely used as a reference for setting the interest rate on U.S. dollar-denominated loans globally. EURIBOR is a basic rate of interest used in lending between Eurozone banks and is widely used as a reference for setting the interest rate on Euro-denominated loans globally. Our Senior Secured Credit Facilities use LIBOR and EURIBOR as reference rates such that the interest due to our creditors under those facilities is calculated using LIBOR or EURIBOR, as applicable.
On July 27, 2017, the U.K.’s Financial Conduct Authority (the authority that administers LIBOR) announced that it intends to phase out LIBOR by the end of 2021, and subsequently extended the phase-out period until June 2023. It is unclear whether new methods of calculating LIBOR will be established such that it continues to exist after 2023, or if alternative rates or benchmarks will be adopted. Changes in the method of calculating LIBOR, or the replacement of LIBOR with an alternative rate or benchmark, may adversely affect interest rates and result in higher borrowing costs. This could materially and adversely affect our results of operations, cash flows, and liquidity. We cannot predict the effect of the potential changes to LIBOR or the establishment and use of alternative rates or benchmarks. We may need to renegotiate our Senior Secured Credit Facilities or incur other indebtedness, and changes in the method of calculating LIBOR, or the use of an alternative rate or benchmark, may negatively impact the terms of such renegotiated Senior Secured Credit Facilities or such other indebtedness. If changes are made to the method of calculating LIBOR or LIBOR ceases to exist, we may need to amend certain contracts and cannot predict what alternative rate or benchmark would be negotiated. This may result in an increase to our interest expense.
The European Money Markets Institute (the authority that administers EURIBOR) has undertaken a number of reforms in response to the EU Benchmark Regulation, which was first published in June 2016 and requires only benchmarks published by “authorized administrators” to be used in new financial contracts beginning on January 1, 2022. It is unclear whether new methods of calculating EURIBOR will be established such that it continues to exist after 2021, or if alternative rates or benchmarks will be adopted. Changes in the method of calculating EURIBOR, or the replacement of EURIBOR with an alternative rate or benchmark, may adversely affect interest rates and result in higher borrowing costs. This could materially and adversely affect our results of operations, cash flows, and liquidity. We cannot predict the effect of the potential changes to EURIBOR or the establishment and use of alternative rates or benchmarks. We may need to renegotiate our First Lien Credit Agreement or incur other indebtedness, and changes in the method of calculating EURIBOR, or the use of an alternative rate or benchmark, may negatively impact the terms of such renegotiated First Lien Credit Agreement or such other indebtedness. If changes are made to the method of calculating EURIBOR or EURIBOR ceases to exist, we may need to amend certain contracts and cannot predict what alternative rate or benchmark would be negotiated. This may result in an increase to our interest expense.
We utilize derivative financial instruments to reduce our exposure to market risks from changes in interest rates on our variable rate indebtedness, including our Senior Secured Credit Facilities, and we will be exposed to risks related to counterparty credit worthiness or non-performance of these instruments.
We have entered into interest rate swap instruments to limit our exposure to changes in variable interest rates. While our hedging strategy is designed to minimize the impact of increases in interest rates applicable to our variable rate debt, including our Senior Secured Credit Facilities, there can be no guarantee that our hedging strategy will be effective, and we may experience credit-related losses in some circumstances. See Note 15 to the Consolidated Financial Statements in Part II, Item 8 for more information.
40
Risks Related to Our Organizational Structure
Our principal asset is our interest in Foundation Technology Worldwide LLC, and we are dependent upon Foundation Technology Worldwide LLC and its consolidated subsidiaries for our results of operations, cash flows, and distributions.
We are a holding company and have no material assets other than our direct and indirect ownership of the LLC Units. As such, we have no independent means of generating revenue or cash flow, and our ability to pay our taxes and operating expenses, including to satisfy our obligations under the tax receivable agreement, or declare and pay dividends in the future, if any, depend upon the results of operations and cash flows of Foundation Technology Worldwide LLC and its consolidated subsidiaries and distributions we receive from Foundation Technology Worldwide LLC. There can be no assurance that our subsidiaries will generate sufficient cash flow to distribute funds to us or that applicable state law and contractual restrictions will permit such distributions.
We anticipate that Foundation Technology Worldwide LLC will continue to be treated as a partnership (and not as a “publicly traded partnership,” within the meaning of Section 7704(b) of the Code, subject to tax as a corporation) for U.S. federal income tax purposes and, as such, generally will not be subject to any entity-level U.S. federal income tax. Instead, taxable income will be allocated to holders of Foundation Technology Worldwide LLC Units. Accordingly, we and our subsidiaries will be required to pay income taxes on our allocable share of any net taxable income of Foundation Technology Worldwide LLC. Further, Foundation Technology Worldwide LLC and its subsidiaries may, absent an election to the contrary, be subject to material liabilities pursuant to partnership audit rules enacted pursuant to the Bipartisan Budget Act of 2015 and related guidance if, for example, its calculations of taxable income are incorrect. Further, we are responsible for the unpaid tax liabilities of the corporate entities we acquired as part of the Reorganization Transactions (as defined herein), including for the taxable year (or portion thereof) of such entities ending on the date of our initial public offering (the “IPO”). To the extent that we need funds and Foundation Technology Worldwide LLC and its subsidiaries are restricted from making such distributions, under applicable law or regulation, or as a result of covenants in the credit agreements of Foundation Technology Worldwide LLC and its subsidiaries, we may not be able to obtain such funds on terms acceptable to us or at all and as a result could suffer an adverse effect on our liquidity and financial condition.
We are required to pay certain Continuing Owners and certain Management Owners for certain tax benefits we may realize or are deemed to realize in accordance with the tax receivable agreement between us and such Continuing Owners and Management Owners, and we expect that the payments we will be required to make will be substantial.
The contribution by certain Continuing Owners and certain Management Owners to McAfee Corp. of certain corporate entities in connection with the Reorganization Transactions and future exchanges of LLC Units for cash or, at our option, for shares of our Class A common stock have produced and are expected to produce or otherwise deliver to us favorable tax attributes that can reduce our taxable income. We are a party to a tax receivable agreement, under which generally we are required to pay to certain of our Continuing Owners and certain Management Owners (collectively, the “TRA Beneficiaries”) 85% of the applicable cash savings, if any, in U.S. federal, state, and local income tax that we actually realize or, in certain circumstances, are deemed to realize as a result of (i) all or a portion of McAfee Corp.’s allocable share of existing tax basis in the assets of Foundation Technology Worldwide LLC (and its subsidiaries) acquired in connection with the Reorganization Transactions, (ii) increases in McAfee Corp.’s allocable share of existing tax basis in the assets of Foundation Technology Worldwide LLC (and its subsidiaries) and tax basis adjustments in the assets of Foundation Technology Worldwide LLC (and its subsidiaries) as a result of sales or exchanges of LLC Units, (iii) certain tax attributes of the corporations McAfee Corp. acquired in connection with the Reorganization Transactions (including their allocable share of existing tax basis in the assets of Foundation Technology Worldwide LLC (and its subsidiaries)), and (iv) certain other tax benefits related to entering into the tax receivable agreement, including tax benefits attributable to payments under the tax receivable agreement. We generally will retain the benefit of the remaining 15% of the applicable tax savings.
The payment obligations under the tax receivable agreement are obligations of McAfee Corp., and we expect that the payments we will be required to make under the tax receivable agreement will be substantial. Potential future reductions in tax payments for us and tax receivable agreement payments by us will be determined in part by reference to the market value of our Class A common stock at the time of the sale and the prevailing tax rates applicable to us over the life of the tax receivable agreement and will be dependent on us generating sufficient future taxable income to realize the benefit. Payments under the tax receivable agreement are not conditioned on the TRA Beneficiaries’ ownership of our shares.
41
The actual increase in tax basis, as well as the amount and timing of any payments under the tax receivable agreement, will vary depending upon a number of factors, including the timing of sales by the Continuing Owners and participating Management Owners, the price of our Class A common stock at the time of the sales, whether such sales are taxable, the amount and timing of the taxable income we generate in the future, the tax rates then applicable to us, and the portions of our payments under the tax receivable agreement constituting imputed interest. Payments under the tax receivable agreement are expected to give rise to certain additional tax benefits attributable to either further increases in basis or in the form of deductions for imputed interest. Any such benefits that we are deemed to realize under the terms of the tax receivable agreement are covered by the tax receivable agreement and will increase the amounts due thereunder. The tax receivable agreement provides that interest, at a rate equal to one-year LIBOR (or if LIBOR ceases to be published, a replacement rate with similar characteristics) plus 1%, will accrue from the due date (without extensions) of the tax return to which the applicable tax benefits relate to the date of payment specified by the tax receivable agreement. In addition, where we fail to make payment by the date so specified, the tax receivable agreement generally provides for interest to accrue on the unpaid amount from the date so specified until the date of actual payment, at a rate equal to one-year LIBOR (or if LIBOR ceases to be published, a replacement rate with similar characteristics) plus 5%, except under certain circumstances specified in the tax receivable agreement where we are unable to make payment by such date, in which case interest will accrue at a rate equal to one-year LIBOR (or if LIBOR ceases to be published, a replacement rate with similar characteristics) plus 1%.
Payments under the tax receivable agreement will be based in part on our tax reporting positions. We will not be reimbursed for any payments previously made under the tax receivable agreement if such basis increases or other attributes or benefits are subsequently disallowed by a taxing authority. As a result, in certain circumstances, the payments we are required to make under the tax receivable agreement could exceed the benefits that we actually realize in respect of the attributes in respect of which the tax receivable agreement required us to make payment.
In addition, the tax receivable agreement provides that in the case of a change of control of McAfee Corp. (as defined therein) or a material breach of our obligations (that is not timely cured) under the tax receivable agreement, or if, at any time, we elect an early termination of the tax receivable agreement, our payment obligations under the tax receivable agreement will accelerate and may significantly exceed the actual benefits we realize in respect of the tax attributes subject to the tax receivable agreement. We will be required to make a payment to the TRA Beneficiaries covered by such termination in an amount equal to the present value of future payments (calculated using a discount rate equal to the lesser of (i) 6.5% per annum and (ii) one-year LIBOR (or if LIBOR ceases to be published, a replacement rate with similar characteristics) plus 1%, which may differ from our, or a potential acquirer’s, then-current cost of capital) under the tax receivable agreement, which payment would be based on certain assumptions, including those relating to our future taxable income. In certain cases, a sale or other disposition of a substantial portion of assets of Foundation Technology Worldwide LLC will be treated as a change of control transaction. In these situations, our obligations under the tax receivable agreement could have a substantial negative impact on our, or a potential acquirer’s, liquidity and could have the effect of delaying, deferring, modifying, or preventing certain mergers, asset sales, other forms of business combinations, or other changes of control. These provisions of the tax receivable agreement may result in situations where the TRA Beneficiaries have interests that differ from or are in addition to those of our other stockholders. In addition, we could be required to make payments under the tax receivable agreement that are substantial, significantly in advance of any potential actual realization of such further tax benefits, and in excess of our, or a potential acquirer’s, actual cash savings in income tax.
Finally, because we are a holding company with no operations of our own, our ability to make payments under the tax receivable agreement is dependent on the ability of our subsidiaries to make distributions to us. The First Lien Credit Agreement restricts the ability of our subsidiaries to make distributions to us, which could affect our ability to make payments under the tax receivable agreement. To the extent that we are unable to make payments under the tax receivable agreement as a result of restrictions in the First Lien Credit Agreement, such payments will be deferred and will accrue interest until paid, which could negatively impact our results of operations and could also affect our liquidity in periods in which such payments are made.
In certain circumstances, under its limited liability company agreement, Foundation Technology Worldwide LLC will be required to make tax distributions to us, the Continuing Owners and certain Management Owners and the distributions that Foundation Technology Worldwide LLC will be required to make may be substantial.
Funds used by Foundation Technology Worldwide LLC to satisfy its tax distribution obligations to the Continuing Owners and certain Management Owners will not be available for reinvestment in our business. Moreover, the tax distributions that Foundation Technology Worldwide LLC will be required to make may be substantial, and will likely exceed (as a percentage of Foundation Technology Worldwide LLC’s net income) the overall effective tax rate applicable to a similarly situated corporate taxpayer.
42
As a result of potential differences in the amount of net taxable income allocable to us and to the Continuing Owners and certain Management Owners, as well as the use of an assumed tax rate in calculating Foundation Technology Worldwide LLC’s tax distribution obligations to the Continuing Owners and the Management Owners, we may receive distributions significantly in excess of our tax liabilities and obligations to make payments under the tax receivable agreement. To the extent, as currently expected, we do not distribute such cash balances as dividends on shares of our Class A common stock and instead, for example, hold such cash balances or lend them to Foundation Technology Worldwide LLC, the Continuing Owners would benefit from any value attributable to such accumulated cash balances as a result of their ownership of Class A common stock following an exchange of their LLC Units for such Class A common stock. Our board of directors, in its sole discretion, will make any determination from time to time with respect to the use of any such excess cash so accumulated, which may include, among other uses, to acquire additional newly issued LLC Units from Foundation Technology Worldwide LLC at a per unit price determined by reference to the market value of the Class A common stock; to pay dividends, which may include special dividends, on its Class A common stock; to fund repurchases of its Class A common stock; to make payments under the tax receivable agreement; or any combination of the foregoing. We will have no obligation to distribute such cash (or other available cash other than any declared dividend) to our stockholders.
Our organizational structure, including the tax receivable agreement, confers certain benefits upon certain Continuing Owners and certain Management Owners, which benefits are not conferred on Class A common stockholders generally.
Our organizational structure, including the tax receivable agreement, confers certain benefits upon certain Continuing Owners and certain Management Owners, which benefits are not conferred on the holders of shares of our Class A common stock generally. In particular, we entered into the tax receivable agreement with Foundation Technology Worldwide LLC and the TRA Beneficiaries, which provides for the payment by us to the TRA Beneficiaries of 85% of the amount of tax benefits, if any, that we actually realize, or in some circumstances are deemed to realize, as a result of (i) all or a portion of McAfee Corp.’s allocable share of existing tax basis in the assets of Foundation Technology Worldwide LLC (and its subsidiaries) acquired in connection with the Reorganization Transactions, (ii) increases in McAfee Corp.’s allocable share of existing tax basis in the assets of Foundation Technology Worldwide LLC (and its subsidiaries) and tax basis adjustments in the assets of Foundation Technology Worldwide LLC (and its subsidiaries) as a result of sales or exchanges of LLC Units, (iii) certain tax attributes of the corporations McAfee Corp. acquired in connection with the Reorganization Transactions (including their allocable share of existing tax basis in the assets of Foundation Technology Worldwide LLC (and its subsidiaries)), and (iv) certain other tax benefits related to entering into the tax receivable agreement, including tax benefits attributable to payments under the tax receivable agreement. Although we will generally retain 15% of the amount of such tax benefits, this and other aspects of our organizational structure may adversely impact the future trading market for the Class A common stock.
We will not be reimbursed for any payments made to the TRA Beneficiaries under the tax receivable agreement in the event that any purported tax benefits are subsequently disallowed by the IRS.
If the IRS or a state or local taxing authority challenges the tax basis adjustments and/or deductions that give rise to payments under the tax receivable agreement and the tax basis adjustments and/or deductions are subsequently disallowed, the recipients of payments under the agreements will not reimburse us for any payments we previously made to them. Any such disallowance would be taken into account in determining future payments under the tax receivable agreement and may, therefore, reduce the amount of any such future payments. Nevertheless, if the claimed tax benefits from the tax basis adjustments and/or deductions are disallowed, our payments under the tax receivable agreement could exceed our actual tax savings, and we may not be able to recoup payments under the tax receivable agreement that were calculated on the assumption that the disallowed tax savings were available.
Unanticipated changes in effective tax rates or adverse outcomes resulting from examination of our income or other tax returns could adversely affect our financial condition and results of operations.
We will be subject to income taxes in the United States, and our domestic and foreign tax liabilities will be subject to the allocation of expenses in differing jurisdictions. Our future effective tax rates could be subject to volatility or adversely affected by a number of factors, including:
43
In addition, we may be subject to audits of our income, sales and other transaction taxes by U.S. federal, state, and local and foreign authorities. Outcomes from these audits could have an adverse effect on our financial condition and results of operations.
Risks Related to Our Class A Common Stock
TPG, Thoma Bravo and Intel will continue to have significant influence over us, including control over decisions that require the approval of stockholders, which could limit your ability to influence the outcome of matters submitted to stockholders for a vote.
We are currently controlled by our TPG, Thoma Bravo and Intel. As long as TPG, Thoma Bravo and Intel collectively own or control at least a majority of our outstanding voting power, they will have the ability to exercise substantial control and significant influence over our management and affairs and all corporate actions requiring stockholder approval, irrespective of how our other stockholders may vote, including the election and removal of directors and the size of our board of directors, any amendment of our certificate of incorporation or bylaws, or the approval of any merger or other significant corporate transaction, including a sale of substantially all of our assets. The concentration of voting power limits your ability to influence corporate matters and, as a result, we may take actions that you do not view as beneficial. As a result, the market price of our Class A common stock could be adversely affected. Even if their collective ownership falls below 50%, TPG, Thoma Bravo and Intel will continue to be able to strongly influence or effectively control our decisions.
Additionally, the interests of TPG, Thoma Bravo and Intel may not align with the interests of our other stockholders. TPG, Thoma Bravo and Intel may, in the ordinary course of their respective businesses, acquire and hold interests in businesses that compete directly or indirectly with us. TPG, Thoma Bravo and Intel each may also pursue acquisition opportunities that may be complementary to our business, and, as a result, those acquisition opportunities may not be available to us.
Certain of our directors have relationships with TPG, Thoma Bravo and Intel, which may cause conflicts of interest with respect to our business.
Three of our seven directors are affiliated with TPG, Thoma Bravo and Intel. Our directors who are affiliated with TPG, Thoma Bravo or Intel have fiduciary duties to us and, in addition, have duties to TPG, Thoma Bravo and Intel. As a result, these directors may face real or apparent conflicts of interest with respect to matters affecting both us and TPG, Thoma Bravo and Intel, whose interests may be adverse to ours in some circumstances.
If we fail to maintain proper and effective internal control over financial reporting in accordance with Section 404 of the Sarbanes-Oxley Act, our ability to produce accurate and timely consolidated financial statements could be impaired, which could harm our results of operations, our ability to operate our business, and investor confidence.
We are required to comply with the SEC’s rules implementing Sections 302 and 404 of the Sarbanes-Oxley Act of 2002 (“Sarbanes-Oxley Act”), which requires management to certify financial and other information in our quarterly and annual reports and provide an annual management report on the effectiveness of our controls over financial reporting. Although we are required to disclose material changes made in our internal controls and procedures on at least a quarterly basis, we are not required to make our first annual assessment of our internal controls over financial reporting pursuant to Section 404 of the Sarbanes-Oxley Act (including an auditor attestation on management’s internal controls report) until our annual report on Form 10-K for the fiscal year ending December 25, 2021.
To comply with the internal controls requirements of being a public company, we may need to undertake various actions as our business or applicable rules and regulations evolve, such as implementing new internal controls and procedures and hiring additional accounting or internal audit staff that have the requisite knowledge of U.S. GAAP. Testing and maintaining internal controls can be costly, challenging, and potentially divert our management’s attention from other matters that are important to the operation of our business.
If we identify any material weaknesses in our internal control over financial reporting, or if we are unable to comply with the demands that will be placed upon us as a public company, including the requirements of Section 404 of the Sarbanes-Oxley Act, in a timely manner, we may be unable to accurately report our consolidated financial results, or report them within the timeframes required by the SEC. We also could become subject to sanctions or investigations by the SEC or other regulatory authorities. In addition, if we are unable to assert that our internal control over financial reporting is effective, or if our independent registered public accounting firm is unable to express an opinion as to the effectiveness of our internal control over financial reporting, when required, investors may lose confidence in the accuracy and completeness of our financial reports, we may face restricted access to the capital markets, and our stock price may be adversely affected.
44
Moreover, no matter how well designed, internal control over financial reporting has inherent limitations. Therefore, internal control over financial reporting determined to be effective can provide only reasonable assurance with respect to financial statement preparation and may not prevent or detect all misstatements. Due to the inherent limitations in all control systems, no evaluation of controls can provide absolute assurance that all control issues and instances of fraud, if any, have been detected. These inherent limitations include the realities that judgments in decision-making can be incorrect, and that breakdowns can occur because of error or mistake. Further, controls can be circumvented by the individual acts of some persons, by collusion of two or more people or by management override of the internal controls. Additionally, projections of any evaluation of effectiveness to future periods are subject to the risk that controls may become inadequate due to changes in conditions, or that the degree of compliance with the policies or procedures may deteriorate. As such, we could lose investor confidence in the accuracy and completeness of our financial reports, which may have a material adverse effect on our reputation and stock price.
We are a “controlled company” under the Exchange’s rules and, as a result, qualify for certain exemptions from certain corporate governance requirements; you will therefore not have the same protections afforded to stockholders of companies that are subject to these governance requirements.
Because TPG, Thoma Bravo and Intel collectively control a majority of the voting power of our outstanding Class A common stock and Class B common stock on a combined basis, we are a “controlled company” within the meaning of the Exchange’s corporate governance standards. Under these rules, a company of which more than 50% of the voting power for the election of directors is held by an individual, group, or another company is a “controlled company” and may elect not to comply with certain corporate governance requirements, including the requirements that, within one year of the date of the listing of our Class A common stock, we have:
Our board of directors is composed of a majority of independent directors. However, we may utilize some or all of the other exemptions applicable to “controlled companies.” Accordingly, for so long as we are a “controlled company,” you will not have the same protections afforded to stockholders of companies that are subject to all of the Exchange’s corporate governance requirements. Our status as a controlled company could make our Class A common stock less attractive to some investors or otherwise harm our stock price.
Our results of operations and the market price of our Class A Common Stock may be volatile.
Our quarterly results of operations are likely to fluctuate in the future. In addition, securities markets worldwide have experienced, and are likely to continue to experience, significant price and volume fluctuations. This market volatility, as well as general economic, market, or political conditions, could subject the market price of our shares to wide price fluctuations regardless of our operating performance. Our results of operations and the trading price of our shares may fluctuate in response to various factors, including:
45
These and other factors, many of which are beyond our control, may cause our results of operations and the market price and demand for our shares to fluctuate substantially. While we believe that results of operations for any particular quarter are not necessarily a meaningful indication of future results, fluctuations in our quarterly results of operations could limit or prevent investors from readily selling their shares and may otherwise negatively affect the market price and liquidity of our shares. In addition, in the past, when the market price of a stock has been volatile, holders of that stock have sometimes instituted securities class action litigation against the company that issued the stock. If any of our stockholders brought a lawsuit against us, we could incur substantial costs defending the lawsuit. Such a lawsuit could also divert the time and attention of our management from our business, which could significantly harm our profitability and reputation.
The Continuing Owners have the right to have their LLC Units exchanged for cash or (at our option) shares of Class A common stock and any disclosure of such exchange or the subsequent sale (or any disclosure of an intent to enter into such an exchange or subsequent sale) of such shares of Class A common stock may cause volatility in our stock price.
As of December 25, 2021, 257 million shares of Class A common stock are issuable upon exchange of LLC Units and MIUs that are held by the Continuing Owners. Under the amended and restated limited liability company agreement of Foundation Technology Worldwide LLC (the “LLC Agreement”), subject to certain restrictions set forth therein, the Continuing Owners are entitled to have their LLC Units exchanged for cash or (at our option) shares of our Class A common stock. The holders of MIUs also have the right, from time to time and subject to certain restrictions, to exchange their MIUs for LLC Units, which will then be immediately redeemed for cash or shares of Class A Common Stock, at the option of the Company, based on the value of such MIUs relative to their applicable distribution threshold.
We cannot predict the timing, size, or disclosure of any future issuances of our Class A common stock resulting from the exchange of LLC Units or the effect, if any, that future issuances, disclosure, if any, or sales of shares of our Class A common stock may have on the market price of our Class A common stock. Sales or distributions of substantial amounts of our Class A common stock, or the perception that such sales or distributions could occur, may cause the market price of our Class A common stock to decline.
We cannot guarantee the timing, amount, or payment of dividends on our Class A common stock.
We intend to fund any future dividends from distributions made by Foundation Technology Worldwide LLC from its available cash generated from operations. If McAfee Corp. decides to pay any other dividend on shares of our Class A common stock in the future, it would likely need to cause Foundation Technology Worldwide LLC to make distributions to McAfee Corp. and its wholly-owned subsidiaries in an amount sufficient to cover such dividend. If Foundation Technology Worldwide LLC makes such distributions to McAfee Corp. and its wholly-owned subsidiaries, the other holders of LLC Units will be entitled to receive pro rata distributions, as well as, in certain cases, the holders of MIUs. The timing, declaration, amount of, and payment of any such dividends will be made at the discretion of McAfee Corp.’s board of directors, subject to applicable laws, and will depend upon many factors, including the amount of the distribution received by McAfee Corp. from Foundation Technology Worldwide LLC, our financial condition, results of operations, capital requirements, contractual restrictions, general business conditions, and other factors that McAfee Corp.’s board of directors may deem relevant. Currently, the provisions of our Senior Secured Credit Facilities place certain limitations on the amount of cash dividends we can pay. Moreover, if as expected McAfee Corp. determines to initially pay a dividend following any quarterly distributions from Foundation Technology Worldwide LLC, there can be no assurance that McAfee Corp. will continue to pay dividends in the same amounts or at all thereafter. As a result, we cannot guarantee the timing, amount or payment of dividends on our Class A common stock.
46
A credit ratings downgrade or other negative action by a credit rating organization could adversely affect the trading price of the shares of our Class A common stock.
Credit rating agencies continually revise their ratings for companies they follow. The condition of the financial and credit markets and prevailing interest rates have fluctuated in the past and are likely to fluctuate in the future. In addition, developments in our business and operations could lead to a ratings downgrade for us or our subsidiaries. Any such fluctuation in the rating of us or our subsidiaries may impact our ability to access debt markets in the future or increase our cost of future debt which could have a material adverse effect on our operations, and financial condition, which in return may adversely affect the trading price of shares of our Class A common stock.
Provisions of our corporate governance documents could make an acquisition of our Company more difficult and may prevent attempts by our stockholders to replace or remove our current management, even if beneficial to our stockholders.
In addition to TPG’s, Thoma Bravo’s and Intel’s beneficial ownership of a controlling percentage of our common stock, our certificate of incorporation and bylaws, and the Delaware General Corporation Law (the “DGCL”) contain provisions that could make it more difficult for a third party to acquire us, even if doing so might be beneficial to our stockholders. These provisions include a classified board of directors and the ability of our board of directors to issue preferred stock without stockholder approval that could be used to dilute a potential acquiror. In addition, these provisions may frustrate or prevent any attempts by our stockholders to replace or remove our current management by making it more difficult for stockholders to replace members of our board of directors. Because our board of directors is responsible for appointing the members of our management team, these provisions could in turn affect any attempt to replace current members of our management team. As a result, you may lose your ability to sell your stock for a price in excess of the prevailing market price due to these protective measures, and efforts by stockholders to change the direction or management of the Company may be unsuccessful.
Our certificate of incorporation designates courts in the State of Delaware as the sole and exclusive forum for certain types of actions and proceedings that may be initiated by our stockholders, and also provides that the federal district courts will be the exclusive forum for resolving any complaint asserting a cause of action arising under the Securities Act, each of which could limit our stockholders’ ability to choose the judicial forum for disputes with us or our directors, officers, stockholders, or employees.
Our certificate of incorporation provides that, subject to limited exceptions, the Court of Chancery of the State of Delaware will be the sole and exclusive forum for:
Our certificate of incorporation also provides that the federal district courts of the United States of America will be the exclusive forum for the resolution of any complaint asserting a cause of action against us or any of our directors, officers, employees or agents and arising under the Securities Act. However, Section 22 of the Securities Act provides that federal and state courts have concurrent jurisdiction over lawsuits brought the Securities Act or the rules and regulations thereunder. To the extent the exclusive forum provision restricts the courts in which claims arising under the Securities Act may be brought, there is uncertainty as to whether a court would enforce such a provision. We note that investors cannot waive compliance with the federal securities laws and the rules and regulations thereunder. This provision does not apply to claims brought under the Exchange Act.
Any person or entity purchasing or otherwise acquiring any interest in shares of our capital stock shall be deemed to have notice of and to have consented to these provisions. These provisions may limit a stockholder’s ability to bring a claim in a judicial forum that it finds favorable for disputes with us or our directors, officers or other employees, which may discourage such lawsuits against us and our directors, officers and employees. Alternatively, if a court were to find these provisions of our certificate of incorporation inapplicable to, or unenforceable in respect of, one or more of the specified types of actions or proceedings, we may incur additional costs associated with resolving such matters in other jurisdictions, which could adversely affect our business and financial condition.
47
Our certificate of incorporation contains a provision renouncing our interest and expectancy in certain corporate opportunities, which could adversely impact our business.
Each of TPG, Intel and its affiliates, and Thoma Bravo, and the members of our board of directors who are affiliated with them, by the terms of our certificate of incorporation, will not be required to offer us any corporate opportunity of which they become aware and can take any such corporate opportunity for themselves or offer it to other companies in which they have an investment. We, by the terms of our certificate of incorporation, have expressly renounced any interest or expectancy in any such corporate opportunity to the extent permitted under applicable law, even if the opportunity is one that we or our subsidiaries might reasonably have pursued or had the ability or desire to pursue if granted the opportunity to do so. Our certificate of incorporation is not able to be amended to eliminate our renunciation of any such corporate opportunity arising prior to the date of any such amendment.
TPG and Thoma Bravo are in the business of making investments in companies and any of TPG, Intel and Thoma Bravo may from time to time acquire and hold interests in businesses that compete directly or indirectly with us. These potential conflicts of interest could have a material adverse effect on our business, financial condition, results of operations or prospects if TPG, Intel and its affiliates, or Thoma Bravo allocate attractive corporate opportunities to themselves or their affiliates instead of to us.
48
Item 1B. Unresolved Staff Comments.
None.
Item 2. Properties.
Our principal office is located in San Jose, California where we lease approximately 85,000 square feet of space under one lease agreement that expires in December 2030. We also lease space for personnel in North America, South America, Europe, and Asia. Refer to Note 6, Leases in Part II, Item 8 of this Annual Report on Form 10-K for more information on our operating leases.
We believe that our current facilities are adequate and that we will be able to find suitable space to accommodate any potential future expansion. We expect to incur additional expenses in connection with any such new or expanded facilities.
Item 3. Legal Proceedings.
From time to time, we are subject to various legal proceedings and claims, either asserted or unasserted, which arise in the ordinary course of business. While the outcome of these matters cannot be predicted with certainty, we do not believe that the outcome of any of these matters, individually or in the aggregate, will have a material adverse effect on our consolidated financial condition, results of operations, or cash flows.
In addition, as previously disclosed, on November 5, 2021, Company entered into the Merger Agreement, as amended, with Parent and Merger Subsidiary, pursuant to which Merger Subsidiary will merge with and into the Company whereupon the separate corporate existence of Merger Subsidiary will cease and the Company will be the surviving corporation in the Merger and will continue as a wholly owned subsidiary of Parent. On December 21, 2021, the Company filed with the SEC its Preliminary Proxy Statement (the “Preliminary Proxy Statement”). On January 4, 2022, the Company filed with the SEC its Definitive Proxy Statement (the “Definitive Proxy Statement”), which was mailed to Company stockholders.
On January 5, 2022, January 11, 2022, and January 21, 2022, the Company received demand letters on behalf of purported shareholders of the Company challenging certain disclosures set forth in the Definitive Proxy Statement (the “Demand Letters”). In addition, two shareholder complaints relating to the Merger were filed in the United States District Court for the Northern District of California, one filed on January 19, 2022 and captioned Coffman v. McAfee Corp. et al., Case No. 5:22-cv-00361, and one filed on January 20, 2022 and captioned Waswick v. McAfee Corp. et al., Case No. 5:22-cv-00395. On January 25, 2022, a shareholder complaint relating to the Merger was filed in the United States District Court for the Eastern District of New York, captioned Sayre v. McAfee Corp. et al., Case No. 1:22-cv-00430. On January 26, 2022, a shareholder complaint relating to the Merger was filed in the United States District Court for the District of Delaware, captioned Kent v. McAfee Corp. et al., Case No. 1:99-mc-09999. On January 28, 2022, a shareholder complaint relating to the Merger was filed in the United States District Court for the Southern District of New York, captioned Finger v. McAfee Corp. et al., Case No. 1:22-cv-00758. Each of the Coffman, Sayre, Kent, and Finger complaints alleges that the Definitive Proxy Statement is false and/or misleading and asserts claims for violations of Section 14(a) and 20(a) of the Exchange Act and SEC Rule 14a-9 against the Company and its directors. The Waswick complaint alleges that the Preliminary Proxy Statement is false and/or misleading and asserts claims for violations of Section 14(a) and 20(a) of the Exchange Act and SEC Rule 14a-9 against the Company and its directors. Each of these complaints (collectively, the “Complaints”) purports to seek, among other things, injunctive relief preventing the Merger, damages, and an award of plaintiffs’ costs and expenses, including reasonable attorneys’ and expert fees. The Company believes that the claims asserted in the Demand Letters and Complaints are without merit.
Item 4. Mine Safety Disclosures.
None.
49
PART II
Item 5. Market for Registrant’s Common Equity, Related Stockholder Matters and Issuer Purchases of Equity Securities.
Market Information and Holders of Record
On October 22, 2020, our Class A common stock, $0.001 par value per share, began trading on the NASDAQ Stock Market under the symbol "MCFE." Prior to that time, there was no public market for our stock. As of December 25, 2021, there were approximately 272 holders of record of our Class A common stock and 24 holders of record for our Cass B common stock. The number of holders of record presented here does not include persons whose stock is held in nominee or “street name” accounts through brokers, banks and intermediaries. Our Class B common stock is neither listed nor traded on any stock exchange, nor is there an established public trading market for this class of common stock.
Dividend
Foundation Technology Worldwide LLC (“FTW”) paid a cash distribution to its members for each of the first three quarters of fiscal 2021 at an aggregate annual rate of approximately $200 million. McAfee Corp. received a portion of such distributions through the LLC Units it holds directly or indirectly through its wholly-owned subsidiaries on the record date such distribution were declared by FTW. McAfee Corp. used a portion of its share of the cash distributions declared by FTW to declare or pay the dividends noted in the table below during the year ended December 25, 2021. Remaining distributions received by McAfee Corp. were used for corporate taxes and general corporate purposes. Pursuant to the terms of the Merger Agreement, the Company has agreed to suspend its dividend during the term of the Merger Agreement.
Declaration Date |
|
Record Date |
|
Payment Date |
|
Dividend per Share |
|
|
Amount |
|
||
December 9, 2020 |
|
December 24, 2020 |
|
January 7, 2021 |
|
$ |
0.087 |
|
|
$ |
14 |
|
March 11, 2021 |
|
March 26, 2021 |
|
April 9, 2021 |
|
$ |
0.115 |
|
|
$ |
19 |
|
June 10, 2021 |
|
June 25, 2021 |
|
July 9, 2021 |
|
$ |
0.115 |
|
|
$ |
19 |
|
August 3, 2021 |
|
August 13, 2021 |
|
August 27, 2021 |
|
$ |
4.500 |
|
|
$ |
760 |
|
September 13, 2021 |
|
September 24, 2021 |
|
October 8, 2021 |
|
$ |
0.115 |
|
|
$ |
21 |
|
50
Stock Performance Graph
The graph below compares the cumulative total stockholder return on our Class A common stock with the cumulative total return on the S&P 500 Composite Index and the S&P Information Technology Sector Index for the 2 years ended December 25, 2021 assuming the initial investment of $100 in our Class A common stock and in each of the other indices on October 22, 2020 (the date our Class A common stock commenced trading on the Nasdaq Stock Market) and the reinvestment of all dividends. The comparisons in the graph below are based on historical data and are not indicative of, nor intended to forecast the possible future performance of our common stock.
COMPARISON OF TWO-YEAR CUMULATIVE TOTAL RETURN
Among McAfee Corp., the S&P 500 Index
and the S&P Information Technology Sector Index
This performance graph shall not be deemed “filed” for purposes of Section 18 of the Exchange Act or otherwise subject to the liabilities under that Section and shall not be deemed to be incorporated by reference into any filing of McAfee Corp. under the Securities Act or the Exchange Act.
Item 6. Reserved.
51
Item 7. Management’s Discussion and Analysis of Financial Condition and Results of Operations.
Organization
McAfee Corp. (the “Corporation”) was incorporated in Delaware on July 19, 2019. The Corporation was formed for the purpose of completing an initial public offering (the “IPO”) and related transactions in order to carry on the business of FTW and its subsidiaries. On October 21, 2020, the Corporation became the sole managing member and holder of 100% of the voting power of FTW due to the reorganization transactions described below. With respect to the Corporation and the Company, each entity owns nothing other than the respective entities below it in the corporate structure and each entity has no other material operations, assets, or liabilities. The Reorganization Transactions were accounted for as a reorganization of entities under common control. As a result, the financial statements for periods prior to the IPO and the Reorganization Transactions are the financial statements of FTW as the predecessor to the Corporation for accounting and reporting purposes. See Note 1 to the Consolidated Financial Statements in Item 8 for a detailed discussion of the Reorganization Transactions, as defined in that note, and the IPO.
The Reorganization Transactions
Reorganization
In connection with the closing of the IPO, the following Reorganization Transactions were consummated:
Organization of Information
In Item 7, we discuss the year ended December 25, 2021 results and compare the year ended December 25, 2021 results to the year ended December 26, 2020 results. Discussions of the year ended December 26, 2020 results and comparisons of the year ended December 26, 2020 results to the year ended December 28, 2019 results can be found in “Management’s Discussion and Analysis of Financial Condition and Results of Operations” in the Corporation’s Prospectus dated September 9, 2021 and filed with the SEC on September 10, 2021 pursuant to Rule 424(b)(4) of the Securities Act.
Overview
As a global leader and trusted brand in cybersecurity for over 30 years, McAfee protects millions of consumers with one of the industry’s most comprehensive cybersecurity portfolios. Our award-winning products offer individuals and families protection for their digital lives. We meet the cyber security needs of consumers wherever they are, with solutions for device security, privacy and safe Wi-Fi, online protection, and identity protection, among others. Our mission is to protect all things that matter through leading-edge cybersecurity products.
Our consumer-focused products protect consumers across the digital spectrum providing holistic digital protection of the individual and family wherever they go under our Total Protection and LiveSafe brands. We achieve this by integrating the following solutions and capabilities within our bundled products:
52
Our go-to-market digitally-led omnichannel approach reaches the consumer at crucial moments in their purchase lifecycle including direct to consumer online sales, acquisition through trial pre-loads on PC OEM devices, and other indirect modes via additional partners such as mobile providers, ISPs, electronics retailers, ecommerce sites, and search providers. We have longstanding exclusive partnerships with many of the leading PC OEMs and continue to expand our presence with mobile service providers and ISPs as the demand for mobile security protection increases. Through these relationships, our consumer security software is pre-installed on devices on either a trial basis until conversion to a paid subscription, which is enabled by a tailored renewal process that fits the customer’s journey, or through a live version that can be purchased directly through the OEMs’ website. Our consumer go-to-market channel also consists of partners including some of the largest electronics retailers and ISPs globally.
Agreement and Plan of Merger; Proposed Merger
On November 5, 2021, the Company entered into an Agreement and Plan of Merger (the “Merger Agreement”) with Condor BidCo, Inc., a Delaware corporation (“Parent”), and Condor Merger Sub, Inc., a Delaware corporation and wholly owned subsidiary of Parent (“Merger Subsidiary”), pursuant to which Merger Subsidiary will merge with and into the Company whereupon the separate corporate existence of Merger Subsidiary will cease and the Company will be the surviving corporation in the Merger and will continue as a wholly owned subsidiary of Parent (the “Merger”). Parent has obtained equity financing and debt financing commitments for the purpose of financing the transactions contemplated by the Merger Agreement. Affiliates of funds advised by each of Advent International Corporation, Permira Advisers LLC, Crosspoint Capital Partners L.P., Abu Dhabi Investment Authority, and Canada Pension Plan Investment Board and GIC Private Ltd. have committed to capitalize Parent at the Closing with an aggregate equity contribution equal to $5.2 billion on the terms and subject to the conditions set forth in signed equity commitment letters. On February 3, 2022, Merger Subsidiary received commitments of $5,160 million under a proposed U.S. dollar term loan facility and Euro-equivalent $1,800 million under a proposed Euro term loan facility. On February 17, 2022, Merger Subsidiary closed its offering of $2,020 million 7.375% senior notes due 2030. Under the terms of the Merger Agreement, the Company’s stockholders will receive $26.00 in cash for each share of Class A common stock they hold on the transaction closing date. The transaction’s closing is subject to customary closing conditions, including, among others, approval by the Company’s stockholders, the expiration or early termination of the applicable waiting period under the Hart-Scott-Rodino Antitrust Improvements Act of 1976, as amended (the “HSR Act”), the receipt of other regulatory approvals, and clearance by the Committee on Foreign Investment in the United States. On December 20, 2021 at 11:59 p.m., the waiting period under the HSR Act expired. On February 9, 2022, the Company’s stockholders approved the Merger at a special meeting of stockholders. On February 22, 2022, the Committee on Foreign Investment in the United States closed its review and cleared the transactions contemplated by the Merger Agreement. Pursuant to the terms of the Merger Agreement, the completion of the Merger remains subject to various customary conditions, including (1) the absence of an order, injunction or law prohibiting the Merger, (2) the receipt of antitrust approval in the European Union and Switzerland, (3) the accuracy of each party’s representations and warranties, subject to certain materiality standards set forth in the Merger Agreement, (4) compliance in all material respects with each party’s obligations under the Merger Agreement, and (5) no Company Material Adverse Effect (as defined in the Merger Agreement) having occurred since the date of the Merger Agreement.
Upon completion of the transaction, McAfee common stock will no longer be listed on any public securities exchange.
In connection with the closing of the Merger, the Company, FTW and certain other parties thereto have entered into a Tax Receivable Agreement and LLC Agreement Amendment (the “Amendment”). The Amendment provides for, among other things, (i) the payment of amounts due under the tax receivable agreement currently in effect (the “TRA”) with respect to U.S. federal income tax year 2020 of the Company in accordance with the terms of the TRA up to an aggregate amount of $2 million, which payments shall be paid no later than 10 business days prior to the Closing Date, (ii) the suspension of all other payments under the TRA from and after November 5, 2021 and (iii) the amendment of the TRA, effective as of immediately prior to and contingent upon the occurrence of the Effective Time of the Merger, which shall result in the TRA (and all of the Company’s obligations thereunder, including the obligation to make any of the foregoing suspended payments) terminating immediately prior to the Effective Time of the Merger. For a summary of the transaction, please refer to our Form 8-K filed with the U.S. Securities and Exchange Commission (the “SEC”) on November 8, 2021.
53
Divestiture of Enterprise Business
On March 6, 2021, we entered into a definitive agreement (the “Purchase Agreement”) with a consortium led by Symphony Technology Group (“STG”) under which STG agreed to purchase certain of our Enterprise assets together with certain of our Enterprise liabilities (“Enterprise Business”), representing substantially all of our Enterprise segment, for an all-cash purchase price of $4.0 billion. The divestiture transaction closed on July 27, 2021. The divestiture of our Enterprise Business, represents a strategic shift in our operations that allows us to focus on our Consumer business. As a result of the divestiture, the results of our Enterprise Business were reclassified as discontinued operations in our consolidated statements of operations and excluded from both continuing operations and segment results for all periods presented. Starting in the first quarter of fiscal 2021, we began to operate as one reportable segment as the Enterprise Business comprised substantially all of our Enterprise segment. Results of discontinued operations includes all revenues and expenses directly derived from our Enterprise Business, with the exception of general corporate overhead costs that were previously allocated to our Enterprise segment but have not been allocated to discontinued operations. The Enterprise Business was reclassified as discontinued operations in our consolidated balance sheets. In connection with the divestiture, we recognized a gain of $2.2 billion, net of estimated taxes and transaction costs. See Note 4, Discontinued Operations and Held-for-Sale Assets in Part II, Item 8 of this Annual Report on Form 10-K for additional information about the divestiture of our Enterprise Business.
On August 3, 2021, the Board of Directors of McAfee Corp., using a portion of the proceeds received from the divestiture of Enterprise Business, declared a special one-time cash dividend of $4.50 per share of Class A common stock payable to shareholders of record on August 13, 2021 (the “Special Dividend”). In connection with the declaration of the Special Dividend, the Board of Directors of McAfee Corp., as sole managing member of FTW, authorized FTW to declare a special one-time cash distribution to its members in the aggregate of $2.8 billion (the “Special Distribution”). The Special Distribution resulted in the payment of $1.7 billion to Continuing LLC Owners and $1.1 billion to McAfee Corp. McAfee Corp. used $0.8 billion of its share of the Special Distribution to pay the Special Dividend to participating shareholders on August 27, 2021.
We used a portion of the proceeds from the divestiture to prepay $332 million of 1st Lien USD Term Loan and €563 million of 1st Lien Euro Term Loan in August 2021. In connection with this prepayment, we incurred a loss on extinguishment of debt of $10 million related to recognition of unamortized discount and deferred financing costs. See Note 13 to the consolidated financial statements for further information. We also terminated $150 million of our $250 million notional interest rate swap that had an expiration date of January 29, 2022. See Note 15 to the consolidated financial statements for further information.
Subsequent to the Enterprise Business divestiture, we concluded that a full valuation allowance against the net deferred tax assets of our domestic entities will no longer be required and released $211 million of the $212 million of valuation allowance that existed as of December 26, 2020.
We also expect to realize certain tax benefits subject to our TRA and thus we recognized and recorded an additional TRA liability. As the net deferred tax assets have been recognized as of the date of divestiture of the Enterprise Business, the full liability under the TRA also became probable as of that date. During the year ended December 25, 2021, TRA liability increases of $121 million resulting from post divestiture exchanges of FTW LLC Units for shares of Class A common stock were recorded to Additional paid-in capital on the consolidated balance sheet. TRA liability increases of $313 million resulting from pre-divestiture exchanges and TRA liability decreases of $6 million resulting from unutilized tax attributes were recorded within Other income (expense), net. TRA liability increases of $4 million resulting from divestiture related events were recorded within Income from discontinued operations on the consolidated statement of operations. As of December 25, 2021, we have TRA liabilities of $2 million and $432 million recorded in the consolidated balance sheet within Accounts payable and other accrued liabilities and Tax receivable agreement liability, less current portion, respectively. See Note 14 to the consolidated financial statements for further information and the income tax impact of the Enterprise Business divestiture.
In July 2021, two amendments to the definitive agreement with a consortium led by STG for the purchase of the Enterprise Business were executed. The amendments modified certain provisions for assets and liabilities to be transferred as well as the timing and procedures for transfer of certain assets and employees in foreign jurisdictions in connection with the sale, and clarifying requirements for maintenance of such assets prior to transfer. The amendments also include certain other modifications or clarifications of the purchase agreement. As a result of the amendments, our results of operations for the year ended December 26, 2020 and December 28, 2019 and our December 26, 2020 consolidated balance sheet reflect changes in the assets and liabilities that were determined to be part of discontinued operations as reported in our previously filed Form 8-K, Item 8 for the year ended December 26, 2020. These changes resulted in increases of $8 million to loss from discontinued operations, net of tax, for the year ended December 26, 2020, as compared to the amounts reported in our previously filed Form 8-K, Item 8 for the year ended December 26, 2020. These changes are reflected in the information presented below and all relevant disclosures. See Note 20 to the Consolidated Financial Statements in Part II, Item 8 of this Annual Report on Form 10-K for revised selected quarterly financial data.
Financial Highlights
For the year ended December 25, 2021 compared to the year ended December 26, 2020 we delivered the following:
54
See “Non-GAAP Financial Measures” for a description of adjusted EBITDA, and free cash flow, and a reconciliation of these measures to the nearest financial measure calculated in accordance with GAAP.
COVID-19 Pandemic
The COVID-19 pandemic is having widespread, rapidly evolving, and unpredictable impacts on global society, economies, financial markets, and business practices. Federal, state and foreign governments have implemented measures to contain the virus, including social distancing, travel restrictions, border closures, limitations on public gatherings, work from home, and closure of non-essential businesses. To protect the health and well-being of our employees, partners, and third-party service providers, we have implemented work-from-home requirements, made substantial modifications to employee travel policies, and cancelled or shifted marketing and other corporate events to virtual-only formats for the foreseeable future.
The ultimate duration and extent of the impact from the COVID-19 pandemic depends on future developments that cannot be accurately forecasted at this time. These developments include the severity and transmission rate of the disease, the actions of governments, businesses and individuals in response to the pandemic, the extent and effectiveness of containment actions and vaccines, the impact on economic activity and the impact of these and other factors. We have experienced growth and increased demand for our solutions in recent quarters, which may be due in part to greater demand for devices or our solutions in response to the COVID-19 pandemic. We cannot determine what, if any, portion of our growth in net revenue, the number of our Direct to Consumer Subscribers, or any other measures of our performance during the fiscal 2021 compared to the fiscal 2020 was the result of such responses to the COVID-19 pandemic.
Fiscal Calendar
We maintain a 52- or 53-week fiscal year that ends on the last Saturday in December. The year ending December 25, 2021 is a 52-week year starting on December 27, 2020. The year ended December 26, 2020 is a 52-week year starting on December 29, 2019 and ending on December 26, 2020.
Key Operating Metrics
We monitor the following key metrics to help us evaluate our business, identify trends affecting our business, measure our performance, formulate business plans, and make strategic decisions. We believe the following metrics are useful in evaluating our business, but should not be considered in isolation or as a substitute for GAAP. Certain judgments and estimates are inherent in our processes to calculate these metrics.
We define Core Direct to Consumer Subscribers as active subscribers whose transaction for a subscription is directly with McAfee. These subscribers include those who (i) transact with us directly through McAfee web properties, (ii) are converted during or after the trial period of the McAfee product preinstalled on their new PC purchase, or (iii) are channel led subscribers who are converted to Core Direct to Consumer Subscribers after expiration of their subscription of our product initially purchased through our retail, ecommerce or PC OEM partners.
We define Trailing Twelve Months (“TTM”) Dollar Based Retention – Core Direct to Consumer Subscribers as the annual contract value of Core Direct to Consumer Subscriber subscriptions that were renewed in the trailing twelve months divided by the annual contract value for Core Direct to Consumer Subscribers subscriptions that were up for renewal in the same period. We monitor TTM Dollar Based Retention as an important measure of the value we retain of our existing Core Direct to Consumer Subscriber base and as a measure of the effectiveness of the strategies we deploy to improve those rates over time.
We define Monthly Average Revenue Per Customer (“ARPC”) as monthly subscription net revenue from transactions directly between McAfee and Core Direct to Consumer Subscribers, divided by average Core to Direct Consumer Subscribers from the same period. ARPC can be impacted by price, mix of products, and change between periods in Core Direct to Consumer Subscriber count. We believe that ARPC allows us to understand the value of our solutions to the portion of our subscriber base transacting directly with us.
55
|
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Core Direct to Consumer Subscribers (in millions) |
|
|
20.7 |
|
|
|
18.0 |
|
TTM Dollar Based Retention - Core Direct to Consumer Subscribers |
|
|
99.9 |
% |
|
|
100.0 |
% |
|
|
Year Ended |
|
|||||
|
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Monthly ARPC |
|
$ |
6.02 |
|
|
$ |
6.01 |
|
Non-GAAP Financial Measures
We have included both financial measures compiled in accordance with GAAP and certain non-GAAP financial measures in this Annual Report on Form 10-K for our continuing operations, including adjusted operating income, adjusted operating income margin, adjusted EBITDA, adjusted EBITDA margin, adjusted net income, adjusted net income margin, and free cash flow and ratios based on these financial measures.
Adjusted Operating Income, Adjusted Operating Income Margin, Adjusted EBITDA and Adjusted EBITDA Margin
We regularly monitor adjusted operating income, adjusted operating income margin, adjusted EBITDA, and adjusted EBITDA margin to assess our operating performance. We define adjusted operating income as net income (loss), excluding the impact of amortization of intangible assets, equity-based compensation expense, restructuring and transition charges, interest expense, foreign exchange (gain) loss, net, provision for income tax expense, Tax Receivable Agreement (“TRA”) adjustment, income from Transition Services Agreement (“TSA”), income (loss) from discontinued operations, net of taxes, and other costs that we do not believe are reflective of our ongoing operations. Adjusted operating income margin is calculated as adjusted operating income divided by net revenue. We define adjusted EBITDA as adjusted operating income, excluding the impact of depreciation expense plus certain other non-operating costs. Adjusted EBITDA margin is calculated as adjusted EBITDA divided by net revenue. We believe presenting adjusted operating income, adjusted operating income margin, adjusted EBITDA, and adjusted EBITDA margin provides management and investors consistency and comparability with our past financial performance and facilitates period to period comparisons of operations, as it eliminates the effects of certain variations unrelated to our overall performance. Adjusted operating income, adjusted operating income margin, adjusted EBITDA, and adjusted EBITDA margin have limitations as analytical tools, and you should not consider it in isolation or as a substitute for analysis of our results as reported under GAAP. Some of these limitations are:
Because of these limitations, you should consider adjusted operating income and adjusted EBITDA alongside other financial performance measures, including operating income (loss), net income (loss) and our other GAAP results. In evaluating adjusted operating income, adjusted operating income margin, adjusted EBITDA, and adjusted EBITDA margin, you should be aware that in the future we may incur expenses that are the same as or similar to some of the adjustments in this presentation. Our presentation of adjusted operating income, adjusted operating income margin, adjusted EBITDA, and adjusted EBITDA margin should not be construed as an inference that our future results will be unaffected by the types of items excluded from the calculation of adjusted operating income, adjusted operating income margin, adjusted EBITDA, and adjusted EBITDA margin. Adjusted operating income, adjusted operating income margin, adjusted EBITDA, and adjusted EBITDA margin are not presentations made in accordance with GAAP and the use of these terms vary from other companies in our industry.
56
The following table presents a reconciliation of our adjusted operating income and adjusted EBITDA to our net income for the periods presented:
|
|
Year Ended |
|
|||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Net income (loss) |
|
$ |
2,688 |
|
|
$ |
(289 |
) |
Add: Amortization |
|
|
170 |
|
|
|
251 |
|
Add: Equity-based compensation |
|
|
71 |
|
|
|
113 |
|
Add: Cash in lieu of equity awards(1) |
|
|
1 |
|
|
|
1 |
|
Add: Acquisition and integration costs(2) |
|
|
1 |
|
|
|
8 |
|
Add: Restructuring and transition charges(3) |
|
|
70 |
|
|
|
2 |
|
Add: Management fees(4) |
|
|
— |
|
|
|
28 |
|
Add: Transformation(5) |
|
|
12 |
|
|
|
20 |
|
Add: Executive severance(6) |
|
|
1 |
|
|
|
3 |
|
Add: Interest expense |
|
|
212 |
|
|
|
303 |
|
Add: Foreign exchange loss (gain), net(7) |
|
|
(41 |
) |
|
|
104 |
|
Add: Provision for income tax expense (benefit) |
|
|
(160 |
) |
|
|
5 |
|
Add: TRA adjustment(8) |
|
|
307 |
|
|
|
2 |
|
Less: Income from TSA(9) |
|
|
(18 |
) |
|
|
— |
|
Add: Other (income) expense, net(10) |
|
|
2 |
|
|
|
2 |
|
Less: Loss (income) from discontinued operations, net of taxes |
|
|
(2,441 |
) |
|
|
79 |
|
Adjusted operating income |
|
|
875 |
|
|
|
632 |
|
Add: Depreciation |
|
|
23 |
|
|
|
23 |
|
Less: Other (income) expense |
|
|
1 |
|
|
|
(1 |
) |
Adjusted EBITDA |
|
$ |
899 |
|
|
$ |
654 |
|
Net revenue |
|
$ |
1,920 |
|
|
$ |
1,558 |
|
Net income (loss) margin |
|
|
140.0 |
% |
|
|
(18.5 |
)% |
Adjusted operating income margin |
|
|
45.6 |
% |
|
|
40.6 |
% |
Adjusted EBITDA margin |
|
|
46.8 |
% |
|
|
42.0 |
% |
See “Description of Non-GAAP Adjustments” section for an explanation of adjustments to non-GAAP measures and other items.
57
Adjusted Net Income and Adjusted Net Income Margin
We regularly monitor adjusted net income and adjusted net income margin to assess our operating performance. Adjusted net income assumes all net income (loss) is attributable to McAfee Corp., which assumes the full exchange of all outstanding LLC Units for shares of Class A common stock of McAfee Corp., and is adjusted for the impact of amortization of intangible assets, amortization of debt issuance costs, equity-based compensation expense, restructuring and transition charges, foreign exchange loss (gain), net, TRA adjustment, income from TSA, income (loss) from discontinued operations, net of taxes, and other costs that we do not believe are reflective of our ongoing operations. The adjusted provision for income taxes represents the tax effect on net income, adjusted for all of the listed adjustments, assuming that all consolidated net income was subject to corporate taxation for all periods presented. We have assumed an annual effective tax rate of 22%, which represents our long term expected corporate tax rate excluding discrete and non-recurring tax items. This amount has been recast for periods reported previously.
Adjusted net income margin is calculated as adjusted net income divided by net revenue. Adjusted net income and adjusted net income margin have limitations as analytical tools, and you should not consider it in isolation or as a substitute for analysis of our results as reported under GAAP. Some of these limitations are:
Because of these limitations, you should consider adjusted net income alongside other financial performance measures, including net income (loss) and our other GAAP results. In evaluating adjusted net income and adjusted net income margin, you should be aware that in the future we may incur expenses that are the same as or similar to some of the adjustments in this presentation. Our presentation of adjusted net income and adjusted net income margin should not be construed as an inference that our future results will be unaffected by the types of items excluded from the calculation of adjusted net income and adjusted net income margin. Adjusted net income and adjusted net income margin are not presentations made in accordance with GAAP and the use of these terms vary from other companies in our industry.
The following table presents a reconciliation of our adjusted net income to our net income for the periods presented:
|
|
Year Ended |
|
|||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Net income (loss) |
|
$ |
2,688 |
|
|
$ |
(289 |
) |
Add: Amortization of debt discount and issuance costs |
|
|
23 |
|
|
|
36 |
|
Add: Amortization |
|
|
170 |
|
|
|
251 |
|
Add: Equity-based compensation |
|
|
71 |
|
|
|
113 |
|
Add: Cash in lieu of equity awards(1) |
|
|
1 |
|
|
|
1 |
|
Add: Acquisition and integration costs(2) |
|
|
1 |
|
|
|
8 |
|
Add: Restructuring and transition charges(3) |
|
|
70 |
|
|
|
2 |
|
Add: Management fees(4) |
|
|
— |
|
|
|
28 |
|
Add: Transformation(5) |
|
|
12 |
|
|
|
20 |
|
Add: Executive severance(6) |
|
|
1 |
|
|
|
3 |
|
Add: Foreign exchange loss (gain), net(7) |
|
|
(41 |
) |
|
|
104 |
|
Add: Provision for income taxes expense (benefit) |
|
|
(160 |
) |
|
|
5 |
|
Add: TRA adjustment(8) |
|
|
307 |
|
|
|
2 |
|
Less: Income from TSA(9) |
|
|
(18 |
) |
|
|
— |
|
Add: Other (income) expense, net(10) |
|
|
2 |
|
|
|
2 |
|
Less: Loss (income) from discontinued operations, net of taxes |
|
|
(2,441 |
) |
|
|
79 |
|
Adjusted income before taxes |
|
$ |
686 |
|
|
$ |
365 |
|
Adjusted provision for income taxes(11) |
|
|
151 |
|
|
|
80 |
|
Adjusted net income |
|
$ |
535 |
|
|
$ |
285 |
|
Net revenue |
|
$ |
1,920 |
|
|
$ |
1,558 |
|
Net income (loss) margin |
|
|
140.0 |
% |
|
|
(18.5 |
)% |
Adjusted net income margin |
|
|
27.9 |
% |
|
|
18.3 |
% |
58
See “Description of Non-GAAP Adjustments” section for an explanation of adjustments to non-GAAP measures and other items.
Description of Non-GAAP Adjustments
Below are additional information to the adjustments for adjusted operating income, adjusted EBITDA, and adjusted net income:
Free Cash Flow
We define free cash flow as net cash provided by operating activities less capital expenditures. We consider free cash flow to be a liquidity measure that provides useful information to management and investors about the amount of cash generated by the business that can be used for strategic opportunities, including investing in our business, making strategic acquisitions, and strengthening the balance sheet.
The following table presents a reconciliation of our free cash flow to our net cash provided by operating activities for the periods presented:
|
|
Year Ended |
|
|||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Net cash provided by operating activities |
|
$ |
513 |
|
|
$ |
760 |
|
Less: Capital expenditures(1) |
|
|
(26 |
) |
|
|
(46 |
) |
Free cash flow(2) |
|
$ |
487 |
|
|
$ |
714 |
|
59
Factors Affecting the Comparability of Our Results of Operations
As a result of a number of factors, our historical results of operations are not comparable from period to period and may not be comparable to our financial results of operations in future periods. Set forth below is a brief discussion of the key factors impacting the comparability of our results of operations.
Payments to Channel Partners
We make various payments to our channel partners, which may include revenue share, product placement fees and marketing development funds. Costs that are incremental to revenue, such as revenue share, are capitalized and amortized over time as cost of sales. This classification is an accounting policy election, which may make comparisons to other companies difficult. Product placement fees and marketing development funds are expensed in sales and marketing expense as the related benefit is received. Many of our channel partner agreements contain a clause whereby we pay the greater of revenue share calculated for the period or product placement fees. This may impact the comparability of our financial results between periods.
Under certain of our channel partner agreements, the partners pay us a royalty on our technology sold to their customers, which we recognize as revenue in accordance with our revenue recognition policy. In certain situations, the payments made to our channel partners are recognized as consideration paid to a customer, and thus are recorded as reductions to revenue up to the amount of cumulative revenue recognized from contracts with the channel partner during the period of measurement. Any payments to channel partners in excess of such cumulative revenue during the period of measurement are recognized as cost of sales or marketing expense as described above. As royalty revenue from individual partners varies, the amount of costs recognized as a reduction of revenue rather than as cost of sales or sales and marketing expense fluctuates and may impact the comparability of our financial statements between periods.
Impact of Purchase Accounting Related to Mergers and Acquisitions
Through April 3, 2017, the McAfee cybersecurity business was operated as a part of a business unit of Intel. Also prior to April 3, 2017, McAfee, Inc., which was then a wholly-owned subsidiary of Intel, was converted into a limited liability company, McAfee, LLC. Following such conversion, Intel contributed McAfee, LLC to FTW, a wholly-owned subsidiary of Intel. On April 3, 2017, Intel and its subsidiaries transferred assets and liabilities of the McAfee business not already held through FTW to FTW. Immediately thereafter on April 3, 2017, investment funds affiliated with or advised by TPG Global, LLC (“TPG”) and Thoma Bravo, L.P. (“Thoma Bravo”) (collectively “Sponsors”) and certain of their co-investors acquired a majority stake in FTW, pursuant to the Sponsor Acquisition. Following the Sponsor Acquisition, our Sponsors and certain of their co-investors owned 51.0% of the common equity interests in FTW, with certain affiliates of Intel retaining the remaining 49.0% of the common equity interests. We have operated as a standalone company at all times following the Sponsor Acquisition. As a result of the Sponsor Acquisition, we recorded all assets and liabilities at their fair value, including our deferred revenue and deferred costs balances, as of the effective date of the Sponsor Acquisition, which in some cases was different than the historical book values. Adjusting our deferred revenue and deferred costs balances to fair value on the date of the Sponsor Acquisition had the effect of reducing revenue and expenses from that which would have otherwise been recognized in subsequent periods. We also recorded identifiable intangible assets that are amortized over their useful lives, increasing expenses from that which would otherwise have been recognized.
In addition, we have made acquisitions and recorded the acquired assets and liabilities at fair value on the date of acquisition, which similarly impacted deferred revenue and deferred costs balances and reduced revenue and expenses from that which would have otherwise been recognized in subsequent periods. We also recorded identifiable intangible assets that are amortized over their useful lives, increasing expenses from that which would otherwise have been recognized.
The accounting impact resulting from these acquisitions limits the comparability of our financial statements between periods. The table below shows the impact of purchase accounting on our financial statements.
|
|
Year Ended |
|
|||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Cost of sales |
|
$ |
94 |
|
|
$ |
109 |
|
Amortization of intangibles |
|
|
76 |
|
|
|
143 |
|
Expense attributable to the impact of purchase accounting related to continuing operations |
|
|
170 |
|
|
|
252 |
|
Expense attributable to the impact of purchase accounting related to discontinued operations |
|
|
36 |
|
|
|
187 |
|
Total expense attributable to the impact of purchase accounting |
|
$ |
206 |
|
|
$ |
439 |
|
60
Income Tax and Tax Receivable Agreement
McAfee Corp. is a corporation for U.S. federal and state income tax purposes. Following the Reorganization Transactions, FTW is the predecessor of McAfee Corp. for accounting purposes. FTW is and remains a partnership for U.S. federal income tax purposes and will therefore generally not be subject to any U.S. federal income taxes at the entity level in respect of income it recognizes directly or through its U.S. and foreign subsidiaries that are also pass- through or disregarded entities for U.S. federal income tax purposes. Instead, taxable income and loss of these entities will flow through to the members of FTW (including McAfee Corp. and certain of its subsidiaries) for U.S. federal income tax purposes. Certain of FTW’s non-U.S. subsidiaries that are treated as pass-through or disregarded entities for U.S. federal income tax purposes are nonetheless treated as taxable entities in their respective jurisdictions and are thus subject to non-U.S. taxes at the entity level. FTW also has certain U.S. and foreign subsidiaries that are treated as corporations for U.S. federal income tax purposes and that therefore are or may be subject to income tax at the entity level. McAfee Corp. pays U.S. federal, state and local income taxes as a corporation on its share of the taxable income of FTW (taking into account the direct and indirect ownership of FTW by McAfee Corp.). In addition, in connection with the Reorganization Transactions and the IPO, McAfee Corp. entered into the tax receivable agreement as described in Note 14 to the Consolidated Financial Statements in Part II, Item 8 of this Annual Report on Form 10-K.
As a result of the divestiture, we expect to utilize certain deferred tax assets from the domestic portion of the gain on the sale. We have concluded that a full valuation allowance against the net deferred tax assets of our domestic entities will no longer be required and have released $211 million of the $212 million of valuation allowance that existed as of December 26, 2020. The valuation allowance of $19 million as of December 25, 2021 relates to foreign capital and state net operating loss carryforwards primarily generated in the current year that we have determined are not more likely than not going to be utilized. In addition, we recognized a deferred tax asset of $223 million with a corresponding charge to equity when FTW LLC Units are exchanged for shares of Class A common stock (the “Exchanges”) in fiscal 2021.
|
|
|
|
|
|
Offset To |
|
||||||||||
(in millions) |
|
Deferred Tax Asset |
|
|
|
Additional Paid-in Capital |
|
|
Provision for Income Tax (Expense) Benefits |
|
|
Income from Discontinued Operations |
|
||||
Release of valuation allowance on deferred tax assets |
|
$ |
211 |
|
|
|
$ |
— |
|
|
$ |
211 |
|
|
$ |
— |
|
Exchanges and tax attributes in Fiscal 2021 |
|
|
223 |
|
|
|
|
223 |
|
|
|
— |
|
|
|
— |
|
As the net deferred tax assets have been recognized as of the date of divestiture of the Enterprise Business, the full liability under the TRA also became probable as of that date. During the year ended December 25, 2021, TRA liability increases of $121 million resulting from post divestiture Exchanges were recorded to Additional paid-in capital on the consolidated balance sheet. TRA liability increases of $313 million resulting from pre-divestiture Exchanges and TRA liability decreases of $6 million resulting from unutilized tax attributes were recorded within Other income (expense), net. TRA liability increases of $4 million resulting from divestiture related events were recorded within Income from discontinued operations on the consolidated statement of operations.
As of December 25, 2021, we have TRA liabilities of $2 million and $432 million recorded in the consolidated balance sheet within Accounts payable and other accrued liabilities and Tax receivable agreement liability, less current portion, respectively.
|
|
TRA Liability |
|
|
|
Offset To |
|
||||||||||||||
(in millions) |
|
Current Portion |
|
|
Noncurrent Portion |
|
|
|
Additional Paid-in Capital |
|
|
Other Income (Expense), Net |
|
|
Income from Discontinued Operations |
|
|||||
As of December 26, 2020 |
|
$ |
2 |
|
|
$ |
— |
|
|
|
|
|
|
|
|
|
|
|
|||
Exchanges and tax attributes that existed prior to divestiture |
|
|
— |
|
|
|
317 |
|
|
|
$ |
— |
|
|
$ |
(313 |
) |
|
$ |
(4 |
) |
Exchanges and tax attributes that existed on or after divestiture |
|
|
— |
|
|
|
115 |
|
|
|
|
(121 |
) |
|
|
6 |
|
|
|
— |
|
As of December 25, 2021 |
|
$ |
2 |
|
|
$ |
432 |
|
|
|
$ |
(121 |
) |
|
$ |
(307 |
) |
|
$ |
(4 |
) |
61
Equity-Based Compensation
Upon consummation of the IPO in October 2020, we recognized a cumulative catch-up of equity-based compensation expense relating to our management equity participation units (“MEPU”s) and cash-settled restricted equity units (“CRSU”s). Concurrently, we modified the terms of our unvested FTW RSUs, outstanding CRSUs, and outstanding MEPUs to permit settlement in the Company’s Class A common stock, par value $0.001 per share (“Class A common stock”) (collectively, “Replacement RSUs”) in lieu of cash settlement, at the Company’s election. No service or performance vesting terms were changed at the time of modification. All of our outstanding equity awards were probable of vesting and the change was accounted for as a Type I modification. In addition, the Company granted stock options with a strike price equal to the IPO price to certain holders of MEPUs with distribution thresholds not fully satisfied at the time of modification and, at the time of the grant, recognized expense for these options immediately. See Note 12 to the Consolidated Financial Statements in Part II, Item 8 of this Annual Report on Form 10-K for a detailed discussion of equity-based compensation.
The accounting impact resulting from the recognition of this equity-based compensation limits the comparability of our financial statements between periods. The table below shows the impact of all equity-based compensation on our financial statements.
|
|
Year Ended |
|
|||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Cost of sales |
|
$ |
3 |
|
|
$ |
5 |
|
Sales and marketing |
|
|
19 |
|
|
|
23 |
|
Research and development |
|
|
20 |
|
|
|
40 |
|
General and administrative |
|
|
29 |
|
|
|
45 |
|
Total equity-based compensation expense from continuing operations |
|
|
71 |
|
|
|
113 |
|
Discontinued operations |
|
|
31 |
|
|
|
200 |
|
Total equity-based compensation expense |
|
$ |
102 |
|
|
$ |
313 |
|
Composition of Revenues, Expenses, and Cash Flows
Net Revenue
We derive our revenue primarily from the sale of software subscriptions or royalty agreements, primarily through our indirect relationships with our partners or direct relationships with end customers through our website. We have various marketing programs with certain business partners who we consider customers and reduce revenue by the cash consideration given to these partners. Revenue is recognized as control of the promised goods or services are transferred to our customers, in an amount that reflects the consideration we expect to be entitled to in exchange for the promised goods or services.
Cost of Sales
Our total cost of sales include fees paid under revenue share arrangements, amortization of certain intangibles, transaction processing fees, the costs of providing delivery (i.e., hosting), support including salaries and benefits for employees and fees related to third parties, and technology licensing fees. We anticipate our total cost of sales to increase in absolute dollars as we grow our net revenue. Cost of sales as a percentage of net revenue may vary from period to period based on our investments in the business, the efficiencies we are able to realize going forward as well as due to the accounting for payments to channel partners discussed in Factors Affecting the Comparability of Our Results of Operations.
We expect the divestiture of the Enterprise Business to lead to costs that were previously allocated to both segments to now be part of continuing operations, which will have a dilutive impact on gross margins.
Operating Expenses
Our operating expenses consist of sales and marketing, research and development, general and administrative, amortization of intangibles, and restructuring and transition charges.
We expect the divestiture of the Enterprise Business to lead to costs that were previously allocated to both segments will be part of continuing operations, which will have a dilutive impact on operating margins.
62
Interest Expense
Interest expense primarily relates to interest expense on our outstanding indebtedness.
Foreign Exchange Gain (Loss), Net
Foreign exchange gain (loss), net is comprised of realized and unrealized gains or losses on non-U.S. Dollar denominated balances and is primarily due to unrealized gains or losses associated with our 1st Lien Euro Term Loan.
Other Income (expense), Net
Other income (expense), net is primarily attributable to adjustments related to the TRA, as well as the revenue from the transition service agreement we entered into in connection with the divestiture of the Enterprise Business under which we provide assistance to Enterprise Business including, but not limited to, business support services and information technology services.
Provision for Income Tax
McAfee Corp. is taxed as a corporation and pays corporate federal, state and local taxes on income allocated to it from FTW based upon McAfee Corp.’s economic interest in FTW. FTW is a pass through entity for U.S. federal income tax purposes and will not incur any federal income taxes either for itself or its U.S. subsidiaries that are also pass through or disregarded subsidiaries. Taxable income or loss for these entities will flow through to its respective members for U.S. tax purposes. FTW does have certain U.S. and foreign subsidiaries that are corporations and are subject to income tax in their respective jurisdiction.
Income from Discontinued Operations, Net of Taxes
Following the agreement with STG, the results of our Enterprise Business through the date of transaction close were classified as discontinued operations in our consolidated statements of operations and excluded from continuing operations.
63
Results of Operations
The following tables set forth the consolidated statements of operations in dollar amounts and as a percentage of our total revenue for the periods indicated. The period-to-period comparison of results is not necessarily indicative of results for future periods.
|
|
Year Ended |
|
|||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Net revenue |
|
$ |
1,920 |
|
|
$ |
1,558 |
|
Cost of sales |
|
|
470 |
|
|
|
444 |
|
Gross profit |
|
|
1,450 |
|
|
|
1,114 |
|
Operating expenses: |
|
|
|
|
|
|
||
Sales and marketing |
|
|
375 |
|
|
|
345 |
|
Research and development |
|
|
184 |
|
|
|
187 |
|
General and administrative |
|
|
196 |
|
|
|
231 |
|
Amortization of intangibles |
|
|
76 |
|
|
|
143 |
|
Restructuring and transition charges |
|
|
70 |
|
|
|
2 |
|
Total operating expenses |
|
|
901 |
|
|
|
908 |
|
Operating income |
|
|
549 |
|
|
|
206 |
|
Interest expense |
|
|
(212 |
) |
|
|
(303 |
) |
Foreign exchange gain (loss), net |
|
|
41 |
|
|
|
(104 |
) |
Other income (expense), net |
|
|
(291 |
) |
|
|
(4 |
) |
Income (loss) from continuing operations before income taxes |
|
|
87 |
|
|
|
(205 |
) |
Provision for income tax expense (benefit) |
|
|
(160 |
) |
|
|
5 |
|
Income (loss) from continuing operations |
|
|
247 |
|
|
|
(210 |
) |
Income (loss) from discontinued operations, net of taxes |
|
|
2,441 |
|
|
|
(79 |
) |
Net income (loss) |
|
|
2,688 |
|
|
|
(289 |
) |
Less: Net income (loss) attributable to redeemable noncontrolling interests |
|
|
1,839 |
|
|
|
(171 |
) |
Net income (loss) attributable to McAfee Corp. |
|
$ |
849 |
|
|
$ |
(118 |
) |
|
|
Year Ended |
|
|||||
|
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Net revenue |
|
|
100.0 |
% |
|
|
100.0 |
% |
Cost of sales |
|
|
24.5 |
% |
|
|
28.5 |
% |
Gross profit |
|
|
75.5 |
% |
|
|
71.5 |
% |
Operating expenses: |
|
|
|
|
|
|
||
Sales and marketing |
|
|
19.5 |
% |
|
|
22.1 |
% |
Research and development |
|
|
9.6 |
% |
|
|
12.0 |
% |
General and administrative |
|
|
10.2 |
% |
|
|
14.8 |
% |
Amortization of intangibles |
|
|
4.0 |
% |
|
|
9.2 |
% |
Restructuring and transition charges |
|
|
3.6 |
% |
|
|
0.1 |
% |
Total operating expenses |
|
|
46.9 |
% |
|
|
58.3 |
% |
Operating income |
|
|
28.6 |
% |
|
|
13.2 |
% |
Interest expense |
|
|
(11.0 |
)% |
|
|
(19.4 |
)% |
Foreign exchange gain (loss), net |
|
|
2.1 |
% |
|
|
(6.7 |
)% |
Other income (expense), net |
|
|
(15.2 |
)% |
|
|
(0.3 |
)% |
Income (loss) from continuing operations before income taxes |
|
|
4.5 |
% |
|
|
(13.2 |
)% |
Provision for income tax expense (benefit) |
|
|
(8.3 |
)% |
|
|
0.3 |
% |
Income (loss) from continuing operations |
|
|
12.9 |
% |
|
|
(13.5 |
)% |
Income (loss) from discontinued operations, net of taxes |
|
|
127.1 |
% |
|
|
(5.1 |
)% |
Net income (loss) |
|
|
140.0 |
% |
|
|
(18.5 |
)% |
Less: Net income (loss) attributable to redeemable noncontrolling interests |
|
|
95.8 |
% |
|
|
(11.0 |
)% |
Net income (loss) attributable to McAfee Corp. |
|
|
44.2 |
% |
|
|
(7.6 |
)% |
64
Net Revenue
|
|
Year Ended |
|
|
Variance in |
|
||||||||||
(in millions, except |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
Dollars |
|
|
Percent |
|
||||
Net revenue |
|
$ |
1,920 |
|
|
$ |
1,558 |
|
|
$ |
362 |
|
|
|
23.2 |
% |
The net revenue increase was primarily driven by (i) growth in Core Direct to Consumer Subscribers, (ii) increases in secure search revenue, (iii) growth in Mobile and Internet Service Provider business, and (iv) an increase in ARPC.
Net Revenue by Geographical Region
Net revenue by geographic region based on the sell-to address of the end-users is as follows:
|
|
Year Ended |
|
|||||||||||||
(in millions except percentages) |
|
December 25, 2021 |
|
|
% of Total |
|
|
December 26, 2020 |
|
|
% of Total |
|
||||
Americas |
|
$ |
1,281 |
|
|
|
66.7 |
% |
|
$ |
1,027 |
|
|
|
65.9 |
% |
EMEA |
|
|
441 |
|
|
|
23.0 |
% |
|
|
365 |
|
|
|
23.4 |
% |
APJ |
|
|
198 |
|
|
|
10.3 |
% |
|
|
166 |
|
|
|
10.7 |
% |
Total net revenue |
|
$ |
1,920 |
|
|
|
100.0 |
% |
|
$ |
1,558 |
|
|
|
100.0 |
% |
The Americas include the U.S., Canada and Latin America; EMEA includes Europe, the Middle East and Africa; APJ includes Asia Pacific and Japan.
Net revenue by geographic region in fiscal 2021 showed growth in all geographies when compared to the corresponding periods in the prior year and we expect such percentages to remain relatively consistent in the near term.
Net Revenue by Channel
Direct to Consumer revenue is from subscribers who transact with us directly through McAfee web properties, including those converted after the trial period of the McAfee product preinstalled on their new PC purchase or converted subsequent to their subscription period purchased from another channel. Indirect revenue is driven by users who purchase directly through a partner inclusive of mobile providers, ISPs, electronics retailers, ecommerce sites, and search providers.
Net revenue by channel of the end-users is as follows:
|
|
Year Ended |
|
|||||||||||||
(in millions except percentages) |
|
December 25, 2021 |
|
|
% of Total |
|
|
December 26, 2020 |
|
|
% of Total |
|
||||
Direct to Consumer |
|
$ |
1,397 |
|
|
|
72.8 |
% |
|
$ |
1,195 |
|
|
|
76.7 |
% |
Indirect |
|
|
523 |
|
|
|
27.2 |
% |
|
|
363 |
|
|
|
23.3 |
% |
Total net revenue |
|
$ |
1,920 |
|
|
|
100.0 |
% |
|
$ |
1,558 |
|
|
|
100.0 |
% |
Cost of Sales
|
|
Year Ended |
|
|
Variance in |
|
||||||||||
(in millions, except percentages) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
Dollars |
|
|
Percent |
|
||||
Cost of sales |
|
$ |
470 |
|
|
$ |
444 |
|
|
$ |
26 |
|
|
|
5.9 |
% |
Gross profit margin |
|
|
75.5 |
% |
|
|
71.5 |
% |
|
|
|
|
|
|
||
The increase in cost of sales was primarily attributable to a $44 million increase in revenue share expense and online transaction processing fees driven by increases in Core Direct to Consumer Subscribers, partially offset by a $14 million decrease in amortization due to assets becoming fully amortized as of March 2021.
Operating Expenses
|
|
Year Ended |
|
|
Variance in |
|
||||||||||
(in millions, except percentages) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
Dollars |
|
|
Percent |
|
||||
Sales and marketing |
|
$ |
375 |
|
|
$ |
345 |
|
|
$ |
30 |
|
|
|
8.7 |
% |
Research and development |
|
|
184 |
|
|
|
187 |
|
|
|
(3 |
) |
|
|
(1.6 |
)% |
General and administrative |
|
|
196 |
|
|
|
231 |
|
|
|
(35 |
) |
|
|
(15.2 |
)% |
Amortization of intangibles |
|
|
76 |
|
|
|
143 |
|
|
|
(67 |
) |
|
|
(46.9 |
)% |
Restructuring and transition charges |
|
|
70 |
|
|
|
2 |
|
|
|
68 |
|
|
|
3400.0 |
% |
Total |
|
$ |
901 |
|
|
$ |
908 |
|
|
$ |
(7 |
) |
|
|
(0.8 |
)% |
65
Sales and Marketing
The increase in sales and marketing expense was primarily attributable to (i) a $25 million increase in marketing spend and (ii) a $9 million increase in expenses for consulting services. These increases were partially offset by the decrease in equity-based compensation expense.
Research and Development
The decrease in research and development expense was primarily attributable to the decrease in equity-based compensation expense, partially offset by an increase in employee expenses.
General and Administrative
The decrease in general and administrative expense was primarily attributable to (i) a $28 million decrease in management fee expense including a one-time fee for the termination of the management agreement at the time of the IPO, and (ii) a decrease in equity-based compensation and acquisition and integration costs. These increases were partially offset by a $9 million increase in professional services expenses primarily related to costs of being a public company.
Amortization of Intangibles
The decrease in amortization of intangibles was attributable to assets that became fully amortized in March 2021.
Restructuring and Transition Charges
The increase in restructuring and transition charges is primarily the result of $60 million of transition charges including legal, advisory, consulting and other costs directly incurred due to the divestiture of the Enterprise Business, including incremental costs associated with data disentanglement and acceleration of data migration to the cloud, that were incurred subsequent to the sale in support of the transition services agreement.
There was an additional $8 million increase driven by restructuring and one-time termination benefits to impacted employees, including severance payments and healthcare and other accrued benefits related to the workforce reduction that was initiated in December 2020.
Operating Income
|
|
Year Ended |
|
|
Variance in |
|
||||||||||
(in millions, except percentages) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
Dollars |
|
|
Percent |
|
||||
Operating income |
|
$ |
549 |
|
|
$ |
206 |
|
|
$ |
343 |
|
|
|
166.5 |
% |
Operating income margin |
|
|
28.6 |
% |
|
|
13.2 |
% |
|
|
|
|
|
|
||
The operating income increase was primarily driven by (i) the $362 million increase in net revenue, (ii) $81 million decrease in amortization expense, (iii) a $42 million decrease in equity-based compensation, and (iv) a $28 million decrease in management fee expense including the one-time termination fee at the time of the IPO. These were partially offset by (i) a $68 million increase in restructuring and transition charges, (ii) a $44 million increase in revenue share expense resulting from increases in Core Direct to Consumer Subscribers, (iii) a $25 million increase in marketing spend, and (iv) an $18 million dollar increase in professional service and external consulting expenses.
Interest Expense
|
|
Year Ended |
|
|
Variance in |
|
||||||||||
(in millions, except percentages) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
Dollars |
|
|
Percent |
|
||||
Interest expense |
|
$ |
(212 |
) |
|
$ |
(303 |
) |
|
$ |
91 |
|
|
|
(30.0 |
)% |
The decrease in interest expense was primarily attributable to (i) lower debt balances due to the payoff of our 2nd Lien Term Loan and prepayment on our 1st Lien USD Term Loan in the fourth quarter of 2020 in addition to our third quarter 2021 prepayment of 1st Lien Term Loans with a portion of the proceeds of the divestiture of the Enterprise business as discussed above and (ii) a $14 million loss on extinguishment in 2020 for the remaining unamortized discount and unamortized deferred financing costs at the time of the payoff of our 2nd Lien Term Loan. These decreases were partially offset by a (i) $10 million loss on extinguishment of debt for recognition of unamortized discount and deferred financing in the third quarter of 2021 for the 1st Lien Term Loans prepayment and (ii) a $9 million increase in interest rate swap expense due to a decrease in LIBOR.
Other Income (Expense), Net
|
|
Year Ended |
|
|
Variance in |
|
||||||||||
(in millions, except percentages) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
Dollars |
|
|
Percent |
|
||||
Other income (expense), net |
|
$ |
(291 |
) |
|
$ |
(4 |
) |
|
$ |
(287 |
) |
|
|
7175.0 |
% |
66
The decrease in other income (expense), net was primarily attributable to $307 million in tax receivable agreement liability recorded to expense subsequent to the release of the valuation allowance against the deferred tax assets discussed within the Provision for Income Tax Expense section below. This was partially offset by $18 million increase in TSA income.
Provision for Income Tax Expense
|
|
Year Ended |
|
|
Variance in |
|
||||||||||
(in millions, except percentages) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
Dollars |
|
|
Percent |
|
||||
Provision for income tax expense (benefit) |
|
$ |
(160 |
) |
|
$ |
5 |
|
|
$ |
(165 |
) |
|
|
(3300.0 |
)% |
The change in the provision for income tax benefit was primarily attributable to the release of the valuation allowance on the deferred tax assets in the U.S. due to no longer being in a cumulative pre-tax loss as a result of the gain on the divestiture of the Enterprise Business, partially offset by increased in income in higher taxed jurisdictions.
Discontinued Operations
|
|
Year Ended |
|
|
Variance in |
|
||||||||||
(in millions, except percentages) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
Dollars |
|
|
Percent |
|
||||
Net revenue |
|
$ |
781 |
|
|
$ |
1,348 |
|
|
$ |
(567 |
) |
|
|
(42.1 |
)% |
Operating income (loss) |
|
|
99 |
|
|
|
(54 |
) |
|
|
153 |
|
|
|
(283.3 |
)% |
Pre-tax gain on divestiture of Enterprise Business |
|
|
2,628 |
|
|
|
— |
|
|
|
2,628 |
|
|
NM |
|
|
Income (loss) from discontinued operations before income taxes |
|
|
2,722 |
|
|
|
(54 |
) |
|
|
2,776 |
|
|
|
(5140.7 |
)% |
Income tax expense |
|
|
281 |
|
|
|
25 |
|
|
|
256 |
|
|
|
1024.0 |
% |
Income (loss) from discontinued operations, net of tax |
|
|
2,441 |
|
|
|
(79 |
) |
|
|
2,520 |
|
|
|
(3189.9 |
)% |
The changes in net revenue and operating income related to discontinued operations was primarily the result of the sale closing July 27, 2021.
The increase in the income from discontinued operations before income taxes was primarily the result of the $2,628 million pre-tax gain on the divestiture of the Enterprise Business recognized in 2021.
The increase in income tax expense is primarily due to the $386 million tax expense related to the gain on the divestiture of the Enterprise Business, partially offset by tax benefits recognized due to basis differences of McAfee Corp. in FTW.
Seasonality
While portions of our business are impacted by seasonality, the net impact of seasonality on our business is limited. Orders are generally higher in the first and fourth quarters and lower in the second and third quarters. A significant number of orders in the fourth quarter is reflective of historically higher holiday sales of PC computers leading to higher subscriptions in the fourth quarter as well as in the first quarter due to lag from computer purchase to paid subscription of our products. This seasonal effect is present both in new subscriptions as well as in the renewal of prior year subscriptions due in those quarters.
Liquidity and Capital Resources
McAfee Corp. is a holding company with no operations and, as such, will depend on its subsidiaries for cash to fund all of its operations and expenses through the payment of distributions by its current and future subsidiaries, including FTW. The terms of the agreements governing our senior secured credit facilities contain certain negative covenants prohibiting certain of our subsidiaries from making cash dividends or distributions to McAfee Corp. or to FTW unless certain financial tests are met. For a discussion of those restrictions, see “—Senior Secured Credit Facilities” below and “Risk Factors—Risks Related to Our Indebtedness—Restrictions imposed by our outstanding indebtedness and any future indebtedness may limit our ability to operate our business and to take certain actions”. We currently anticipate that such restrictions will not impact our ability to meet our cash obligations.
Sources of Liquidity
As of December 25, 2021, we had cash and cash equivalents of $816 million. Our primary source of cash for funding operations and growth has been through cash flows generated from operating activities. In addition, we have funded certain acquisitions, distributions to members, and to a lesser extent, capital expenditures and our operations, through borrowings under the Senior Secured Credit Facilities, primarily in the form of long-term debt obligations. As of December 25, 2021, we had $660 million of additional unused borrowing capacity under our Revolving Credit Facility.
67
We believe that our existing cash on hand, expected future cash flows from operating activities, and additional borrowings available under our credit facilities will provide sufficient resources to fund our operating requirements as well as future capital expenditures, debt service requirements, and investments in future growth for at least the next twelve months. Our future capital requirements will depend on many factors, including our growth rate, the timing and extent of spending to support development efforts, the expansion of sales and marketing activities, the introduction of new and enhanced product and service offerings, and the continuing market acceptance of our products. In the event that additional financing is required from outside sources, we may not be able to raise such financing on terms acceptable to us or at all. If we are unable to raise additional capital when desired, our business, operating results, and financial condition may be adversely affected.
On July 27, 2021, we completed the sale of our Enterprise Business for an all-cash purchase price of $4.0 billion and received $3.9 billion, net of transaction costs. Refer to “—Divestiture of Enterprise Business” above.
Senior Secured Credit Facilities
As of December 25, 2021, our Senior Secured Credit Facilities consisted of a U.S. dollar-denominated term loan tranche of $2,369 million (the “First Lien USD Term Loan”), a Euro-denominated term loan tranche of €499 million (the “First Lien EUR Term Loan”, and together with the First Lien USD Term Loan, the “First Lien Term Loans”), and a $664 million Revolving Credit Facility, of which we had $4 million outstanding as letters of credit. The Revolving Credit Facility includes a $50 million sublimit for the issuance of letters of credit.
The commitments under the First Lien Term Loans will mature on September 29, 2024. As of December 25, 2021, our total outstanding indebtedness under the Senior Secured Credit Facilities was $2,935 million. The First Lien Term Loans require equal quarterly repayments equal to 0.25% of the total amount borrowed.
Our 1st Lien Net Leverage Ratio as defined in the credit facility agreement was 1.7 as of December 25, 2021. For the year ended December 25, 2021, the weighted average interest rate was 3.9% under the First Lien USD Term Loan and 3.5% under the First Lien EUR Term Loan. The commitment fee of the unused portion of the Revolving Credit Facility was 0.25% as of December 25, 2021.
In August 2021, we prepaid $332 million of 1st Lien USD Term Loan and €563 million of 1st Lien Euro Term Loan. In connection with this prepayment, we incurred a loss on extinguishment of debt in the third quarter of our 2021 fiscal year of $10 million related to recognition of unamortized discount and deferred financing costs. See Note 13 to the consolidated financial statements for more information. We also terminated $150 million of our $250 million notional interest rate swap that had an expiration date of January 29, 2022. See Note 15 to the consolidated financial statements for more information and refer to “—Divestiture of Enterprise Business” above.
Tax Receivable Agreement
The contribution by the Continuing Owners (as defined in Note 1 to the consolidated financial statements in Part II, Item 8 of this Annual Report on Form 10-K) to the Corporation of certain corporate entities in connection with the IPO (including the Reorganization Transactions) and future exchanges of LLC Units for shares of the Corporation’s Class A common stock are expected to produce or otherwise deliver to the Corporation favorable tax attributes that can reduce its taxable income. Prior to the completion of the IPO, the Corporation entered into a Tax Receivable Agreement (“TRA”), which generally will require it to pay the TRA Beneficiaries, as defined in Note 1 to the consolidated financial statements, 85% of the applicable cash savings, if any, in U.S. federal, state, and local income tax that the Corporation actually realizes or, in certain circumstances, is deemed to realize as a result of (i) all or a portion of the Corporation’s allocable share of existing tax basis in the assets of FTW (and its subsidiaries) acquired in connection with the Reorganization Transactions, (ii) increases in the Corporation’s allocable share of existing tax basis in the assets of FTW (and its subsidiaries) and tax basis adjustments in the assets of FTW (and its subsidiaries) as a result of sales or exchanges of LLC Units after the IPO, (iii) certain tax attributes of the corporations acquired by McAfee Corp. in connection with the Reorganization Transactions (including their allocable share of existing tax basis in the assets of FTW (and its subsidiaries)), and (iv) certain other tax benefits related to entering into the tax receivable agreement, including tax benefits attributable to payments under the tax receivable agreement. The Corporation generally will retain the benefit of the remaining 15% of the applicable tax savings. The payment obligations under the tax receivable agreement are obligations of McAfee Corp., and we expect that the payments that will be required to make under the tax receivable agreement will be substantial.
On July 27, 2021, we completed the sale of our Enterprise Business to STG for an all-cash purchase price of $4.0 billion. As the net deferred tax assets have been recognized as of the date of divestiture of the Enterprise Business, the full liability under the TRA also became probable as of that date. During the year ended December 25, 2021, TRA liability increases of $121 million resulting from post divestiture Exchanges were recorded to Additional paid-in capital on the consolidated balance sheet. TRA liability increases of $313 million resulting from pre-divestiture Exchanges and TRA liability decreases of $6 million resulting from unutilized tax attributes were recorded within Other income (expense), net. TRA liability increases of $4 million resulting from divestiture related events were recorded within Income from discontinued operations on the consolidated statement of operations.
68
As of December 25, 2021, we have TRA liabilities of $2 million and $432 million recorded in the consolidated balance sheet within Accounts payable and other accrued liabilities and Tax receivable agreement liability, less current portion, respectively. See Note 1 and 14 to the consolidated financial statements in Part II, Item 8 of this Annual Report on Form 10-K for further information.
Dividend Policy
FTW paid a cash distribution to its members for each of the first three quarters of fiscal 2021 at an aggregate annual rate of approximately $200 million. McAfee Corp. received a portion of such distributions through the LLC Units it holds directly or indirectly through its wholly-owned subsidiaries on the record date such distributions were declared by FTW. McAfee Corp. used a portion of its share of the cash distributions declared by FTW to declare or pay the dividends noted in the table below during the year ended December 25, 2021. Remaining distributions received by McAfee Corp. were used for corporate taxes and general corporate purposes. Pursuant to the terms of the Merger Agreement, the Company has agreed to suspend its dividend during the term of the Merger Agreement.
Declaration Date |
|
Record Date |
|
Payment Date |
|
Dividend per Share |
|
|
Amount |
|
||
December 9, 2020 |
|
December 24, 2020 |
|
January 7, 2021 |
|
$ |
0.087 |
|
|
$ |
14 |
|
March 11, 2021 |
|
March 26, 2021 |
|
April 9, 2021 |
|
$ |
0.115 |
|
|
$ |
19 |
|
June 10, 2021 |
|
June 25, 2021 |
|
July 9, 2021 |
|
$ |
0.115 |
|
|
$ |
19 |
|
August 3, 2021 |
|
August 13, 2021 |
|
August 27, 2021 |
|
$ |
4.500 |
|
|
$ |
760 |
|
September 13, 2021 |
|
September 24, 2021 |
|
October 8, 2021 |
|
$ |
0.115 |
|
|
$ |
21 |
|
On August 3, 2021, we declared a one-time Special Dividend of $4.50 per share of Class A common stock outstanding in connection with the consummation of the sale of our Enterprise Business. See Note 7 to the consolidated financial statements for additional dividend information on the Special Dividend.
69
Consolidated Statements of Cash Flows
Our cash flows for the years ended December 25, 2021 and December 26, 2020 were:
|
|
Year Ended |
|
|||||
|
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Net cash provided by operating activities |
|
$ |
513 |
|
|
$ |
760 |
|
Net cash provided by (used in) investing activities |
|
|
3,935 |
|
|
|
(51 |
) |
Net cash used in financing activities |
|
|
(3,851 |
) |
|
|
(651 |
) |
Effect of exchange rate fluctuations on cash and cash equivalents |
|
|
(12 |
) |
|
|
6 |
|
Change in cash and cash equivalents |
|
$ |
585 |
|
|
$ |
64 |
|
See Note 4 to the consolidated financial statements for additional cash flow information associated with our discontinued operations.
Operating Activities
For the year ended December 25, 2021, net cash provided by operating activities was $513 million, as a result of net income of $2,688 million, adjusted for non-cash charges of $2,161 million and net cash outflow of $14 million from changes in operating assets and liabilities. Non-cash charges primarily consisted of $2,628 million of pre-tax gain on divestiture of Enterprise Business, $173 million in deferred taxes primarily from the release of valuation allowance due to divestiture of Enterprise Business, and $41 million in foreign exchange gains, partially offset by $311 million in TRA remeasurement, $236 million in depreciation and amortization, $102 million in equity-based compensation, and $35 million in other operating activities primarily consisting of lease asset amortization, and amortization of debt discount and issuance costs. The net cash outflow from changes in operating assets and liabilities was primarily due to (i) a $55 million decrease in other liabilities primarily due to payment of annual bonuses and year-end commissions in fiscal 2021 to employees of Enterprise Business, (ii) a $51 million increase in deferred costs primarily due to increased deferred revenue share resulting from an increased subscriber base, (iii) a $51 million increase in other assets primarily due to increases in long-term deferred revenue share and in right of use assets recorded primarily due to renewed leases, and (iv) a $30 million increase in receivable from and payable to the Enterprise Business primarily due to receivable related to TSA receivable and misdirected payments. These changes were partially offset by (i) an $86 million decrease in accounts receivable, net primarily due to collection of accounts receivable outstanding at December 26, 2020, including those related to the Enterprise Business, (ii) a $32 million increase in other current liabilities primarily due to accrual of transition costs incurred in 2021, (iii) a $24 million increase of deferred revenue primarily due to an increased subscriber base, and (iv) a $28 million increase of income taxes payable primarily due to tax obligations from the gain on the divestiture of Enterprise Business. The increase in income taxes paid, net of refunds from the year ended December 26, 2020 to the year ended December 25, 2021 is primarily driven by taxes paid related to the gain on the sale of the Enterprise Business.
For the year ended December 26, 2020, net cash provided by operating activities was $760 million, as a result of a net loss of $289 million, adjusted for non-cash charges of $968 million and net cash inflow of $81 million from changes in operating assets and liabilities. Non-cash charges primarily consisted of $491 million in depreciation and amortization, $313 million in equity-based compensation, $104 million for foreign exchange loss, and $70 million in other operating activities primarily consisting of lease asset amortization, and amortization of debt discount and issuance costs, partially offset by $10 million in deferred income taxes. The net cash inflow from changes in operating assets and liabilities was primarily due to (i) a $106 million increase in deferred revenue balances resulting from increases in Consumer deferred revenue consistent with the increases in subscriber base and dollar retention rates, partially offset by decrease in deferred revenue primarily due to recognition of Enterprise deferred revenue outpacing billings, (ii) a $41 million increase other current liabilities due largely to increased amounts for revenue share and shipments fees related to our increased Consumer subscriber base and increased PC shipments for our OEM partners as well as timing of vendor payments, and (iii) a $15 million decrease in accounts receivable, net which is primarily caused by the decrease in Enterprise billings. These changes were partially offset by (i) a $46 million increase in deferred costs primarily due to increased deferred revenue share resulting from an increased consumer subscriber base and new Consumer affiliate programs, (ii) a $26 million decrease in other liabilities primarily due to lower bonus attainment in 2020 due to slightly lower performance against target, and a slightly lower ending headcount in 2020, and (iii) a $9 million increase in other assets primarily due to new leases signed during the period.
Investing Activities
For the year ended December 25, 2021, net cash provided by investing activities was $3,935 million, which was primarily $3,930 million of net proceeds from divestiture of Enterprise Business and $31 million from disposal of the Plano facility. These in flows were partially offset by additions to property and equipment and other investing activities totaling $26 million.
For the year ended December 26, 2020, net cash used in investing activities was $51 million, which was primarily the result of additions to property and equipment and other investing activities totaling $46 million and a $5 million business acquisition, net of cash.
70
Financing Activities
For the year ended December 25, 2021, net cash used in financing activities was $3,852 million, which was primarily the result of (i) distribution to members of FTW of $1,894 million, (ii) payment of long-term debt of $1,038 million including prepayments made using a portion of the proceeds from divestiture of the Enterprise Business, (iii) $833 million of dividends paid to holders of Class A common stock, and (iv) $101 million of payment of tax withholding for shares withheld.
For the year ended December 26, 2020, net cash used in financing activities was $651 million, which was primarily the result of (i) payment of long-term debt of $869 million, (ii) distributions to members of FTW of $277 million before our IPO, (iii) $24 million in payment of tax withholding on equity awards, (iv) $8 million in payment of IPO related costs, and (v) $23 million in other financing activities primarily relating to equity repurchases. The uses were partially offset by proceeds from IPO of $586 million, net of underwriters’ discount, commissions offset by $33 million to purchase FTW LLC Units.
Contractual Obligations and Commitments
The following is a summary of our contractual obligations as of December 25, 2021:
|
|
Payments Due by Period(1) |
|
|||||||||||||||||
(in millions) |
|
Total |
|
|
Less than 1 |
|
|
1-3 Years |
|
|
3-5 Years |
|
|
Over 5 Years |
|
|||||
Long-term debt(2) |
|
$ |
2,935 |
|
|
$ |
43 |
|
|
$ |
2,892 |
|
|
$ |
— |
|
|
$ |
— |
|
Cash interest(3) |
|
|
391 |
|
|
|
156 |
|
|
|
235 |
|
|
|
— |
|
|
|
— |
|
Purchase obligations |
|
|
399 |
|
|
|
108 |
|
|
|
209 |
|
|
|
82 |
|
|
|
— |
|
Operating lease obligations, including |
|
|
51 |
|
|
|
8 |
|
|
|
12 |
|
|
|
10 |
|
|
|
21 |
|
Total |
|
$ |
3,776 |
|
|
$ |
315 |
|
|
$ |
3,348 |
|
|
$ |
92 |
|
|
$ |
21 |
|
Off-Balance Sheet Arrangements
As of December 25, 2021, and December 26, 2020, we did not have any relationships with unconsolidated entities or financial partnerships, such as structured finance or special purpose entities, that were established for the purpose of facilitating off-balance sheet arrangements or other purposes.
71
Critical Accounting Policies and Use of Estimates
Our discussion and analysis of operating results and financial condition are based upon our consolidated financial statements included elsewhere in this document. The preparation of our financial statements in accordance with GAAP requires us to make estimates and assumptions that affect the reported amounts of assets, liabilities, revenue, expenses and related disclosures of contingent assets and liabilities. We base our estimates on past experience and other assumptions that we believe are reasonable under the circumstances, and we evaluate these estimates on an ongoing basis. Actual results may differ from those estimates.
Our critical accounting policies are those that materially affect our consolidated financial statements including those that involve difficult, subjective or complex judgments by management. A thorough understanding of these critical accounting policies is essential when reviewing our consolidated financial statements. We believe that the critical accounting policies listed below are those that are most important to the portrayal of our results of operations or involve the most difficult management decisions related to the use of significant estimates and assumptions as described above. For further information, see Note 2 of our consolidated financial statements (Part II, Item 8 of this Form 10-K).
Revenue Recognition
We derive revenue from the sale of security products, subscriptions, software as a service (“SaaS”) offerings, support and maintenance, professional services, or a combination of these items, primarily through our indirect relationships with our partners or direct relationships with end customers through our internal sales force.
We recognize revenue pursuant to the five-step framework within ASC Topic 606:
We generally consider our customer to be the entity with which we have a contractual agreement. This could be the end user, or when we sell products and services through the channel, our customer could be either the distributor or the reseller. As part of determining whether a contract exists, probability of collection is assessed on a customer-by-customer basis at the outset of the contract. Customers are subjected to a credit review process that evaluates the customers’ financial position and the ability and intention to pay.
At contract inception, we assess the goods and services promised in our contracts with customers and identify a performance obligation for each promise to transfer to the customer a good or service (or bundle of goods or services) that is distinct — i.e., if a good or service is separately identifiable from other items in the bundled package and if a customer can benefit from it on its own or together with other resources that are readily available to the customer. To identify our performance obligations, we consider all of the goods or services promised in the contract regardless of whether they are explicitly stated or are implied by customary business practices. Determining whether products and services are considered distinct performance obligations or should be combined to create a single performance obligation may require significant judgment. We recognize revenue when (or as) we satisfy a performance obligation by transferring control of a good or service to a customer.
The transaction price is determined based on the consideration to which we will be entitled in exchange for transferring goods or services to the customer, adjusted for estimated variable consideration, if any. We typically estimate the transaction price impact of sales returns and discounts offered to the customers, including discounts for early payments on receivables, rebates or certain distribution partner incentives, including marketing programs. Constraints are applied when estimating variable considerations based on historical experience where applicable.
Once we have determined the transaction price, we allocate it to each performance obligation in a manner depicting the amount of consideration to which we expect to be entitled in exchange for transferring the goods or services to the customer (the “allocation objective”). If the allocation objective is met at contractual prices, no allocations are made. Otherwise, we allocate the transaction price to each performance obligation identified in the contract on a relative SSP basis, except when the criteria are met for allocating variable consideration or a discount to one or more, but not all, performance obligations in the contract.
72
To determine the SSP of our goods or services, we conduct a regular analysis to determine whether various goods or services have an observable SSP. If we do not have an observable SSP for a particular good or service, then SSP for that particular good or service is estimated using an approach that maximizes the use of observable inputs. We generally determine SSPs using various methodologies such as historical prices, expected cost plus margin, adjusted market assessment or non-standalone selling prices.
We recognize revenue as control of the promised goods or services is transferred to our customers, in an amount that reflects the consideration we expect to be entitled to in exchange for the promised goods or services. Revenue is recognized net of any taxes collected from customers and subsequently remitted to governmental authorities. Control of the promised goods or services is transferred to our customers at either a point in time or over time, depending on the performance obligation.
The nature of our promise to the customer to provide our time-based software licenses and related support and maintenance is to stand ready to provide protection for a specified or indefinite period of time. Maintenance and support in these cases are typically not distinct performance obligations as the licenses are dependent upon regular threat updates to the customer. Instead the maintenance and support is combined with a software license to create a single performance obligation. We typically satisfy these performance obligations over time, as control is transferred to the customer as the services are provided.
Additional Revenue Recognition Considerations
Partner Royalty Revenues
Our original equipment manufacturer (“OEM”), mobile and internet service provider (“MISP”) and retail sales channels have revenues derived from sales- or usage-based royalties. Such revenue is excluded from any variable consideration and transaction price calculations and is recognized at the later of when the sale or usage occurs, or the performance obligation is satisfied or partially satisfied.
Consideration Payable to a Customer
We make various payments to our channel partners, which may include revenue share, product placement fees and marketing development funds. Costs that are incremental to revenue, such as revenue share, are capitalized and amortized over time as cost of sales. Product placement fees and marketing development funds are expensed in sales and marketing expense as the related benefit is received and were $185 million, $187 million and $142 million for the years ended December 25, 2021, December 26, 2020, and December 28, 2019, respectively.
Under certain of our channel partner agreements, the partners pay us royalties on our technology sold to their customers, which we recognize as revenue in accordance with our revenue recognition policy. In these situations, the payments made to our channel partners are recognized as consideration paid to a customer, and thus are recorded as reductions to revenue up to the amount of cumulative revenue recognized from the contract with the channel partner during the period of measurement.
Contract Costs
Contract acquisition costs consist mainly of sales commissions and associated fringe benefits, as well as revenue share under programs with certain of our distribution partners. For revenue share, the partner receives a percentage of the revenue we receive from an end user upon conversion to a paid customer or renewal. These costs would not have been incurred if the contract was not obtained and are considered incremental and recoverable costs of obtaining a contract with a customer. These costs are capitalized and amortized over time in accordance with Accounting Standards Codification (“ASC”) 340-40.
Contract fulfillment costs consist of software and related costs. These costs are incremental and recoverable and are capitalized and amortized on a systematic basis that is consistent with the pattern of transfer of the goods and services to which the asset relates.
Discontinued Operations
Certain of our perpetual software licenses or hardware with integrated software are not distinct from their accompanying maintenance and support, as they are dependent upon regular threat updates. These contracts typically contain a renewal option that we have concluded creates a material right for our customer. The license, hardware and maintenance and support revenue is recognized over time, as control is transferred to the customer over the term of the initial contract period while the corresponding material right is recognized over time beginning at the end of the initial contractual period over the remainder of the technology constrained customer life.
Alternatively, certain of our perpetual software licenses, hardware appliances, or hardware with integrated software provide a benefit to the customer that is separable from the related support as they are not dependent upon regular threat updates. Revenue for these products is recognized at a point in time when control is transferred to our customers, generally at shipment. The related maintenance and support represent a separate performance obligation and the associated transaction price allocated to it is recognized over time as control is transferred to the customer.
73
The nature of our promise to the customer to provide our SaaS offerings and related support and maintenance is to stand ready to provide protection for a specified or indefinite period of time. Maintenance and support in these cases are typically not distinct performance obligations as the licenses are dependent upon regular threat updates to the customer. Instead the maintenance and support is combined with a software license to create a single performance obligation. We typically satisfy these performance obligations over time, as control is transferred to the customer as the services are provided.
Revenue for professional services that are a separate and distinct performance obligation is recognized as services are provided to the customer.
Payment Terms and Warranties
Our payment terms vary by the type and location of our customer and the products or services offered. The term between invoicing and when payment is due is not significant. For certain products or services and customer types, we require payment before the products or services are delivered to the customer.
We provide assurance warranties on our products and services. The warranty timeframe varies depending on the product or service sold, and the resolution of any issues is at our discretion to either repair, replace, reperform or refund the fee.
Contract Costs
Contract acquisition costs consist mainly of sales commissions and associated fringe benefits.
We typically recognize the initial commissions that are not commensurate with renewal commissions over the longer of the customer relationship (generally estimated to be four to five years) or over the same period as the initial revenue arrangement to which these costs relate. Renewal commissions paid are generally amortized over the renewal period.
Contract fulfillment costs consist primarily of hardware and related costs. These costs are incremental and recoverable and are capitalized and amortized on a systematic basis that is consistent with the pattern of transfer of the goods and services to which the asset relates.
Goodwill
Goodwill is recorded as the excess of consideration transferred over the acquisition-date fair values of assets acquired and liabilities assumed in a business combination. Historically, we have assigned goodwill to our reporting units based on the relative fair value expected at the time of the acquisition. Goodwill and intangible assets to be disposed of as a result of our agreement with STG to sell certain assets of Enterprise Business were included in assets of discontinued operations in our consolidated balance sheet as of December 26, 2020. We now have one reporting unit for goodwill.
We perform an annual impairment assessment on the first day of the third month in the fourth quarter or more frequently if indicators of potential impairment exist, which includes evaluating qualitative and quantitative factors to assess the likelihood of an impairment of our reporting unit’s goodwill. If the conclusion of an impairment assessment is that it is more likely than not that the fair value is more than its carrying value, goodwill is not considered impaired and we are not required to perform the quantitative goodwill impairment test.
If the conclusion of an impairment assessment is that it is more likely than not that the fair value is less than its carrying value, we perform the quantitative goodwill impairment test, which compares the fair value of the reporting unit to its carrying value. Impairments, if any, are based on the excess of the carrying amount over the fair value. Our goodwill impairment test considers the income method and/or market method to estimate a reporting unit’s fair value.
Identified Intangible Assets
We amortize all finite-lived intangible assets that are subject to amortization over their estimated useful life of economic benefit on a straight-line basis.
For significant intangible assets subject to amortization, we perform a quarterly assessment to determine whether facts and circumstances indicate that the useful life is shorter than we had originally estimated or that the carrying amount of assets may not be recoverable. If such facts and circumstances exist, we assess recoverability by comparing the projected undiscounted net cash flows associated with the related asset or group of assets over their remaining useful lives against their respective carrying amounts. Impairments, if any, are based on the excess of the carrying amount over the fair value of those assets. If an asset’s useful life is shorter than originally estimated, we accelerate the rate of amortization and amortize the remaining carrying value over the updated, shorter useful life.
74
For our intangible assets not subject to amortization, we perform an annual impairment assessment on the first day of the third month in the fourth quarter, or more frequently if indicators of potential impairment exist, to determine whether it is more likely than not that the carrying value of the asset may not be recoverable. If necessary, a quantitative impairment test is performed to compare the fair value of the indefinite-lived intangible asset with its carrying value. Impairments, if any, are based on the excess of the carrying amount over the fair value of the asset.
Research and Development
Costs incurred in the research and development of new software products are expensed as incurred until technological feasibility is established. Research and development costs include salaries and benefits of researchers, supplies, and other expenses incurred during research and development efforts. Development costs are capitalized beginning when a product’s technological feasibility has been established and ending when the product is available for general release to customers. Technological feasibility is reached when the product reaches the working-model stage. To date, new products and enhancements generally have reached technological feasibility and have been released for sale at substantially the same time. All research and development costs to date have been expensed as incurred except for software subject to a hosting arrangement.
Software development costs of both internal-use applications and software sold subject to hosting arrangements are capitalized when we have determined certain factors are present, including factors that indicate technology exists to achieve the performance requirements, the decision has been made to develop internally versus buy and our management has authorized the funding for the project. Capitalization of software costs ceases when the software is substantially complete and is ready for its intended use and capitalized costs are amortized over their estimated useful life of three to five years using the straight-line method. When events or circumstances indicate the carrying value of internal use software might not be recoverable, we assess the recoverability of these assets by determining whether the amortization of the asset balance over its remaining life can be recovered through undiscounted future operating cash flows.
Equity-Based Awards
We currently provide various equity-based compensation to those whom, in the opinion of the Board or its designee, are in a position to make a significant contribution to our success.
Equity-based compensation cost is measured at the grant date based on the fair value of the award and recognized as expense over the appropriate service period. Determining the fair value of equity-based awards requires considerable judgment, including assumptions and estimates of the following:
Before our IPO, the fair value of the unit was determined by the Board reasonably and in good faith. Generally, this involved a review by an independent valuation of our business, which requires judgmental inputs and assumptions such as our cash flow projections, peer company comparisons, market data, growth rates and discount rate. The Board reviewed its prior determination of fair value of a unit on a quarterly basis to decide whether any change was appropriate (including whether to obtain a new independent valuation), considering such factors as any significant financial, operational, or market changes affecting the business since the last valuation date. Due to us not having sufficient historical volatility, we used the historical volatilities of publicly traded companies which were similar to us in size, stage of life cycle and financial leverage. We continued to use this peer group of companies unless a situation arose within the group that would require evaluation of which publicly traded companies were included or once sufficient data was available to use our own historical volatility. In addition, for awards where vesting was dependent upon achieving certain operating performance goals, we estimated the likelihood of achieving the performance goals. For goals dependent upon a qualifying liquidity event, (i.e., a change of control or public offering registered on a Form S-1 (or successor form), in either case, occurring on or before April 3, 2024) (a “Qualifying Liquidity Event”), we would not recognize any expense until the event occurs. Upon consummation of our IPO, we recognized a cumulative catch-up of expense based on the vesting dates for our time-based awards and expected vesting dates for our performance-based awards. We recognize forfeitures as they occur. For awards with only time-vesting requirement, we recognize the expense over a straight-line basis during the vesting period.
After the close of our IPO, our outstanding Management Equity Participation Units (“MEPUs”) and Cash RSU (“CRSUs”) were converted into RSUs (“Replacement RSUs”), which are to be settled in Class A common stock. The fair value of these Replacement RSUs was our IPO price less the present value of the expected dividends not received during the vesting period. For all other RSU grants after our IPO, we utilize the closing price of our common stock on the day of the grant date, less the present value of expected dividends not received during the vesting period to determine grant date fair value.
75
In addition, certain MEPU holders were also granted stock options with a strike price equal to our IPO price. For all other stock option grants after our IPO, we utilize the closing price of our common stock on the day of grant date to determine the strike price. All of our granted stock options are non-qualified and expire 10 years after grant. We utilize a Black-Scholes model to determine grant date fair value of our stock options.
Our time-based awards generally vest evenly over the 16 quarters following grant date. For time-based awards granted to our new hires, the vesting period is generally 25% vest one year after grant date and quarterly thereafter for 12 quarters. Time-based awards granted to our non-employee directors vest one year from grant date. Generally, unvested awards are forfeited upon termination of employment with us, however, our executive officers may have provisions permitting acceleration or pro rata acceleration upon termination without cause (as defined in the respective award agreements).
Our performance-based RSU awards (“PSUs”) are granted to executive officers and certain employees annually. These awards vest after approximately three years, with the number vesting based upon internal profitability targets that are communicated to employees in the year to which the targets relate. The number of shares of common stock issued will range from zero to stretch, with stretch typically defined as 130% of target. At the time our Board approves such grants, the targets for performance years other than the current year are not known or knowable by us nor our employees. Upon determination and communication of such targets in future years, grant date fair value is determined based upon the closing price, less the present value of expected dividends not received during the vesting period.
A portion of our RSU awards and all of our performance-based stock option and performance-based MIU awards vest upon achievement of certain return of cash metrics. In January 2021, these awards were modified to vest annually in equal tranches over the three year anniversaries of our IPO. If the original return of cash performance is achieved prior to such anniversaries, the awards vest in full. In both cases, the unvested portion of the awards are forfeited upon termination.
Upon the settlement of RSUs, we withhold a portion of the earned units to cover no more than the maximum statutory income and employment taxes and remit the net shares to an individual brokerage account. Authorized shares of our common stock are used to settle RSUs and stock options.
Awards granted prior to our IPO and/or converted at the time of our IPO are covered under our 2017 Management Incentive Plan (“2017 Plan”). Stock options granted at our IPO and/or awards granted at our IPO or after are covered under our 2020 Equity Omnibus Plan (“2020 Plan”). No new awards may be authorized under our 2017 Plan.
Derivative and Hedging Instruments
The fair values of each of our derivative instruments are recorded as an asset or liability on a net basis at the balance sheet date within other current or long-term assets or liabilities. The change in fair value of our derivative instruments is recorded through earnings in the line item on the consolidated statements of operations to which the derivatives most closely relate, primarily in Interest expense. Changes in the fair value of the underlying assets and liabilities associated with the hedged risk are generally offset by the changes in the fair value of the related derivatives. We do not use derivative financial instruments for speculative trading purposes.
To reduce the interest rate risk inherent in variable rate debt, we entered into certain interest rate swap agreements to convert a portion of our variable rate borrowing into a fixed rate obligation (Note 15). These interest rate swap agreements fix the London Interbank Offered Rate (“LIBOR”) portion of the U.S. dollar denominated variable rate borrowings. Accordingly, to the extent the cash flow hedge is effective, changes in the fair value of interest rate swaps will be included within Accumulated other comprehensive income (loss) in the consolidated balance sheets. Hedge accounting will be discontinued when the interest rate swap is no longer effective in offsetting cash flows attributable to the hedged risk, the interest rate swap expires or the cash flow hedge is dedesignated because it is no longer probable that the forecasted transaction will occur according to the original strategy. When hedge accounting is discontinued, any related amounts previously included in Accumulated other comprehensive income (loss) would be reclassified to Interest expense, within the consolidated statements of operations.
Leases
We adopted ASC No. 2016-02, Leases, and all related updates (collectively, “Topic 842”), which primarily requires leases to be recognized on the balance sheet. We adopted the standard using the modified retrospective approach with an effective date as of the beginning of our 2019 fiscal year, December 30, 2018.
We determine if an arrangement contains a lease and classification of that lease, if applicable, at inception based on:
76
Right-of-use (“ROU”) assets represent the right to use an underlying asset for the lease term and lease liabilities represent the obligation to make minimum lease payments arising from the lease. A ROU asset is initially measured at an amount which represents the lease liability, plus any initial direct costs incurred and less any lease incentives received. The lease liability is initially measured at lease commencement date based on the present value of minimum lease payments over the lease term. The lease term may include options to extend or terminate when it is reasonably certain that we will exercise the option. We have lease agreements with lease and non-lease components, and the non-lease components are generally accounted for separately and not included in our leased assets and corresponding liabilities.
The depreciable life of assets and leasehold improvements are limited by the expected lease term unless there is a transfer of title or purchase option reasonably certain of exercise. Payments related to short-term leases are expensed on a straight-line basis over the lease term and reflected as a component of lease cost within our consolidated statements of operations. Lease payments generally consist of fixed amounts, as well as variable amounts based on a market rate or an index which are not material to our consolidated lease cost. Our leases do not contain significant terms and conditions for variable lease payments.
When available, we use the rate implicit in the lease to discount lease payments to present value; however, most of our leases do not provide a readily determinable implicit rate. Therefore, we estimate our incremental borrowing rate to discount the lease payments based on information available at lease commencement. For leases which commenced prior to our adoption of ASC Topic 842, we estimated our incremental borrowing rate as of adoption date based on our credit rating, current economic conditions, and collateralized borrowing.
Discontinued Operations
We review the presentation of planned business dispositions in the consolidated financial statements based on the available information and events that have occurred. The review consists of evaluating whether the business meets the definition of a component for which the operations and cash flows are clearly distinguishable from the other components of the business, and if so, whether it is anticipated that after the disposal the cash flows of the component would be eliminated from continuing operations and whether the disposition represents a strategic shift that has a major effect on operations and financial results. In addition, we evaluate whether the business has met the criteria as a business held for sale. In order for a planned disposition to be classified as a business held for sale, the established criteria must be met as of the reporting date, including an active program to market the business and the expected disposition of the business within one year.
Planned business dispositions are presented as discontinued operations when all the criteria described above are met. For those divestitures that qualify as discontinued operations, all comparative periods presented are reclassified in the consolidated balance sheets. Additionally, the results of operations of a discontinued operation are reclassified to income from discontinued operations, net of tax, for all periods presented in the consolidated statements of operations. Results of discontinued operations include all revenues and expenses directly derived from such businesses; general corporate overhead is not allocated to discontinued operations.
Income Tax
McAfee Corp. is taxed as a corporation and pays corporate federal, state and local taxes on income allocated to it from FTW based upon McAfee Corp.’s economic interest in FTW. FTW is a pass through entity for U.S. federal income tax purposes and will not incur any federal income taxes either for itself or its U.S. subsidiaries that are also pass through or disregarded subsidiaries. Taxable income or loss for these entities will flow through to its respective members for U.S. tax purposes. FTW does have certain U.S. and foreign subsidiaries that are corporations and are subject to income tax in their respective jurisdiction.
We account for income taxes under the asset and liability method, which requires the recognition of deferred tax assets and liabilities (“DTAs” and “DTLs”) for the expected future tax consequences of events that have been included in the financial statements. Under this method, we determine DTAs and DTLs on the basis of the differences between the financial statement and tax bases of assets and liabilities by using enacted tax rates in effect for the year in which the differences are expected to reverse. The effect of a change in tax rates on DTAs and DTLs is recognized in income in the period that includes the enactment date. We recognize DTAs to the extent that we believe that these assets are more likely than not to be realized. In making such a determination, we consider all available positive and negative evidence, including future reversals of existing taxable temporary differences, projected future taxable income, tax-planning strategies, carryback potential if permitted under the tax law, and results of recent operations. If we determine that we would be able to realize our DTAs in the future in excess of their net recorded amount, we would make an adjustment to the DTA valuation allowance, which would reduce the provision for income taxes. We record uncertain tax positions in accordance with ASC 740 on the basis of a two-step process in which (1) we determine whether it is more likely than not that the tax positions will be sustained on the basis of the technical merits of the position and (2) for those tax positions that meet the more-likely-than-not recognition threshold, we recognize the largest amount of tax benefit that is more than 50 percent likely to be realized upon ultimate settlement with the related tax authority.
77
Tax Receivable Agreement
Pursuant to our election under Section 754 of the Internal Revenue Code (the “Code”), we expect to obtain an increase in our share of the tax basis in the net assets of FTW when FTW LLC Units are redeemed or exchanged by the Continuing LLC Owners and MIUs are redeemed or exchanged by Management Owners. We intend to treat any redemptions and exchanges of LLC Units as direct purchases of LLC Units for United States federal income tax purposes. These increases in tax basis may reduce the amounts that we would otherwise pay in the future to various tax authorities. They may also decrease gains (or increase losses) on future dispositions of certain capital assets to the extent tax basis is allocated to those capital assets.
In October 2020, we entered into a TRA that provides for the payment by us of 85% of the amount of any tax benefits that we actually realize, or in some cases are deemed to realize, as a result of: (i) all or a portion of the Corporation’s allocable share of existing tax basis in the assets of FTW (and its subsidiaries) acquired in connection with the Reorganization Transactions, (ii) increases in the Corporation’s allocable share of existing tax basis in the assets of FTW (and its subsidiaries) and tax basis adjustments in the assets of FTW (and its subsidiaries) as a result of sales or exchanges of LLC Units after the IPO, (iii) certain tax attributes of the corporations acquired by McAfee Corp. in connection with the Reorganization Transactions (including their allocable share of existing tax basis in the assets of FTW (and its subsidiaries)), and (iv) certain other tax benefits related to entering into the tax receivable agreement, including tax benefits attributable to payments under the tax receivable agreement. The Corporation generally will retain the benefit of the remaining 15% of the applicable tax savings. The payment obligations under the tax receivable agreement are obligations of the Corporation. The timing and amount of aggregate payments due under the TRA may vary based on a number of factors, including the timing and amount of taxable income generated by the Corporation each year, as well as the tax rate then applicable.
Recent Accounting Pronouncements
See Note 3 to the consolidated financial statements (Part II, Item 8 of this Form 10-K) for further discussion.
78
Item 7A. Quantitative and Qualitative Disclosures About Market Risk.
We are exposed to certain risk arising from both our business operations and economic conditions. We principally manage our exposure to a wide variety of business and operational risks through management of our core business activities. We manage economic risks, including interest rate, liquidity, and credit risk primarily by managing the amount, sources, and duration of our debt funding and through the use of derivative financial instruments.
Foreign Currency Exchange Risk
Our sales contracts are primarily denominated in U.S. dollars. A portion of our operating expenses are incurred outside of the United States and are denominated in foreign currencies and are subject to fluctuations due to changes in foreign currency exchange rates, particularly changes in the Euro, Argentine Peso, Indian Rupee, British Pound Sterling, Australian Dollar, and Japanese Yen. Additionally, fluctuations in foreign currency exchange rates may cause us to recognize transaction gains and losses in our consolidated statement of operations. The effect of an immediate 10% adverse change in foreign exchange rates on monetary assets and liabilities at December 25, 2021 would not be material to our financial condition or results of operations. To date, foreign currency transaction gains and losses and exchange rate fluctuations have not been material to our consolidated financial statements, and we have not engaged in any foreign currency hedging transactions.
As our international operations continue to grow, our risks associated with fluctuation in currency rates will become greater, and we will continue to reassess our approach to managing this risk, such as using foreign currency forward and option contracts to hedge certain exposures to fluctuations in foreign currency exchange rates. In addition, currency fluctuations or a weakening U.S. dollar can increase the costs of our international expansion, and the currently strengthening U.S. dollar could slow international demand as products and services priced in the U.S. dollar become more expensive.
Interest Rate Risk
We utilize long-term debt to, among other things, finance our acquisitions and, to a lesser extent, our operations. We are exposed to interest rate risk on our outstanding floating rate debt instruments which bear interest at rates that fluctuate with changes in certain short-term prevailing interest rates. Borrowings under the Senior Secured Credit Facilities bear interest at a Euro currency rate determined by reference to LIBOR, plus an applicable margin, subject to established floors of 0.00%. During the years ended December 25, 2021 and December 26, 2020, applicable interest rates have been lower than the designated floors under our Senior Secured Credit Facilities; therefore, interest rates under the Senior Secured Credit Facilities have not been subject to change. Assuming that the rates remain below the applicable floors under the Senior Secured Credit Facilities, a 25 basis point increase or decrease in the applicable interest rates on our variable rate debt, excluding debt outstanding under the Senior Secured Credit Facilities, would result in a minor change in interest expense on an annual basis.
In 2018 and through 2021, we entered into multiple interest rate swaps in order to fix a substantial amount of the LIBOR portion of our USD denominated variable rate borrowings. Our derivative financial instruments are used to manage differences in the amount, timing, and duration of the our known or expected cash payments principally related to our variable-rate borrowings.
A hypothetical 10% increase or decrease in interest rates during any of the periods presented would not have had a material impact on our interest expense.
Inflation Rate Risk
We do not believe that inflation has had a material effect on our business, financial condition or results of operations. Nonetheless, if our costs were to become subject to significant inflationary pressures, we may not be able to fully offset such higher costs through price increases. Our inability or failure to do so could harm our business, financial condition, and results of operations.
79
Item 8. Financial Statements and Supplementary Data
Index to Consolidated Financial Statements |
|
|
|
|
Page |
|
|
Report of Independent Registered Public Accounting Firm (PCAOB ID |
81 |
Consolidated Balance Sheets as of December 25, 2021 and December 26, 2020 |
83 |
84 |
|
85 |
|
86 |
|
87 |
|
89 |
|
80
Report of Independent Registered Public Accounting Firm
To the Board of Directors and Stockholders of McAfee Corp.
Opinions on the Financial Statements and Internal Control over Financial Reporting
We have audited the accompanying consolidated balance sheets of McAfee Corp. and its subsidiaries (the “Company”) as of December 25, 2021 and December 26, 2020, and the related consolidated statements of operations, of comprehensive income (loss), of equity (deficit) and redeemable noncontrolling interests and of cash flows for each of the three years in the period ended December 25, 2021, including the related notes (collectively referred to as the “consolidated financial statements”). We also have audited the Company's internal control over financial reporting as of December 25, 2021, based on criteria established in Internal Control - Integrated Framework (2013) issued by the Committee of Sponsoring Organizations of the Treadway Commission (COSO).
In our opinion, the consolidated financial statements referred to above present fairly, in all material respects, the financial position of the Company as of December 25, 2021 and December 26, 2020, and the results of its operations and its cash flows for each of the three years in the period ended December 25, 2021 in conformity with accounting principles generally accepted in the United States of America. Also in our opinion, the Company maintained, in all material respects, effective internal control over financial reporting as of December 25, 2021, based on criteria established in Internal Control - Integrated Framework (2013) issued by the COSO.
Change in Accounting Principle
As discussed in Note 2 to the consolidated financial statements, the Company changed the manner in which it accounts for leases in fiscal 2019.
Basis for Opinions
The Company's management is responsible for these consolidated financial statements, for maintaining effective internal control over financial reporting, and for its assessment of the effectiveness of internal control over financial reporting, included in Management’s Report on Internal Control Over Financial Reporting appearing under Item 9A. Our responsibility is to express opinions on the Company’s consolidated financial statements and on the Company's internal control over financial reporting based on our audits. We are a public accounting firm registered with the Public Company Accounting Oversight Board (United States) (PCAOB) and are required to be independent with respect to the Company in accordance with the U.S. federal securities laws and the applicable rules and regulations of the Securities and Exchange Commission and the PCAOB.
We conducted our audits in accordance with the standards of the PCAOB. Those standards require that we plan and perform the audits to obtain reasonable assurance about whether the consolidated financial statements are free of material misstatement, whether due to error or fraud, and whether effective internal control over financial reporting was maintained in all material respects.
Our audits of the consolidated financial statements included performing procedures to assess the risks of material misstatement of the consolidated financial statements, whether due to error or fraud, and performing procedures that respond to those risks. Such procedures included examining, on a test basis, evidence regarding the amounts and disclosures in the consolidated financial statements. Our audits also included evaluating the accounting principles used and significant estimates made by management, as well as evaluating the overall presentation of the consolidated financial statements. Our audit of internal control over financial reporting included obtaining an understanding of internal control over financial reporting, assessing the risk that a material weakness exists, and testing and evaluating the design and operating effectiveness of internal control based on the assessed risk. Our audits also included performing such other procedures as we considered necessary in the circumstances. We believe that our audits provide a reasonable basis for our opinions.
Definition and Limitations of Internal Control over Financial Reporting
A company’s internal control over financial reporting is a process designed to provide reasonable assurance regarding the reliability of financial reporting and the preparation of financial statements for external purposes in accordance with generally accepted accounting principles. A company’s internal control over financial reporting includes those policies and procedures that (i) pertain to the maintenance of records that, in reasonable detail, accurately and fairly reflect the transactions and dispositions of the assets of the company; (ii) provide reasonable assurance that transactions are recorded as necessary to permit preparation of financial statements in accordance with generally accepted accounting principles, and that receipts and expenditures of the company are being made only in accordance with authorizations of management and directors of the company; and (iii) provide reasonable assurance regarding prevention or timely detection of unauthorized acquisition, use, or disposition of the company’s assets that could have a material effect on the financial statements.
81
Because of its inherent limitations, internal control over financial reporting may not prevent or detect misstatements. Also, projections of any evaluation of effectiveness to future periods are subject to the risk that controls may become inadequate because of changes in conditions, or that the degree of compliance with the policies or procedures may deteriorate.
Critical Audit Matters
The critical audit matter communicated below is a matter arising from the current period audit of the consolidated financial statements that was communicated or required to be communicated to the audit committee and that (i) relates to accounts or disclosures that are material to the consolidated financial statements and (ii) involved especially challenging, subjective, or complex judgments. The communication of critical audit matters does not alter in any way our opinion on the consolidated financial statements, taken as a whole, and we are not, by communicating the critical audit matter below, providing a separate opinion on the critical audit matter or on the accounts or disclosures to which it relates.
Tax Receivable Agreement (“TRA”) Liability
As described in Notes 1 and 14 to the consolidated financial statements, the Company has recorded a liability under the Tax Receivable Agreement (“TRA”) of $434 million as of December 25, 2021. Prior to the initial public offering in October 2020, the Company entered into a TRA with the Continuing Owners and certain Management Owners (collectively, the “TRA Beneficiaries”). The TRA provides for the payment by the Company of 85% of the amount of any tax benefits recognized resulting from its future taxable income. As disclosed by management, obligations under the TRA are recognized by management after concluding that it is probable that the Company would have sufficient future taxable income to realize the benefit. On July 27, 2021, the Company completed the divestiture of the Enterprise Business and as a result, management expects to utilize certain deferred tax assets. As the net deferred tax assets have been recognized as of the date of divestiture, the TRA liability also became probable. The determination of the TRA liability involves the interpretation and application of complex tax laws and regulations. The key inputs used by management in the calculation of the TRA liability included the partnership tax basis, net operating losses (“NOLs”), and foreign tax credits.
The principal considerations for our determination that performing procedures relating to the TRA liability is a critical audit matter are (i) the significant judgment by management when determining the TRA liability, including interpretation and application of complex tax laws and regulations, (ii) a high degree of auditor judgment, subjectivity, and effort in performing procedures and evaluating management’s determination of the TRA liability and key inputs related to partnership tax basis, NOLs, and foreign tax credits, and (ii) the audit effort involved the use of professionals with specialized skill and knowledge.
Addressing the matter involved performing procedures and evaluating audit evidence in connection with forming our overall opinion on the consolidated financial statements. These procedures included testing the effectiveness of controls relating to management’s determination of the TRA liability, including controls over the development of key inputs related to partnership tax basis, NOLs, and foreign tax credits. These procedures also included, among others (i) testing management’s process for determining the TRA liability; (ii) testing the completeness and accuracy of the underlying data used in the calculation of the TRA Liability; (iii) evaluating the appropriateness of the methodology used to calculate the TRA liability including testing the calculation; and (iv) evaluating the reasonableness of the partnership tax basis, NOLs, and foreign tax credits key inputs used by management. Evaluating management’s key inputs involved, on a test basis, testing the (i) existence, completeness and accuracy of the NOLs and foreign tax credits and; (ii) completeness and accuracy of the partnership income and partnership tax basis allocated to the TRA beneficiaries. Professionals with specialized skill and knowledge were used to assist in evaluating the interpretation and application of the complex tax laws and regulations.
/s/
February 23, 2022
We have served as the Company's or its predecessor’s auditor since 2017.
82
MCAFEE CORP.
CONSOLIDATED BALANCE SHEETS
(in millions, except share and per share amounts)
|
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Assets |
|
|
|
|
|
|
||
Current assets: |
|
|
|
|
|
|
||
Cash and cash equivalents |
|
$ |
|
|
$ |
|
||
Accounts receivable, net |
|
|
|
|
|
|
||
Deferred costs |
|
|
|
|
|
|
||
Receivable from Enterprise Business |
|
|
|
|
|
|
||
Other current assets |
|
|
|
|
|
|
||
Current assets of discontinued operations |
|
|
|
|
|
|
||
Total current assets |
|
|
|
|
|
|
||
Property and equipment, net |
|
|
|
|
|
|
||
Goodwill |
|
|
|
|
|
|
||
Identified intangible assets, net |
|
|
|
|
|
|
||
Deferred tax assets |
|
|
|
|
|
|
||
Other long-term assets |
|
|
|
|
|
|
||
Long-term assets of discontinued operations |
|
|
|
|
|
|
||
Total assets |
|
$ |
|
|
$ |
|
||
Liabilities, redeemable noncontrolling interests and deficit |
|
|
|
|
|
|
||
Current liabilities: |
|
|
|
|
|
|
||
Accounts payable and other current liabilities |
|
$ |
|
|
$ |
|
||
Accrued compensation and benefits |
|
|
|
|
|
|
||
Accrued marketing |
|
|
|
|
|
|
||
Income taxes payable |
|
|
|
|
|
|
||
Long-term debt, current portion |
|
|
|
|
|
|
||
Deferred revenue |
|
|
|
|
|
|
||
Payable to Enterprise Business |
|
|
|
|
|
|
||
Current liabilities of discontinued operations |
|
|
|
|
|
|
||
Total current liabilities |
|
|
|
|
|
|
||
Long-term debt, net |
|
|
|
|
|
|
||
Deferred tax liabilities |
|
|
|
|
|
|
||
Tax receivable agreement liability, less current portion |
|
|
|
|
|
|
||
Other long-term liabilities |
|
|
|
|
|
|
||
Deferred revenue, less current portion |
|
|
|
|
|
|
||
Long-term liabilities of discontinued operations |
|
|
|
|
|
|
||
Total liabilities |
|
|
|
|
|
|
||
) |
|
|
|
|
|
|
||
Redeemable noncontrolling interests |
|
|
|
|
|
|
||
Equity (deficit): |
|
|
|
|
|
|
||
Class A common stock, $ |
|
|
|
|
|
|
||
Class B common stock, $ |
|
|
|
|
|
|
||
Additional paid-in capital |
|
|
( |
) |
|
|
( |
) |
Retained earnings (accumulated deficit) |
|
|
|
|
|
( |
) |
|
Accumulated other comprehensive income (loss) |
|
|
( |
) |
|
|
( |
) |
Total deficit |
|
|
( |
) |
|
|
( |
) |
Total liabilities, redeemable noncontrolling interests and deficit |
|
$ |
|
|
$ |
|
||
See the accompanying notes to the consolidated financial statements
83
MCAFEE CORP.
CONSOLIDATED STATEMENTS OF OPERATIONS
(in millions except per share amounts)
|
|
Year Ended |
|
|||||||||
|
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Net revenue |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Cost of sales |
|
|
|
|
|
|
|
|
|
|||
Gross profit |
|
|
|
|
|
|
|
|
|
|||
Operating expenses: |
|
|
|
|
|
|
|
|
|
|||
Sales and marketing |
|
|
|
|
|
|
|
|
|
|||
Research and development |
|
|
|
|
|
|
|
|
|
|||
General and administrative |
|
|
|
|
|
|
|
|
|
|||
Amortization of intangibles |
|
|
|
|
|
|
|
|
|
|||
Restructuring and transition charges (Note 9) |
|
|
|
|
|
|
|
|
|
|||
Total operating expenses |
|
|
|
|
|
|
|
|
|
|||
Operating income |
|
|
|
|
|
|
|
|
|
|||
Interest expense |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Foreign exchange gain (loss), net |
|
|
|
|
|
( |
) |
|
|
|
||
Other income (expense), net |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Income (loss) from continuing operations before income taxes |
|
|
|
|
|
( |
) |
|
|
( |
) |
|
Provision for income tax expense (benefit) |
|
|
( |
) |
|
|
|
|
|
|
||
Income (loss) from continuing operations |
|
|
|
|
|
( |
) |
|
|
( |
) |
|
Income (loss) from discontinued operations, net of taxes |
|
|
|
|
|
( |
) |
|
|
( |
) |
|
Net income (loss) |
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|
Less: Net income (loss) attributable to redeemable noncontrolling interests |
|
|
|
|
|
( |
) |
|
N/A |
|
||
Net income (loss) attributable to McAfee Corp. |
|
$ |
|
|
$ |
( |
) |
|
N/A |
|
||
|
|
|
|
|
|
|
|
|
|
|||
Net income (loss) attributable to McAfee Corp.: |
|
|
|
|
|
|
|
|
|
|||
Income (loss) from continuing operations attributable to McAfee Corp. |
|
$ |
|
|
$ |
( |
) |
|
N/A |
|
||
Income (loss) from discontinued operations attributable to McAfee Corp. |
|
|
|
|
|
( |
) |
|
N/A |
|
||
Net income (loss) attributable to McAfee Corp. |
|
$ |
|
|
$ |
( |
) |
|
N/A |
|
||
|
|
|
|
|
|
|
|
|
|
|||
Earnings (loss) per share attributable to McAfee Corp., basic: |
|
|
|
|
|
|
|
|
|
|||
Continuing operations |
|
$ |
|
|
$ |
( |
) |
|
N/A |
|
||
Discontinued operations |
|
|
|
|
|
( |
) |
|
N/A |
|
||
Earnings (loss) per share, basic(1) |
|
$ |
|
|
$ |
( |
) |
|
N/A |
|
||
|
|
|
|
|
|
|
|
|
|
|||
Earnings (loss) per share attributable to McAfee Corp., diluted: |
|
|
|
|
|
|
|
|
|
|||
Continuing operations |
|
$ |
|
|
$ |
( |
) |
|
N/A |
|
||
Discontinued operations |
|
|
|
|
|
( |
) |
|
N/A |
|
||
Earnings (loss) per share, diluted(1) |
|
$ |
|
|
$ |
( |
) |
|
N/A |
|
||
|
|
|
|
|
|
|
|
|
|
|||
Weighted-average shares outstanding, basic |
|
|
|
|
|
|
|
N/A |
|
|||
Weighted-average shares outstanding, diluted |
|
|
|
|
|
|
|
N/A |
|
|||
See the accompanying notes to the consolidated financial statements
84
MCAFEE CORP.
CONSOLIDATED STATEMENTS OF COMPREHENSIVE INCOME (LOSS)
(in millions)
|
|
Year Ended |
|
|||||||||
|
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Net income (loss) |
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|
Other comprehensive income (loss): |
|
|
|
|
|
|
|
|
|
|||
Interest rate cash flow hedges: |
|
|
|
|
|
|
|
|
|
|||
Gain (loss) on interest rate cash flow hedges, net of tax |
|
|
|
|
|
( |
) |
|
|
( |
) |
|
Reclassification adjustments for income on interest rate |
|
|
|
|
|
|
|
|
|
|||
Pension and postretirement benefits income (loss), net of tax |
|
|
|
|
|
( |
) |
|
|
( |
) |
|
Total comprehensive income (loss) |
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|
Less: Comprehensive income (loss) attributable to redeemable |
|
|
|
|
|
( |
) |
|
N/A |
|
||
Total comprehensive income (loss) attributable to McAfee Corp. |
|
$ |
|
|
$ |
( |
) |
|
N/A |
|
||
See the accompanying notes to the consolidated financial statements
85
MCAFEE CORP.
CONSOLIDATED STATEMENTS OF CASH FLOWS
(in millions)
|
|
Year Ended |
|
|||||||||
|
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
|
|
|
|
|
|
|
|
|
|
|||
Cash flows from operating activities: |
|
|
|
|
|
|
|
|
|
|||
Net income (loss) |
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|
Adjustments to reconcile net income (loss) to net cash provided by operating activities: |
|
|
|
|
|
|
|
|
|
|||
Depreciation and amortization |
|
|
|
|
|
|
|
|
|
|||
Equity-based compensation |
|
|
|
|
|
|
|
|
|
|||
Deferred taxes |
|
|
( |
) |
|
|
( |
) |
|
|
|
|
Foreign exchange (gain) loss, net |
|
|
( |
) |
|
|
|
|
|
( |
) |
|
Pre-tax gain on divestiture of Enterprise Business |
|
|
( |
) |
|
|
— |
|
|
|
|
|
Tax Receivable Agreement remeasurement |
|
|
|
|
|
|
|
|
— |
|
||
Other operating activities |
|
|
|
|
|
|
|
|
|
|||
Change in assets and liabilities: |
|
|
|
|
|
|
|
|
|
|||
Receivable and payable from/to Enterprise Business |
|
|
( |
) |
|
|
— |
|
|
|
— |
|
Accounts receivable, net |
|
|
|
|
|
|
|
|
( |
) |
||
Deferred costs |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Other assets |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Income taxes payable |
|
|
|
|
|
( |
) |
|
|
|
||
Other current liabilities |
|
|
|
|
|
|
|
|
|
|||
Deferred revenue |
|
|
|
|
|
|
|
|
|
|||
Other liabilities |
|
|
( |
) |
|
|
( |
) |
|
|
|
|
Net cash provided by operating activities |
|
|
|
|
|
|
|
|
|
|||
Cash flows from investing activities: |
|
|
|
|
|
|
|
|
|
|||
Acquisitions, net of cash acquired |
|
|
|
|
|
( |
) |
|
|
( |
) |
|
Additions to property and equipment |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Proceeds from divestiture of Enterprise Business, net of transaction costs (Note 4) |
|
|
|
|
|
|
|
|
|
|||
Proceeds from disposal of property, net |
|
|
|
|
|
|
|
|
|
|||
Other investing activities |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Net cash provided by (used in) investing activities |
|
|
|
|
|
( |
) |
|
|
( |
) |
|
Cash flows from financing activities: |
|
|
|
|
|
|
|
|
|
|||
Proceeds from IPO, net of underwriters discount and commissions |
|
|
|
|
|
|
|
|
|
|||
Use of proceeds from issuance of Class A common stock to purchase |
|
|
|
|
|
( |
) |
|
|
|
||
Proceeds from issuance of equity |
|
|
|
|
|
|
|
|
|
|||
Payment for long-term debt |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Proceeds from long-term debt |
|
|
|
|
|
|
|
|
|
|||
Payment for debt issuance costs |
|
|
|
|
|
( |
) |
|
|
( |
) |
|
Distributions to members of FTW |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Payment of dividends |
|
|
( |
) |
|
|
|
|
|
|
||
Payment of tax withholding for shares and units withheld |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Payment of IPO related expenses |
|
|
( |
) |
|
|
( |
) |
|
|
|
|
Other financing activities |
|
|
|
|
|
( |
) |
|
|
( |
) |
|
Net cash used in financing activities |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Effect of exchange rate fluctuations on cash and cash equivalents |
|
|
( |
) |
|
|
|
|
|
|
||
Change in cash and cash equivalents |
|
|
|
|
|
|
|
|
( |
) |
||
Cash and cash equivalents, beginning of period |
|
|
|
|
|
|
|
|
|
|||
Cash and cash equivalents, end of period |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Supplemental disclosures of noncash investing and financing activities and cash flow information: |
|
|
|
|
|
|
|
|
|
|||
Acquisition of property and equipment included in current liabilities |
|
$ |
( |
) |
|
$ |
( |
) |
|
$ |
( |
) |
Distributions to members of FTW included in liabilities |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Dividends payable included in liabilities |
|
|
|
|
|
( |
) |
|
|
|
||
Tax withholding for shares and units withheld included in liabilities |
|
|
|
|
|
( |
) |
|
|
|
||
Proceeds receivable related to divestiture of Enterprise Business |
|
|
|
|
|
|
|
|
|
|||
Transaction costs payable related to divestiture of Enterprise Business |
|
|
( |
) |
|
|
|
|
|
|
||
Other |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Cash paid during the period for: |
|
|
|
|
|
|
|
|
|
|||
Interest, net of cash flow hedges |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Income taxes, net of refunds |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
See the accompanying notes to the consolidated financial statements
86
MCAFEE CORP.
CONSOLIDATED STATEMENTS OF EQUITY (DEFICIT) AND REDEEMABLE NONCONTROLLING INTERESTS
(in millions, except share amounts)
|
|
Foundation Technology Worldwide, LLC |
|
McAfee Corp. Stockholders' Equity |
|
|
|
|
|
|
|
|
||||||||||||||||||||||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
Class A Common Stock |
|
|
Class B Common Stock |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||||||||||||
|
|
Accumulated |
|
|
Members’ |
|
|
Accumulated |
|
|
|
Shares |
|
|
Amount |
|
|
Shares |
|
|
Amount |
|
|
Additional |
|
|
Retained Earnings (Accumulated |
|
|
Accumulated |
|
|
Total |
|
|
|
Redeemable |
|
|
Total |
|
|||||||||||||
Balance at December 29, 2018 |
|
$ |
|
|
$ |
|
|
$ |
( |
) |
|
|
|
|
|
$ |
|
|
|
|
|
$ |
|
|
$ |
|
|
$ |
|
|
$ |
|
|
$ |
|
|
|
$ |
— |
|
|
$ |
( |
) |
||||||||||
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
( |
) |
|
Distributions to Members |
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
( |
) |
Other comprehensive loss, net of tax |
|
|
( |
) |
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
( |
) |
Equity-based awards expense, net of equity withheld to cover taxes |
|
|
— |
|
|
|
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
|
||
Unit issuances |
|
|
— |
|
|
|
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
|
||
Unit repurchases |
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
( |
) |
Net loss |
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
( |
) |
Balance at December 28, 2019 |
|
$ |
( |
) |
|
$ |
( |
) |
|
$ |
( |
) |
|
|
|
|
|
$ |
|
|
|
|
|
$ |
|
|
$ |
|
|
$ |
|
|
$ |
|
|
$ |
|
|
|
$ |
|
|
$ |
( |
) |
|||||||||
Activity prior to Reorganization Transactions and IPO |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||||||
Distributions to Members |
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
( |
) |
Other comprehensive loss, net of tax |
|
|
( |
) |
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
( |
) |
Equity-based awards expense, net of equity withheld to cover taxes |
|
|
— |
|
|
|
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
|
||
Unit issuances |
|
|
— |
|
|
|
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
|
||
Unit repurchases (Note 8) |
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
( |
) |
Reclassification of redeemable units (Note 7) |
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
( |
) |
Reclassification of redeemable units (Note 7) |
|
|
— |
|
|
|
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
|
||
Net income |
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
|
||
Other |
|
|
— |
|
|
|
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
|
||
Activity in connection with Reorganization Transactions and IPO |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||||||
Impact of reorganization transactions |
|
|
|
|
|
|
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
( |
) |
|
|
( |
) |
|
|
|
— |
|
|
|
— |
|
|||
Issuance of Class A common stock, net of costs |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
Issuance of Class B common stock |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
Initial effect of the Reorganization Transactions and IPO on redeemable noncontrolling interests |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
— |
|
|
|
|
|
|
|
|
|
|
( |
) |
|
|
— |
|
|||
Proceeds from IPO on sale of Class A shares |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
|
||||
Purchase of FTW LLC units |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
|
— |
|
|
|
( |
) |
IPO costs capitalized |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
|
— |
|
|
|
( |
) |
Deferred tax adjustment |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
|
|||
Balance subsequent to Reorganization Transactions and IPO |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
( |
) |
|
|
( |
) |
|
|
|
( |
) |
|
|
( |
) |
||
Activity subsequent to Reorganization Transactions and IPO |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|||||||||||||
Distributions to RNCI |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
( |
) |
|
|
( |
) |
Dividend declared |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
|
— |
|
|
|
( |
) |
Other comprehensive loss, net of tax |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||
Stock compensation expense, net of withholding to cover taxes |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
|
||||
Dividend declared |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
Net loss |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
( |
) |
|
|
|
( |
) |
|
|
( |
) |
Other |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
|
— |
|
|
|
( |
) |
Impact of change in ownership in RNCI |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
|
|
|
|
— |
|
|
Fair value adjustment for RNCI |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
|
|
|
|
— |
|
|
Balance at December 26, 2020 |
|
$ |
|
|
$ |
|
|
$ |
|
|
|
|
|
|
$ |
|
|
|
|
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|
$ |
( |
) |
|
$ |
( |
) |
|
|
$ |
|
|
$ |
( |
) |
||||||||
Distributions to RNCI |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
( |
) |
|
|
( |
) |
Dividend declared |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
( |
) |
|
|
— |
|
|
|
( |
) |
|
|
|
— |
|
|
|
( |
) |
87
Other comprehensive loss, net of tax |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||
Stock compensation expense, net of withholding to cover taxes |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
|
|
|
|
|||||
Stock issuances |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
|
||||
RNCI units conversion into Class A shares |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
Deferred tax adjustments |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
|
— |
|
|
|
|
|||
TRA adjustments |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
|
— |
|
|
|
( |
) |
Net income |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
|
|
— |
|
|
|
|
|
|
|
|
|
|
|
||||
Other |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
|
— |
|
|
|
( |
) |
Impact of change in ownership in RNCI |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
( |
) |
|
|
( |
) |
|
|
|
|
|
|
— |
|
|
Fair value adjustment for RNCI |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
— |
|
|
|
— |
|
|
|
( |
) |
|
|
|
|
|
|
— |
|
|
Balance at December 25, 2021 |
|
$ |
|
|
$ |
|
|
$ |
|
|
|
|
|
|
$ |
|
|
|
|
|
$ |
|
|
$ |
( |
) |
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|
|
$ |
|
|
$ |
( |
) |
See the accompanying notes to the consolidated financial statements
88
MCAFEE CORP.
NOTES TO THE CONSOLIDATED FINANCIAL STATEMENTS
NOTE 1: BASIS OF PRESENTATION
Background
McAfee is a leading-edge cybersecurity company that provides advanced security solutions to consumers. Security technologies from McAfee use a unique, predictive capability that is powered by McAfee Global Threat Intelligence, which enables home users to stay one step ahead of the next wave of fileless attacks, viruses, malware, and other online threats.
McAfee Corp. (the “Corporation”) was formed as a Delaware corporation on
In October 2020, the Corporation completed an IPO pursuant to which the Corporation and selling stockholders sold an aggregate of
We refer to the holders of management incentive units of FTW (“MIUs”) as well as members of management who hold LLC Units following the closing of the offering or are to receive Class A common stock in satisfaction of existing incentive awards as “Management Owners.” We refer to those of our pre-IPO investors and certain of their affiliates who received shares of Class A common stock in connection with the Reorganization Transactions (as defined below) and who do not hold LLC Units as “Continuing Corporate Owners,” and together with the Continuing LLC Owners, as “Continuing Owners.”
The Reorganization Transactions
Reorganization
In connection with the closing of the IPO, the following Reorganization Transactions were consummated:
89
Divestiture of Enterprise Business
On March 6, 2021, we entered into a definitive agreement (the “Purchase Agreement”) with a consortium led by Symphony Technology Group (“STG”) under which STG agreed to purchase certain of our Enterprise assets together with certain of our Enterprise liabilities (“Enterprise Business”), representing substantially all of our Enterprise segment, for an all-cash purchase price of $
Agreement and Plan of Merger; Proposed Merger
On November 5, 2021, the Company entered into an Agreement and Plan of Merger (the “Merger Agreement”) with Condor BidCo, Inc., a Delaware corporation (“Parent”), and Condor Merger Sub, Inc., a Delaware corporation and wholly owned subsidiary of Parent (“Merger Subsidiary”), pursuant to which Merger Subsidiary will merge with and into the Company whereupon the separate corporate existence of Merger Subsidiary will cease and the Company will be the surviving corporation in the Merger (the “Surviving Corporation”) and will continue as a wholly owned subsidiary of Parent (the “Merger”).
As a result of the Merger, at the effective time of the Merger (the “Effective Time”) (subject to certain exceptions, including for shares of Class A Common Stock of the Company and Class B Common Stock of the Company (collectively, the “Company Stock”) owned by stockholders of the Company who did not vote in favor of the adoption of the Merger Agreement and properly exercised appraisal rights in accordance with Section 262 of the General Corporation Law of the State of Delaware), each share of Company Stock outstanding immediately prior to the Effective Time will be automatically canceled and converted into the right to receive $
Pursuant to the Merger Agreement, immediately prior to the Effective Time, except as provided therein, (i) the Company will require each member of FTW to effect an exchange of all such member’s vested MIUs (if any) for New Class A Units, and, thereafter, will require each member to effect a redemption of all of such member’s Class A LLC Units and Class B Common Stock in exchange for shares of Class A Common Stock (the “Exchange and Redemption”) and (ii) each share of Class B Common Stock will automatically be canceled immediately upon the consummation of the Exchange and Redemption, such that no shares of Class B Common Stock remain outstanding immediately prior to the Effective Time. In addition, the Board shall take all actions so that all MIUs of FTW shall be vested in full as of immediately prior to the Exchange and Redemption.
Pursuant to the Merger Agreement, immediately prior to the Effective Time:
90
Each cash award will provide the holder with the opportunity to be paid an amount in cash equal to (1) with respect to each in-the-money Company Stock Option that is not vested, (A) the excess of the Per Share Consideration over the option exercise price of such in-the-money Company Stock Option multiplied by (B) the number of shares of Common Stock subject to such in-the-money Company Stock Option as of immediately prior to the closing and (2) with respect to each restricted stock award, Company RSU, or Company PSU that is not vested, (A) the number of shares of Company Stock subject to such restricted stock award, Company RSU, or Company PSU as of immediately prior to the closing multiplied by (B) the Per Share Consideration; provided, that (x) in the case of a Company PSU that is not vested and that has an applicable one-year performance period that ends on or ended prior to the closing, for purposes of determining the number of shares of Company Stock subject to such Company PSU converted into the Cash Award, such Company PSU shall be deemed earned based on the actual performance during such performance period, and (y) in the case of a Company PSU that is not vested and that has an applicable one-year performance period that ends after the closing, for purposes of determining the number of shares of Company Stock subject to such Company PSU converted into the Cash Award, the number of shares of Company Stock subject to such Company PSU shall be determined as though such performance conditions were satisfied at the applicable target levels. Each award payable in a fixed amount of cash issued in connection with the initial public offering of the Company to employees in certain jurisdictions, and each right to receive previously accrued but not yet paid cash dividends or distributions in respect of Company Awards, Class A LLC Units, or MIUs of FTW will be assumed, honored, or continued in accordance with its terms defined in the Merger Agreement.
The Company has made customary representations, warranties and covenants in the Merger Agreement, including, among others, covenants to use reasonable best efforts to conduct its business in the ordinary course during the period between the date of the Merger Agreement and the Closing. The parties have agreed to use reasonable best efforts to take all actions necessary to consummate the merger, including cooperating to obtain the regulatory approvals necessary to complete the Merger.
In connection with the closing of the Merger, the Company, FTW and certain other parties thereto have entered into a Tax Receivable Agreement and LLC Agreement Amendment (the “Amendment”). The Amendment provides for, among other things, (i) the payment of amounts due under the tax receivable agreement currently in effect (the “TRA”) with respect to U.S. federal income tax year 2020 of the Company in accordance with the terms of the TRA up to an aggregate amount of $
The obligation of the parties to consummate the Merger is subject to receipt of stockholder approval, the expiration of the waiting period (and any extension thereof) under the Hart-Scott-Rodino Antitrust Improvements Act of 1976 (the “HSR Act”), receipt of clearance under other regulatory approvals, clearance by the Committee on Foreign Investment in the United States and other customary conditions. On December 20, 2021 at 11:59 p.m., the waiting period under the HSR Act expired. On February 9, 2022, the Company’s stockholders approved the Merger at a special meeting of stockholders. On February 22, 2022, the Committee on Foreign Investment in the United States closed its review and cleared the transactions contemplated by the Merger Agreement. Pursuant to the terms of the Merger Agreement, the completion of the Merger remains subject to various customary conditions, including (1) the absence of an order, injunction or law prohibiting the Merger, (2) the receipt of antitrust approval in the European Union and Switzerland, (3) the accuracy of each party’s representations and warranties, subject to certain materiality standards set forth in the Merger Agreement, (4) compliance in all material respects with each party’s obligations under the Merger Agreement, and (5) no Company Material Adverse Effect (as defined in the Merger Agreement) having occurred since the date of the Merger Agreement.
Upon completion of the transaction, McAfee common stock will no longer be listed on any public securities exchange.
Principles of Consolidation
91
Subsequent to the Reorganization Transactions and IPO, the Corporation is a holding company, and its sole material asset held directly or through wholly-owned subsidiaries is its equity interest in FTW. The Corporation, as the sole managing member of FTW, exclusively operates and controls the business and affairs of FTW. The Corporation consolidates the financial results of FTW and reports a redeemable noncontrolling interest (“RNCI”) related to the LLC Units held by the Continuing LLC Owners and vested MIUs held by Management Owners (Note 16).
As the Continuing LLC Owners control both the Corporation and FTW, before and after the Reorganization Transactions, the Reorganization Transactions were accounted for as a reorganization of entities under common control. As a result, the financial statements for periods prior to the IPO and the Reorganization Transactions are the financial statements of FTW as the predecessor to the Corporation for accounting and reporting purposes.
Financial information includes the accounts of McAfee and was prepared in accordance with U.S. GAAP. All intercompany balances and transactions within McAfee have been eliminated in consolidation. We have reclassified certain prior period amounts to conform to our current period presentation.
We consolidate entities in which we have a controlling financial interest, the usual condition of which is ownership of a majority voting interest. We also consider for consolidation certain interests where the controlling financial interest may be achieved through arrangements that do not involve voting interests. Such an entity, known as a variable interest entity (“VIE”), is required to be consolidated by its primary beneficiary. The primary beneficiary of a VIE is considered to possess the power to direct the activities of the VIE that most significantly impact its economic performance and has the obligation to absorb losses or the rights to receive benefits from the VIE that are significant to it (Note 18).
Use of Estimates
The preparation of the consolidated financial statements required us to make certain estimates and judgments that affect the amounts reported. Actual results may differ materially from our estimates. The accounting estimates that required our most significant and subjective judgments include:
The effect of the novel coronavirus (“COVID-19”) pandemic on our business, operations, and financial results is dependent upon future developments, including the duration of the pandemic and the related length of its impact on the global economy, which are unknown at this time. As a result, some of our estimates and assumptions required increased judgment and carry a higher degree of variability and volatility. As events continue to evolve and additional information becomes available, several of our estimates and assumptions may change materially in future periods due to the impact of the COVID-19 pandemic.
Fiscal Calendar
We maintain a 52- or 53-week fiscal year that ends on the last Saturday in December. The year ended December 25, 2021 is a 52-week year starting on December 27, 2020 and ending on December 25, 2021. The year ending December 26, 2020 is a 52-week year starting on December 29, 2019 and ending on December 26, 2020. The year ended December 28, 2019 is a 52-week year starting on December 30, 2018 and ending on December 28, 2019.
92
NOTE 2: SIGNIFICANT ACCOUNTING POLICIES
Revenue Recognition
We derive revenue from the sale of security products, subscriptions, software as a service (“SaaS”) offerings, support and maintenance, professional services, or a combination of these items, primarily through our indirect relationships with our partners or direct relationships with end customers through our internal sales force.
We recognize revenue pursuant to the five-step framework within ASC Topic 606:
We generally consider our customer to be the entity with which we have a contractual agreement. This could be the end user, or when we sell products and services through the channel, our customer could be either the distributor or the reseller. As part of determining whether a contract exists, probability of collection is assessed on a customer-by-customer basis at the outset of the contract. Customers are subjected to a credit review process that evaluates the customers’ financial position and the ability and intention to pay.
At contract inception, we assess the goods and services promised in our contracts with customers and identify a performance obligation for each promise to transfer to the customer a good or service (or bundle of goods or services) that is distinct — i.e., if a good or service is separately identifiable from other items in the bundled package and if a customer can benefit from it on its own or together with other resources that are readily available to the customer. To identify our performance obligations, we consider all of the goods or services promised in the contract regardless of whether they are explicitly stated or are implied by customary business practices. Determining whether products and services are considered distinct performance obligations or should be combined to create a single performance obligation may require significant judgment. We recognize revenue when (or as) we satisfy a performance obligation by transferring control of a good or service to a customer.
The transaction price is determined based on the consideration to which we will be entitled in exchange for transferring goods or services to the customer, adjusted for estimated variable consideration, if any. We typically estimate the transaction price impact of sales returns and discounts offered to the customers, including discounts for early payments on receivables, rebates or certain distribution partner incentives, including marketing programs. Constraints are applied when estimating variable considerations based on historical experience where applicable.
Once we have determined the transaction price, we allocate it to each performance obligation in a manner depicting the amount of consideration to which we expect to be entitled in exchange for transferring the goods or services to the customer (the “allocation objective”). If the allocation objective is met at contractual prices, no allocations are made. Otherwise, we allocate the transaction price to each performance obligation identified in the contract on a relative SSP basis, except when the criteria are met for allocating variable consideration or a discount to one or more, but not all, performance obligations in the contract.
To determine the SSP of our goods or services, we conduct a regular analysis to determine whether various goods or services have an observable SSP. If we do not have an observable SSP for a particular good or service, then SSP for that particular good or service is estimated using an approach that maximizes the use of observable inputs. We generally determine SSPs using various methodologies such as historical prices, expected cost plus margin, adjusted market assessment or non-standalone selling prices.
93
We recognize revenue as control of the promised goods or services is transferred to our customers, in an amount that reflects the consideration we expect to be entitled to in exchange for the promised goods or services. Revenue is recognized net of any taxes collected from customers and subsequently remitted to governmental authorities. Control of the promised goods or services is transferred to our customers at either a point in time or over time, depending on the performance obligation.
The nature of our promise to the customer to provide our time-based software licenses and related support and maintenance is to stand ready to provide protection for a specified or indefinite period of time. Maintenance and support in these cases are typically not distinct performance obligations as the licenses are dependent upon regular threat updates to the customer. Instead the maintenance and support is combined with a software license to create a single performance obligation. We typically satisfy these performance obligations over time, as control is transferred to the customer as the services are provided.
Additional Revenue Recognition Considerations
Partner Royalty Revenues
Our original equipment manufacturer (“OEM”), mobile and internet service providers (“MISP”) and retail sales channels have revenues derived from sales- or usage-based royalties. Such revenue is excluded from any variable consideration and transaction price calculations and is recognized at the later of when the sale or usage occurs, or the performance obligation is satisfied or partially satisfied.
Consideration Payable to a Customer
We make various payments to our channel partners, which may include revenue share, product placement fees and marketing development funds. Costs that are incremental to revenue, such as revenue share, are capitalized and amortized over time as cost of sales (Note 5). Product placement fees and marketing development funds are expensed in sales and marketing expense as the related benefit is received and were $
Under certain of our channel partner agreements, the partners pay us royalties on our technology sold to their customers, which we recognize as revenue in accordance with our revenue recognition policy. In these situations, the payments made to our channel partners are recognized as consideration paid to a customer, and thus are recorded as reductions to revenue up to the amount of cumulative revenue recognized from the contract with the channel partner during the period of measurement.
Contract Costs
Contract acquisition costs consist mainly of sales commissions and associated fringe benefits, as well as revenue share under programs with certain of our distribution partners. For revenue share, the partner receives a percentage of the revenue we receive from an end user upon conversion to a paid customer or renewal. These costs would not have been incurred if the contract was not obtained and are considered incremental and recoverable costs of obtaining a contract with a customer. These costs are capitalized and amortized over time in accordance with Accounting Standards Codification (“ASC”) 340-40.
Contract fulfillment costs consist of software and related costs. These costs are incremental and recoverable and are capitalized and amortized on a systematic basis that is consistent with the pattern of transfer of the goods and services to which the asset relates.
Discontinued Operations
Certain of our perpetual software licenses or hardware with integrated software are not distinct from their accompanying maintenance and support, as they are dependent upon regular threat updates. These contracts typically contain a renewal option that we have concluded creates a material right for our customer. The license, hardware and maintenance and support revenue is recognized over time, as control is transferred to the customer over the term of the initial contract period while the corresponding material right is recognized over time beginning at the end of the initial contractual period over the remainder of the technology constrained customer life.
Alternatively, certain of our perpetual software licenses, hardware appliances, or hardware with integrated software provide a benefit to the customer that is separable from the related support as they are not dependent upon regular threat updates. Revenue for these products is recognized at a point in time when control is transferred to our customers, generally at shipment. The related maintenance and support represent a separate performance obligation and the associated transaction price allocated to it is recognized over time as control is transferred to the customer.
94
The nature of our promise to the customer to provide our SaaS offerings and related support and maintenance is to stand ready to provide protection for a specified or indefinite period of time. Maintenance and support in these cases are typically not distinct performance obligations as the licenses are dependent upon regular threat updates to the customer. Instead the maintenance and support is combined with a software license to create a single performance obligation. We typically satisfy these performance obligations over time, as control is transferred to the customer as the services are provided.
Revenue for professional services that are a separate and distinct performance obligation is recognized as services are provided to the customer.
Payment Terms and Warranties
Our payment terms vary by the type and location of our customer and the products or services offered. The term between invoicing and when payment is due is not significant. For certain products or services and customer types, we require payment before the products or services are delivered to the customer.
We provide assurance warranties on our products and services. The warranty timeframe varies depending on the product or service sold, and the resolution of any issues is at our discretion to either repair, replace, reperform or refund the fee.
Contract Costs
Contract acquisition costs consist mainly of sales commissions and associated fringe benefits. We typically recognize the initial commissions that are not commensurate with renewal commissions over the longer of the customer relationship (generally estimated to be to
Advertising Expenses
Accounts Receivable
Cash and Cash Equivalents
Goodwill
Goodwill is recorded as the excess of consideration transferred over the acquisition-date fair values of assets acquired and liabilities assumed in a business combination. Historically, we have assigned goodwill to our reporting units based on the relative fair value expected at the time of the acquisition. Goodwill and intangible assets disposed as a result of the Enterprise Divestiture were included in assets of discontinued operations in our consolidated balance sheet as of December 26, 2020. We now have one reporting unit for goodwill (Note 10).
We perform an annual impairment assessment on the first day of the third month in the fourth quarter or more frequently if indicators of potential impairment exist, which includes evaluating qualitative and quantitative factors to assess the likelihood of an impairment of our reporting unit’s goodwill. If the conclusion of an impairment assessment is that it is more likely than not that the fair value is more than its carrying value, goodwill is not considered impaired and we are not required to perform the quantitative goodwill impairment test.
If the conclusion of an impairment assessment is that it is more likely than not that the fair value is less than its carrying value, we perform the quantitative goodwill impairment test, which compares the fair value of the reporting unit to its carrying value. Impairments, if any, are based on the excess of the carrying amount over the fair value.
95
Identified Intangible Assets
We amortize all finite-lived intangible assets that are subject to amortization over their estimated useful life of economic benefit on a straight-line basis (Note 10).
For significant intangible assets subject to amortization, we perform a quarterly assessment to determine whether facts and circumstances indicate that the useful life is shorter than we had originally estimated or that the carrying amount of assets may not be recoverable. If such facts and circumstances exist, we assess recoverability by comparing the projected undiscounted net cash flows associated with the related asset or group of assets over their remaining useful lives against their respective carrying amounts. Impairments, if any, are based on the excess of the carrying amount over the fair value of those assets. If an asset’s useful life is shorter than originally estimated, we accelerate the rate of amortization and amortize the remaining carrying value over the updated, shorter useful life.
Research and Development
Costs incurred in the research and development of new software products are expensed as incurred until technological feasibility is established. Research and development costs include salaries and benefits of researchers, supplies, and other expenses incurred during research and development efforts. Development costs are capitalized beginning when a product’s technological feasibility has been established and ending when the product is available for general release to customers. Technological feasibility is reached when the product reaches the working-model stage. To date, new products and enhancements generally have reached technological feasibility and have been released for sale at substantially the same time. All research and development costs to date have been expensed as incurred except for software subject to a hosting arrangement.
Equity-Based Awards
We currently provide various equity-based compensation to those whom, in the opinion of the Board or its designee, are in a position to make a significant contribution to our success.
Equity-based compensation cost is measured at the grant date based on the fair value of the award and recognized as expense over the appropriate service period. Determining the fair value of equity-based awards requires considerable judgment, including assumptions and estimates of the following:
96
Before our IPO, the fair value of the unit was determined by the Board reasonably and in good faith. Generally, this involved a review by an independent valuation of our business, which required judgmental inputs and assumptions such as our cash flow projections, peer company comparisons, market data, growth rates and discount rate. The Board reviewed its prior determination of fair value of a unit on a quarterly basis to decide whether any change was appropriate (including whether to obtain a new independent valuation), considering such factors as any significant financial, operational, or market changes affecting the business since the last valuation date. Due to us not having sufficient historical volatility, we used the historical volatilities of publicly traded companies which were similar to us in size, stage of life cycle and financial leverage. We continued to use this peer group of companies unless a situation arose within the group that would require evaluation of which publicly traded companies were included or once sufficient data was available to use our own historical volatility. In addition, for awards where vesting was dependent upon achieving certain operating performance goals, we estimated the likelihood of achieving the performance goals. For goals dependent upon a qualifying liquidity event, (i.e., a change of control or public offering registered on a Form S-1 (or successor form), in either case, occurring on or before April 3, 2024) (a “Qualifying Liquidity Event”), we would not recognize any expense until the event occurs. Upon consummation of our IPO, we recognized a cumulative catch-up of expense based on the vesting dates for our time-based awards and expected vesting dates for our performance-based awards. We recognize forfeitures as they occur. For awards with only time-vesting requirement, we recognize the expense over a straight-line basis during the vesting period.
After the close of our IPO, our outstanding Management Equity Participation Units (“MEPUs”) and Cash RSU (“CRSUs”) were converted into RSUs (“Replacement RSUs”), which are to be settled in Class A common stock. The fair value of these Replacement RSUs was our IPO price less the present value of the expected dividends not received during the vesting period. For all other RSU grants after our IPO, we utilize the closing price of our common stock on the day of the grant date, less the present value of expected dividends not received during the vesting period to determine grant date fair value.
In addition, certain MEPU holders were also granted stock options with a strike price equal to our IPO price. For all other stock option grants after our IPO, we utilize the closing price of our common stock on the day of grant date to determine the strike price. All of our granted stock options are non-qualified and expire
Our time-based awards generally vest evenly over the following grant date. For time-based awards granted to our new hires, the
Our performance-based RSU awards (“PSU”s) are granted to executive officers and certain employees annually. These awards vest after approximately
A portion of our RSU awards and all of our performance-based stock option and performance-based MIU awards vest upon achievement of certain return of cash metrics. In January 2021, these awards were modified to vest annually in equal tranches over the three year anniversaries of our IPO. If the original return of cash performance is achieved prior to such anniversaries, the awards vest in full. In both cases, the unvested portion of the awards are forfeited upon termination.
Upon the settlement of RSUs, we withhold a portion of the earned units to cover no more than the maximum statutory income and employment taxes and remit the net shares to an individual brokerage account. Authorized shares of our common stock are used to settle RSUs and stock options.
Awards granted prior to our IPO and/or converted at the time of our IPO are covered under our 2017 Management Incentive Plan (“2017 Plan”). Stock options granted at our IPO and/or awards granted at our IPO or after are covered under our 2020 Equity Omnibus Plan (“2020 Plan”). No new awards may be authorized under our 2017 Plan.
Derivative and Hedging Instruments
The fair values of each of our derivative instruments are recorded as an asset or liability on a net basis at the balance sheet date within other current or long-term assets or liabilities. The change in fair value of our derivative instruments is recorded through earnings in the line item on the consolidated statements of operations to which the derivatives most closely relate, primarily in Interest expense. Changes in the fair value of the underlying assets and liabilities associated with the hedged risk are generally offset by the changes in the fair value of the related derivatives. We do not use derivative financial instruments for speculative trading purposes.
97
To reduce the interest rate risk inherent in variable rate debt, we entered into certain interest rate swap agreements to convert a portion of our variable rate borrowing into a fixed rate obligation (Note 15). These interest rate swap agreements fix the London Interbank Offered Rate (“LIBOR”) portion of the US dollar denominated variable rate borrowings. Accordingly, to the extent the cash flow hedge is effective, changes in the fair value of interest rate swaps will be included within Accumulated other comprehensive income (loss) in the consolidated balance sheets. Hedge accounting will be discontinued when the interest rate swap is no longer effective in offsetting cash flows attributable to the hedged risk, the interest rate swap expires or the cash flow hedge is dedesignated because it is no longer probable that the forecasted transaction will occur according to the original strategy. When hedge accounting is discontinued, any related amounts previously included in Accumulated other comprehensive income (loss) would be reclassified to Interest expense, within the consolidated statements of operations.
Leases
We adopted ASU No. 2016-02, Leases, and all related updates (collectively, “ASC Topic 842”), which primarily requires leases to be recognized on the balance sheet, using the modified retrospective approach with an effective date as of the beginning of our 2019 fiscal year,
We determine if an arrangement contains a lease and classification of that lease, if applicable, at inception based on:
Right-of-use (“ROU”) assets represent the right to use an underlying asset for the lease term and lease liabilities represent the obligation to make minimum lease payments arising from the lease. A ROU asset is initially measured at an amount which represents the lease liability, plus any initial direct costs incurred and less any lease incentives received. The lease liability is initially measured at lease commencement date based on the present value of minimum lease payments over the lease term. The lease term may include options to extend or terminate when it is reasonably certain that we will exercise the option. We have lease agreements with lease and non-lease components, and the non-lease components are generally accounted for separately and not included in our leased assets and corresponding liabilities.
The depreciable life of assets and leasehold improvements are limited by the expected lease term unless there is a transfer of title or purchase option reasonably certain of exercise. Payments related to short-term leases are expensed on a straight-line basis over the lease term and reflected as a component of lease cost within our consolidated statements of operations. Lease payments generally consist of fixed amounts, as well as variable amounts based on a market rate or an index which are not material to our consolidated lease cost. Our leases do not contain significant terms and conditions for variable lease payments.
Discontinued Operations
We review the presentation of planned business dispositions in the consolidated financial statements based on the available information and events that have occurred. The review consists of evaluating whether the business meets the definition of a component for which the operations and cash flows are clearly distinguishable from the other components of the business, and if so, whether it is anticipated that after the disposal the cash flows of the component would be eliminated from continuing operations and whether the disposition represents a strategic shift that has a major effect on operations and financial results. In addition, we evaluate whether the business has met the criteria as a business held for sale. In order for a planned disposition to be classified as a business held for sale, the established criteria must be met as of the reporting date, including an active program to market the business and the expected disposition of the business within one year.
Planned business dispositions are presented as discontinued operations when all the criteria described above are met. For those divestitures that qualify as discontinued operations, all comparative periods presented are reclassified in the consolidated balance sheets. Additionally, the results of operations of a discontinued operation are reclassified to income from discontinued operations, net of tax, for all periods presented in the consolidated statements of operations. Results of discontinued operations include all revenues and expenses directly derived from such businesses; general corporate overhead is not allocated to discontinued operations.
98
NOTE 3: RECENT ACCOUNTING STANDARDS
Recently Adopted Account Standards
In December 2019, the FASB issued ASU 2019-12, Income Taxes (Topic 740): Simplifying the Accounting for Income Taxes (“ASU 2019-12”), which simplifies the accounting for income taxes by removing certain exceptions for recognizing deferred taxes for investments, performing intra-period allocation and calculating income taxes in interim periods. ASU 2019-12 also adds guidance to reduce complexity in certain areas, including recognizing deferred taxes for tax goodwill and allocating taxes to members of a consolidated group. We adopted ASU 2019-12 on December 27, 2020 and it had no material impact on our consolidated financial statements and related disclosures.
Recent Accounting Standards Not Yet Adopted
In August 2020, the FASB issued ASU 2020-06, Debt—Debt with Conversion and Other Options (Subtopic 470-20) and Derivatives and Hedging—Contracts in Entity’s Own Equity (Subtopic 815-40) (“ASU 2020-06”), which simplifies current guidance for convertible financial instruments. ASU 2020-06 also amends derivatives guidance for certain contracts in an entity’s own equity. Finally, ASU 2020-06 amends earnings per share guidance related to convertible instruments. ASU 2020-06 is effective for us in the first quarter of fiscal year 2022. We do not expect the adoption of ASU 2020-06 to have a material effect on our consolidated financial statements.
NOTE 4: DISCONTINUED OPERATIONS
Divestiture of Enterprise Business
On March 6, 2021, we entered into a definitive agreement with a consortium led by STG, pursuant to which STG agreed to purchase our Enterprise Business for an all-cash purchase price of $
The following table presents the gain associated with the sale, presented in the results of our discontinued operations below:
(in millions) |
|
|
|
|
Gross purchase price |
|
$ |
|
|
Net assets sold |
|
|
( |
) |
Transaction costs |
|
|
( |
) |
Pre-tax gain on divestiture of Enterprise Business |
|
|
|
|
Income tax expense on gain on divestiture of Enterprise Business |
|
|
( |
) |
Total gain on divestiture of Enterprise Business |
|
$ |
|
|
The carrying value of the net assets sold are as follows:
(in millions) |
|
|
|
|
Accounts receivable, net |
|
$ |
|
|
Deferred costs |
|
|
|
|
Other current assets |
|
|
|
|
Property and equipment, net |
|
|
|
|
Intangible assets, net |
|
|
|
|
Goodwill |
|
|
|
|
Other long-term assets |
|
|
|
|
Accounts payable and other current liabilities |
|
|
( |
) |
Accrued compensation and benefits |
|
|
( |
) |
Accrued marketing |
|
|
( |
) |
Deferred revenue |
|
|
( |
) |
Other long-term liabilities |
|
|
( |
) |
Total net assets sold |
|
$ |
|
|
99
Transition Services Agreement And Commercial Services Agreement
In connection with the divestiture of the Enterprise Business, we entered into a Transition Service Agreement (“TSA”) under which we will provide assistance to the Enterprise Business subsequent to the divestiture including, but not limited to, business support services and information technology services. Income for the transition services was $
Our Receivable from and Payable to Enterprise Business consisted of the following:
(in millions) |
|
December 25, 2021 |
|
|
Receivable from Enterprise Business |
|
|
|
|
Proceeds receivable |
|
$ |
|
|
TSA receivables and misdirected payments |
|
|
|
|
Total |
|
$ |
|
|
Payable to Enterprise Business |
|
|
|
|
Transaction costs |
|
|
|
|
Misdirected payments |
|
|
|
|
Total |
|
$ |
|
|
Discontinued Operations
The following table presents the aggregate amounts of the classes of assets and liabilities of the Enterprise Business classified as discontinued operations:
(in millions) |
|
December 26, 2020 |
|
|
Assets: |
|
|
|
|
Accounts receivable, net |
|
$ |
|
|
Deferred costs |
|
|
|
|
Other current assets |
|
|
|
|
Total current assets of discontinued operations |
|
|
|
|
Property and equipment, net |
|
|
|
|
Intangible assets, net |
|
|
|
|
Goodwill |
|
|
|
|
Deferred tax assets |
|
|
|
|
Other long-term assets |
|
|
|
|
Total assets of discontinued operations |
|
$ |
|
|
Liabilities: |
|
|
|
|
Accounts payable and other current liabilities |
|
$ |
|
|
Accrued compensation and benefits |
|
|
|
|
Accrued marketing |
|
|
|
|
Deferred revenue |
|
|
|
|
Total current liabilities of discontinued operations |
|
|
|
|
Deferred tax liabilities |
|
|
|
|
Other long-term liabilities |
|
|
|
|
Deferred revenue, less current portion |
|
|
|
|
Total liabilities of discontinued operations |
|
$ |
|
|
The following table presents information regarding certain components of income (loss) from discontinued operations, net of taxes:
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Net revenue |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Operating income (loss) |
|
|
|
|
|
( |
) |
|
|
|
||
Pre-tax gain on divestiture of Enterprise Business |
|
|
|
|
|
— |
|
|
|
— |
|
|
Income (loss) before income taxes |
|
|
|
|
|
( |
) |
|
|
|
||
Income tax expense(1) |
|
|
|
|
|
|
|
|
|
|||
Income (loss) from discontinued operations, net of taxes |
|
|
|
|
|
( |
) |
|
|
( |
) |
|
100
In July 2021, two amendments to the definitive agreement with a consortium led by STG for the purchase of the Enterprise Business were executed. The amendments modified certain provisions for assets and liabilities to be transferred as well as the timing and procedures for transfer of certain assets and employees in foreign jurisdictions in connection with the sale, and clarifying requirements for maintenance of such assets prior to transfer. The amendments also include certain other modifications or clarifications of the purchase agreement. As a result of the amendments, our results of operations for the years ended December 26, 2020 and December 28, 2019 and our December 26, 2020 consolidated balance sheet reflect changes in the assets and liabilities that were determined to be part of discontinued operations as reported in our previously filed Form 8-K, Item 8 for the year ended December 26, 2020. These changes resulted in increases of $
In connection with the sale of the Enterprise Business, we have incurred costs up to the date of the sale consisting primarily of consulting fees, legal fees, and other costs to facilitate the separation of the Enterprise Business, including incremental costs associated with data disentanglement and acceleration of data migration to the cloud. During the year ended December 25, 2021, we recorded $
The following table presents significant non-cash items and capital expenditures of discontinued operations:
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Depreciation and amortization |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Equity-based compensation expense |
|
|
|
|
|
|
|
|
|
|||
Deferred taxes (benefit) |
|
|
|
|
|
( |
) |
|
|
|
||
Additions to property and equipment |
|
|
|
|
|
|
|
|
|
|||
NOTE 5: REVENUE FROM CONTRACTS WITH CUSTOMERS
Deferred Revenue
During the year ended December 25, 2021, we recognized $
During the year ended December 27, 2020, we recognized $
During the year ended December 28, 2019, we recognized $
Transaction Price Allocated to the Remaining Performance Obligations
As of December 25, 2021, we have $
101
Contract Costs
The following tables summarize the various contract costs capitalized on our consolidated financial statements:
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Capitalized acquisition costs within: |
|
|
|
|
|
|
||
Deferred costs |
|
$ |
|
|
$ |
|
||
Other long-term assets |
|
|
|
|
|
|
||
Total capitalized acquisition costs |
|
$ |
|
|
$ |
|
||
Capitalized fulfillment costs within: |
|
|
|
|
|
|
||
Deferred costs |
|
$ |
|
|
$ |
|
||
Other long-term assets |
|
|
|
|
|
|
||
Total capitalized fulfillment costs |
|
$ |
|
|
$ |
|
||
The following tables summarize the amortization of contract acquisitions and fulfillment costs on our consolidated financial statements:
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Amortization of capitalized acquisition costs: |
|
|
|
|
|
|
|
|
|
|||
Net revenue |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Cost of sales |
|
|
|
|
|
|
|
|
|
|||
Sales and marketing |
|
|
|
|
|
|
|
|
|
|||
Total amortization of capitalized acquisition costs from continuing operations |
|
|
|
|
|
|
|
|
|
|||
Discontinued operations |
|
|
|
|
|
|
|
|
|
|||
Total amortization of capitalized acquisition costs |
|
$ |
|
|
$ |
|
|
$ |
|
|||
|
|
|
|
|
|
|
|
|
|
|||
Amortization of capitalized fulfillment costs: |
|
|
|
|
|
|
|
|
|
|||
Cost of sales |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Discontinued operations |
|
|
|
|
|
|
|
|
|
|||
Total amortization of capitalized fulfillment costs |
|
$ |
|
|
$ |
|
|
$ |
|
|||
There were
Net Revenue by Geographic Region
Net revenue by geographic region based on the sell-to address of the end-users is as follows:
|
|
Year Ended |
|
|||||||||||||||||||||
(in millions except percentages) |
|
December 25, 2021 |
|
|
% of Total |
|
|
December 26, 2020 |
|
|
% of Total |
|
|
December 28, 2019 |
|
|
% of Total |
|
||||||
Americas |
|
$ |
|
|
|
% |
|
$ |
|
|
|
% |
|
$ |
|
|
|
% |
||||||
EMEA |
|
|
|
|
|
% |
|
|
|
|
|
% |
|
|
|
|
|
% |
||||||
APJ |
|
|
|
|
|
% |
|
|
|
|
|
% |
|
|
|
|
|
% |
||||||
Total net revenue |
|
$ |
|
|
|
% |
|
$ |
|
|
|
% |
|
$ |
|
|
|
% |
||||||
102
Note: The Americas include U.S., Canada and Latin America; EMEA includes Europe, Middle East and Africa; APJ includes Asia Pacific and Japan. See Note 8 for individual countries that accounted for more than 10% of net revenue.
Net Revenue by Channel
Direct to Consumer revenue is from subscribers who transact with us directly through McAfee web properties, including those converted after the trial period of the McAfee product preinstalled on their new PC purchase or converted subsequent to their subscription period purchased from another channel. Indirect revenue is driven by users who purchase directly through a partner inclusive of mobile providers, ISPs, electronics retailers, ecommerce sites, and search providers.
|
|
Year Ended |
|
|||||||||||||||||||||
(in millions except percentages) |
|
December 25, 2021 |
|
|
% of Total |
|
|
December 26, 2020 |
|
|
% of Total |
|
|
December 28, 2019 |
|
|
% of Total |
|
||||||
Direct to Consumer |
|
$ |
|
|
|
% |
|
$ |
|
|
|
% |
|
$ |
|
|
|
% |
||||||
Indirect |
|
|
|
|
|
% |
|
|
|
|
|
% |
|
|
|
|
|
% |
||||||
Total net revenue |
|
$ |
|
|
|
% |
|
$ |
|
|
|
% |
|
$ |
|
|
|
% |
||||||
NOTE 6: LEASES
As of December 25, 2021, we have operating leases for corporate offices and data centers and no significant finance leases.
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Cash paid for amounts included in the measurement of lease liabilities |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Right-of-use assets obtained in exchange for lease obligations |
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
|||
Lease expense from continuing operations |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Lease expense from discontinued operations |
|
|
|
|
|
|
|
|
|
|||
Total lease expense |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Balance sheet information related to leases, excluding leases associated with our discontinued operations, was as follows:
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
|
$ |
|
|
$ |
|
|||
|
$ |
|
|
$ |
|
|||
|
|
|
|
|
|
|||
Total lease liabilities |
|
$ |
|
|
$ |
|
||
Weighted Average Remaining Lease Term (in years) |
|
|
|
|
|
|
||
Weighted Average Discount Rate (percentage) |
|
|
% |
|
|
% |
||
Maturities of lease liabilities were as follows:
(in millions) |
|
December 25, 2021 |
|
|
2022 |
|
$ |
|
|
2023 |
|
|
|
|
2024 |
|
|
|
|
2025 |
|
|
|
|
2026 |
|
|
|
|
Thereafter |
|
|
|
|
Total lease payments |
|
|
|
|
Less imputed interest |
|
|
( |
) |
Total lease liabilities |
|
$ |
|
|
103
NOTE 7: TRANSACTIONS WITH MEMBERS, SHAREHOLDERS AND RELATED PARTIES
Total tax and excess cash distributions to its members declared by FTW were as follows:
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
FTW members excluding McAfee Corp. |
|
$ |
|
|
$ |
|
|
$ |
|
|||
McAfee Corp. |
|
|
|
|
|
|
|
|
|
|||
Total tax and excess cash distributions declared |
|
$ |
|
|
$ |
|
|
$ |
|
|||
McAfee Corp. used a portion of its share of the cash distributions declared by FTW to declare or pay the dividends noted in the table below. Remaining distributions received by McAfee Corp. were used for corporate taxes and general corporate purposes. Pursuant to the terms of the Merger Agreement, the Company has agreed to suspend its dividend program during the term of the Merger Agreement.
Declaration Date |
|
Record Date |
|
Payment Date |
|
Dividend per Share |
|
|
Amount |
|
||
|
|
|
$ |
|
|
$ |
|
|||||
|
|
|
$ |
|
|
$ |
|
|||||
|
|
|
$ |
|
|
$ |
|
|||||
|
|
|
$ |
|
|
$ |
|
|||||
|
|
|
$ |
|
|
$ |
|
|||||
As a result of the divestiture of the Enterprise Business, in August 2021 the Board of Directors of McAfee Corp. declared a special one-time cash dividend of $
In February 2020, we entered into an agreement with our former President and Chief Executive Officer to repurchase equity units for an aggregate repurchase price of $
At the time of the IPO in 2020, McAfee Corp. made a one-time payment of $
We had these additional transactions, inclusive of discontinued operations, with TPG, Intel or other Continuing LLC Owners and companies owned or partially owned by those parties that therefore qualify as related parties.
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Sales with related parties: |
|
|
|
|
|
|
|
|
|
|||
Intel |
|
$ |
|
|
$ |
|
|
$ |
|
|||
TPG |
|
|
|
|
|
|
|
|
|
|||
TPG affiliates |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Other |
|
|
|
|
|
|
|
|
|
|||
Total |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Payments to related parties: |
|
|
|
|
|
|
|
|
|
|||
Intel |
|
$ |
|
|
$ |
|
|
$ |
|
|||
TPG |
|
|
|
|
|
|
|
|
|
|||
TPG affiliates |
|
|
|
|
|
|
|
|
|
|||
Other |
|
|
|
|
|
|
|
|
|
|||
Total |
|
$ |
|
|
$ |
|
|
$ |
|
|||
104
Revenue from the sales transactions are recognized in accordance with our revenue recognition policy.
Our receivable from Intel, net consisted of the following:
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Intel receivable(1) |
|
|
|
|
|
|
||
Tax indemnity |
|
$ |
|
|
$ |
|
||
Total |
|
|
|
|
|
|
||
Intel payable(1) |
|
|
|
|
|
|
||
Tax indemnity |
|
|
( |
) |
|
|
( |
) |
Total |
|
|
( |
) |
|
|
( |
) |
Total, net(2) |
|
$ |
|
|
$ |
|
||
NOTE 8: OPERATING SEGMENTS
Historically, we had
Revenue by country based on the sell-to address of the end-users is as follows:
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
U.S. |
|
$ |
|
|
$ |
|
|
$ |
|
|||
United Kingdom |
|
|
|
|
|
|
|
|
|
|||
Other(1) |
|
|
|
|
|
|
|
|
|
|||
Total net revenue |
|
$ |
|
|
$ |
|
|
$ |
|
|||
(1)
Customer Information
In the years ended December 25, 2021, December 26, 2020, and December 28, 2019, our largest customer accounted for
NOTE 9: RESTRUCTURING AND TRANSITION CHARGES
Restructuring charges generally include significant actions impacting the way we manage our business. Employee severance and benefit charges are largely based upon substantive severance plans, while some charges result from mandated requirements in certain foreign jurisdictions. These charges include items such as employee severance, ongoing benefits, and excess payroll costs directly attributable to the restructuring plan. Transition charges are costs incurred subsequent to the divestiture of the Enterprise Business in support of the transition services agreement. These costs include legal, advisory, consulting and other costs and are generally paid when incurred.
105
In connection with divestiture of the Enterprise Business, a portion of our Restructuring and transition charges were classified to discontinued operations for all periods presented.
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Employee severance and benefits |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Transition charges |
|
|
|
|
|
— |
|
|
|
|
||
Restructuring and transition charges attributable to continuing operations |
|
|
|
|
|
|
|
|
|
|||
|
|
|
|
|
|
|
|
|
|
|||
Employee severance and benefits |
|
|
|
|
|
|
|
|
|
|||
Facility restructuring |
|
|
|
|
|
— |
|
|
|
|
||
Restructuring charges attributable to discontinued operations |
|
|
|
|
|
|
|
|
|
|||
Total restructuring and transition charges |
|
$ |
|
|
$ |
|
|
$ |
|
|||
In January 2019, we announced the “Transformation 2019” initiative, in which we realigned our staffing across various departments. As part of the initiative, we recognized employee severance and benefits and facility restructuring costs of $
In January 2020, we commenced the 2020 transformation initiative, in which we realigned our staffing across various departments. As part of the initiative, we incurred employee severance and benefits costs of $
In December 2020, we initiated a workforce reduction and other restructuring activities designed to continue to improve operating margins in connection with the reorientation of our Enterprise Business and realignment of staffing in other departments, which was announced in February 2021 following the notification of affected employees. These activities have been substantially completed. As part of the initiative, in December 2020 we recognized employee severance and benefits costs of $
During the year ended December 25, 2021, we recognized $
The balance of our restructuring activities are as follows:
(in millions) |
|
Total |
|
|
Employee severance and benefits |
|
|
|
|
As of December 26, 2020 |
|
$ |
|
|
Additional accruals, inclusive of expenses attributed to discontinued operations |
|
|
|
|
Cash payments |
|
|
( |
) |
As of December 25, 2021 |
|
$ |
|
|
NOTE 10: GOODWILL AND INTANGIBLE ASSETS, NET
Goodwill and intangible assets disposed of as a result of the Enterprise Divestiture were included in assets of discontinued operations in our consolidated balance sheet as of December 26, 2020, and accordingly, are excluded from the tables below.
Goodwill and Indefinite-lived Intangibles
During the fourth quarter of each year, we perform our annual impairment assessment.
106
Intangible Assets, Net
|
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||||||||||||||||||
(in millions) |
|
Gross Assets |
|
|
Accumulated |
|
|
Net |
|
|
Gross Assets |
|
|
Accumulated |
|
|
Net |
|
||||||
Intangible assets subject to amortization: |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||
Customer relationships and other |
|
$ |
|
|
$ |
( |
) |
|
$ |
|
|
$ |
|
|
$ |
( |
) |
|
$ |
|
||||
Acquired and developed technology |
|
|
|
|
|
( |
) |
|
|
|
|
|
|
|
|
( |
) |
|
|
|
||||
Total intangible assets subject to |
|
|
|
|
|
( |
) |
|
|
|
|
|
|
|
|
( |
) |
|
|
|
||||
Intangible assets not subject to amortization: |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||
Brand |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||
Total intangible assets not subject to |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
— |
|
|
|
|
|||||
Total intangible assets |
|
$ |
|
|
$ |
( |
) |
|
$ |
|
|
$ |
|
|
$ |
( |
) |
|
$ |
|
||||
Amortization expense for purchased and developed intangible assets is as follows:
|
|
Year Ended |
|
|
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|
Statements of Operations Classification |
|||
Customer relationships and other |
|
$ |
|
|
$ |
|
|
$ |
|
|
Amortization of intangibles |
|||
Acquired and developed technology |
|
|
|
|
|
|
|
|
|
|
Cost of sales |
|||
Total |
|
$ |
|
|
$ |
|
|
$ |
|
|
|
|||
Based on identified intangible assets that are subject to amortization as of December 25, 2021, we expect future amortization expense to be as follows:
(in millions) |
|
Total |
|
|
2022 |
|
$ |
|
|
2023 |
|
|
|
|
2024 |
|
|
|
|
2025 |
|
|
|
|
2026 |
|
|
|
|
Total |
|
$ |
|
|
NOTE 11: PROPERTY AND EQUIPMENT
Property and equipment assets disposed of as a result of the Enterprise Divestiture were included in assets of discontinued operations in our consolidated balance sheet as of December 26, 2020, and accordingly, are excluded from the table below.
Property and equipment, net was as follows:
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Land, buildings and leasehold improvements |
|
$ |
|
|
$ |
|
||
Computer equipment, software and other |
|
|
|
|
|
|
||
Construction in progress |
|
|
|
|
|
|
||
Total property and equipment |
|
|
|
|
|
|
||
Less: accumulated depreciation |
|
|
( |
) |
|
|
( |
) |
Total property and equipment, net |
|
$ |
|
|
$ |
|
||
We computed depreciation using the straight-line method over the estimated useful life of
107
Sale of Plano Facility
On September 13, 2021, we entered into a Purchase and Sale Agreement with Capital Commercial Investments, Inc. pursuant to which the Company sold its property (land and office building with approximately
NOTE 12: EMPLOYEE INCENTIVE / BENEFIT PLANS
Equity-Based Compensation
Equity-based compensation costs recognized in our consolidated statements of operations were:
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Cost of sales |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Sales and marketing |
|
|
|
|
|
|
|
|
|
|||
Research and development |
|
|
|
|
|
|
|
|
|
|||
General and administrative |
|
|
|
|
|
|
|
|
|
|||
Total equity-based compensation expense from continuing operations |
|
|
|
|
|
|
|
|
|
|||
Discontinued operations |
|
|
|
|
|
|
|
|
|
|||
Total equity-based compensation expense |
|
$ |
|
|
$ |
|
|
$ |
|
|||
During 2021, the tax benefit that we realized for the tax deduction from equity-based awards totaled $
During 2020, the tax benefit that we realized for the tax deduction from equity-based awards totaled $
The following information related to our equity-based awards includes awards associated with both our continuing and discontinued operations.
Class A Share Awards
RSU activity was as follows:
|
|
Number of |
|
|
Weighted |
|
||
Balance as of December 26, 2020 |
|
|
|
|
$ |
|
||
Grants |
|
|
|
|
|
|
||
Dividend adjustments |
|
|
|
|
|
|
||
Vested |
|
|
( |
) |
|
|
|
|
Forfeited |
|
|
( |
) |
|
|
|
|
Balance as of December 25, 2021 |
|
|
|
|
$ |
|
||
As of December 25, 2021, our unrecognized compensation costs related to the RSU grants was $
PSU
PSU activity was as follows:
|
|
Number of |
|
|
Weighted |
|
||
Balance as of December 26, 2020 |
|
|
|
|
$ |
|
||
Grants |
|
|
|
|
|
|
||
Additional units for over attainment |
|
|
|
|
|
|
||
Forfeited |
|
|
( |
) |
|
|
|
|
Balance as of December 25, 2021 |
|
|
|
|
$ |
|
||
108
As of December 25, 2021, our remaining unrecognized compensation costs related to the PSU grants was $
Stock Options
S
|
|
Time-based |
|
|
Performance-based |
|
||||||||||
|
|
Number of |
|
|
Weighted |
|
|
Number of |
|
|
Weighted |
|
||||
Balance of unvested options as of December 26, 2020 |
|
|
|
|
$ |
|
|
|
|
|
$ |
|
||||
Vested |
|
|
( |
) |
|
|
|
|
|
( |
) |
|
|
|
||
Forfeited |
|
|
( |
) |
|
|
|
|
|
( |
) |
|
|
|
||
Balance of unvested options as of December 25, 2021 |
|
|
|
|
$ |
|
|
|
|
|
$ |
|
||||
Exercisable options as of December 25, 2021 |
|
|
|
|
|
|
|
|
|
|
|
|
||||
Weighted average strike price |
|
$ |
|
|
|
|
|
|
|
|
|
|
||||
As of December 25, 2021, our remaining unrecognized compensation costs related to the stock options grants was $
The weighted average estimated value of the stock options granted was valued using the Black-Scholes model with the following inputs:
|
|
Year Ended |
||
|
|
December 25, 2021 |
|
December 26, 2020 |
Estimated values |
|
$ |
|
$ |
Expected life (in years) |
|
|
||
Risk-free interest rate |
|
|
||
Dividend yield |
|
|
||
Volatility |
|
|
||
Management Incentive and Equity Participation Unit Awards
The time-based awards’ fair value was calculated using the Black-Scholes model. The performance-based awards’ fair value was calculated using Monte Carlo simulations. In January 2021, these awards were modified to vest annually in equal tranches over the three year anniversaries of our IPO. If the original return of cash performance is achieved prior to such anniversaries, the awards vest in full. In both cases, the unvested portion of the awards are forfeited upon termination.
Management Incentive Units
MIU activity was as follows:
|
|
Time-based |
|
|
Performance-based |
|
||||||||||
|
|
Number of |
|
|
Weighted |
|
|
Number of |
|
|
Weighted |
|
||||
Balance as of December 26, 2020 |
|
|
|
|
$ |
|
|
|
|
|
$ |
|
||||
Vested |
|
|
( |
) |
|
|
|
|
|
( |
) |
|
|
|
||
Forfeited |
|
|
( |
) |
|
|
|
|
|
( |
) |
|
|
|
||
Balance as of December 25, 2021 |
|
|
|
|
$ |
|
|
|
|
|
$ |
|
||||
As of December 25, 2021, unrecognized compensation costs of the MIUs were $
The weighted average estimated value of the time-based portion of MIUs granted was valued using the Black-Scholes model with the following inputs:
|
|
Year Ended |
|
|||||
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
||
Estimated values |
|
$ |
|
|
$ |
|
||
Expected life (in years) |
|
|
|
|
||||
Risk-free interest rate |
|
|
|
|
||||
Dividend yield |
|
|
% |
|
|
% |
||
Volatility |
|
|
|
|
||||
109
During February 2020, we modified the terms of certain MIU grants to provide for vesting subject to the satisfaction of certain conditions, which resulted in the recognition of $
Deferred Cash and Equity
In connection with our acquisitions in prior periods, we made deferred cash payments over the service period completed by certain employees and issued equity to certain employees subjected to service condition. Deferred cash and equity are recognized as compensation cost.
As of December 25, 2021, our outstanding deferred cash and equity, as it relates to all acquisitions, including acquisitions related to our discontinued operations, are as follows:
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Beginning outstanding deferred cash and equity balance |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Accruals |
|
|
|
|
|
|
|
|
|
|||
Restricted Class A Unit Vesting |
|
|
|
|
|
( |
) |
|
|
( |
) |
|
Cash payment |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
Ending outstanding deferred cash and equity balance |
|
$ |
|
|
$ |
|
|
$ |
|
|||
As of December 25, 2021, we have
Defined Contribution Plans
We provide tax-qualified retirement contribution plans in the United States for the benefit of all full-time employees. The plans are designed to provide employees with an accumulation of funds for retirement on a tax-deferred basis. Additionally, our operations in certain countries require we make payments to defined contribution plans for the benefit of our employees. Under the United States’ 401(k) and the foreign countries’ various defined contribution plans, we expensed $
Defined Benefit Plans
NOTE 13: DEBT
Our long-term debt balance consisted of the following:
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Long-term debt, net: |
|
|
|
|
|
|
||
1st Lien USD Term Loan(1) |
|
$ |
|
|
$ |
|
||
1st Lien Euro Term Loan(2) |
|
|
|
|
|
|
||
Long-term debt, net of unamortized discounts |
|
|
|
|
|
|
||
Unamortized deferred financing costs |
|
|
( |
) |
|
|
( |
) |
Current installments of long-term debt |
|
|
( |
) |
|
|
( |
) |
Total |
|
$ |
|
|
$ |
|
||
110
(1)
(2)
As of December 25, 2021, the material terms of our outstanding debt was as follows:
Debt |
|
Issue Date |
|
Issue |
|
|
Interest Rate |
|
Interest Payment |
|
Maturity Date |
|
1st Lien |
|
|
$ |
|
|
|
|
|||||
1st Lien |
|
|
€ |
|
|
|
|
|||||
Additions to and Modifications of Debt
In June, 2019, McAfee, LLC entered into an agreement to increase our term loans under the 1st Lien credit facility. We increased our 1st Lien USD Term Loan by $
Subsequent to the IPO of McAfee Corp. in October 2020, we repaid all outstanding principal obligations with respect to our 2nd Lien Term loan of $
On December 24, 2020, we prepaid $
In August 2021, we used a portion of the proceeds of the divestiture of the Enterprise Business (Note 4) to prepay $
As of December 25, 2021, our debt repayment obligations for the five succeeding fiscal years and thereafter are as follows:
|
|
(in millions) |
|
|
2022 |
|
$ |
|
|
2023 |
|
|
|
|
2024 |
|
|
|
|
2025 |
|
|
|
|
2026 |
|
|
|
|
Thereafter |
|
|
|
|
Total debt repayment obligations |
|
$ |
|
|
Revolving Credit Facility
In March 2020, we borrowed $
In October 2020, McAfee, LLC entered into an agreement to extend the maturity date of, and increased the amount available to us under, the Revolving Credit Facility. As a result of this agreement, the Revolving Credit Facility consists of a $
As of December 25, 2021 and December 26, 2020, we had a letter of credit of $
111
Debt Covenants and Restrictions
Our credit facilities contain customary covenants, including a springing financial maintenance covenant under our revolving credit facility, events of default and change of control provisions. In the event we have outstanding loans and letters of credit under the revolving credit facility of more than $
We may be required to make a mandatory prepayment in excess of the
•
•
•
NOTE 14: INCOME TAX
McAfee Corp. is taxed as a corporation and pays corporate federal, state and local taxes on income allocated to it from FTW based upon McAfee Corp.’s economic interest in FTW. FTW is a pass through entity for U.S. federal income tax purposes and will not incur any federal income taxes either for itself or its U.S. subsidiaries that are also pass through or disregarded subsidiaries. Taxable income or loss for these entities will flow through to its respective members for U.S. tax purposes. FTW does have certain U.S. and foreign subsidiaries that are corporations and are subject to income tax in their respective jurisdiction.
We account for income taxes under the asset and liability method, which requires the recognition of deferred tax assets and liabilities (“DTAs” and “DTLs”) for the expected future tax consequences of events that have been included in the financial statements. Under this method, we determine DTAs and DTLs on the basis of the differences between the financial statement and tax bases of assets and liabilities by using enacted tax rates in effect for the year in which the differences are expected to reverse. The effect of a change in tax rates on DTAs and DTLs is recognized in income in the period that includes the enactment date. We recognize DTAs to the extent that we believe that these assets are more likely than not to be realized. In making such a determination, we consider all available positive and negative evidence, including future reversals of existing taxable temporary differences, projected future taxable income, tax-planning strategies, carryback potential if permitted under the tax law, and results of recent operations. If we determine that we would be able to realize our DTAs in the future in excess of their net recorded amount, we would make an adjustment to the DTA valuation allowance, which would reduce the provision for income taxes. We record uncertain tax positions in accordance with ASC 740 on the basis of a two-step process in which (1) we determine whether it is more likely than not that the tax positions will be sustained on the basis of the technical merits of the position and (2) for those tax positions that meet the more-likely-than-not recognition threshold, we recognize the largest amount of tax benefit that is more than 50 percent likely to be realized upon ultimate settlement with the related tax authority.
The income (loss) from continuing operations before income taxes expense includes the following components:
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
U.S. |
|
$ |
( |
) |
|
$ |
( |
) |
|
$ |
( |
) |
Non-U.S. |
|
|
|
|
|
|
|
|
|
|||
Income (loss) before income taxes |
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|
112
The provision for income tax expense (benefit) from continuing operations consists of the following:
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Current: |
|
|
|
|
|
|
|
|
|
|||
Federal |
|
$ |
|
|
$ |
|
|
$ |
|
|||
State |
|
|
|
|
|
|
|
|
|
|||
Non-U.S. |
|
|
|
|
|
|
|
|
|
|||
Total current |
|
|
|
|
|
|
|
|
|
|||
Deferred: |
|
|
|
|
|
|
|
|
|
|||
Federal |
|
|
( |
) |
|
|
|
|
|
|
||
State |
|
|
( |
) |
|
|
|
|
|
|
||
Non-U.S. |
|
|
|
|
|
( |
) |
|
|
|
||
Total deferred |
|
|
( |
) |
|
|
( |
) |
|
|
|
|
Provision for income tax expense (benefit) |
|
$ |
( |
) |
|
$ |
|
|
$ |
|
||
The difference between the tax provision and the tax provision computed at the U.S. federal statutory income tax rate for each period was as follows:
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Income taxes computed at the U.S. federal statutory rate |
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|
Non-U.S. income taxed at different rates |
|
|
|
|
|
|
|
|
|
|||
Withholding taxes |
|
|
|
|
|
|
|
|
|
|||
State tax expense |
|
|
( |
) |
|
|
|
|
|
|
||
Partnership earnings flow through to partners |
|
|
|
|
|
|
|
|
|
|||
Redeemable noncontrolling interest |
|
|
( |
) |
|
|
|
|
|
|
||
Valuation allowances |
|
|
( |
) |
|
|
|
|
|
|
||
Foreign tax credits |
|
|
( |
) |
|
|
( |
) |
|
|
|
|
Uncertain tax positions |
|
|
|
|
|
( |
) |
|
|
|
||
Investment in partnerships |
|
|
|
|
|
( |
) |
|
|
|
||
Tax receivable agreement |
|
|
|
|
|
— |
|
|
|
— |
|
|
Other |
|
|
( |
) |
|
|
( |
) |
|
|
|
|
Provision for income tax expense (benefit) |
|
$ |
( |
) |
|
$ |
|
|
$ |
|
||
A portion of provision for income taxes has been indemnified by Intel (Note 7).
113
The components of the deferred tax assets and liabilities are as follows:
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Deferred tax assets: |
|
|
|
|
|
|
||
Accrued compensation and other benefits |
|
$ |
|
|
$ |
|
||
Deferred revenue |
|
|
|
|
|
|
||
Share-based compensation |
|
|
|
|
|
|
||
Net operating losses |
|
|
|
|
|
|
||
Credits |
|
|
|
|
|
|
||
Intangibles |
|
|
|
|
|
|
||
Interest expense carryforward |
|
|
|
|
|
|
||
Investment in partnership |
|
|
|
|
|
|
||
Other |
|
|
|
|
|
|
||
Total deferred tax assets |
|
|
|
|
|
|
||
Deferred tax liabilities: |
|
|
|
|
|
|
||
Unremitted earnings of non-US subsidiaries |
|
|
( |
) |
|
|
( |
) |
Investment in partnership |
|
|
|
|
|
( |
) |
|
Total deferred tax liabilities |
|
|
( |
) |
|
|
( |
) |
Valuation allowance |
|
|
( |
) |
|
|
( |
) |
Net deferred tax assets (liabilities) |
|
$ |
|
|
$ |
|
||
Reported as: |
|
|
|
|
|
|
||
Deferred tax assets |
|
$ |
|
|
$ |
|
||
Deferred tax liabilities |
|
|
( |
) |
|
|
( |
) |
Net deferred tax assets (liabilities) |
|
$ |
|
|
$ |
|
||
As of December 25, 2021, our deferred tax assets were primarily comprised of intangibles acquired in connection with reorganization transaction including basis adjustments created upon partner exchanges, investment in partnership, net operating losses, and amounts related to deferred revenue. As of December 26, 2020, our deferred tax assets were primarily comprised of intangibles acquired in connection with the reorganization transactions, net operating losses, credits and amounts related to deferred revenue.
As of December 25, 2021, our deferred tax liabilities were primarily comprised of unremitted earnings of Non-U.S. subsidiaries. As of December 26, 2020, our deferred tax liabilities were primarily comprised of outside basis differences due to the Reorganization Transactions and prior acquisitions.
As of December 25, 2021, we had federal, state, and non-U.S. net operating loss carryforwards of $
As of December 25, 2021, we are not permanently reinvested; therefore, we have recognized deferred taxes for all of our undistributed earnings of certain foreign subsidiaries.
Management assesses the available positive and negative evidence to estimate whether sufficient future taxable income will be generated to permit use of the existing deferred tax assets. On July 27, 2021, we completed the divestiture of the Enterprise Business (Note 4). As a result of the divestiture, we expect to utilize certain deferred tax assets from the domestic portion of the gain on the sale. In addition to objectively verifiable evidence, we have considered subjective evidence, such as our projections for future growth, in evaluating if the realizability of the net deferred tax assets has met the more likely than not recognition criteria. We have concluded that a full valuation allowance against the net deferred tax assets of our domestic entities will no longer be required. During the year ended December 25, 2021, we have released $
Changes to our deferred tax assets consisted of the following:
114
|
|
|
|
|
|
Offset To |
|
||||||||||
(in millions) |
|
Deferred Tax Asset |
|
|
|
Additional Paid-in Capital |
|
|
Provision for Income Tax (Expense) Benefits |
|
|
Income from Discontinued Operations |
|
||||
Release of valuation allowance on deferred tax assets |
|
$ |
|
|
|
$ |
|
|
$ |
211 |
|
|
$ |
|
|||
Exchanges and tax attributes in Fiscal 2021 |
|
|
|
|
|
|
|
|
|
|
|
|
|
||||
A reconciliation of the aggregate changes in the balance of gross unrecognized tax benefits was as follows:
|
|
Year Ended |
|
|||||||||
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
|
December 28, 2019 |
|
|||
Beginning gross unrecognized tax benefits |
|
$ |
|
|
$ |
|
|
$ |
|
|||
Settlements with taxing authorities |
|
|
( |
) |
|
|
|
|
|
|
||
Increases in tax positions for prior years |
|
|
|
|
|
|
|
|
|
|||
Decreases in tax positions for prior years |
|
|
( |
) |
|
|
( |
) |
|
|
|
|
Increases in tax positions for current year |
|
|
|
|
|
|
|
|
|
|||
Ending gross unrecognized tax benefits |
|
$ |
|
|
$ |
|
|
$ |
|
|||
We recognize interest and penalties related to unrecognized tax benefits within the Provision for income tax expense on the consolidated statements of operations.
We consider many factors when evaluating and estimating our tax positions, which may require periodic adjustments and may not accurately anticipate actual outcomes. Tax position recognition is a matter of judgment based on the individual facts and circumstances of our position evaluated in light of all available evidence. As of December 25, 2021 and December 26, 2020, we had uncertain tax positions of $
We are subject to examination by taxing authorities for income taxes in many of the domestic and foreign jurisdictions in which we operate.
Tax Receivable Agreement
Pursuant to our election under Section 754 of the Internal Revenue Code (the “Code”), we expect to obtain an increase in our share of the tax basis in the net assets of FTW when FTW LLC Units are redeemed or exchanged by the Continuing LLC Owners and MIUs are redeemed or exchanged by Management Owners. We intend to treat any redemptions and exchanges of LLC Units as direct purchases of LLC Units for United States federal income tax purposes. These increases in tax basis may reduce the amounts that we would otherwise pay in the future to various tax authorities. They may also decrease gains (or increase losses) on future dispositions of certain capital assets to the extent tax basis is allocated to those capital assets.
In October 2020, we entered into a TRA that provides for the payment by us of
115
As the net deferred tax assets have been recognized as of the date of divestiture of the Enterprise Business, the full liability under the TRA also became probable as of that date. During the year ended December 25, 2021, TRA liability increases of $
As of December 25, 2021, we have TRA liabilities of $
|
|
TRA Liability |
|
|
|
Offset To |
|
||||||||||||||
(in millions) |
|
Current Portion |
|
|
Noncurrent Portion |
|
|
|
Additional Paid-in Capital |
|
|
Other Income (Expense), Net |
|
|
Income from Discontinued Operations |
|
|||||
As of December 26, 2020 |
|
$ |
|
|
$ |
|
|
|
|
|
|
|
|
|
|
|
|||||
Exchanges and tax attributes that existed prior to divestiture |
|
|
|
|
|
|
|
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|||
Exchanges and tax attributes that existed on or after divestiture |
|
|
|
|
|
|
|
|
|
( |
) |
|
|
|
|
|
|
||||
As of December 25, 2021 |
|
$ |
|
|
$ |
|
|
|
$ |
( |
) |
|
$ |
( |
) |
|
$ |
( |
) |
||
See Note 1 for further information on changes to the TRA upon completion of the Merger.
NOTE 15: FAIR VALUE OF FINANCIAL INSTRUMENTS AND INTEREST RATE SWAPS
Fair Value of Financial Instruments
For assets and liabilities that are measured using quoted prices in active markets (Level 1), total fair value is the published market price per unit multiplied by the number of units held without consideration of transaction costs, discounts or blockage factors. Assets and liabilities that are measured using significant other observable inputs are valued by reference to similar assets or liabilities (Level 2), adjusted for contract restrictions and other terms specific to that asset or liability. For these items, a significant portion of fair value is derived by reference to quoted prices of similar assets or liabilities in active markets. For all remaining assets and liabilities, fair value is derived using other valuation methodologies, including option pricing models, discounted cash flow models and similar techniques (Level 3) and not based on market exchange, dealer or broker traded transactions. These valuations incorporate certain assumptions and projections in determining the fair value assigned to such assets or liabilities.
The fair value of our financial instruments are as follows:
(in millions) |
|
Level 1 |
|
|
Level 2 |
|
|
Level 3 |
|
|||
As of December 25, 2021 |
|
|
|
|
|
|
|
|
|
|||
Financial instruments not carried at fair value: |
|
|
|
|
|
|
|
|
|
|||
Long-term debt, gross of discounts and deferred |
|
$ |
|
|
$ |
( |
) |
|
$ |
|
||
Financial instruments carried at fair value: |
|
|
|
|
|
|
|
|
|
|||
Interest rate swaps |
|
$ |
|
|
$ |
( |
) |
|
$ |
|
||
As of December 26, 2020 |
|
|
|
|
|
|
|
|
|
|||
Financial instruments not carried at fair value: |
|
|
|
|
|
|
|
|
|
|||
Long-term debt, gross of discounts and deferred |
|
$ |
|
|
$ |
( |
) |
|
$ |
|
||
Financial instruments carried at fair value: |
|
|
|
|
|
|
|
|
|
|||
Interest rate swaps |
|
$ |
|
|
$ |
( |
) |
|
$ |
|
||
The fair value of the debt is based on third party quotations and is therefore classified as Level 2. The fair value of our derivative financial instruments, including interest rate swaps, are valued in the market using discounted cash flow techniques. These techniques incorporate Level 1 and Level 2 fair value measurement inputs such as spot rates, foreign currency exchange rates, and the instrument’s term, notional amount and discount rate.
The fair values of our financial instruments included in Cash and cash equivalents, Accounts receivable, net, Other current assets and Accounts payable and accrued liabilities on the consolidated balance sheets approximate their carrying amounts due to their short
116
maturities. We measure the fair value of money market accounts, included in Cash and cash equivalents on the consolidated balance sheets, on a recurring basis and have classified as Level 1 because the fair value is measured with quoted prices in active markets. These amounts have been excluded from the table.
There were no transfers of assets or liabilities between fair value measurement. Transfers between fair value measurement levels are recognized at the end of the reporting period.
Interest Rate Swaps
We have multiple interest rate swaps in order to fix the LIBOR portion of our USD denominated variable rate borrowings (Note 13). As of December 25, 2021, the outstanding effective hedging arrangements were as follows:
Notional Value |
|
Effective Date |
|
Expiration Date |
|
Fixed Rate |
$ |
|
|
|
|||
$ |
|
|
|
|||
$ |
|
|
|
|||
$ |
|
|
|
|||
$ |
|
|
|
|||
$ |
|
|
|
|||
$ |
|
|
|
In August 2021, we terminated $
The gross amounts of our interest rate swaps, which are subject to master netting arrangements, were as follows:
(in millions) |
|
Gross |
|
|
Gross |
|
|
Net amounts |
|
|||
As of December 25, 2021 |
|
|
|
|
|
|
|
|
|
|||
Other long-term assets |
|
$ |
|
|
$ |
( |
) |
|
$ |
|
||
Accounts payable and other current liabilities |
|
|
( |
) |
|
|
|
|
|
( |
) |
|
Other long-term liabilities |
|
|
( |
) |
|
|
|
|
|
( |
) |
|
As of December 26, 2020 |
|
|
|
|
|
|
|
|
|
|||
Accounts payable and other current liabilities |
|
$ |
( |
) |
|
$ |
|
|
$ |
( |
) |
|
Other long-term liabilities |
|
|
( |
) |
|
|
|
|
|
( |
) |
|
NOTE 16: REDEEMABLE NONCONTROLLING INTERESTS
We report a RNCI based on the LLC Units of FTW held by Continuing LLC Owners and vested MIUs held by Management Owners. The Continuing LLC Owners (or certain permitted transferees), subject to certain restrictions, can exchange their LLC Units for shares of Class A common stock on a
The Company’s decision of whether to exchange LLC Units for Class A common stock or cash is currently made solely at the discretion of the Continuing LLC Owners through their control of our Board of Directors. Accordingly, the LLC Units owned by the Continuing LLC Owners are treated as RNCI as the holders have the option to exchange their LLC Units for cash or for shares of the Corporation’s Class A common stock. The RNCI is reported at the greater of the redemption value of the units or the carrying value as of the balance sheet date, with a corresponding adjustment to Additional paid-in capital. The redemption value of our redeemable noncontrolling interests was derived from the closing stock price of the Company’s Class A common stock on the last day of the period.
117
Future redemptions or direct exchanges of LLC Units by the Continuing LLC Owners will result in a change in ownership and reduce or increase the carrying value of the RNCI and increase or decrease Additional paid-in capital when FTW has positive or negative net assets, respectively.
The following table summarizes the ownership and economic interest in FTW LLC:
|
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||||||||||
(in millions except percentages) |
|
Units Outstanding |
|
|
Ownership % |
|
|
Units Outstanding |
|
|
Ownership % |
|
||||
Number of LLC Units held by McAfee Corp. |
|
|
|
|
|
% |
|
|
|
|
|
% |
||||
Number of LLC Units and vested MIUs held by RNCI |
|
|
|
|
|
% |
|
|
|
|
|
% |
||||
Total LLC Units and vested MIUs outstanding |
|
|
|
|
|
% |
|
|
|
|
|
% |
||||
NOTE 17: EARNINGS (LOSS) PER SHARE
Basic earnings (loss) per share is computed by dividing net income (loss) attributable to McAfee Corp. for the period subsequent to the Reorganization Transactions by the weighted average number of shares of Class A common stock outstanding for the same period. Shares issued during the period and shares reacquired during the period are weighted for the portion of the period in which the shares were outstanding. Diluted earnings (loss) per share has been computed in a manner consistent with that of basic earnings (loss) per share while giving effect to shares of potentially dilutive common stock that were outstanding during the period.
Prior to the Reorganization Transactions, the FTW capital structure primarily included FTW LLC Units. Certain holders of these units exchanged their FTW LLC units for Class A common stock of the Corporation in the Reorganization Transactions with the remaining FTW LLC Units reflecting RNCI in the Corporation. The completion of the Reorganization Transactions created the Corporation’s current capital structure, which is not reflective of the capital structure of FTW’s business prior to the Reorganization Transactions. Therefore, net loss per unit information has not been presented for the portion of the fiscal year ended December 26, 2020, that was prior to the completion of the Reorganization Transactions, or for the fiscal year ended December 28, 2019.
Shares of Class B common stock do not share in the earnings or losses attributable to McAfee Corp. and are therefore not participating securities. As such, separate presentation of basic and diluted net loss per share of Class B common stock under the two-class method has not been presented. Shares of Class B common stock are, however, considered potentially dilutive shares of Class A common stock because shares of Class B common stock, together with the related FTW LLC Units, are exchangeable into shares of Class A common stock on a
118
The following table sets forth reconciliations of the numerators and denominators used to compute basic and diluted earnings (loss) per share of Class A common stock for the fiscal years ended December 25, 2021 and December 26, 2020. The basic and diluted earnings (loss) per share for the year ended December 26, 2020 represents only the period from October 22, 2020 to December 26, 2020, the period wherein the Corporation had outstanding Class A common stock.
|
|
Year Ended |
|
|
Year Ended |
|
||||||||||||||||||
(in millions except per share data) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||||||||||||||||||
|
|
Continuing Operations |
|
|
Discontinued Operations |
|
|
Total |
|
|
Continuing Operations |
|
|
Discontinued Operations |
|
|
Total |
|
||||||
Numerator: |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||
Net income (loss) |
|
$ |
|
|
$ |
|
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|
$ |
( |
) |
|||
Less: Net (income) loss attributable to FTW prior to the Reorganization Transactions |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
( |
) |
|
|
( |
) |
||||
Less: Net (income) loss attributable to redeemable noncontrolling interests after the Reorganization Transactions |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
|
|
|
|
|
|
|
|
|
|||
Net income (loss) attributable to McAfee Corp., basic and diluted |
|
$ |
|
|
$ |
|
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|
$ |
( |
) |
|||
Denominator: |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||
Weighted average shares of Class A common stock outstanding, basic and diluted |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||
Earnings (loss) per share attributable to McAfee Corp., basic |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||
Earnings (loss) per share, basic |
|
$ |
|
|
$ |
|
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|
$ |
( |
) |
|||
Earnings (loss) per share attributable to McAfee Corp., diluted |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||
Earnings (loss) per share, diluted(1)(2) |
|
$ |
|
|
$ |
|
|
$ |
|
|
$ |
( |
) |
|
$ |
( |
) |
|
$ |
( |
) |
|||
NOTE 18: VARIABLE INTEREST ENTITIES
Upon completion of our IPO, McAfee Corp. became the sole managing member of FTW with
119
The following table reflects the balance sheet of FTW that is consolidated within the consolidated balance sheets, including Receivable from Parent, net and McAfee Corp.’s interest in the variable interest entity (“VIE”) that are eliminated upon consolidation.
(in millions) |
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Assets |
|
|
|
|
|
|
||
Current assets: |
|
|
|
|
|
|
||
Cash and cash equivalents |
|
$ |
|
|
$ |
|
||
Accounts receivable, net |
|
|
|
|
|
|
||
Deferred costs |
|
|
|
|
|
|
||
Receivable from Enterprise Business |
|
|
|
|
|
|
||
Receivable from Parent |
|
|
|
|
|
|
||
Other current assets |
|
|
|
|
|
|
||
Current assets of discontinued operations |
|
|
|
|
|
|
||
Total current assets |
|
|
|
|
|
|
||
Property and equipment, net |
|
|
|
|
|
|
||
Goodwill |
|
|
|
|
|
|
||
Identified intangible assets, net |
|
|
|
|
|
|
||
Deferred tax assets |
|
|
|
|
|
|
||
Receivable from Parent, net |
|
|
|
|
|
|
||
Other long-term assets |
|
|
|
|
|
|
||
Long-term assets of discontinued operations |
|
|
|
|
|
|
||
Total assets |
|
$ |
|
|
$ |
|
||
Liabilities and deficit |
|
|
|
|
|
|
||
Current liabilities: |
|
|
|
|
|
|
||
Accounts payable and other current liabilities |
|
$ |
|
|
$ |
|
||
Accrued compensation and benefits |
|
|
|
|
|
|
||
Accrued marketing |
|
|
|
|
|
|
||
Income taxes payable |
|
|
|
|
|
|
||
Long-term debt, current portion |
|
|
|
|
|
|
||
Deferred revenue |
|
|
|
|
|
|
||
Payable to Enterprise Business |
|
|
|
|
|
|
||
Current liabilities of discontinued operations |
|
|
|
|
|
|
||
Total current liabilities |
|
|
|
|
|
|
||
Long-term debt, net |
|
|
|
|
|
|
||
Deferred tax liabilities |
|
|
|
|
|
|
||
Payable to Parent |
|
|
|
|
|
|
||
Other long-term liabilities |
|
|
|
|
|
|
||
Deferred revenue, less current portion |
|
|
|
|
|
|
||
Long-term liabilities of discontinued operations |
|
|
|
|
|
|
||
Total liabilities |
|
|
|
|
|
|
||
Members’ deficit: |
|
|
|
|
|
|
||
Deficit attributable to Continuing LLC Owners |
|
|
( |
) |
|
|
( |
) |
Deficit attributable to McAfee Corp. |
|
|
( |
) |
|
|
( |
) |
Total deficit |
|
|
( |
) |
|
|
( |
) |
Total liabilities and deficit |
|
$ |
|
|
$ |
|
||
120
NOTE 19: COMMITMENTS AND CONTINGENCIES
As of December 25, 2021, we have unconditional purchase obligations, including those related to our discontinued operations in connection with costs to support our obligations under our transition services agreement, of $399 million
As of December 25, 2021, excluding the amounts related to lease obligations which are disclosed in Note 6, the future minimum payments under all unconditional purchase obligations with a remaining term in excess of one year were as follows:
|
|
(in millions) |
|
|
2022 |
|
$ |
|
|
2023 |
|
|
|
|
2024 |
|
|
|
|
2025 |
|
|
|
|
2026 |
|
|
|
|
Total |
|
$ |
|
|
We are a party to various legal proceedings that have arisen in the ordinary course of our business. At present, we do not expect that any ordinary course legal proceedings, individually or in the aggregate, will have a material adverse effect on our business, results of operations, financial condition or cash flows.
NOTE 20: QUARTERLY FINANCIAL DATA (UNAUDITED)
The following table summarizes the Company's unaudited quarterly financial information for each of the four quarters of 2021 and 2020. As a result of the amendments to the agreement for the sale of the Enterprise Business discussed in Note 4, our results of operations have been recast from amounts reported prior to our Form 10-Q for the period ended September 25, 2021.
2021 for Quarter Ended |
|
|
|
|
|
|
|
|
|
|
|
|
||||
(in millions, except per share amounts) |
|
December 25, |
|
|
September 25, |
|
|
June 26, |
|
|
March 27, |
|
||||
Net revenue |
|
$ |
|
|
$ |
|
|
$ |
|
|
$ |
|
||||
Gross profit |
|
|
|
|
|
|
|
|
|
|
|
|
||||
Operating income |
|
|
|
|
|
|
|
|
|
|
|
|
||||
Net income (loss) from continuing operations |
|
|
|
|
|
( |
) |
|
|
|
|
|
|
|||
Net income (loss) from discontinued operations |
|
|
( |
) |
|
|
|
|
|
|
|
|
|
|||
Net income |
|
|
|
|
|
|
|
|
|
|
|
|
||||
Net income attributable to redeemable noncontrolling interests |
|
|
|
|
|
|
|
|
|
|
|
|
||||
Net income attributable to McAfee Corp. |
|
|
|
|
|
|
|
|
|
|
|
|
||||
Earnings (loss) per share - basic attributable to continuing operations |
|
|
|
|
|
( |
) |
|
|
|
|
|
|
|||
Earnings (loss) per share - basic attributable to discontinued operations |
|
|
( |
) |
|
|
|
|
|
|
|
|
|
|||
Earnings per share - basic |
|
|
|
|
|
|
|
|
|
|
|
|
||||
Earnings (loss) per share - diluted attributable to continuing operations |
|
|
|
|
|
( |
) |
|
|
|
|
|
|
|||
Earnings (loss) per share - diluted attributable to discontinued operations |
|
|
( |
) |
|
|
|
|
|
|
|
|
|
|||
Earnings per share - diluted |
|
|
|
|
|
|
|
|
|
|
|
|
||||
121
2020 for Quarter Ended |
|
|
|
|
|
|
|
|
|
|
|
|
||||
(in millions, except per share amounts) |
|
December 26, |
|
|
September 26, |
|
|
June 27, |
|
|
March 28, |
|
||||
Net revenue |
|
$ |
|
|
$ |
|
|
$ |
|
|
$ |
|
||||
Gross profit |
|
|
|
|
|
|
|
|
|
|
|
|
||||
Operating income (loss) |
|
|
( |
) |
|
|
|
|
|
|
|
|
|
|||
Net income (loss) from continuing operations |
|
|
( |
) |
|
|
( |
) |
|
|
( |
) |
|
|
|
|
Net income (loss) from discontinued operations |
|
|
( |
) |
|
|
|
|
|
|
|
|
( |
) |
||
Net income (loss) |
|
|
( |
) |
|
|
— |
|
|
|
|
|
|
|
||
Net loss attributable to noncontrolling interests |
|
|
( |
) |
|
N/A |
|
|
N/A |
|
|
N/A |
|
|||
Net loss attributable to McAfee Corp. |
|
|
( |
) |
|
N/A |
|
|
N/A |
|
|
N/A |
|
|||
Net loss per share - basic attributable to continuing operations |
|
|
( |
) |
|
N/A |
|
|
N/A |
|
|
N/A |
|
|||
Net loss per share - basic attributable to discontinued operations |
|
|
( |
) |
|
N/A |
|
|
N/A |
|
|
N/A |
|
|||
Net loss per share - basic |
|
|
( |
) |
|
N/A |
|
|
N/A |
|
|
N/A |
|
|||
Net loss per share - diluted attributable to continuing operations |
|
|
( |
) |
|
N/A |
|
|
N/A |
|
|
N/A |
|
|||
Net loss per share - diluted attributable to discontinued operations |
|
|
( |
) |
|
N/A |
|
|
N/A |
|
|
N/A |
|
|||
Net loss per share - diluted |
|
|
( |
) |
|
N/A |
|
|
N/A |
|
|
N/A |
|
|||
122
Item 9. Changes in and Disagreements With Accountants on Accounting and Financial Disclosure.
None.
Item 9A. Controls and Procedures.
Evaluation of Disclosure Controls and Procedures
As of December 25, 2021, an evaluation of the effectiveness of our disclosure controls and procedures (as defined in Rules 13a-15(e) and 15d-15(e) under the Securities Exchange Act of 1934, as amended (the “Act”)), was carried out by our management and with the participation of our Chief Executive Officer (principal executive officer) and Chief Financial Officer (principal financial officer). Based upon the evaluation, our principal executive officer and principal financial officer concluded that our disclosure controls and procedures were effective as of December 25, 2021.
Management's Report on Internal Control Over Financial Reporting
Our management are responsible for establishing and maintaining adequate internal control over financial reporting (as defined in Rules 13a-15(f) and 15d-15(f) under the Exchange Act). Internal control over financial reporting is a process designed to provide reasonable assurance regarding the reliability of financial reporting and the preparation of financial statements for external purposes in accordance with generally accepted accounting principles.
Our management, under the supervision of our Chief Executive Officer and Chief Financial Officer, conducted an evaluation of the effectiveness of our internal control over financial reporting based on the framework in Internal Control—Integrated Framework (2013), issued by the Committee of Sponsoring Organizations of the Treadway Commission. Based on this evaluation, management concluded that our internal control over financial reporting was effective as of December 25, 2021.
The effectiveness of our internal control over financial reporting as of December 25, 2021 has been audited by PricewaterhouseCoopers LLP, an independent registered public accounting firm, as stated in their report, which is included in Item 8 of this Annual Report on Form 10-K.
Changes in Internal Control Over Financial Reporting
There have been no changes in our internal control over financial reporting during the most recently completed fiscal quarter that materially affected, or is reasonably likely to materially affect, our internal control over financial reporting.
Item 9B. Other Information.
None.
Item 9C. Disclosure Regarding Foreign Jurisdictions that Prevent Inspections.
Not applicable.
123
PART III
Item 10. Directors, Executive Officers and Corporate Governance.
Executive Officers and Directors
Below is a list of the names, ages, positions and a brief account of the business experience of the individuals who serve as our executive officers and directors as of December 25, 2021.
Name |
|
Age |
|
Title |
|
Held Position Since |
Peter Leav |
|
51 |
|
President and Chief Executive Officer and Director |
|
2020 |
Venkat Bhamidipati |
|
55 |
|
Executive Vice President and Chief Financial Officer |
|
2020 |
Gagandeep Singh |
|
44 |
|
Executive Vice President, Chief Product and Revenue Officer |
|
2021 |
Sohaib Abbasi |
|
65 |
|
Director |
|
2018 |
Gunther Bright |
|
63 |
|
Director |
|
2021 |
Mary Cranston |
|
73 |
|
Director |
|
2018 |
Tim Millikin |
|
38 |
|
Director |
|
2017 |
Emily Rollins |
|
52 |
|
Director |
|
2021 |
Jon Winkelried |
|
62 |
|
Director |
|
2018 |
Kathy Willard |
|
55 |
|
Director |
|
2019 |
Jeff Woolard |
|
52 |
|
Director |
|
2019 |
Peter Leav has been the President, Chief Executive Officer and director since February 2020. Prior to McAfee, Peter served as President and CEO of BMC Software, a software and services company that helps enterprises meet escalating digital demands and maximize IT innovation, from December 2016 to April 2019. Prior to BMC, Peter served as President and CEO of Polycom, a global collaboration business serving the enterprise market, from December 2013 to September 2016. Peter also served as President of Industry and Field operations at NCR Corporation, the global leader in consumer transaction technologies. Prior to NCR, Peter was Corporate Vice President and General Manager of Motorola’s enterprise business in North America, Latin America and EMEA. Earlier in Peter’s career, Peter held executive sales leadership positions at Symbol Technologies, Cisco Systems, and Tektronix. Peter has served on the board of Box since June 2019, and previously served on the boards of Proofpoint (July 2019 to February 2020) and HD Supply, Inc. (October 2014 to July 2017). Peter holds a bachelor’s degree from Lehigh University. We believe that Peter’s board and industry experience qualifies Peter to serve on the Board.
Venkat Bhamidipati has been an Executive Vice President and the Chief Financial Officer since September 2020. In this role, Venkat oversees the finance, IT, and security operations strategy and teams that support McAfee’s business worldwide. Prior to McAfee, Venkat was an Executive Vice President and the Chief Financial Officer at Providence, a healthcare system with $25B in annual revenues, from July 2017 to September 2020. In this role, Venkat led all finance and most corporate functions, including information technology, growth and corporate development, supply chain, and real estate. Prior to this role at Providence, Venkat spent 13 years at Microsoft from June 2004 to July 2017, where Venkat held several executive positions, including, Chief Financial Officer of the Worldwide Enterprise and Partner Group, Chief Financial Officer of the Worldwide Operations Group, and Managing Director for Business Development and Strategy. Venkat earned a Master’s degree in Commerce from Osmania University and an M.B.A in Finance and Marketing from the Kelly School of Business at Indiana University.
Gagandeep Singh has been Executive Vice President, Chief Product and Revenue Officer since September 2021. Prior to McAfee, Gagandeep most recently served as Chief Product Officer for NortonLifeLock from May 2020 to September 2021. Gagandeep previously served as Chief Product Officer and Senior Vice President for Avast from November 2018 to April 2020 and as General Manager of Mobile, IoT and Family Business Units from August 2015 to November 2018. Prior to Avast, Gagandeep held a variety of roles leading product, strategy and operations at a number of consumer focused companies. Gagandeep earned a Master of Public Administration from Harvard University, an MBA from the Massachusetts Institute of Technology and a Bachelor of Science from the University of California at Berkeley.
Sohaib Abbasi has served as a director since November 2018. Sohaib also serves as chairman of Forecast.app (since May 2021) and as director for StreamSets Inc. (since July 2017). Sohaib previously served as a director of Red Hat (March 2011 to July 2019), New Relic (May 2016 to September 2019), Nutanix (March 2020 to December 2020) and as the chair of the board of Peakon (June 2020 to March 2021). In addition, Sohaib serves as a senior advisor to TPG. Sohaib served as president and chief executive officer of Informatica from July 2004 until August 2015. Sohaib served as chairperson of Informatica from March 2005 until December 2015. Prior to Informatica, Sohaib served at Oracle Corporation for 20 years, most recently, as a member of Oracle’s executive committee and as senior vice president of two major divisions, Oracle Tools and Oracle Education. Sohaib earned a bachelor’s degree and an M.S. degree from the University of Illinois at Urbana-Champaign. We believe that Sohaib’s board and industry experience qualifies Sohaib to serve on the Board.
124
Gunther Bright has served as director since September 2021. Gunther has served as Executive Vice President and General Manager of Global and U.S. Large Enterprises at American Express since 2020. Prior to this role, Gunther served as Executive Vice President and General Manager of the Merchant Services business of American Express from 2014 to 2020. Gunther has served on the board of Warburg Pincus Capital Corp. I-B since June 2021. Gunther currently serves as an Executive Committee Member of the Junior Achievement of New York Board of Directors, Vice Chairman and Executive Committee Member of the Alvin Ailey American Dance Theater Board of Trustees, and a member of the Executive Leadership Council. Gunther received his Bachelor of Arts degree in Economics from Pace University and completed an Advanced Executive Management Program at the Wharton School. We believe that Gunther’s board and industry experience qualifies Gunther to serve on the Board.
Mary Cranston has served as a director since November 2018. Since December 2012 when Mary retired as the Firm Senior Partner and Chair Emeritus of Pillsbury Winthrop Shaw Pittman LLP, an international law firm, Mary has served on various boards of companies and non-profits, including Visa, Inc. (since 2007), where Mary is a member of the finance committee and Nominating and Corporate Governance Committee, The Chemours Company (since 2015), Boardspan (since March 2016), CSAA Insurance Group (since 2008), and TPG Inc. (since January 2022), and previously served on the board of MyoKardia (May 2016 to November 2020). Mary holds a bachelor’s degree in political science from Stanford University, a J.D. degree from Stanford Law School, and M.A. degree in education from the University of California, Los Angeles. We believe that Mary’s legal and board experience qualifies Mary to serve on the Board.
Tim Millikin has served as a director since April 2017. Tim is a Partner at TPG based in San Francisco, California, where Tim co-leads TPG’s investment activities in software & enterprise technology. Tim has served on the boards of Delinea Inc. since March 2021, Government Brands since August 2021, and Ellucian since September 2015. Tim previously served on the boards of Renaissance Learning from July 2018 to January 2019, INFINIDAT from December 2017 to February 2019, and Isola Group from July 2012 to January 2018. Tim holds an M.B.A. degree from the Stanford Graduate School of Business, where Tim was an Arjay Miller Scholar, and a bachelor’s degree from Dartmouth College. We believe that Tim’s board and industry experience qualifies Tim to serve on the Board.
Emily Rollins has served as a director since September 2021. Emily has served in various positions at Deloitte & Touche LLP from September 1992 to September 2020, including most recently as an Audit & Assurance Partner, specializing in the technology, venture capital and life sciences industries. Emily currently serves on the boards of Dolby Laboratories, Inc., Xometry, Inc, and Science 37 Holdings, Inc., for which she serves as chair of the respective audit committees. Emily holds a B.A. in Accounting and International Relations from Claremont McKenna College. We believe that Emily’s financial expertise and industry experience qualify Emily to serve on the Board.
Jon Winkelried has served as a director since January 2018. Jon is the Chief Executive Officer and a Partner of TPG based in San Francisco, California. Prior to joining TPG in 2015, Jon was with Goldman, Sachs & Co. for more than 27 years, until Jon retired in 2009 as President and Co-Chief Operating Officer. Jon has served on the board of directors for Evolution Media since May 2016, Anastasia Beverly Hills since August 2018, Bounty Minerals LLC since December 2012, ATTN: from May 2019 to May 2021, MX Technologies since December 2020 and TPG Inc. since January 2022. Jon was elected to the Board of Trust of Vanderbilt University in 2012, and was elected Chair for the Investment Committee in 2017. Jon served as a trustee at the University of Chicago from 2006 to 2012. Jon received a bachelor’s degree in business from the University of Chicago and an M.B.A. degree from the University of Chicago. We believe that Jon’s board and industry experience qualifies Jon to serve on the Board.
Kathy Willard has served as a director since November 2019. Kathy served as the Chief Financial Officer of Live Nation Entertainment from September 2007 through June 2021, and currently serves as Senior Advisor. Prior to these roles, Kathy served in various positions at Live Nation Entertainment as well as its predecessors, Clear Channel Entertainment and SFX Entertainment, originally joining the organization in 1998. Earlier in Kathy’s career, Kathy served as an Audit Manager at Arthur Andersen from 1988 to 1993. Kathy is also a member of the board of directors for the House of Blues Music Forward Foundation. Kathy received a bachelor of business administration degree in accounting at the University of Oklahoma. We believe that Kathy’s financial expertise and industry experience qualify Kathy to serve on the Board.
Jeff Woolard has served as a director since August 2019. Jeff is the Chief Financial Officer at Solidigm, which he joined in September 2021. Previously, Jeff held numerous roles at Intel during the past 25 years, serving as a Corporate Vice President and the Chief Financial Officer of the Manufacturing and Technology Group from June 2020 to September 2021. Prior to this role, Jeff served as a Vice President and Chief Financial Officer for Intel Capital and the New Technology Group from March 2013 until June 2020, focusing on Intel’s corporate venture investments and acquisition activities. Jeff received a bachelor’s degree in finance from Arizona State University and an M.B.A. from the University of Washington. We believe that Jeff’s board and industry experience qualifies Jeff to serve on the Board.
Corporate Governance
Controlled Company
Our Sponsors and Intel control a majority of the voting power of our outstanding common stock. As a result, we are a “controlled company” under the Nasdaq Global Select Market’s (“Nasdaq”) corporate governance standards. As a controlled company, exemptions under Nasdaq’s standards exempt us from certain of Nasdaq’s corporate governance requirements, including the requirements:
125
Accordingly, for so long as we are a “controlled company,” you will not have the same protections afforded to stockholders of companies that are subject to all of Nasdaq’s corporate governance requirements. In the event that we cease to be a controlled company, we will be required to comply with these provisions within the transition periods specified in the rules of Nasdaq.
These exemptions do not modify the independence requirements for our audit committee, and we expect to satisfy the member independence requirement for the audit committee prior to the end of the transition period provided under Nasdaq listing standards and SEC rules and regulations for companies completing their initial public offering.
Board Composition and Director Independence
Our business and affairs are managed under the direction of our board of directors. Our amended and restated certificate of incorporation provides that our board of directors shall consist of at least three but not more than 12 directors and that the number of directors may be fixed from time to time by resolution of our board of directors. Our board of directors consists of nine members. Our amended and restated certificate of incorporation will provide that our board of directors will be divided into three classes of directors, as nearly equal in number as possible. The division of the three classes is as follows:
At this time, the Board believes that the classified board structure is in the best interest of the Company. The three-year term ensures that at any given time the majority of the directors have deep knowledge of the Company and a firm understanding of its goals, and it allows for continuity and stability of the Board, promoting the balance of long-term and short-term interests of the Company and its stockholders. The structure also safeguards the Company from third-party takeover attempts, as it requires a longer period to change majority control of the Board. A classified board remains accountable to the Company’s stockholders. The directors continue to have a fiduciary responsibility to the stockholders, and the stockholders have the ability to elect one third of the Board annually to ensure their interests are represented.
Amendments to certain provisions of our certificate of incorporation and bylaws, including the classified board provision, require the approval of holders of at least 66 2/3% of the voting power of our outstanding shares of capital stock. The Company believes this heightened threshold is appropriate as it relates to fundamental elements of our corporate governance. The provision does not preclude changes being made to governing documents but rather it requires broad stockholder consensus in order to effect change. By requiring a 66 2/3% stockholder vote, the Board is better positioned to protect the Company from third-party takeover attempts and encourage those interested in acquiring the Company to negotiate directly with the Board.
Upon the expiration of the initial term of office for each class of directors, each director in such class shall be elected for a term of three years and serve until a successor is duly elected and qualified and the director’s earlier death, resignation or removal. Subject to the terms of the stockholders agreement that we entered into in connection with our initial public offering (our “IPO”), any additional directorships resulting from an increase in the number of directors or a vacancy may be filled by the directors then in office, even if less than a quorum, or by a sole remaining director.
In connection with our IPO, we entered into a stockholders agreement with investment funds affiliated with certain affiliates of TPG Global, LLC (“TPG”) and Thoma Bravo, L.P. (“Thoma Bravo” and together with TPG, our “Sponsors”), Intel Americas, Inc. (“Intel”), and certain other stockholders governing certain nomination rights with respect to the Board. Under the agreement, we are required to take all necessary action to cause the Board to include individuals designated by TPG and Intel in the slate of nominees recommended by the Board for election by our stockholders, as follows:
126
TPG and Intel also have the exclusive right to remove their respective designees and to fill vacancies created by the removal or resignation of their designees, and we are required to take all necessary action to cause such removals and fill such vacancies at the request of TPG or Intel, as applicable.
The Board has undertaken a review of the independence of each director. Based on the information provided by each director concerning his or her background, employment, and affiliations, the Board has determined that each of Sohaib Abbasi, Gunther Bright, Mary Cranston, Tim Millikin, Emily Rollins, Jon Winkelried, Kathy Willard, and Jeff Woolard are independent directors under the rules of Nasdaq. In making this determination, the Board considered the relationships that such directors have with our Company and all other facts and circumstances that the Board deemed relevant in determining such directors’ independence, including beneficial ownership of our capital stock by each non-employee director and their affiliates, and the transactions involving them described in “Certain Relationships and Related Party Transactions.”
Annual Board and Committee Performance Review
Pursuant to our corporate governance guidelines, the Nominating and Corporate Governance Committee of the Board is responsible for reporting annually to the Board an evaluation of the overall performance of the Board. Additionally, the charters of the Audit Committee, Leadership Development and Compensation Committee, and Nominating and Corporate Governance Committees each provide that the respective committee is responsible for performing or participating in an annual evaluation of its performance, the results of which are presented to the Board.
Board Leadership Structure
We have not designated a chairperson or a lead director of the Board. The independent members of the Board periodically review the Board’s leadership structure and have determined that the Company and our stockholders are well served with this structure.
Board Committees
As of December 25, 2021, the Board has three standing committees: the Audit Committee; the Leadership Development and Compensation Committee; and the Nominating and Corporate Governance Committee. Each committee operates under its own written charter adopted by the Board, each of which is available on our website at https://ir.mcafee.com.
Audit Committee
Our Audit Committee consists of four non-employee directors: Gunther Bright, Mary Cranston, Emily Rollins and Kathy Willard, with Mary Cranston serving as chair of the committee. Our Audit Committee has determined that each of Gunther Bright, Mary Cranston, Emily Rollins and Kathy Willard meets the definition of “independent director” under the rules Nasdaq and under Rule 10A-3 under the Exchange Act. The Board has determined that Gunther Bright, Mary Cranston, Emily Rollins and Kathy Willard each is an “audit committee financial expert” within the meaning of the SEC’s regulations and applicable listing standards of Nasdaq. The Audit Committee’s responsibilities include:
127
Leadership Development and Compensation Committee
The Leadership Development and Compensation Committee of the Board is composed of Jon Winkelried, Tim Millikin, Jeff Woolard, and Sohaib Abbasi, with Jon Winkelried serving as chairperson of the committee. The Leadership Development and Compensation Committee’s responsibilities include:
Nominating and Corporate Governance Committee
The Nominating and Corporate Governance Committee is composed of Tim Millikin, Mary Cranston, and Jeff Woolard, with Tim Millikin serving as chairperson of the committee. The Nominating and Corporate Governance Committee’s responsibilities include:
128
Board Oversight of Risk Management
While the full Board has the ultimate oversight responsibility for the risk management process, its committees oversee risk in certain specified areas. In particular, the Audit Committee oversees management of enterprise risks as well as financial risks and is responsible for overseeing the review and approval of related party transactions. The Leadership Development and Compensation Committee is responsible for overseeing the management of risks relating to our executive compensation plans and arrangements and the incentives created by the compensation awards it administers. The Nominating and Corporate Governance Committee oversees risks associated with corporate governance, business conduct and ethics. Pursuant to the Board’s instruction, management regularly reports on applicable risks to the relevant committee or the full Board, as appropriate, with additional review or reporting on risks conducted as needed or as requested by the Board and its committees.
Leadership Development and Compensation Committee Interlocks and Insider Participation
None of the members of the Leadership Development and Compensation Committee has been one of our officers or employees. None of our executive officers currently serves, or in the past fiscal year has served, as a member of the board or the compensation committee of any entity that has one or more executive officers serving on the Board or the Leadership Development and Compensation Committee. For a description of transactions between us and members of the Leadership Development and Compensation Committee and affiliates of such members, see “Certain Relationships and Related Party Transactions.”
Code of Ethics
We have adopted a code of ethics that applies to all of our employees, officers and directors. The code of ethics is available on our website at https://ir.mcafee.com. If we make any substantive amendments to the code of ethics or grant any waiver, including any implicit waiver, from a provision of the code of ethics affecting our directors or executive officers, we will disclose the nature of such amendment or waiver on that website or in a Current Report on Form 8-K.
Corporate Governance Guidelines
We believe that good corporate governance is important to ensure that we are managed for the long-term benefit of our stockholders. The Board has adopted a set of corporate governance guidelines to set clear parameters for the operation of the Board. Our corporate governance guidelines are available on our website at https://ir.mcafee.com.
Director Nomination Process
The Nominating and Corporate Governance Committee recommends, and the Board nominates, candidates to stand for election as directors. The Nominating and Corporate Governance Committee has the authority to engage search firms for the purpose of identifying highly qualified director candidates, for which such firms are paid a fee. Stockholders may also nominate persons to be elected as directors in accordance with our bylaws and applicable law.
Board Membership Criteria
We seek a Board that collectively possess the experiences, skills, backgrounds, and qualifications appropriate to function effectively in light of the Company’s current and evolving business circumstances. It is the policy of the Board that directors should possess strong personal and professional ethics, integrity, and values; be business savvy and genuinely interested in the Company; and be committed to representing the long-term interests of our stockholders. Our goal is a balanced and diverse Board, with members whose skills, background and experience are complementary and, together, cover the spectrum of areas that impact our business.
Communications with Directors
129
Stockholders and other interested parties wishing to communicate directly with the Board or individual directors may do so by writing to the Board or such individual c/o the Secretary, McAfee Corp., 6220 America Center Drive, San Jose, California 95002. The Secretary will forward such communications to the Board or individual at or prior to the next meeting of the Board. The Secretary will not forward any communication determined in the Secretary’s good faith belief to be frivolous, unduly hostile, threatening or similarly unsuitable.
Item 11. Executive Compensation.
Compensation Discussion and Analysis
This Compensation Discussion and Analysis focuses on the compensation we provide to our executive officers listed in the “Summary Compensation Table for Fiscal 2021” (our “named executive officers”) and should be read in conjunction with the accompanying tables and text below. In accordance with SEC executive compensation disclosure rules, this Compensation Discussion and Analysis focuses on our compensation decisions with respect to our named executive officers for fiscal 2021. With the assistance of our independent compensation consultant, we have reviewed and plan to continue to review all elements of our executive compensation program. In this Compensation Discussion and Analysis and the accompanying tables and narratives, references to “the Board” and “the Committee” refer to the Board of Directors of the Company and its Leadership Development and Compensation Committee for all periods following the restructuring.
Our named executive officers for fiscal 2021 are:
Name |
|
Title |
Peter Leav |
|
President and Chief Executive Officer |
Venkat Bhamidipati |
|
Executive Vice President and Chief Financial Officer |
Gagandeep Singh(1) |
|
Executive Vice President, Chief Product and Revenue Officer |
Lynne Doherty McDonald(2) |
|
Former Executive Vice President, Global Sales and Marketing, Enterprise Business Group |
Terry Hicks(3) |
|
Former Executive Vice President, Consumer Business Group |
Industry Background and Overarching Compensation Considerations
Industry Background
McAfee has been a pioneer and leader in protecting consumers from cyberattacks for more than 30 years with integrated security, privacy and trust solutions. We built our platform through a deep, rich history of innovation and have established a leading global brand. We are securing the digital experience of a consumer who is increasingly living life online and singularly committed to one mission: to protect all things digital that matter to consumers through leading-edge cybersecurity. We live in a digital world. Consumers are increasingly moving their daily lives online, interacting through multiple devices, networks and platforms, and leveraging technology in nearly every aspect of their lives. This shift is most noticeable in the way individuals are working, banking, socializing, consuming, and paying, leading to a proliferation of digital touchpoints and applications. Remote work and increasing work from home arrangements are driving a pronounced convergence of work and personal life. While people expect effective and frictionless security at work and in their personal lives, this lifestyle shift has been accompanied by a more challenging threat landscape and an increase in points of vulnerability, risking individuals’ privacy, identity, data and other vital resources.
Competitive Hiring Environment and Fiscal 2021 Senior Executive Hiring
Cybersecurity is a fast-paced and competitive industry experiencing a widely-reported shortage of skilled talent and leadership in the face of high and increasing demand. We compete for executive talent with many other cybersecurity companies, large and small in geographic areas, such as Silicon Valley, and in related industries, such as software development, in which talented executives are in high demand, resulting in an increasingly competitive environment for attracting and retaining executive talent. Given the unique skillset required of our executive team as well as competition from industries beyond cybersecurity for our executives, during fiscal 2021 we offered competitive compensation that accounted for these external factors.
130
In recruiting Gagandeep Singh, who joined us in fiscal 2021, McAfee and the Committee were guided by the same executive compensation philosophy as described below for fiscal 2021 and negotiated the level of Gagandeep’s compensation and the terms of Gagandeep’s executive compensation arrangements, which included an offer letter, as well as a restricted stock unit (“RSU”) grant. These arrangements were finalized taking into account market compensation level determined by the Committee based on prior input from our independent compensation consultants and the experience of members of the Committee, internal pay equity considerations and the circumstances of our executives’ hires, including their prior roles and compensation in those roles.
Key Strategic Transactions
In fiscal 2021, we undertook two transformative strategic transactions that will shape our company going forward. First, on July 27, 2021, we completed the sale of certain assets of our Enterprise business (the “Enterprise Division Sale”) for $4.0 billion in cash before tax, which allowed us to pay a special dividend of $4.50 per Class A common share and reduce our debt by approximately $1 billion. As a result of the Enterprise Division Sale, McAfee became a pure play consumer cybersecurity company. Second, on November 5, 2021, we announced that we had entered into a definitive agreement to sell McAfee pursuant to the Merger (as defined above), which will result in a consortium of private investors owning McAfee and our delisting from NASDAQ. The Committee viewed (and continues to view, in the case of the ongoing process related to the Merger) the efforts and dedication of our currently employed named executive officers as vital to the success of those key strategic transactions.
Philosophy and Objectives of our Executive Compensation Program
Our global compensation philosophy is to compensate employees competitively, fairly and based on performance to incentivize actions that support achievement of our business objectives and equityholder value appreciation. To that end, we frequently monitor the integrity and functionality of our executive compensation program and refine it as we deem appropriate. Equitable pay practices are critical to our culture. During fiscal 2021, we continued our cybersecurity industry-leading efforts to review and bring about global pay parity, which we define as fair and equal pay for employees in the same job, level, and location, controlling for pay differentiators such as performance, tenure and experience. As part of our ongoing review of pay practices, in fiscal 2021 we engaged in extensive compensation audits covering 43 countries and 6,345 employees because we believe that every employee should be compensated fairly and equally for the employee’s individual contribution to the company.
Consistent with our global compensation philosophy, our goal has been to implement an executive compensation program that drives results and that is built upon our long-standing executive compensation philosophy and objectives, as outlined below:
Key Features of Our Executive Compensation Program
Our executive compensation program includes the following practices, each of which the Committee believes reinforces our executive compensation philosophy and objectives:
We have followed good governance practices in our executive compensation practices by:
131
Decision-making Responsibility
During fiscal 2021, the Leadership Development and Compensation Committee generally oversaw our executive compensation program.
The Committee considers the views and recommendations of management, in particular those of our President and Chief Executive Officer and our Chief People Officer, in making decisions regarding executive compensation. Among other things, our Chief Executive Officer makes recommendations about executive performance, annual base salary levels, annual incentive targets, and payout levels and long-term incentive grants for our named executive officers (other than for the Chief Executive Officer).
During fiscal 2021, the Committee convened two meetings in which executive compensation matters were discussed and acted by written consent on eleven other occasions. In addition, the Board held one special meeting and acted by written consent on one occasion on matters that included certain items related to our executive compensation program.
Compensation Setting Process
Independent Compensation Consultants
In fiscal 2021, we continued to engage Compensia, a nationally known compensation consulting firm, to serve as an independent advisor to the Committee on executive compensation matters. In late fiscal 2020, Compensia assisted the Committee with an evaluation of the competitiveness of the Company’s existing executive compensation program and assisted in developing recommendations regarding executive compensation adjustments for fiscal 2021.
Market Comparison
For fiscal 2021, the Committee considered market pay practices when setting compensation for executive officers. The Committee uses market data to assess the overall competitiveness and reasonableness of the compensation elements and the Company’s overall executive compensation program. As a starting point, we assess overall competitiveness and reasonableness of compensation at a target total direction compensation basis, while appropriately balancing the individual base salary and target annual cash incentive components. Assessment of each of the base salary, target annual cash incentive and equity holding elements is reviewed against market percentiles, competitive retentive value, and annual target compensation. For our named executive officers, our long-term incentive program targets a total unvested equity retention value of our equity at approximately five times’ annual grant values of our peer group at the 60th percentile. In assessing the competitive market, we use survey data from the peer group noted below as the primary market data source, with proxy peer group data providing a supplemental viewpoint.
The Committee believes that compensation decisions are complex and require a deliberate review of Company performance, market compensation levels, and other factors it deems relevant in a given situation. Accordingly, factors that may influence the amount of compensation awarded include, but are not limited to:
132
The Committee believes that the Company’s executive compensation peer group should reflect the markets in which the Company competes for business and executive talent. Accordingly, the Company’s peer group consists of peer companies that we believe are our most direct cybersecurity and business competitors, and software companies that are generally comparable to the Company in terms of revenue and number of employees, taking into account the availability of relevant comparison data. No one factor determines whether a company is included within our peer group. We believe these comparisons provide us with a valuable window into the executive pay practices of companies similar to us, and we seek to use information about their compensation levels whenever available to us. As a result of these similarities, we view the companies in the custom peer group below as those that are mostly likely to compete with us for executive talent. We do not pre-screen members of our peer group for their compensation levels or practices. The Committee, together with Compensia and our management team, expects to periodically re-evaluate and revise our selection criteria and list of peer companies, as it deems appropriate.
After soliciting input from Compensia, the Committee determined our peer companies for purposes of benchmarking fiscal 2021 compensation were as follows:
|
|
|
Cadence Design Systems |
Citrix Systems |
F5 Networks |
|
|
|
FireEye |
Fortinet |
Juniper Networks |
|
|
|
NortonLifeLock |
Nuance Communications |
Open Text |
|
|
|
Palo Alto Networks |
Proofpoint |
Splunk |
|
|
|
Synopsys |
Teradata |
|
|
|
|
For purposes of benchmarking compensation for fiscal 2021, we removed Carbon Black and ForeScout Technologies, which had been part of our peer group for fiscal 2020, because both companies were acquired and after those acquisitions were no longer publicly traded.
Elements of Compensation
Consistent with our pay-for-performance philosophy and executive compensation program objectives described above, in determining the fiscal 2021 adjustments to executive compensation levels discussed below, the Committee considered each named executive officer’s role and responsibilities, personal performance and contributions, business performance and conditions, overall job market conditions, internal pay equity, and competitive market data.
The following is a discussion of the primary elements of the compensation for each of our named executive officers.
Annual Base Salary
Annual base salary is one element of the cash compensation that we provide to our named executive officers and is determined based on the core contributions the executive is expected to make and the specific requirements for the named executive officer’s role. As noted above, we generally consider how a named executive officer’s base salary contributes to named executive officer’s total target direct compensation, and its resulting positioning as compared to our peer group. Under this construct, we place more emphasis on performance-linked elements of total direct compensation as we believe annual incentive pay provides a stronger connection between pay and performance.
In connection with our annual compensation review for fiscal 2021, we reviewed the annual base salaries of the named executive officers who were then employed by us. As part of that review, in late fiscal 2020, our Chief Executive Officer, in collaboration with our Chief People Officer, made recommendations to the Committee regarding annual base salary levels of our named executive officers (other than related to our Chief Executive Officer) who were then employed and any adjustments to their base salary levels. Recommendations were based on market considerations (including base salary levels relative to our peers described above) and a holistic assessment of the named executive officer’s performance over the prior year.
133
As a result of this review, the Committee approved an increase in Terry Hicks’ annual base salary in fiscal 2021 from $650,000 to $675,000, effective January 1, 2021, to further align Terry’s compensation with the competitive market.
In connection with our annual review, no changes were made to the annual base salary of Peter Leav, Venkat Bhamidipati or Lynne Doherty McDonald, each of whom was determined to have an annual base salary that was consistent with our peer group, as well as individual performance and contributions.
Gagandeep Singh was hired after the beginning of fiscal 2021 and Gagandeep’s annual base salary was determined in a similar manner and with special consideration given to the need to secure Gagandeep’s hire in light of Gagandeep’s preexisting compensation arrangements, alternative employment opportunities, the competitive market, and internal pay equity. Gagandeep’s annual base salary remained the same throughout fiscal 2021 after Gagandeep’s date of hire.
The Committee may also adjust annual base salaries of our named executive officers at other times during the year in connection with promotions, increased responsibilities or to maintain market competitive compensation levels, but did not do so in fiscal 2021.
The table below sets forth the 2021 annualized base salary level for each of our named executive officers as of the end of fiscal 2021 (for those named executive officers who remained employed with us as of that time):
Named Executive Officer |
|
2021 Base |
|
|
Peter Leav |
|
$ |
900,000 |
|
Venkat Bhamidipati |
|
$ |
650,000 |
|
Gagandeep Singh |
|
$ |
600,000 |
|
Annual Incentives
Our executive compensation program ties a substantial portion of the cash compensation that our executives are eligible to receive directly to the Company’s performance. We believe our annual incentive plan (“AIP”) is an integral component of our overall executive compensation program because a competitive incentive program is essential to attracting, retaining, and motivating talented leaders. Our AIP is linked to the achievement of certain individual and company goals that we believe are important for our short-term and long-term success and are key to driving increases in the value of the Company. Payouts under our AIP are based on the Company’s performance and our executives’ performance against Company and executive goals, respectively, with the AIP funding only if the Company’s performance exceeds threshold goals relating to “Billings”, “Unlevered Free Cash Flow” (for the period of fiscal 2021 that ended in connection with the consummation of the Enterprise Division Sale), “EBITDA” and “Net Revenues”, each as described below.
In addition, prior to the Enterprise Division Sale, each of our named executive officers that was employed by us prior to the closing of the Enterprise Division Sale was aligned with our Consumer business unit, our Enterprise business unit or our overall Company performance (which we refer to as “Corporate” and which encompasses both the Consumer and Enterprise business units). These alignments in turn affected how performance was measured with respect to that named executive officer and how named executive officer’s AIP payout is determined. In light of the Enterprise Division Sale, the Committee eliminated the distinction between Consumer business unit and Corporate alignment (since the Company consisted solely of its Consumer business unit).
Setting the Annual Incentive Target Opportunity
In general, each of our named executive officers participates in our AIP and is eligible to receive a cash-based annual incentive at a target level that is based on a percentage of the officer’s calendar year annual base salary. These annual incentive targets are prorated for any changes in annual base salary during the calendar year and for any partial years of service. After reviewing our named executive officers’ total on-target earning opportunities as part of our annual compensation review process, Terry Hicks’ annual incentive target for fiscal 2021 was increased from $750,035 to $825,000. As noted above, Gagandeep Singh joined us after the beginning of fiscal 2021 and Gagandeep’s annual incentive opportunity was determined in connection with Gagandeep’s hire in a manner that is consistent with our general philosophy but with particular attention on the need to secure Gagandeep’s hire in light of Gagandeep’s preexisting compensation arrangements, alternative employment opportunities, the competitive market, and provide for internal pay equity. No adjustment was made to the AIP target awards for Peter Leav, Venkat Bhamidipati or Lynne Doherty McDonald in fiscal 2021.
The table below sets forth the fiscal 2021 annual incentive target opportunities for each of our named executive officers who remained employed with us as of the end of fiscal 2021:
134
Named Executive Officer |
|
Target |
|
|
Peter Leav |
|
$ |
1,350,000 |
|
Venkat Bhamidipati |
|
$ |
650,000 |
|
Gagandeep Singh |
|
$ |
300,000 |
|
AIP Pool Funding and Attainment
For fiscal 2021, the Committee established an AIP pool for all participants in our AIP, including our participating named executive officers, and the performance metrics and goals for our fiscal 2021 AIP. The initial target funding for this pool was equal to the aggregate amount that would be payable to all AIP participants if each participant received the participant’s full annual incentive target, subject to achievement of financial metrics, adjustment for new hires, changes in status, and changes in participant compensation as provided in the AIP.
As noted above, following the Enterprise Division Sale, each AIP participant, including our named executive officers, if they were not already so aligned became aligned with our overall Corporate performance. Prior to the Enterprise Division Sale, certain named executive officers were aligned with either our Enterprise business unit or our Consumer business unit. Our named executive officers were aligned as follows prior to the Enterprise Division Sale:
Named Executive Officer |
|
AIP Alignment |
Peter Leav |
|
Corporate |
Venkat Bhamidipati |
|
Corporate |
Gagandeep Singh |
|
N/A |
Lynne Doherty McDonald |
|
Enterprise |
Terry Hicks |
|
Consumer |
Through the end of our fiscal July month (“Fiscal July”), the funding of the AIP pool with respect to those AIP participants aligned with Corporate, Consumer and Enterprise was based on measuring the relevant targets for the metrics set forth below.
Corporate |
Consumer |
Enterprise |
EBITDA for the Company (25% weighting) Billings for the Company (25% weighting) Net Revenue for the Company (25% weighting) Unlevered Free Cash Flow for the Company (25% weighting) |
Corporate Attainment(1) (25% weighting) EBITDA for the Consumer business unit (25% weighting) Billings for the Consumer business unit (25% weighting) Net Revenue for the Consumer business unit (25% weighting) |
Corporate Attainment(1) (25% weighting) EBITDA for the Enterprise business unit (25% weighting) Billings for the Enterprise business unit (25% weighting) Net Revenue for the Enterprise business unit (25% weighting) |
Following Fiscal July, the funding of the AIP pool with respect to those AIP participants was based on measuring the relevant targets for the metrics set forth below.
Corporate |
EBITDA for the Company (33% weighting) Billings for the Company (33% weighting) Net Revenue for the Company (33% weighting) |
Performance against each metric is calculated on a constant currency basis (i.e., calculated assuming no changes in the currency exchange rates from budgeted currency exchange rates). A minimum threshold of achievement for each applicable metric within the Corporate-, Consumer- or Enterprise-related calculations (as applicable) had to be achieved for any portion of the AIP pool related to participants with that alignment to be funded. Each of the fiscal 2021 AIP metrics is described below.
135
Financial |
Description |
EBITDA |
For the AIP and our post-IPO long-term incentive program (discussed below), EBITDA, with respect to the period through the end of Fiscal July, is cash EBITDA, which is a non-GAAP financial measure, which is defined as net income (loss), excluding the impact of amortization of intangible assets, equity-based compensation expense, interest expense and other provision for income tax expense, foreign exchange gain or loss, and other costs that we do not believe are reflective of our ongoing operations, and excluding the impact of depreciation expense and other non-operating costs (as described in “Management’s Discussion and Analysis of Financial Condition and Results of Operations”), and further adjusted to eliminate the impact of purchase accounting, capital expenditures, capitalized software expenses and other revenue that we not believe is reflective our ongoing operations, plus the change in year-over-year deferred revenue. For the AIP and our post-IPO long-term incentive program, EBITDA, with respect to the period following Fiscal July, is pro forma adjusted EBITDA—the same as cash EBITDA, but excludes “pro forma stranded costs,” which include general corporate overhead, and other shared or dis-synergy costs previously allocated to our Enterprise business. This pro forma adjustment represents the estimated impact of removing certain costs primarily as a result of the divestiture of our Enterprise business in 2021.
|
Billings |
Billings, with respect to an applicable period, is a non-GAAP financial measure, which is defined as net revenue plus the change in deferred revenue from the beginning to the end of the period, excluding the impact of deferred revenue assumed through acquisitions during the period. Annual Billings includes changes in our deferred revenue during the period. |
Net Revenue |
Net revenue is as determined under GAAP for the applicable period.
|
Unlevered Free Cash Flow |
Unlevered Free Cash Flow, with respect to an applicable period, is a non-GAAP financial measure that represents net cash from operating activities less capital expenditures, and then adding back interest payments and items related to projects with a limited time frame that are outside normal operating activities and are generally transformational in nature. |
|
|
The AIP pool for fiscal 2021 is funded proportionally based on achievements of the relevant AIP metrics for the relevant period of fiscal 2021 prior to the Enterprise Division Sale and for the period following Fiscal July. The funding of the AIP pool increases or decreases for achievement above or below the target achievement level, subject to minimum achievement levels of 90% of the EBITDA target, 90% of the Unlevered Free Cash Flow target (for the period through the end of Fiscal July), 95% of the Billings target, and 95% of the Net Revenue target. After all financial metrics are compared to relevant targets (and subject to these minimums), they are weighted as described above and the weighted metrics are added together. The funding of the AIP pool is then determined by applying a slope of 2.5x to the resulting percentage (i.e., subject to the thresholds described above, for each percentage above or below 100%, the AIP pool funding increases or decreases by 2.5%), subject to a maximum achievement level of 140% (which results in funding of the AIP pool at 200% of its target level).
Before determining the final AIP pool funding level, the Committee and the Board, with input from our President and Chief Executive Officer, may then adjust the aggregate pool funding level based upon a combination of Company performance as well as the Board’s evaluation of a variety of subjective and objective Company performance metrics. For fiscal 2021, the Committee and the Board increased the aggregate pool funding by $500,000. Our fiscal 2021 company performance goals, and our levels of achievement of those goals, were as follows for the period through Fiscal July and for the period following Fiscal July:
Prior to the Enterprise Division Sale (Through the End of Fiscal July) |
||||||
Performance Metric |
|
Goal (in $MM) |
|
Actual (in $MM) |
|
Percentage |
EBITDA (Corporate) |
|
$632 |
|
$792 |
|
125% |
EBITDA (Consumer) |
|
$561 |
|
$652 |
|
116% |
EBITDA (Enterprise) |
|
$71 |
|
$139 |
|
196% |
Billings (Corporate) |
|
$1,706 |
|
$1,847 |
|
108% |
Billings (Consumer) |
|
$1,077 |
|
$1,177 |
|
109% |
Billings (Enterprise) |
|
$629 |
|
$670 |
|
107% |
Unlevered Free Cash Flow (Corporate) |
|
$1,251 |
|
$1,391 |
|
111% |
Corporate Attainment (Consumer) |
|
$2,642 |
|
$2,889 |
|
109% |
Corporate Attainment (Enterprise) |
|
$2,684 |
|
$2,980 |
|
111% |
Net Revenue (Corporate) |
|
$1,737 |
|
$1,839 |
|
106% |
Net Revenue (Consumer) |
|
$1,004 |
|
$1,059 |
|
106% |
Net Revenue (Enterprise) |
|
$734 |
|
$780 |
|
106% |
136
Following the Enterprise Division Sale (After Fiscal July) |
||||||
Performance Metric |
|
Goal (in $MM) |
|
Actual (in $MM) |
|
Percentage |
EBITDA (Corporate) |
|
$402 |
|
$520 |
|
129% |
Billings (Corporate) |
|
$813 |
|
$917 |
|
113% |
Net Revenue (Corporate) |
|
$789 |
|
$860 |
|
109% |
After the AIP pool has been funded, our President and Chief Executive Officer (with input from our Chief People Officer) may exercise discretion to adjust the funded percentages. In fiscal 2021, this discretion was applied to increase the Corporate-aligned AIP pool funding from 133% to 142%, to increase the Consumer-aligned AIP pool funding from 126% to 140% and to decrease the Enterprise-aligned AIP pool funding from 178% to 143% (in each case, for the first half of fiscal 2021). In fiscal 2021, this discretion was also applied to decrease the Corporate-aligned AIP pool funding from 143% to 137% (for the period of fiscal 2021 following Fiscal July). No adjustments were made with respect Corporate-, Consumer- or Enterprise-aligned AIP pool funding for Fiscal July.
After the funding of each AIP segment (Corporate, Consumer and Enterprise) was determined by the Committee, individual incentives for each of our named executive officers were then determined by the Committee by applying the relevant AIP pool funding percentage for the named executive officer to the named executive officer’s individual incentive target. The actual amount paid to the named executive officer is then determined by multiplying that amount by a discretionary multiplier determined by the Committee, based on its assessment of the named executive officer’s individual performance relative to predetermined operational and strategic goals. Based on individual performance, a named executive officer was eligible to earn 0% to 200% of the total funded AIP amount.
For our named executive officers who were eligible to participate in our AIP, individual goals related to our financial and operational performance, as well as adding new portfolio offerings, strategic transactions, building out existing offerings, consumer and enterprise customer initiatives, business optimization and driving a diverse and inclusive culture. These operational and strategic goals were designed to be challenging but achievable with strong management performance.
Following the end of the year, each of our named executive officers assessed the named executive officer’s individual performance against that named executive officer’s individual performance goals for the fiscal year. For fiscal 2021, our President and Chief Executive Officer reviewed these self-assessments (other than with respect to our President and Chief Executive Officer) and the achievement of each named executive officer who was then employed by us and recommended an attainment level for each named executive officer’s annual incentive based on individual performance. After reviewing our President and Chief Executive Officer’s recommendations and these self-assessments, the Committee recommended, and the Board approved the following AIP payouts:
Named Executive Officer |
|
Actual |
Peter Leav |
|
3,002,400 |
Venkat Bhamidipati |
|
1,084,200 |
Gagandeep Singh |
|
360,904(2) |
Lynne Doherty McDonald |
|
255,200(3) |
Commission Arrangement for Lynne Doherty McDonald
In addition to participating in the AIP (as of the beginning of fiscal 2021), through the end of Fiscal July, Lynne Doherty McDonald was eligible to earn cash commission payments based on Annual Bookings related to our Enterprise business unit, which were paid within 30 days of being earned. Annual Bookings are a non-GAAP financial measure, which are defined as contractual commitments for McAfee to provide product, support, subscription and/or professional services to a customer over a contractual term. Under this arrangement, Lynne Doherty McDonald would have been eligible to earn up to $675,070 on a full-year basis if the Annual Bookings – Enterprise target was achieved. Lynne Doherty McDonald’s commission payment rates, as in effect while Lynne was employed by us, are summarized below:
137
Attainment (% of Goal) |
|
Commission Rate |
0-100% |
|
0.036% |
>100-101% |
|
0.125% |
>101-102.5% |
|
0.214% |
>102.5% |
|
0.285% |
The Annual Bookings – Enterprise goal for fiscal 2021 was $1,388,000,000 but was pro-rated based on Lynne’s termination date. To the extent attainment exceeds the relevant tier shown above, commissions would be earned at the higher commission rate reflected above. Based on actual achievement through the end of Fiscal July equal to $918,827,204 (66.2% of the full-year target level), Lynne received an actual payout for fiscal 2021 equal to $423,534.
Long-Term Incentives
The Board believes that members of senior management should hold a personally significant interest in the equity of the Company. In furtherance of this philosophy, the Company issued incentive equity awards to our senior management team in fiscal 2021, which (in combination with personal investments in the Company’s equity made, and incentive equity awards from prior fiscal years held, by certain members of our senior management team) serve to align their interests and the interests of our equityholders.
Long-term incentives continued to be the most heavily weighted component of our executive compensation program for named executive officers in fiscal 2021. This reflects our focus on aligning executive interests with those of our equityholders, supporting a pay-for-performance philosophy, and encouraging executives to take actions that we believe will grow the value of the Company over time. We also believe that long-term equity awards serve an important retentive function and are essential to attract and retain talented leaders in the competitive market in which we operate.
Pre-IPO Long-Term Incentive Program
Before our IPO, FTW (our ultimate parent company prior to our IPO) maintained an incentive equity plan (the “2017 Plan”) under which we issued profits interests (called Management Incentive Units or “MIUs”) and RSUs to our senior management team and other employees and service providers. These awards held by certain of our named executive officers are generally eligible to vest based on continued employment over four years, subject to accelerated vesting in connection with the Merger as described below.
Pre-IPO Purchased Equity Program
Prior to our IPO, we also offered each of our named executive officers the opportunity to purchase Class A Units of FTW at fair market value. Because the Class A Units purchased by our named executive officers represent an investment of personal funds by the executives, these units were not subject to a vesting requirement and are not reflected in the executive compensation tables below. Of our named executive officers who remain employed by us, Peter Leav made a personal cash investment in Class A Units of FTW.
IPO-Related Changes to Pre-IPO Equity Holdings and Post-Lockup Transfer Restrictions on Pre-IPO Equity
Prior to our IPO, our business was conducted through FTW and its subsidiaries. FTW is treated as a partnership for U.S. federal income tax purposes. Our IPO was conducted through what is commonly referred to as an “Up-C” structure. The Up-C structure can allow existing owners of a partnership (or limited liability company that is treated as a partnership for U.S. federal income tax purposes) to continue to realize the tax benefits associated with their ownership of an entity that is treated as a partnership for income tax purposes following an initial public offering, and provides potential tax benefits and associated cash flow to both the issuer corporation and the existing owners of the partnership (including FTW as a limited liability company that is treated as a partnership for U.S. federal income tax purposes). Our continuing pre-IPO equityholders (which included our named executive officers other than Gagandeep Singh) have the right, from time to time and subject to certain restrictions, to exchange one or more of their FTW units for (1) either (i) cash based upon the market price of the shares of our Class A common stock (in the case of MIUs, after those MIUs are exchanged for FTW Class A Units of equal value), or (ii) at our option, shares of our Class A common stock on a one-for-one basis (in the case of MIUs, after those MIUs are exchanged for FTW Class A Units of equal value) and we will cancel a corresponding number of shares of Class B common stock held by the exchanging member in connection therewith, to the extent the exchanging member has shares of Class B common stock, subject to customary conversion rate adjustments for stock splits, stock dividends, reclassifications, and other similar transactions and (2) payments of additional amounts pursuant to our tax receivable agreement (which is described above and which was amended in connection with the signing of the definitive agreement related to the Merger, as also described above). Because the payments under the tax receivable agreement do not represent compensation to our named executive officers, no amount is shown in the compensation tables below related to those payments.
138
In connection with our IPO, each of our named executive officers other than Gagandeep Singh (who was not employed by us at the time) entered into an equity adjustment agreement that provided for certain adjustments to their equity and equity-based awards issued by FTW prior to our IPO. Under each of these equity adjustment agreements (i) FTW Class A Units issued to the named executive officer before the completion of our IPO (whether purchased directly or issued in connection with the vesting of awards) may, at the election of the applicable named executive officer, be exchanged for Class A common stock, (ii) vested MIUs, including MIUs that become vested following our IPO, may, at the election of the participant, be exchanged for Class A common stock, (iii) MIUs that were not vested at the time of our IPO remained outstanding and continued to vest on and be subject to the same terms and conditions that applied prior to our IPO, except for the adjustments described in the following paragraph, (iv) outstanding phantom profits interests (referred to as Management Equity Participation Units or “MEPUs”) and RSUs that by their terms became payable in connection with our IPO were generally settled in shares of Class A common stock following our IPO, and (v) outstanding MEPUs and RSUs that were not vested as of immediately before the completion of our IPO were converted into RSUs in respect of Class A common stock (“Converted RSUs”), and such Converted RSUs continued to vest on and be subject to the same terms and conditions that applied to the corresponding RSU prior to our IPO, except that upon vesting the Converted RSU would be settled in Class A common stock.
The portion of any award subject to vesting based on TPG and certain co-investors receiving specified returns (which were held only by Terry Hicks among our named executive officers who remained employed as of our IPO) were adjusted so that the vesting after our IPO was based on the returns received by TPG (and not other co-investors). Further, in January 2021, the Committee approved an additional vesting opportunity with respect to all awards (including those held by our named executive officers) that are eligible to vest based on TPG receiving specified returns such that these awards, if they had not earlier vested based on TPG returns, would be eligible to vest in three equal installments on the first three anniversaries of our IPO.
Additionally, after the expiration of the post-IPO lock-up period, our named executive officers who were then employed by us became subject to additional transfer restrictions on all MIUs, as well as all FTW Class A Units and Class A common stock that they acquired prior to our IPO (or under awards originally granted prior to our IPO). Specifically, after our post-IPO lock-up expired on April 19, 2021, the named executive officers are limited to selling the sum of the following on a quarterly basis: (i) 5.0% of vested Class A common stock received in respect of vested equity awards (or upon exchange of vested MIUs or Class A Units as described above), (ii) 5.0% of the shares of Class A common stock the applicable executive is eligible to receive in respect of the named executive officer’s exchange of vested Class A Units, and (iii) the shares of Class A common stock the applicable named executive officer is eligible to receive in respect of the exchange of 5.0% of the number of vested MIUs subject to each of the applicable MIU grants to each such executive. Furthermore, on each date on which TPG sells any portion of its shares of Class A common stock, to the extent it would result in the ability to sell more shares of Class A common stock than the remaining amounts available for sale as described in the immediately preceding sentence, the applicable named executive officer will be permitted to sell a pro rata portion of such Class A common stock or Class A common stock the named executive officer could receive upon exchange of the named executive officer’s Class A Units or MIUs, in each case, based on the percentage of Class A common stock and Class A Units sold by TPG.
Post-IPO Long-Term Incentive Program
Under our post-IPO long-term incentive program, awards are provided in the form of time-based RSUs (which we generally refer to simply as “RSUs”) and performance-based RSUs (which we refer to as “PSUs”). For our President and Chief Executive Officer, long-term incentive awards are weighted 50% toward RSUs and 50% toward PSUs. For our Executive Vice Presidents, long-term incentive awards are weighted 60% toward RSUs and 40% toward PSUs. Under our current program, RSUs generally vest on a quarterly basis (with a one-year vesting cliff for any new hires) over a four-year period (generally starting with the beginning of the quarter in which the grant is made). PSUs will generally be eligible to vest based on performance over a three-year period. With respect to each grant of PSUs, it is anticipated that there will be three one-year performance measurement periods within that three-year performance period and that the Committee will determine, on an annual basis, the performance targets that apply with respect to the PSUs. The last PSU grants to our then-employed named executive officers were made in the fourth quarter of fiscal 2020 and, of those PSUs, one-third are eligible to vest based on achievement of performance targets for each of the relevant fiscal years within the three-year performance period and vest following the end of the three-year period.
From the beginning of fiscal 2021 through the end of Fiscal July, the metrics that applied to our PSUs linked to 2021 performance were Billings, Unlevered Free Cash Flow and EBITDA, with each performance metric weighted at 33.3%. In connection with the Enterprise Division Sale, the Committee adjusted the metrics that applied to our 2021 performance-linked PSUs. From August 1, 2021 through the end of fiscal 2021, the metrics that applied to these PSUs were EBITDA and Net Revenue, with each performance metric weighted at 50%. As with their use under the AIP, the Committee believes success against those metrics supports the Company’s growth imperatives and long-term equity appreciation, while balancing financial metrics to capture both top-line and bottom-line growth. Unlike under the AIP, where through the end of Fiscal July performance for certain named executive officers was aligned with only one of our primary business lines, performance under our post-IPO long-term incentive program is measured based on the performance of McAfee as a whole.
Treatment of Long-Term Incentive Awards in Connection with the Merger
Pursuant to the Merger Agreement and immediately prior to the effective time of the Merger, equity awards and rights held by our named executive officers will be treated as follows (which is consistent with how rights held by other employees are treated):
139
Following the execution of the Merger agreement, McAfee and the purchasing parties further agreed to provide a special vesting opportunity (the “Special Vesting Opportunity”) to certain employees and other service providers in connection with the closing of the transactions contemplated by the Merger agreement and generally subject to an applicable individual’s continued employment or other service to McAfee and its affiliates through the time that is immediately prior to the closing of the Merger. None of our named executive officers will benefit from the Special Vesting Opportunity because they hold equity awards that by their terms will exceed the benefit provided by the Special Vesting Opportunity.
Fiscal 2021 Long-Term Incentive Awards
The equity awards granted to our named executive officers during fiscal 2021 are summarized below:
Named Executive Officer |
|
RSUs |
|
|
PSUs |
|
||
Peter Leav (Distribution Adjustment Grants)(1) |
|
|
37,993 |
|
|
|
9,425 |
|
Venkat Bhamidipati (Distribution Adjustment Grants)(1) |
|
|
130,397 |
|
|
|
— |
|
Gagandeep Singh (Initial Hiring Grant)(2) |
|
|
1,143,118 |
|
|
|
— |
|
Lynne Doherty McDonald (Distribution Adjustment Grants)(1) |
|
|
— |
|
|
|
— |
|
Terry Hicks (Distribution Adjustment Grants)(1) |
|
|
66,842 |
|
|
|
13,030 |
|
Sign-On, Retention and Special Incentive Bonuses
140
The Committee may elect to award special bonuses as it deems appropriate for recruitment, retention, or incentive purposes. The Committee determines the level of the bonuses as well as the specific terms based on its review of the competitive market, including compensation offered by competing employers, as well as compensation to be forfeited by the executive upon joining the Company.
On December 31, 2020, during our 2021 fiscal year, Lynne Doherty McDonald received the third and final $500,000 installment of Lynne’s hiring bonus package that had totaled $1,500,000.
Employee Benefits
Employee health and wellbeing are of great importance to us, therefore ensuring our benefits remain highly competitive is a key focus for McAfee. We continuously review our benefit offerings with the goal of providing competitive benefits that have our employees and their unique family needs in mind. In addition to standard medical and retirement offerings, we offer on a global basis benefits like tuition reimbursement programs, domestic partner coverage and other family-friendly initiatives. We strive to maintain market competitive employee benefits to attract and retain top talent. Our named executive officers are eligible to participate in our broad-based employee benefit plans on the same terms as our other salaried U.S.-based employees, including our 401(k) plan and our health and welfare benefit plans.
We also provide a nonqualified deferred compensation plan, the McAfee Nonqualified Deferred Compensation Plan (the “NQDC Plan”). The NQDC Plan provides a vehicle for additional deferred compensation with discretionary matching contributions from the Company. No match under the NQDC Plan was provided in fiscal 2021. We believe that this type of plan is consistent with competitive pay practices and is an important element in attracting and retaining talent in a competitive market. Please see “—Nonqualified Deferred Compensation for Fiscal 2021” and accompanying narrative disclosure for further information regarding the NQDC Plan.
Perquisites and Executive Benefits
We offer limited perquisites and executive benefits to our named executive officers, including financial planning services and enhanced business travel benefits. While we generally weight executive compensation heavily toward total direct compensation (and particularly performance-based compensation), we believe the modest costs associated with these perquisites and benefits enhance executive retention.
Employment Arrangements
The Company generally executes an offer of employment before an executive joins the Company and, if applicable, will generally provide an updated offer of employment at the time of promotion. Those offers typically provide, among other things, the basic terms of the executive’s employment, including the executive’s start date, starting salary and bonus target. In more limited cases, we may enter into employment agreements with our most senior executives. The terms of the employment agreements, offer and promotion letters are based on competitive market data, including in some cases compensation that may be paid by a competing employer or forfeited upon separation from the executive’s prior employer.
Employment agreements, offer letters and other letter agreements with our named executive officers that were entered into in or prior to fiscal 2021 remained in effect during fiscal 2021, and are described further below.
Severance and Change in Control Arrangements
As described in further detail under “—Potential Payments Upon Termination or Change in Control for Fiscal 2021” below, we have entered into employment or letter agreements with certain of our named executive officers that provide for severance benefits in the event their employment is terminated in certain circumstances and provide certain change in control benefits. We believe that reasonable severance and change in control benefits are appropriate in certain circumstances to attract and retain top talent.
Equity Ownership Requirements
141
Each of our executive officers has a significant interest in our equity, whether held directly or as the result of outstanding equity-based awards. The Committee believes that equity ownership by senior management and non-employee directors aligns executive officer and shareholder interests and that, even after their equity is vested, members of senior management and non-employee directors should maintain a meaningful baseline equity stake in our business. In connection with our IPO, we adopted equity ownership requirements that apply to our named executive officers and non-employee directors (other than those associated with TPG and Intel).
Our minimum equity ownership requirements for our executive officers and non-employee directors require holdings of vested equity and equity-based awards with the following values:
Position |
|
Applicable Target |
Chief Executive Officer |
|
2.5x of target annual cash compensation |
Executive Vice Presidents |
|
1.5x of target annual cash compensation |
Employees at the level of Senior Vice President or above who have been designated by the Board |
|
1.0x of target annual cash compensation |
Non-employee director |
|
$500,000 |
The value of a share of our Class A common stock is determined based on the average calendar month-end closing price over the 12 calendar months of the calendar year immediately preceding the relevant measurement date. The value of an FTW unit is based on its implied value determined by applying the foregoing methodology to value a share of Class A common stock (where applicable to MIUs, less any unsatisfied return threshold). A stock option is valued at the value of the underlying shares of Class A common stock under the foregoing methodology less the applicable exercise price. Any shares that would be withheld or sold to pay any applicable withholding tax upon exercise of an option or delivery of shares will nonetheless be considered owned for purposes determining an executive officer’s ownership level.
Any executive officer or non-employee director who does not meet or exceed the foregoing requirements is subject to a 50% retention requirement that restricts the sale by such executive officer or non-employee directors’ equity. The retention requirements do not apply to equity that was vested prior to our IPO, or shares withheld or sold to satisfy tax or exercise price payment obligations. Each named executive officer is required to achieve the applicable level of ownership by the 5th anniversary of the date on which the named executive officer was first employed. A named executive officer who, due to a promotion, becomes subject to a higher level of ownership is required to achieve such higher level of ownership within 18 months after the date of such promotion. Each covered non-employee director is required to achieve the applicable level of ownership by the 4th anniversary of the date on which covered non-employee director was first appointed to the Board.
Once the requisite level has been achieved, ownership of the required amount must be maintained for as long as the individual remains subject to the minimum equity ownership requirements, except that an executive officer or non-employee director will not be considered out of compliance if the value of the individual’s equity declines between one measurement date and the next so long as the individual comes into compliance by the subsequent measuring date.
As noted above, in connection with our IPO, each of the named executive officers also agreed to certain extended transfer restrictions that apply to equity originally issued to them prior to our IPO.
Clawback Policy
We have adopted a clawback policy that permits us, subject to certain conditions, to recoup, cancel, and/or reduce performance-based awards in the event of a restatement of the Company’s financial results due to material noncompliance with financial reporting requirements, restatement of results, or other errors/omissions. Our clawback policy applies to our named executive officers who are currently employed by us.
Tax Considerations
142
Section 162(m) of the Internal Revenue Code of 1986, as amended (the “Code”) limits the deductibility of compensation paid to certain individuals to $1.0 million per year and may fully or partially limit deductions associated with compensation paid to our named executive officers. In certain cases, the Committee may consider the potential impact of Section 162(m) of the Code when structuring our executive compensation arrangements with our named executive officers. However, the Committee retains flexibility to approve compensation arrangements that promote the objectives of our compensation program, but which may not qualify for full or partial tax deductibility.
Compensation Committee Report
The Leadership Development and Compensation Committee has reviewed and discussed with management the foregoing Compensation Discussion and Analysis. Based on such review and discussions, the Leadership Development and Compensation Committee recommended to the Board that the Compensation Discussion and Analysis be included in this Form 10-K.
Leadership Development and Compensation Committee
Jon Winkelried, Chair
Sohaib Abbasi
Tim Millikin
Jeff Woolard
Summary Compensation Table for Fiscal 2021
The following table provides information regarding the compensation earned by our named executive officers for fiscal 2021, 2020 and 2019.
Name and principal position |
|
Year |
|
Salary |
|
Bonus |
|
|
Stock |
|
Non-equity |
|
Change in Pension Value and Earnings on Nonqualified Deferred Compensation(5) |
|
|
All Other |
|
Total |
||
Peter Leav |
|
2021 |
|
900,000 |
|
— |
|
|
5,144,616 |
|
3,002,400 |
|
— |
|
|
1,773 |
|
9,048,789 |
||
Venkat Bhamidipati |
|
2021 |
|
650,000 |
|
— |
|
|
— |
|
1,084,200 |
|
1,840 |
|
|
1,625 |
|
1,737,665 |
||
Gagandeep Singh |
|
2021 |
|
156,818 |
|
|
— |
|
|
23,857,587 |
|
360,904 |
|
|
— |
|
|
1,625 |
|
24,376,934 |
Lynne Doherty McDonald |
|
2021 |
|
495,833 |
|
755,200 |
|
|
— |
|
423,534 |
|
— |
|
|
12,161 |
|
1,686,728 |
||
Terry Hicks |
|
2021 |
|
508,807 |
|
— |
|
|
7,047,470 |
|
— |
|
736 |
|
|
264,285 |
|
7,821,298 |
||
143
144
Grants of Plan-Based Awards Table for Fiscal 2021
The following table provides information regarding the possible payouts to our named executive officers in fiscal 2021 under the AIP and Lynne Doherty McDonald’s special commission arrangement, as well as equity awards granted in fiscal 2021 to our named executive officers.
|
|
|
|
|
|
Estimated Possible Payouts |
|
|
Estimated Future Payouts |
|
|
|
|
|
|
|
||||||||||||||||
Name |
|
Committee |
|
Grant |
|
Threshold |
|
Target |
|
Maximum |
|
|
Threshold |
|
Target |
|
Maximum |
|
|
All Other Stock |
|
|
Grant Date |
|
||||||||
Peter Leav |
|
|
|
— |
|
— |
|
|
1,350,000 |
|
|
5,400,000 |
|
|
— |
|
— |
|
— |
|
|
— |
|
|
— |
|
||||||
|
|
12/15/2020 |
|
12/9/2021 |
|
|
|
|
|
|
|
|
|
339,147 |
|
|
484,496 |
|
|
629,845 |
|
|
— |
|
|
5,144,616(2) |
|
|||||
|
|
1/20/2021 |
|
1/20/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
— |
|
|
|
11,245 |
|
|
—(4) |
|
|||||||
|
|
1/20/2021 |
|
1/20/2021 |
|
— |
|
— |
|
— |
|
|
|
1,735 |
|
|
2,479 |
|
|
3,223 |
|
|
— |
|
|
—(4) |
|
|||||
|
|
4/9/2021 |
|
4/9/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
— |
|
|
|
9,736 |
|
|
—(4) |
|
|||||||
|
|
4/9/2021 |
|
4/9/2021 |
|
— |
|
— |
|
— |
|
|
|
1,623 |
|
|
2,318 |
|
|
3,013 |
|
|
— |
|
|
—(4) |
|
|||||
|
|
7/9/2021 |
|
7/9/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
— |
|
|
|
7,657 |
|
|
—(4) |
|
|||||||
|
|
7/9/2021 |
|
7/9/2021 |
|
— |
|
— |
|
— |
|
|
|
1,387 |
|
|
1,981 |
|
|
2,575 |
|
|
— |
|
|
—(4) |
|
|||||
|
|
10/8/2021 |
|
10/8/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
— |
|
|
|
9,355 |
|
|
—(4) |
|
|||||||
|
|
10/8/2021 |
|
10/8/2021 |
|
— |
|
— |
|
— |
|
|
|
1,854 |
|
|
2,649 |
|
|
3,444 |
|
|
— |
|
|
—(4) |
|
|||||
Venkat Bhamidipati |
|
|
|
— |
|
— |
|
|
650,000 |
|
|
2,600,000 |
|
|
— |
|
— |
|
— |
|
|
— |
|
|
— |
|
||||||
|
|
1/20/2021 |
|
1/20/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
— |
|
|
|
4,316 |
|
|
—(4) |
|
|||||||
|
|
4/9/2021 |
|
4/9/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
— |
|
|
|
3,765 |
|
|
—(4) |
|
|||||||
|
|
7/9/2021 |
|
7/9/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
— |
|
|
|
2,988 |
|
|
—(4) |
|
|||||||
|
|
8/27/2021 |
|
8/27/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
— |
|
|
|
115,021 |
|
|
—(4) |
|
|||||||
|
|
10/8/2021 |
|
10/8/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
— |
|
|
|
4,307 |
|
|
—(4) |
|
|||||||
Gagandeep Singh |
|
|
|
— |
|
— |
|
|
300,000 |
|
|
1,200,000 |
|
|
— |
|
— |
|
|
|
|
— |
|
|
— |
|
||||||
|
|
10/19/2021 |
|
10/19/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
|
|
|
1,143,118(3) |
|
|
|
23,857,587 |
|
|||||||
Lynne Doherty McDonald |
|
|
|
— |
|
— |
|
|
224,995 |
|
|
224,995 |
|
|
— |
|
— |
|
— |
|
|
— |
|
|
— |
|
||||||
|
|
|
|
— |
|
— |
|
675,070(5) |
|
— |
|
|
— |
|
— |
|
— |
|
|
— |
|
|
— |
|
||||||||
|
|
5/17/2021 |
|
5/17/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
— |
|
|
— |
|
|
—(6) |
|
||||||||
Terry Hicks |
|
|
|
— |
|
— |
|
|
778,883 |
|
|
3,115,530 |
|
|
— |
|
— |
|
— |
|
|
— |
|
|
— |
|
||||||
|
|
12/15/2020 |
|
3/26/2021 |
|
|
54,263 |
|
|
77,519 |
|
|
100,775 |
|
|
— |
|
— |
|
— |
|
|
— |
|
|
663,804(2) |
|
|||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
||||||||
|
|
8/27/2021 |
|
8/27/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
— |
|
|
|
66,842 |
|
|
—(4) |
|
|||||||
|
|
8/27/2021 |
|
8/27/2021 |
|
— |
|
— |
|
— |
|
|
|
9,121 |
|
|
13,030 |
|
|
16,939 |
|
|
— |
|
|
—(4) |
|
|||||
|
|
9/28/2021 |
|
10/6/2021 |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
— |
|
|
— |
|
|
6,383,666(7) |
|
||||||||
145
Narrative Disclosure to Summary Compensation Table and Grant of Plan-Based Awards Table
Employment Agreement with Peter Leav
In connection with Peter Leav’s commencement of employment as our President and Chief Executive Officer, Peter Leav entered into an employment agreement that became effective on February 3, 2020, and was subsequently amended on October 1, 2020 in connection with our IPO. Peter Leav’s amended employment agreement provides for an annual base salary of $900,000, a target bonus equal to 150% of annual base salary and an entitlement to participate in our employee benefit plans and programs made available to executive level employees. Pursuant to Peter Leav’s amended employment agreement, in fiscal 2020, Peter Leav was also granted 1,874,456 RSUs and 1,249,636 MIUs with an original return threshold of $8.64 per unit, and Peter Leav purchased 57,856 Class A Units.
In addition, any compensation paid to Peter Leav is subject to recoupment to the extent required by law, the limited liability company agreement of FTW, our equity plans, the award agreements governing the awards granted under our equity plans, Peter Leav’s subscription agreement, our clawback policy, or the requirements of the exchange on which the shares of an affiliate of ours are listed.
See “—Potential Payments Upon Termination or Change in Control for Fiscal 2021” for a description of the termination-related provisions under Peter Leav’s employment agreement.
Employment Agreement with Venkat Bhamidipati
In connection with Venkat Bhamidipati’s commencement of employment, Venkat Bhamidipati entered into an employment agreement, effective September 2, 2020, and was subsequently amended on September 30, 2020 in connection with our IPO, that provides for an annual base salary of $650,000, a target annual bonus equal to 100% of annual base salary and an entitlement to participate in our employee benefit plans and programs made available to executive level employees. Pursuant to Venkat Bhamidipati’s amended employment agreement, Venkat Bhamidipati was also granted 800,000 RSUs and 800,000 MIUs with an original return threshold of $8.64 per unit.
In addition, any compensation paid to Venkat Bhamidipati is subject to recoupment to the extent required by law, the limited liability company agreement of FTW, the 2017 Plan, the award agreements governing the awards granted under the 2017 Plan, Venkat Bhamidipati’s subscription agreement, our clawback policy, or the requirements of the exchange on which the shares of an affiliate of ours are listed.
146
See “—Potential Payments Upon Termination or Change in Control for Fiscal 2020” for a description of the termination-related provisions under Venkat Bhamidipati’s employment agreement.
Offer Letter with Gagandeep Singh
Gagandeep Singh is party to an offer letter with the Company providing for an annual base salary of $600,000 and an annual incentive bonus target equal to $600,000 per full fiscal year. Pursuant to Gagandeep Singh’s offer letter, Gagandeep Singh also was granted 1,143,118 RSUs in fiscal 2021.
See “—Potential Payments Upon Termination or Change in Control for Fiscal 2021” for a description of the termination-related provisions under Gagandeep Singh’s offer letter.
Offer Letter with Lynne Doherty McDonald
Prior to Lynne Doherty McDonald’s termination of employment in fiscal year 2021, Lynne was party to an offer letter with the Company providing for an annual base salary of $850,000 and an annual incentive bonus target equal to 105.9% of annual base salary. Pursuant to Lynne Doherty McDonald’s offer letter, Lynne Doherty McDonald also (i) was granted 500,000 RSUs and 2,435,504 MIUs with an original return threshold of $8.64 per unit in fiscal 2020, and (ii) received the hiring bonus described above under “Sign-On, Retention and Special Incentive Bonuses” in the “Compensation Discussion and Analysis”.
See “—Potential Payments Upon Termination or Change in Control for Fiscal 2020” for a description of the termination-related provisions under Lynne Doherty McDonald’s offer letter.
Letter Agreement with Terry Hicks
Prior to Terry Hicks’ termination of employment in fiscal year 2021, Terry was party to a letter agreement with the Company providing for an annual base salary of $650,000 and an annual incentive bonus target equal to 115.39% of annual base salary.
Outstanding Equity Awards at Fiscal Year-End for Fiscal 2021
The following table summarizes unvested stock awards held by each named executive officer on December 25, 2021.
|
|
|
|
Stock Awards |
||||||||
Name |
|
Grant |
|
Number of Shares |
|
Market Value of |
|
|
Equity Incentive |
|
Equity Incentive Plan Awards: |
|
Peter Leav |
|
2/3/2020 |
|
702,924(3) |
|
|
15,879,967 |
|
|
— |
|
— |
|
|
2/24/2020 |
|
1,051,122(4) |
|
|
27,045,369 |
|
|
— |
|
— |
|
|
10/20/2020 |
|
131,076(4) |
|
|
3,372,585 |
|
|
— |
|
— |
|
|
12/15/2020 |
|
362,530(4) |
|
|
9,327,897 |
|
|
339,147(5) |
|
8,726,252(5) |
|
|
1/20/2021 |
|
7,906(6) |
|
|
203,421 |
|
|
1,735(6) |
|
44,642(6) |
|
|
4/9/2021 |
|
7,407(6) |
|
|
190,582 |
|
|
1,623(6) |
|
41,760(6) |
|
|
7/9/2021 |
|
6,329(6) |
|
|
162,845 |
|
|
1,387(6) |
|
35,688(6) |
|
|
10/8/2021 |
|
8,468(6) |
|
|
217,882 |
|
|
1,854(6) |
|
47,703(6) |
Venkat Bhamidipati |
|
8/13/2020 |
|
550,000(3) |
|
|
12,532,850 |
|
|
— |
|
— |
|
|
8/13/2020 |
|
540,085(4) |
|
|
13,896,387 |
|
|
— |
|
— |
|
|
10/20/2020 |
|
67,346(4) |
|
|
1,732,813 |
|
|
— |
|
— |
|
|
1/20/2021 |
|
3,107(6) |
|
|
79,943 |
|
|
— |
|
— |
|
|
4/9/2021 |
|
2,954(6) |
|
|
76,006 |
|
|
— |
|
— |
|
|
7/9/2021 |
|
2,526(6) |
|
|
64,994 |
|
|
— |
|
— |
|
|
8/27/2021 |
|
105,434(6) |
|
|
2,712,817 |
|
|
— |
|
— |
|
|
10/8/2021 |
|
3,948(6) |
|
|
101,582 |
|
|
— |
|
— |
Gagandeep Singh |
|
10/19/2021 |
|
1,143,118 |
|
|
29,412,426 |
|
|
— |
|
— |
Lynne Doherty McDonald |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
Terry Hicks |
|
— |
|
— |
|
— |
|
|
— |
|
— |
|
147
Stock and Units Vested in Fiscal 2021
The following table summarizes the number and market value of equity awards held by each named executive officer that vested during fiscal 2021. No named executive officers held or exercised stock options during fiscal 2021.
|
|
Stock and Unit Awards |
|
|||||
Name |
|
Number of Shares |
|
|
Value Realized |
|
||
Peter Leav |
|
|
969,839 |
|
|
|
20,858,268 |
|
Venkat Bhamidipati |
|
|
437,306 |
|
|
|
9,204,239 |
|
Gagandeep Singh |
|
|
— |
|
|
|
— |
|
Lynne Doherty McDonald |
|
|
558,337 |
|
|
|
11,989,902 |
|
Terry Hicks |
|
|
610,647 |
|
|
|
12,293,773 |
|
Pension Benefits for Fiscal 2021
None of our named executive officers participated in or was entitled to receive benefits under a defined benefit pension plan in fiscal 2021.
148
Nonqualified Deferred Compensation for Fiscal 2021
The following table provides information regarding compensation that was deferred by our named executive officers pursuant to the terms of the NQDC Plan during fiscal 2021.
Name |
|
Executive |
|
|
Registrant |
|
|
Aggregate |
|
|
Aggregate |
|
|
Aggregate |
|
|||||
Peter Leav |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
Venkat Bhamidipati |
|
|
325,000 |
|
|
|
— |
|
|
|
18,966 |
|
|
|
— |
|
|
|
343,966 |
|
Gagandeep Singh |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
Lynne Doherty McDonald |
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
|
|
— |
|
Terry Hicks |
|
|
649,153 |
|
|
|
— |
|
|
|
37,914 |
|
|
|
136,686 |
|
|
|
550,381 |
|
During fiscal 2021, we maintained the NQDC Plan, for certain of our employees, and our named executive officers were eligible to participate. Under the NQDC Plan, participants may defer up to 50% of their compensation, as defined in the Company’s 401(k) plan, and incentive bonuses other than retention, relocation and sign-on bonuses. The NQDC also provides the Company with discretion to make matching and discretionary contributions into the NQDC Plan. Participants may specify the timing of the payment of their accounts by choosing either a specified payment date or electing payment upon separation from service, and in either case, may elect to receive their accounts in a lump sum or in annual installments over a period of up to ten years, with accelerated payouts in the event of death or disability of the participant. Participants are generally permitted to choose from among the mutual funds available for investment under the 401(k) plan for purposes of determining the imputed earnings, gains, and losses applicable to their NQDC Plan accounts
Potential Payments Upon Termination or Change in Control for Fiscal 2021
During fiscal 2021, certain of our named executive officers were entitled to receive certain benefits upon a qualifying termination of employment and upon certain change in control transactions, as described below.
Agreements with Executives
Employment Agreement with Peter Leav
Under the terms of Peter Leav’s amended employment agreement, if we terminate Peter Leav’s employment without cause (as defined in the amended employment agreement) or if Peter Leav resigns for good reason (as defined in the amended employment agreement), in either case, other than within two years following a change in control, Peter Leav would be entitled to: (i) one and one-half times the sum of then current annual base salary plus target bonus, payable over an 18-month period; (ii) any earned but unpaid annual bonus related to the completed fiscal year preceding the fiscal year in which termination of employment occurs, payable in accordance with regular payroll practices; (iii) an annual bonus for the year in which the termination date occurs, with payment based on actual performance during the year of termination, pro-rated to reflect the number of days during the bonus year in which Peter Leav was employed by us, payable in accordance with regular payroll practices; and (iv) provided that Peter Leav timely elects under the Consolidated Omnibus Budget Reconciliation Act (“COBRA”), a COBRA subsidy that, on an after-tax basis, is equal to the employer-paid portion of the premium equivalent for active employees who elect the same type of medical, dental and vision coverage during the 18-month period that follows Peter Leav’s termination of employment (or, if earlier, the time at which Peter Leav becomes eligible for group health coverage from another employer), payable on a monthly basis during such period. In the event such a termination of employment occurs during the two-year period following a change in control, Peter Leav would be entitled to the same payments (subject to the same requirements), except that the severance multiplier would be two (rather than one and one-half) and would be paid over a 24-month period (instead of an 18-month period), and the COBRA subsidy would be paid for up to 24 months (instead of 18 months). In addition, in each case, Peter Leav would also be entitled to: (i) any earned but unpaid base salary accrued through the date of termination; (ii) unreimbursed business expenses; and (iii) employee benefits, if any, to which Peter Leav or Peter Leav’s dependents may be entitled under the employee benefit plans or programs of the Company (“Peter Leav’s Accrued Rights”).
Upon a termination of employment due to Peter Leav’s death or disability, Peter Leav would be entitled to: (i) Peter Leav’s Accrued Rights; (ii) any earned but unpaid annual bonus related to the completed fiscal year preceding the fiscal year in which termination of employment occurs, payable in accordance with regular payroll practices; and (iii) an annual bonus for the year in which the termination date occurs, with payment based on actual performance during the year of termination, pro-rated to reflect the number of days during the bonus year in which Peter Leav was employed by the us, payable in accordance with regular payroll practices.
Upon a resignation without good reason or a termination for cause, Peter Leav would be entitled only to Peter Leav’s Accrued Rights.
149
Peter Leav’s receipt of the severance payments described above (other than Peter Leav’s Accrued Rights) are subject to Peter Leav’s signing (and not revoking) a release of all claims against us and Peter Leav’s continuing to comply with the limited liability company agreement of FTW, the 2017 Plan, the award agreements governing the awards granted under the 2017 Plan, Peter Leav’s subscription agreement, and Peter Leav’s amended employment agreement, the latter of which includes a covenant not to compete with us or to solicit our customers or employees during and, subject to certain limitations, for 18 months following Peter Leav’s employment with us, as well as a perpetual confidentiality covenant.
Peter Leav’s Long-Term Incentive Awards
Peter Leav’s MIU, RSU and PSU award agreements each provide that in the event of a change in control (as defined in the 2017 Plan or the McAfee 2020 Omnibus Incentive Plan (the “2020 Plan”), as applicable), Peter Leav’s awards will accelerate in full (and, in the case of Peter Leav’s PSUs, will be deemed earned based on target performance or, if higher and if determinable, based on the actual performance of the Company and/or FTW, as applicable, through the date of the change in control (or an earlier date selected for administrative convenience)) as of immediately prior to the change in control, provided that Peter Leav remains employed through the date of the change in control. We expect that Peter Leav’s MIUs, RSUs and PSUs will accelerate in full immediately prior to the Merger (and, in the case of Peter Leav’s PSUs, will be deemed earned on actual performance of the Company) in respect of PSUs with an annual performance period related to fiscal 2021 and target performance with respect to PSUs with an annual performance period rated to fiscal 2022 or fiscal 2023
Peter Leav’s MIU, RSU and PSU award agreements each also provide that if Peter Leav’s employment or other service is terminated without cause (but not due to death or disability) or Peter Leav resigns for good reason, in either case, other than under circumstances where cause exists and within 24 months following a sale of the Company’s Consumer business unit or Enterprise business unit (either, as applicable, the “Divested Business”) that does not constitute a change in control, then, subject to Peter Leav’s continued material compliance with Peter Leav’s amended employment agreement, the award agreement, the applicable long-term incentive plan and the second amended and restated limited liability company agreement of FTW, and Peter Leav’s execution, delivery and non-revocation of a general release of claims within a specified period, a portion of the then unvested and outstanding award will vest as of immediately prior to such termination, with the portion determined by multiplying the number of then unvested and outstanding MIUs, RSUs or PSUs (or, in each case, any securities or rights for which such MIUs, RSUs or PSUs were previously exchanged) by a ratio of A /(A+B), where “A” is the actual distributed proceeds (i.e., cash and marketable securities) resulting from the sale of the Divested Business, plus any excess cash retained by the Company after appropriate debt pay down, and “B” is the aggregate fair market of the equity of FTW immediately following the sale of the Divested Business (without any duplication of any amount included in “A”).
Employment Agreement with Venkat Bhamidipati
Under the terms of Venkat Bhamidipati’s amended employment agreement, if we terminate Venkat Bhamidipati’s employment without cause (as defined in Venkat Bhamidipati’s amended employment agreement) or if Venkat Bhamidipati resigns for good reason (as defined in Venkat Bhamidipati’s amended employment agreement), Venkat Bhamidipati would be entitled to: (i) a sum equal to then current annual base salary plus target annual bonus, payable over a 12-month period and (ii) provided that Venkat Bhamidipati timely elects COBRA, monthly COBRA enrollment premiums that are equal to the employer-paid portion for active employees who elect the same type of medical, dental and vision coverage during the 12-month period that follows Venkat Bhamidipati’s termination of employment (or, if earlier, the time at which Venkat Bhamidipati becomes eligible for group health coverage from another employer), payable directly to our COBRA provider. In addition, if we terminate Venkat Bhamidipati’s employment without cause, Venkat Bhamidipati would be entitled to any earned but unpaid annual bonus related to (i) the fiscal year in which the termination date occurs if Venkat Bhamidipati was employed through the end of the third quarter of such fiscal year, or (ii) the completed fiscal year preceding the fiscal year in which termination of employment occurs, in each case based on actual performance for the applicable fiscal year and payable in accordance with regular payroll practices. In each case, Venkat Bhamidipati would also be entitled to: (i) any earned but unpaid base salary accrued through the date of termination; (ii) unreimbursed business expenses; (iii) any earned and unused vacation; and (iv) employee benefits, if any, to which Venkat Bhamidipati, Venkat Bhamidipati’s estate, or Venkat Bhamidipati’s dependents may be entitled under the employee benefit plans or programs of the Company (“Venkat Bhamidipati’s Accrued Rights”).
Upon a termination of employment due to Venkat Bhamidipati’s death or disability, a resignation without good reason, or a termination for cause, Venkat Bhamidipati would be entitled only to Venkat Bhamidipati’s Accrued Rights.
Venkat Bhamidipati’s receipt of the severance payments described above (other than Venkat Bhamidipati’s Accrued Rights) are subject to Venkat Bhamidipati’s signing (and not revoking) a release of all claims against us and that Venkat Bhamidipati continue to comply with the limited liability company agreement of FTW, the 2017 Plan, the award agreements governing the awards granted under the 2017 Plan, and the amended employment agreement, the latter of which includes a covenant not to compete with us or to solicit our customers or employees during and, subject to certain limitations, for 12 months following Venkat Bhamidipati’s employment with us, as well as a perpetual confidentiality covenant.
Venkat Bhamidipati’s Long Term Incentive Awards
150
Venkat Bhamidipati’s MIU and RSU award agreements each provide that in the event of a change in control (as defined in the 2017 Plan or the 2020 Plan, as applicable), Venkat Bhamidipati’s awards will accelerate in full as of immediately prior to the change in control, provided that Venkat Bhamidipati remains employed through the date of the change in control. We expect that Venkat Bhamidipati’s MIUs, and RSUs will accelerate in full immediately prior to the Merger.
If Venkat Bhamidipati’s employment or other service is terminated without cause (but not due to death or disability) or Venkat Bhamidipati resigns for good reason, in either case, other than under circumstances where cause exists, then, subject to Venkat Bhamidipati’s continued material compliance with Venkat Bhamidipati’s amended employment agreement, Venkat Bhamidipati’s MIU and RSU award agreement, the 2017 Plan and the second amended and restated limited liability company agreement of FTW and Venkat Bhamidipati’s execution, delivery and non-revocation of a general release of claims within a specified period, if such termination occurs prior to September 2, 2021, the portion of the applicable award that was otherwise scheduled to vest during the one year period following such termination would immediately vest.
Executive Severance Arrangements
In connection with our IPO, we entered into severance agreements (the “Severance Agreements”) with our current executive officers (other than Peter Leav) who were employed by the Company at the time of the IPO. We entered into a Severance Agreement with Gagandeep Singh in connection with the commencement of Gagandeep’s employment with the Company. Under the terms of the Severance Agreements, each eligible senior management team member (each a “Covered Executive”) is eligible to receive severance in the event the Covered Executive’s employment is terminated by the Company without cause (as defined in the Severance Agreement) or terminates the Covered Executive’s employment with the Company for good reason (as defined in the Severance Agreement), in either case, at a time other than during the period beginning three months prior to, and ending 18 months following, the consummation of a change in control, in an amount equal to the sum of (i) an amount equal to 1.0x the Covered Executive’s base salary and target annual bonus as in effect on the date of the Covered Executive’s termination (or, if higher, the base salary and target annual bonus in effect immediately before any reduction in such amounts which resulted in good reason), payable in substantially equal installments over a period of 12 months after the Covered Executive’s termination of employment in accordance with the Company’s regular payroll practices, and (ii) if the Covered Executive elects continuation coverage under our health plan, a monthly amount equal to the employer portion of the monthly premiums paid under our group health plans (as of the date of the Covered Executive’s termination of employment) for up to 12 months.
Under the Severance Agreements, in the event a Covered Executive’s employment is terminated without cause (as defined in the Severance Agreement), or the Covered Executive terminates the Covered Executive’s employment with the Company for good reason (as defined in the Severance Agreement), in either case, during the period beginning three months prior to, and ending 18 months following, the consummation of a change in control (“Qualifying Change in Control Termination”), the Covered Executive will be eligible to receive severance in an amount equal to the sum of (i) 1.5x the sum of the Covered Executive’s base salary and target annual bonus (in each case at the highest level in effect during the 12-month period leading up to the date of the Covered Executive’s termination of employment), payable in a lump sum, (ii) the pro rata portion of the Covered Executive’s annual bonus, based on actual performance for the year in which termination occurs, payable at the time at the time annual bonuses are payable to senior executives of the Company and its affiliates generally, and (iii) if the Covered Executive elects continuation coverage under our health plan, a monthly amount equal to the employer portion of the monthly premiums paid under our group health plans (as of the date of the Covered Executive’s termination of employment) for up to 18 months. Furthermore, in the event of a Qualifying Change in Control Termination, all the Covered Executive’s unvested time-based equity will accelerate and vest in full as of the date of the Covered Executive’s termination of employment and all performance-based equity granted following our IPO would vest as of the separation date based on target performance or, if higher and if determinable, based on our actual performance through the date of termination of employment, as applicable, in accordance with the documents governing such performance-based equity award.
The payments provided under the Severance Agreement are in lieu of and will supersede any severance or similar payments or benefits that the Covered Executive may otherwise be entitled to upon termination of the Covered Executive’s employment, but, other than in the case of Gagandeep Singh’s Severance Agreement, if payments or benefits become payable under the Severance Agreement and if the severance payments and benefits provided under the Covered Executive’s employment agreement, offer letter, or prior severance agreement (the “Prior Agreement”) remained payable, to the extent such payments and benefits would be greater than the payments and benefits payable under the Severance Agreement (the “Excess Payments”), the Excess Payments will, subject to terms and conditions of the Severance Agreement, be payable under the Severance Agreement but in accordance with the payment schedule that would have applied to them under the Prior Agreement.
All severance payable under the Severance Agreement is contingent upon the Covered Executive’s compliance with the restrictive covenants related to non-competition, non-solicitation and no-hire and material compliance with other restrictive covenants that apply to the Covered Executive, and the Covered Executive’s execution and non-revocation of a general release of claims.
In addition, each Covered Executive’s Severance Agreement provides that in the event the Covered Executive’s then unvested time-based equity awards are not continued, assumed or substituted for in connection with a change in control with awards or rights having the same intrinsic value (determined as of the change in control), such time-based equity awards will vest in full effective as of the change in control.
151
Long-Term Incentive Award Agreement for Gagandeep Singh
As of the end of fiscal 2021, Gagandeep Singh held unvested RSUs that were subject to time-based vesting conditions that were issued under the 2020 Plan. Under the terms of Gagandeep’s RSU agreement and offer letter, 25% of Gagandeep’s RSUs will accelerate if (i) a change in control occurs (as defined in Gagandeep’s Severance Agreement) within 12 months following Gagandeep’s date of hire and Gagandeep remains employed by the Company as of the date of the change in control, or (ii) if Gagandeep resigns employment from the Company for Good Reason (as defined in Gagandeep’s Severance Agreement) within 12 months following his date of hire. Those RSUs are anticipated to vest in connection with the Merger. The remaining RSUs held by Gagandeep will be converted to Cash Awards, which will remain subject to the same time-vesting terms and conditions that apply to them immediately prior to the Merger, and those Cash Awards will be paid out on the next payroll date following the applicable vesting date, so long as the applicable portion becomes vested prior to Gagandeep’s termination of employment (taking into account the terms of Gagandeep’s Severance Agreement).
Separation Agreement with Terry Hicks
Terry Hicks’ separation agreement, which was effective as of October 1, 2021, provided that in exchange for a release of claims (that was not revoked) and Terry’s agreement to adhere to certain restrictive covenants, Terry Hicks was entitled to receive (i) severance pay in the amount of $1,500,053, payable over the 12-month period following Terry Hicks’ termination of employment, (ii) provided that Terry Hicks timely elects COBRA, for the period ending on the earlier of (A) 12 months after Terry’s termination of employment with us and (B) the date on which Terry becomes eligible to be covered under another employer’s health plan, a COBRA subsidy paid directly to the Company’s COBRA provider on Terry Hicks’ behalf equal to a monthly amount of $779.42, (iii) continued eligibility to vest in Terry’s RSUs and MIUs that were regularly scheduled to vest on September 30, 2021 and October 21, 2021, and (iv) continued provision of Ayco financial services for three months following October 1, 2021.
The amounts that would have been payable by us to each of the named executive officers under their agreements with us that were then in effect, assuming that each individual’s employment had terminated on December 24, 2021, the last business day of fiscal 2021, are set forth below:
Potential Payments Upon a Qualifying Termination of Employment(1)
Name |
|
Severance |
|
|
Prorated Annual |
|
|
Value of |
|
|
Welfare |
|
|
Aggregate |
|
|||||
Peter Leav |
|
|
3,375,000 |
|
|
|
3,002,400 |
|
|
|
— |
|
|
|
47,878 |
|
|
|
6,425,278 |
|
Venkat Bhamidipati |
|
|
1,300,000 |
|
|
|
1,084,200 |
|
|
|
— |
|
|
|
15,813 |
|
|
|
2,400,013 |
|
Gagandeep Singh |
|
|
900,000 |
|
|
|
360,904 |
|
|
|
— |
|
|
|
29,199 |
|
|
|
1,290,103 |
|
152
Potential Payments Upon a Change in Control or a Qualifying Termination of Employment in Connection with a Change in Control(1)
The amounts that would have been payable by us to each of the named executive officers, assuming that each individual’s employment had terminated and/or a change in control of the Company had occurred on the last business day of our 2021 fiscal year, are as set forth below. Except where noted below that the payment would have been made regardless of a termination of employment, these amounts are payable in connection with a qualifying termination of employment and would be in addition to the amounts in the table directly above.
Name |
|
Severance |
|
|
Prorated Annual |
|
|
Value of |
|
|
Welfare |
|
|
Aggregate |
|
|||||
Peter Leav |
|
|
4,500,000 |
|
|
|
3,002,400 |
|
|
|
69,109,187 |
|
|
|
63,837 |
|
|
|
76,675,424 |
|
Venkat Bhamidipati |
|
|
1,950,000 |
|
|
|
1,084,200 |
|
|
|
31,197,392 |
|
|
|
23,720 |
|
|
|
34,255,312 |
|
Gagandeep Singh |
|
|
1,350,000 |
|
|
|
360,904 |
|
|
|
29,412,426 |
|
|
|
43,798 |
|
|
|
31,167,128 |
|
153
Equity Compensation Plan Information
The following table summarizes the following information as of December 25, 2021:
Plan category |
|
Number of securities to be issued upon exercise of outstanding options, warrants and rights |
|
|
Weighted-average exercise price of outstanding options, warrants and rights |
|
|
Number of securities remaining available for future issuance under equity compensation plans (excluding securities reflected in column (a)) |
|
|||
Equity compensation plans approved by security holders |
|
|
14,710,979 |
|
|
$ |
14.66 |
|
|
|
53,861,290 |
|
Equity compensation plans not approved by security holders |
|
|
— |
|
|
|
— |
|
|
|
— |
|
Total |
|
|
14,710,979 |
|
|
|
|
|
|
53,861,290 |
|
|
CEO Pay Ratio
We are required under SEC rules to provide a pay ratio comparing our Chief Executive Officer’s fiscal 2021 compensation to our median employee’s fiscal 2021 compensation (excluding our Chief Executive Officer). To identify the median employee, we conducted a review and analysis of 2,156 full-time and part-time employees and interns as of December 7, 2021 (the “Determination Date”), which represented all of our employees on the Determination Date (other than those in the countries identified below). We did not employ any seasonal or temporary employees on the Determination Date. We identified the median employee based on comparisons of actual base salary or base wages paid during the period from January 1, 2021 through September 30, 2021 (the “Measurement Period”). As permitted under SEC rules, we annualized the base salary or base wages paid to full-time employees who did not work the entire Measurement Period. As required by SEC rules, except as described below, all of our part-time employees as of the Determination Date were taken into account for purposes of identifying our median employee under SEC rules, without annualizing the compensation paid to these workers as if they were full-time employees. We did not implement a cost-of-living adjustment to account for the economic differences in countries outside of the United States. For our non-US employees, we applied a conversion rate as of the last day of the Measurement Period. As also permitted under SEC rules, we adjusted our total employee population for purposes of identifying our median employee by excluding approximately 4.98% of our employee population (113 in total) as follows (all amounts are approximate): 2 in Turkey; 63 in Columbia; 2 in Peru; 20 in Argentina; 5 in Indonesia; 14 in Mexico; and 7 in Thailand.
We have estimated that our pay ratio for 2021 is 53 to 1, calculated by dividing our Chief Executive Officer’s fiscal 2021 total compensation set forth in the Summary Compensation Table, by the annual total compensation of our median employee. Our median employee’s annual total compensation was determined using the same methodology we used to determine the annual total compensation of our named executive officers.
Director Compensation for Fiscal 2021
The following table shows information regarding the compensation earned by or paid to our non-employee directors during our fiscal 2021.
154
Name |
|
Fees Earned |
|
|
Stock |
|
|
Total |
|
|||
Sohaib Abbasi |
|
|
90,443 |
|
|
|
224,975 |
|
|
|
315,418 |
|
Gunther Bright(4) |
|
|
23,718 |
|
|
|
161,499 |
|
|
|
185,217 |
|
Mary Cranston |
|
|
116,413 |
|
|
|
224,975 |
|
|
|
341,388 |
|
Tim Millikin |
|
|
— |
|
|
|
— |
|
|
|
— |
|
Emily Rollins(4) |
|
|
18,814 |
|
|
|
148,565 |
|
|
|
167,379 |
|
Kathy Willard |
|
|
94,239 |
|
|
|
224,975 |
|
|
|
319,214 |
|
Jon Winkelried |
|
|
— |
|
|
|
— |
|
|
|
— |
|
Jeff Woolard |
|
|
— |
|
|
|
— |
|
|
|
— |
|
Director Compensation Program
In connection with our IPO, the Board adopted a new non-employee director compensation policy for non-employee directors who are not employed by TPG, Intel or Thoma Bravo. Individuals that are covered under the program are referred to as “covered directors” and individuals who are excluded are referred to as “excluded directors.” Excluded directors are not eligible to receive any compensation in respect of their service on the Board.
Under this program, each covered director receives an annual cash retainer for service to the Board and an additional annual cash retainer for service on any committee of the Board or for serving as the chair of the Board or any of its committees, in each case, pro-rated for partial years of service, as follows:
|
|
Board or |
|
|
Board or |
|
||
Annual cash retainer |
|
$ |
75,000 |
|
|
$ |
— |
|
Additional annual cash retainer for Leadership Development and Compensation Committee |
|
$ |
7,500 |
|
|
$ |
20,000 |
|
Additional annual cash retainer for Nominating and Governance Committee |
|
$ |
5,000 |
|
|
$ |
15,000 |
|
Additional annual cash retainer for Audit Committee |
|
$ |
10,000 |
|
|
$ |
25,000 |
|
All cash fees are payable in arrears on a quarterly basis (or, if earlier, within 30 days following the earlier resignation or removal of the covered director). Each covered director may elect to receive vested shares of Class A common stock in lieu of all or a portion of the covered director’s annual cash fees payable under our non-employee director compensation policy.
155
Commencing in calendar year 2021, on the first trading day following each annual meeting of our stockholders, each covered director will be granted RSUs having a fair market value of $225,000. The RSUs will vest on the earliest of the following to occur: (i) the first anniversary of the date the RSUs were granted, (ii) the covered director’s death or permanent disability, or (iii) a change in control (as defined in the 2020 Plan), subject, in each case, to the non-employee director’s continued service as a member of the Board through the applicable vesting date. However, if our next annual meeting of stockholders that follows the grant date is less than one year after the prior annual meeting of our stockholders, and the covered director continues to serve on the Board through immediately prior to such meeting, but does not stand for re-election, is not elected or is not nominated for re-election at such meeting, any then unvested RSUs granted in the immediately preceding 12 months will accelerate and vest in full as of the immediately prior to such meeting.
All cash fees are prorated for any fiscal quarter of partial service, based on the number of calendar days the covered director was a member of the Board or the applicable committee, in a manner determined by the Board or the Committee. Covered directors may also receive prorated equity awards if they are appointed or elected to the Board other than at the Company’s annual meeting of stockholders.
The aggregate value of cash compensation and the grant date fair value of shares of capital stock of the Company that may be paid or granted during any fiscal year of the Company will not exceed the amount prescribed in the 2020 Plan (or any successor plan).
Equity Ownership Requirements
As described further above under “Equity Ownership Requirements” in the “Compensation Discussion and Analysis” section, we have an equity ownership requirements that apply to covered directors.
Item 12. Security Ownership of Certain Beneficial Owners and Management and Related Stockholder Matters.
The following table sets forth information, as of the December 25, 2021, regarding ownership of our common stock by:
The amounts for our NEOs and executive officers and directors as a group and our significant stockholders are as of the December 25, 2021 unless otherwise indicated in a footnote below (and in that case are based upon SEC filings made on behalf of such owners). Beneficial ownership in this table is determined in accordance with the rules of the SEC, and does not necessarily indicate beneficial ownership for any other purpose. Under these rules, the number of shares of Company Stock deemed outstanding includes those shares issuable upon exercise of options held by the respective person or group that may be exercised within 60 days after the December 25, 2021. For purposes of calculating each person’s or group’s percentage ownership, unvested stock options exercisable within 60 days and all shares of restricted stock are included for that person or group, but not for any other person or group. Percentage of beneficial ownership is based on the shares of common stock outstanding as of the December 25, 2021. Beneficial ownership representing less than 1% is denoted with an asterisk (*).
Pursuant to the terms of the stockholders agreement entered into by the Company and certain of our stockholders in connection with our IPO (the “Stockholders Agreement”), the TPG Funds (as defined below) have the right to appoint a majority of the directors serving on the Board. As a result, the TPG Funds may be deemed to control the Company’s exercise of its option to settle exchanges of Class A Units into shares of Class A Common Stock or cash with respect to any such exchange by the TPG Funds. As a result of this control, the TPG Funds beneficially own all shares of Class A common stock underlying its Class A Units. Other than with respect to the TPG Funds, the beneficial ownership of Class A Common Stock in the table below does not take into account the potential redemption and exchange of a stockholder’s Class A Units for Class A Common Stock and the corresponding cancellation of an equivalent number of shares of Class B Common Stock. The TPG Funds’ beneficial ownership of Class A Common Stock in the table below aggregates both its direct ownership of Class A Common Stock and the number of shares of Class A Common Stock into which its Class A Units could be converted. If this were to actually occur, all of the TPG Funds’ Class B Common Stock would be cancelled and its beneficial ownership percentage of the Class B Common Stock would be 0%.
156
|
|
Class A common stock |
|
|
Class B common stock |
|
||||||||||
|
|
Number |
|
|
Percentage |
|
|
Number |
|
|
Percentage |
|
||||
Name of beneficial owner |
|
|
|
|
|
|
|
|
|
|
|
|
||||
5% Stockholders |
|
|
|
|
|
|
|
|
|
|
|
|
||||
Intel Americas, Inc.(3) |
|
|
5,696,831 |
|
|
|
3.1 |
% |
|
|
169,742,322 |
|
|
|
67.0 |
% |
TPG Funds(4) |
|
|
117,501,906 |
|
|
|
48.2 |
% |
|
|
57,607,138 |
|
|
|
22.8 |
% |
Thoma Bravo Funds(5) |
|
|
16,611,135 |
|
|
|
8.9 |
% |
|
|
24,075,115 |
|
|
|
9.5 |
% |
Snowlake Investment Pte Ltd.(6) |
|
|
24,411,754 |
|
|
|
13.1 |
% |
|
|
— |
|
|
* |
|
|
Directors and Named Executive Officers |
|
|
|
|
|
|
|
|
|
|
|
|
||||
Peter Leav(7) |
|
|
923,526 |
|
|
* |
|
|
|
252,464 |
|
|
* |
|
||
Venkat Bhamidipati(8) |
|
|
456,999 |
|
|
* |
|
|
|
37,444 |
|
|
* |
|
||
Gagandeep Singh |
|
|
— |
|
|
* |
|
|
|
— |
|
|
* |
|
||
Sohaib Abbasi |
|
|
78,947 |
|
|
* |
|
|
|
— |
|
|
* |
|
||
Mary Cranston |
|
|
59,356 |
|
|
* |
|
|
|
— |
|
|
* |
|
||
Tim Millikin(9) |
|
|
— |
|
|
* |
|
|
|
— |
|
|
* |
|
||
Kathy Willard |
|
|
35,892 |
|
|
* |
|
|
|
— |
|
|
* |
|
||
Jon Winkelried |
|
|
— |
|
|
* |
|
|
|
— |
|
|
* |
|
||
Jeff Woolard |
|
|
— |
|
|
* |
|
|
|
— |
|
|
* |
|
||
Gunther Bright |
|
|
— |
|
|
* |
|
|
|
— |
|
|
* |
|
||
Emily Rollins |
|
|
— |
|
|
* |
|
|
|
— |
|
|
* |
|
||
All directors and executive officers as a group (12 people)(10) |
|
|
1,643,568 |
|
|
* |
|
|
|
289,908 |
|
|
* |
|
||
* Represents beneficial ownership of less than 1%.
157
Equity compensation plan information
The following table provides information about our common stock that may be issued upon the exercise of options, warrants and rights under the McAfee 2020 Omnibus Incentive Plan, McAfee Corp. 2020 Employee Stock Purchase Plan, and McAfee 2017 Management Incentive Plan, which are our equity compensation plans as of December 25, 2021. A description of the material terms of such plan are set forth in Note 12 (Equity-based compensation) of to our consolidated financial statements included elsewhere in this Annual Report on Form 10-K.
Plan category |
|
Number of securities to be issued upon exercise of outstanding options, warrants and rights |
|
|
Weighted-average exercise price of outstanding options, warrants and rights |
|
|
Number of securities remaining available for future issuance under equity compensation plans |
|
|||
Equity compensation plans approved by security holders: |
|
|
|
|
|
|
|
|
|
|||
2020 Omnibus Incentive Plan |
|
|
644,291 |
|
|
$ |
14.66 |
|
|
|
53,861,290 |
|
2020 Employee Stock Purchase Plan |
|
|
— |
|
|
|
— |
|
|
|
9,389,809 |
|
Total |
|
|
644,291 |
|
|
$ |
14.66 |
|
|
|
63,251,099 |
|
158
Item 13. Certain Relationships and Related Transactions, and Director Independence.
In addition to the compensation arrangements discussed in the section titled “Executive compensation” of this Annual Report on Form 10-K, the following is a description of each transaction since December 27, 2020 and each currently proposed transaction in which:
Recapitalization Transactions in Connection with our IPO
These summaries do not purport to be complete descriptions of all of the provisions of the documents relating to the recapitalization transactions, and they are qualified in their entirety by reference to the complete text of agreements which have been filed with the SEC. For information on how to obtain copies of these agreements or other exhibits, see the section entitled “Item 1, Business-Available information.”
Tax Receivable Agreement
The contribution by the certain of our pre-IPO equityholders to McAfee Corp. of the equity of certain corporate entities in connection with our IPO and future exchanges of Class A Units for cash or, at our option, shares of our Class A common stock are expected to produce or otherwise deliver to us favorable tax attributes that can reduce our taxable income. Upon the completion of our IPO, we are a party to a tax receivable agreement, under which we generally are required to pay certain of our pre-IPO equityholders 85% of the applicable cash savings, if any, in U.S. federal, state, and local income tax that we actually realize or, in certain circumstances, are deemed to realize as a result of (i) all or a portion of McAfee Corp.’s allocable share of existing tax basis in the assets of Foundation Technology Worldwide LLC (and its subsidiaries) acquired in connection with the Reorganization Transactions, (ii) increases in McAfee Corp.’s allocable share of existing tax basis in the assets of Foundation Technology Worldwide LLC (and its subsidiaries) and tax basis adjustments in the assets of Foundation Technology Worldwide LLC (and its subsidiaries) as a result of sales or exchanges of Class A Units after our IPO, (iii) certain tax attributes of the corporations McAfee Corp. acquired in connection with the reorganization transactions effected in connection with our IPO (including their allocable share of existing tax basis in the assets of Foundation Technology Worldwide LLC (and its subsidiaries)), and (iv) certain other tax benefits related to entering into the tax receivable agreement, including tax benefits attributable to payments under the tax receivable agreement. We generally will retain the benefit of the remaining 15% of the applicable tax savings.
Pursuant to the exchange mechanics, from time to time we may be required to acquire Class A Units of Foundation Technology Worldwide LLC from the holders thereof in exchange for cash or, at our option, shares of our Class A common stock. An exchange of Class A Units is intended to be treated as a purchase of such Class A Units for U.S. federal income tax purposes. Each of Foundation Technology Worldwide LLC and McAfee Finance 2, LLC, a subsidiary of Foundation Technology Worldwide LLC intended to be treated as a partnership for U.S. federal income tax purposes and through which Foundation Technology Worldwide LLC owns its interests in the assets of the McAfee business, intends to have an election under Section 754 of the Internal Revenue Code of 1986, as amended, in effect for taxable years in which such sales or exchanges of Class A Units occur. Pursuant to the Section 754 election, sales of Class A Units are expected to result in an increase in the tax basis of tangible and intangible assets of Foundation Technology Worldwide LLC and certain of its subsidiaries, including McAfee Finance 2, LLC. When we acquire Class A Units from the holders thereof, we expect that both the existing basis for certain assets and the anticipated basis adjustments will increase depreciation and amortization deductions allocable to us for tax purposes from Foundation Technology Worldwide LLC, and therefore reduce the amount of income tax we would otherwise be required to pay in the future to various tax authorities. This increase in tax basis may also decrease gain (or increase loss) on future dispositions of certain assets of Foundation Technology Worldwide LLC and its subsidiaries to the extent increased tax basis is allocated to those assets.
Stockholders Agreement
In connection with our IPO, we entered into a stockholders agreement with the Sponsors, Intel, and certain other stockholders. Pursuant to the stockholders agreement, we are required to take all necessary action to cause the Board and its committees to include director candidates designated by TPG and Intel in the slate of director nominees recommended by the Board for election by our stockholders. The stockholders agreement also provides that we will obtain customary director indemnity insurance. Pursuant to the stockholders agreement, each of our Sponsors and Intel also agreed to certain standstill provisions pursuant to which it is restricted from, among other things, acquiring our securities if that would result in it owning more than 49% of our outstanding voting power without our consent.
Registration Rights Agreement
We entered into a registration rights agreement with our Sponsors, Intel, certain other stockholders, and our Chief Executive Officer in connection with our IPO. The registration rights agreement provides the stockholders party thereto certain registration rights as described below.
159
Demand Registration Rights
Each of our Sponsors and Intel has the right to demand that we file registration statements. These registration rights are subject to specified conditions and limitations, including the right of the underwriters, if any, to limit the number of shares included in any such registration under specified circumstances. Upon such a request, we are required to use reasonable best efforts to promptly effect the registration.
Piggyback Registration Rights
If we propose to register any shares of our equity securities under the Securities Act of 1933, as amended (the “Securities Act”), either for our own account or for the account of any other person, the parties to the registration rights agreement will be entitled to notice of the registration and will be entitled to include their shares of Class A common stock in the registration statement. These piggyback registration rights are subject to specified conditions and limitations, including the right of the underwriters, if any, to limit the number of shares included in any such registration under specified circumstances.
Shelf Registration Rights
At any time after we become eligible to file a registration statement on Form S-3, our Sponsors and Intel will be entitled to have their shares of Class A common stock registered by us on a Form S-3 registration statement at our expense. These shelf registration rights are subject to specified conditions and limitations.
Expenses and Indemnification
We will pay all expenses relating to any demand, piggyback or shelf registration, other than underwriting discounts and commissions and any transfer taxes, subject to specified conditions and limitations. The registration rights agreement will include customary indemnification provisions, including indemnification of the participating holders of shares of Class A common stock and their directors, officers and employees by us for any losses, claims, damages or liabilities in respect thereof and expenses to which such holders may become subject under the Securities Act, state law or otherwise.
Indemnification Agreements
Prior to the completion of our IPO, we entered into indemnification agreements with each of our directors. These agreements require us to indemnify these individuals and, in certain cases, affiliates of such individuals, to the fullest extent permissible under Delaware law against liabilities that may arise by reason of their service to us or at our direction, and to advance expenses incurred as a result of any proceeding against them as to which they could be indemnified. Insofar as indemnification for liabilities arising under the Securities Act may be permitted to directors, we have been informed that in the opinion of the SEC such indemnification is against public policy and is therefore unenforceable.
Certain Relationships
From time to time, Intel, our Sponsors and/or their affiliates have entered into, and may continue to enter into, arrangements with us to use our products and services. We believe that all such arrangements (other than transactions pursuant to a commercial services agreement) have been entered into in the ordinary course of business and have been negotiated on commercially reasonable terms.
Related Party Transactions Policy
In connection with our IPO, we adopted a policy with respect to the review, approval, and ratification of related person transactions. Under the policy, the Audit Committee is responsible for reviewing and approving related person transactions. In the course of its review and approval of related person transactions, the Audit Committee will consider the relevant facts and circumstances to decide whether to approve such transactions. Related person transactions must be approved or ratified by the Audit Committee based on full information about the proposed transaction and the related person’s interest.
Director Independence
Based on the information provided by each director concerning his or her background, employment, and affiliations, the Board has determined that each of Sohaib Abbasi, Gunther Bright, Mary Cranston, Tim Millikin, Emily Rollins, Jon Winkelried, Kathy Willard, and Jeff Woolard are independent directors under the rules of Nasdaq. For further information, see “Item 10. Directors, Executive Officers and Corporate Governance.”
Item 14. Principal Accounting Fees and Services.
The following sets forth fees billed by PwC, for the audit of our annual financial statements and other services rendered for the fiscal years ended December 25, 2021 and December 26, 2020:
160
|
|
Year Ended |
|
|||||
|
|
December 25, 2021 |
|
|
December 26, 2020 |
|
||
Audit Fees(1) |
|
$ |
6,786,249 |
|
|
$ |
7,270,715 |
|
Audit Related Fees(2) |
|
|
3,133,059 |
|
|
|
1,012,000 |
|
Tax Fee(3) |
|
|
101,140 |
|
|
|
300,554 |
|
All Other Fees(4) |
|
|
235,900 |
|
|
|
974 |
|
Total |
|
$ |
10,256,348 |
|
|
$ |
8,584,243 |
|
Pursuant to the Audit Committee charter, the Audit Committee is responsible for the oversight of our accounting, reporting, and financial practices. The Audit Committee has the responsibility to select, appoint, engage, oversee, retain, evaluate, and terminate our external auditors; pre-approve all audit and non-audit services to be provided, consistent with all applicable laws, to us by our external auditors; and establish the fees and other compensation to be paid to our external auditors. During 2021 and 2020, the Audit Committee pre-approved all audit and permitted non-audit services provided by PwC.
There were no other fees billed by PwC for services rendered to us, other than the services described above, for fiscal years ended December 25, 2021 and December 26, 2020.
161
PART IV
Item 15. Exhibits, Financial Statement Schedules.
(a) The following documents are filed as part of this Annual Report on Form 10-K:
(1) Financial statements (included in Item 8 of this Annual Report on Form 10-K)
(2) Financial Statement Schedules
Separate financial statement schedules have been omitted because such information is inapplicable or is included in the financial statements or notes described above.
(3) Exhibits
162
Exhibit Index
Exhibit |
|
|
|
Incorporated by Reference |
||||||
Number |
|
Exhibit Description |
|
Form |
|
File No. |
|
Exhibit |
|
Filing Date |
|
|
|
|
|
|
|
|
|
|
|
2.1 |
|
|
8-K |
|
001-39651 |
|
2.1 |
|
3/8/2021 |
|
|
|
|
|
|
|
|
|
|
|
|
2.2 |
|
|
8-K |
|
001-39651 |
|
2.1 |
|
7/2/2021 |
|
|
|
|
|
|
|
|
|
|
|
|
2.3 |
|
|
8-K |
|
001-39651 |
|
2.1 |
|
8/2/2021 |
|
|
|
|
|
|
|
|
|
|
|
|
3.1 |
|
Amended and Restated Certificate of Incorporation of McAfee Corp. |
|
8-K |
|
001-39651 |
|
3.1 |
|
10/26/2020 |
|
|
|
|
|
|
|
|
|
|
|
3.2 |
|
|
8-K |
|
001-39651 |
|
3.2 |
|
10/26/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
4.1 |
|
|
S-1/A |
|
333-249101 |
|
4.1 |
|
10/13/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
4.2 |
|
|
10-K |
|
001-39651 |
|
4.2 |
|
3/1/2021 |
|
|
|
|
|
|
|
|
|
|
|
|
10.1 |
|
|
S-1/A |
|
333-249101 |
|
10.1 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.2 |
|
|
S-1/A |
|
333-249101 |
|
10.2 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.3 |
|
|
S-1/A |
|
333-249101 |
|
10.3 |
|
10/13/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.4 |
|
|
S-1/A |
|
333-249101 |
|
10.4 |
|
10/13/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.5 |
|
|
S-1/A |
|
333-249101 |
|
10.39 |
|
10/13/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.6 |
|
Office Lease, dated April as of April 10, 2019 between US ER America Center 4, LLC and McAfee, LLC |
|
S-1/A |
|
333-249101 |
|
10.8 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
10.7 |
|
|
8-K |
|
001-39651 |
|
10.1 |
|
10/26/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
163
10.8 |
|
|
8-K |
|
001-39651 |
|
10.2 |
|
10/26/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.9 |
|
|
8-K |
|
001-39651 |
|
10.3 |
|
10/26/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.10 |
|
|
8-K |
|
001-39651 |
|
10.4 |
|
10/26/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.11+ |
|
|
S-1/A |
|
333-249101 |
|
10.13 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.12+ |
|
|
S-1/A |
|
333-249101 |
|
10.14 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.13+ |
|
|
S-1/A |
|
333-249101 |
|
10.15 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.14+ |
|
|
S-1/A |
|
333-249101 |
|
10.16 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.15+ |
|
|
S-1/A |
|
333-249101 |
|
10.17 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.16+ |
|
Offer Letter, dated as of January 31, 2017, by and between Intel Security and Michael Berry. |
|
S-1/A |
|
333-249101 |
|
10.18 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
10.17+ |
|
Offer Letter by and between McAfee, Inc. and John Giamatteo. |
|
S-1/A |
|
333-249101 |
|
10.19 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
10.18+ |
|
Offer Letter, dated as of September 30, 2020, by and between McAfee, LLC and Ashutosh Kulkarni. |
|
S-1/A |
|
333-249101 |
|
10.20 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
10.19+ |
|
Offer Letter, dated as of September 30, 2020, by and between McAfee, LLC and Terry Hicks. |
|
S-1/A |
|
333-249101 |
|
10.21 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
10.20+ |
|
Offer Letter, dated as of April 6, 2020, by and between McAfee, LLC and Lynne Doherty McDonald. |
|
S-1/A |
|
333-249101 |
|
10.22 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
10.21+ |
|
Promotion Letter, dated as of June 11, 2018, by and between McAfee, LLC and with John Giamatteo. |
|
S-1/A |
|
333-249101 |
|
10.23 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
10.22+ |
|
|
S-1/A |
|
333-249101 |
|
10.24 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.23+ |
|
Separation Agreement, dated February 3, 2020, by and between McAfee, LLC and Christopher D. Young. |
|
S-1/A |
|
333-249101 |
|
10.25 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
10.24+ |
|
|
S-1/A |
|
333-249101 |
|
10.26 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.25+ |
|
|
8-K |
|
001-39651 |
|
10.5 |
|
10/26/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.26+ |
|
|
8-K |
|
001-39651 |
|
10.6 |
|
10/26/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.27+ |
|
|
8-K |
|
001-39651 |
|
10.7 |
|
10/26/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.28+ |
|
|
S-1/A |
|
333-249101 |
|
10.34 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
164
10.29+ |
|
|
S-1/A |
|
333-249101 |
|
10.31 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.30+ |
|
|
S-1/A |
|
333-249101 |
|
10.32 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.31+ |
|
Form of Management Incentive Unit (MIU) Agreement under the 2017 Plan. |
|
S-1/A |
|
333-249101 |
|
10.28 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
10.32+ |
|
|
S-1/A |
|
333-249101 |
|
10.29 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.33+ |
|
|
S-1/A |
|
333-249101 |
|
10.35 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.34+ |
|
|
S-1/A |
|
333-249101 |
|
10.36 |
|
10/13/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.35+ |
|
|
S-1/A |
|
333-249101 |
|
10.37 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.36+ |
|
|
S-1/A |
|
333-249101 |
|
10.38 |
|
10/8/2020 |
|
|
|
|
|
|
|
|
|
|
|
|
10.37 |
|
|
10-Q |
|
001-39651 |
|
10.1 |
|
11/9/2021 |
|
|
|
|
|
|
|
|
|
|
|
|
10.38+ |
|
|
10-Q |
|
001-39651 |
|
10.2 |
|
11/9/2021 |
|
|
|
|
|
|
|
|
|
|
|
|
10.39+ |
|
|
10-Q |
|
001-39651 |
|
10.3 |
|
11/9/2021 |
|
|
|
|
|
|
|
|
|
|
|
|
10.40+ |
|
|
10-Q |
|
001-39651 |
|
10.4 |
|
11/9/2021 |
|
|
|
|
|
|
|
|
|
|
|
|
21.1* |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
23.1* |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
31.1* |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
31.2* |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
32.1* |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
32.2* |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
101.INS |
|
Inline XBRL Instance Document |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
101.SCH |
|
Inline XBRL Taxonomy Extension Schema Document |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
101.CAL |
|
Inline XBRL Taxonomy Extension Calculation Linkbase Document |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
101.DEF |
|
Inline XBRL Taxonomy Extension Definition Linkbase Document |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
101.LAB |
|
Inline XBRL Taxonomy Extension Label Linkbase Document |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
101.PRE |
|
Inline XBRL Taxonomy Extension Presentation Linkbase Document |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
104 |
|
Cover Page Interactive Data File (formatted as inline XBRL and contained in Exhibit 101) |
|
|
|
|
|
|
|
|
+ Indicates management contract or compensatory plan or arrangement.
* Filed herewith.
165
Item 16. Form 10-K Summary
None.
166
SIGNATURES
Pursuant to the requirements of Section 13 or 15(d) of the Securities Exchange Act of 1934, as amended, the Registrant has duly caused this Report to be signed on its behalf by the undersigned, thereunto duly authorized.
|
|
McAfee Corp. |
|
|
|
|
|
Date: February 23, 2022 |
|
By: |
/s/ Peter Leav |
|
|
|
Peter Leav |
|
|
|
President, Chief Executive Officer and Director |
|
|
|
(Principal Executive Officer) |
Pursuant to the requirements of the Securities Exchange Act of 1934, as amended, this Report has been signed below by the following persons on behalf of the Registrant in the capacities and on the dates indicated.
Name |
|
Title |
|
Date |
|
|
|
|
|
/s/ Peter Leav |
|
President, Chief Executive Officer and Director |
|
February 23, 2022 |
Peter Leav |
|
(Principal Executive Officer) |
|
|
|
|
|
|
|
/s/ Venkat Bhamidipati |
|
Executive Vice President and Chief Financial Officer |
|
|
Venkat Bhamidipati |
|
(Principal Financial Officer) |
|
|
|
|
|
|
|
/s/ Christine Kornegay |
|
Vice President and Chief Accounting Officer |
|
|
Christine Kornegay |
|
(Principal Accounting Officer) |
|
|
|
|
|
|
|
/s/ Sohaib Abbasi |
|
Director |
|
|
Sohaib Abbasi |
|
|
|
|
|
|
|
|
|
/s/ Mary Cranston |
|
Director |
|
|
Mary Cranston |
|
|
|
|
|
|
|
|
|
/s/ Tim Millikin |
|
Director |
|
|
Tim Millikin |
|
|
|
|
|
|
|
|
|
/s/ Jon Winkelried |
|
Director |
|
|
Jon Winkelried |
|
|
|
|
|
|
|
|
|
/s/ Kathy Willard |
|
Director |
|
|
Kathy Willard |
|
|
|
|
|
|
|
|
|
/s/ Jeff Woolard |
|
Director |
|
|
Jeff Woolard |
|
|
|
|
|
|
|
|
|
/s/ Gunther Bright |
|
Director |
|
|
Gunther Bright |
|
|
|
|
|
|
|
|
|
/s/ Emily Rollins |
|
Director |
|
|
Emily Rollins |
|
|
|
|
167